Details
This is a writeup for the basic missions from http://hackthissite.org/
Basic One
![]()
The hint for this task caused me to think of the html source as this is a common entry level task
![]()
Within the html source I was able to find the password
915491ce
I then used this to login
![]()
Basic Two
Here I thought, if it was simply comparing two strings and one was missing, if it didn't crash it would be comparing to a blank string. So I submitted an empty password
Basic Three
I started by checking the source code, where I found a link to /password.php
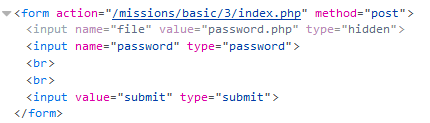
So I went to https://www.hackthissite.org/missions/basic/3/password.php
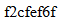
Now with a password
f2cfef6f
I used it to login
Basic Four
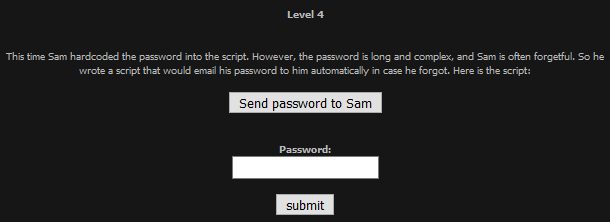
Upon inspecting the source code I found the email was set in the html
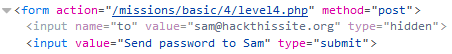
I then changed the email to my own email and clicked the button to send the it. When I checked my email I had the password
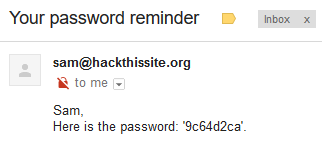
9c64d2ca
Using this to login
Basic Five
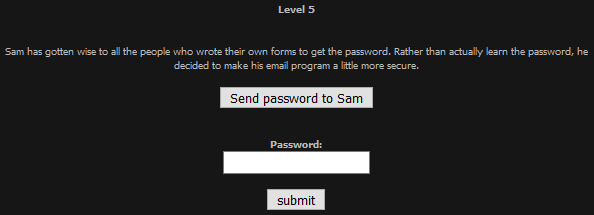
This looked similar to the last one, so I repeated the process
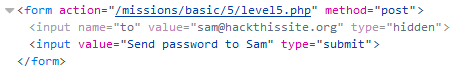
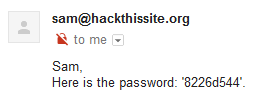
8226d544
Then I logged in
Basic Six
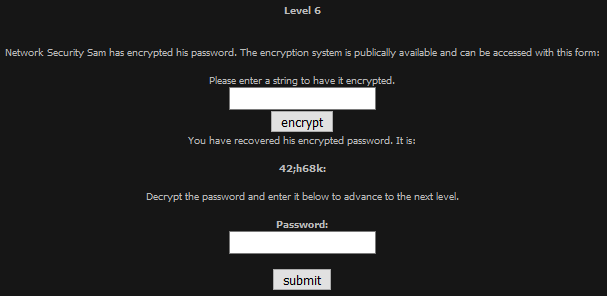
On this task I carried out a bit of trial and error, and deduced that the encryption merely added the 0-indexed position of the character, to the characters ASCII code, as such I could reverse it by subtracting that value. Which led to the password
419e23e3
Basic Seven
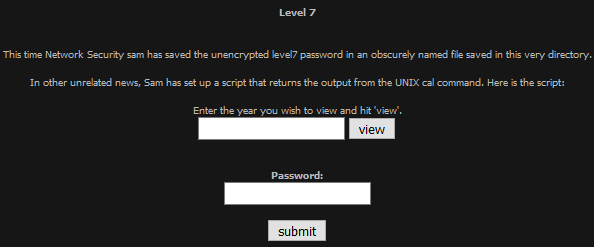
This looked like an easy command injection based on the hint, so I submitted
; ls -la
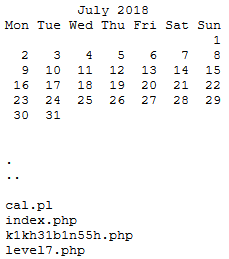
I then navigated to https://www.hackthissite.org/missions/basic/7/k1kh31b1n55h.php to get the password
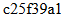
c25f39a1
Using this I progressed to the next level
Basic Eight
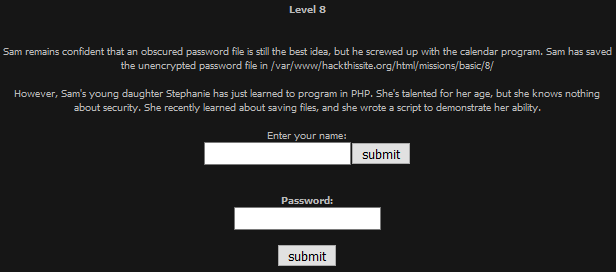
To started with I entered "test"
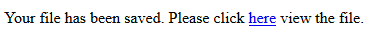
I then clicked on "here"
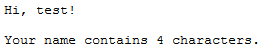
In this file I noticed the extension was .shtml which meant I may be able to inject a server side include to find the password. So I injected
<!-- #exec cmd="ls ../" -->
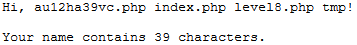
I then navigated to https://www.hackthissite.org/missions/basic/8/au12ha39vc.php
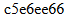
c5e6ee66
Using this I logged in again
Basic Nine
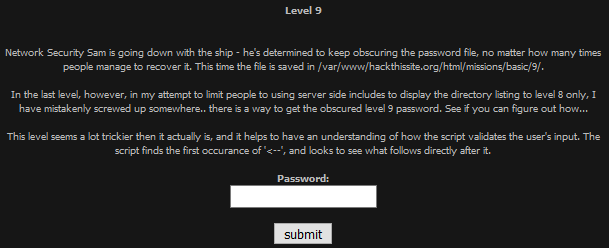
To do this, I went back to level 8 and injected
<!--#exec cmd="ls ../../9" -->
Using directory traversal to get the location of the password
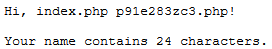
To get the password I went to https://www.hackthissite.org/missions/basic/9/p91e283zc3.php
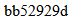
bb52929d
Which led to
Basic Ten
I tried looking around, then a random password. When I noticed in the response there was a cookie, upon inspection it seemed the cookie was used for auth
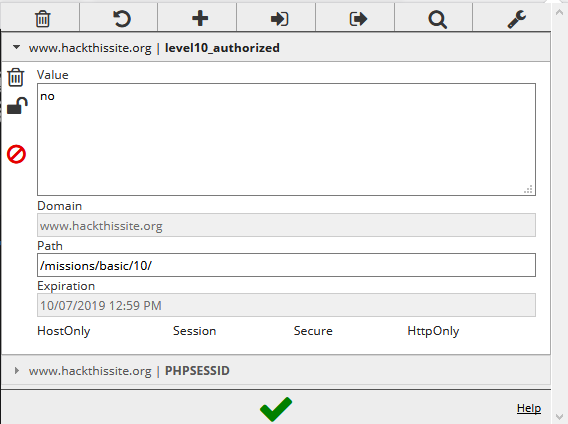
I set the value to "yes" then tried another random password
Basic Eleven
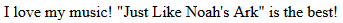
I found the on every load the name of the song changed. To start I tried to access .htaccess but could not. I then tried /index.php
Now knowing where to put the password once I had it. I began to dig some more, trying some directories, I then found /e
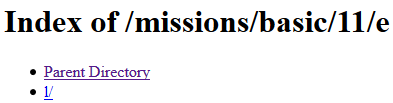
I followed the directories down to https://www.hackthissite.org/missions/basic/11/e/l/t/o/n/ which was blank, I then tried .htaccess again
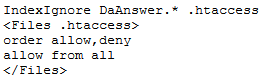
This led me to going to https://www.hackthissite.org/missions/basic/11/e/l/t/o/n/DaAnswer

I tried looking for some more files to do with it, but found nothing. So I decided to take the hint literally and try "available" as the password
And that was basic 11 done and with that, all the basic missions