Prerequisties
For this tutorial I am assuming you have already installed VirtualBox and the VirtualBox Extension Pack. Both of which can be found at https://www.virtualbox.org/wiki/Downloads.
I will be using virtual box 5.2.12 on Ubuntu 18.04 throughout this tutorial but the process should not be different on other systems.
Downloading the kali image
Now kali has been known to be a bit awkward to setup in VMs, so the good people over at Offensive Security have put together some pre-made images available here. On that page scroll down to the section labelled "Download Kali Linux VMware and VirtualBox Images". In the table below are download links for another VM tool called VMware. We want the virtual box ones so click on the other tab in the table.
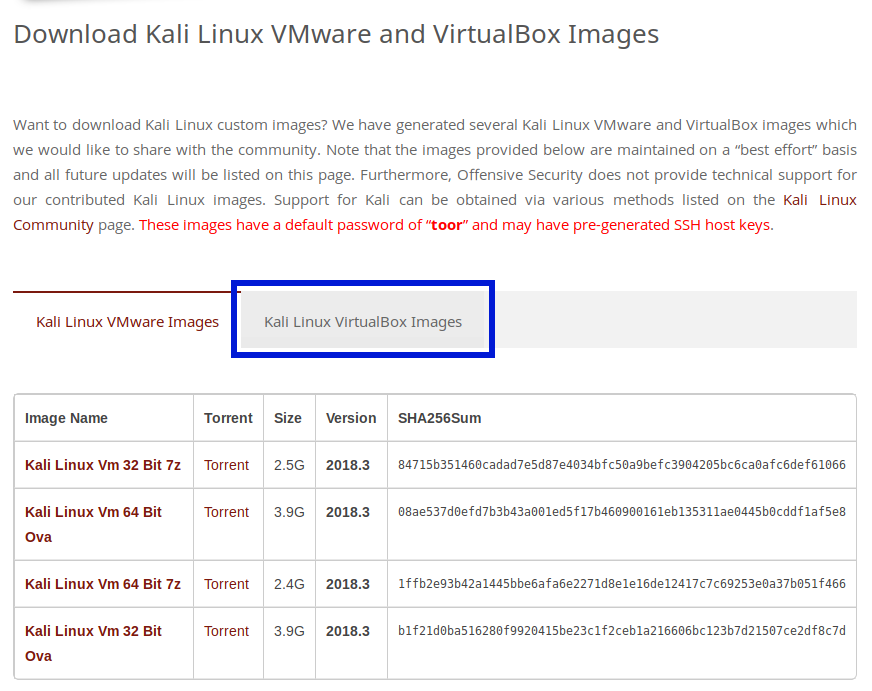
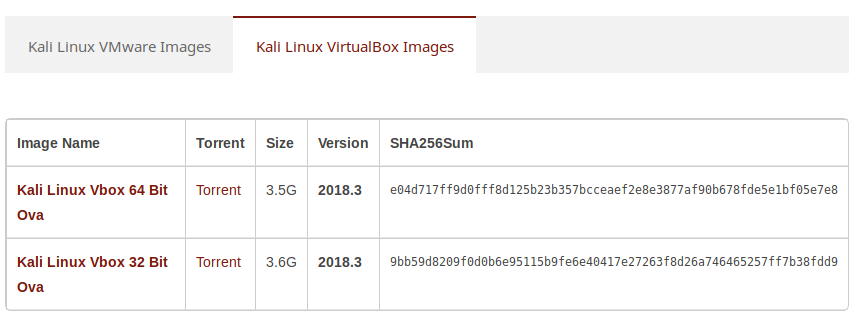
Once you have the virtual box option selected, there should be 2 rows in the table, one for 32 bit and one for 64 bit. I will be downloading the 64 bit version, but you should download the version that is correct for you.
Importing the image
The first step is obviously to open virtual box where you should be presented with something which looks similar too this
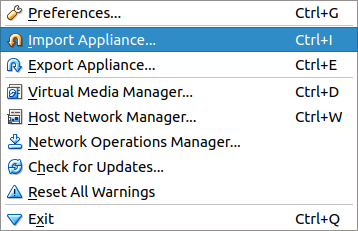
From here you want to click "File" from the top menu, and then "Import Appliance"
A new box will show up,
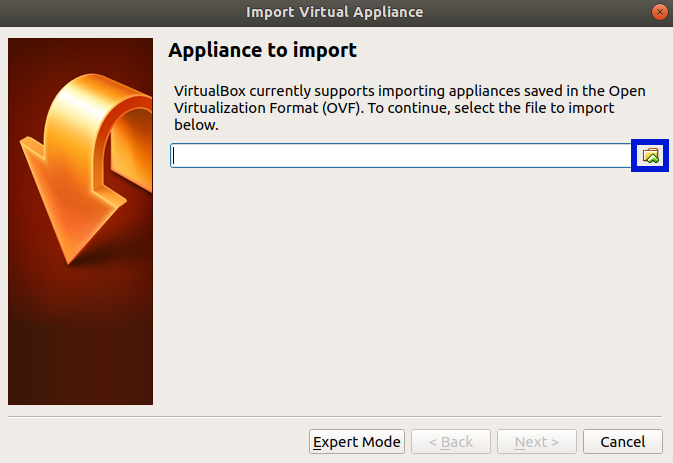
Click on the folder icon, and select the kali iso downloaded earlier, then click next. On the next menu click import
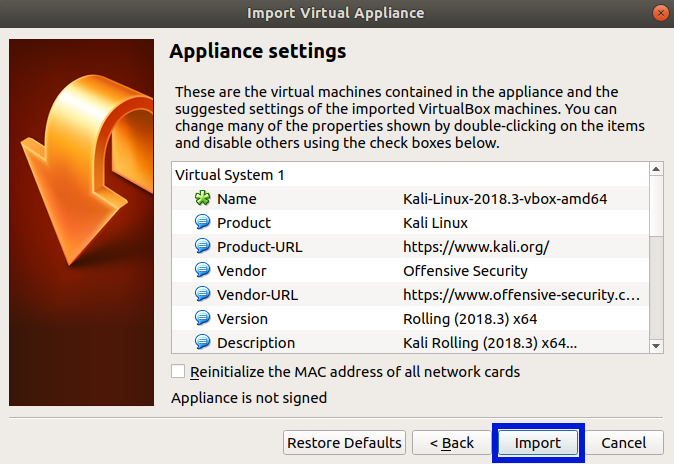
A progress bar will show up, wait for it to complete!
After which there should now be a machine listed on the main menu
Setting up the machine
The next step is to right click on that machine and click settings
In the settings, first go to "General" and then "Advanced", here I personally set Drag and drop to off
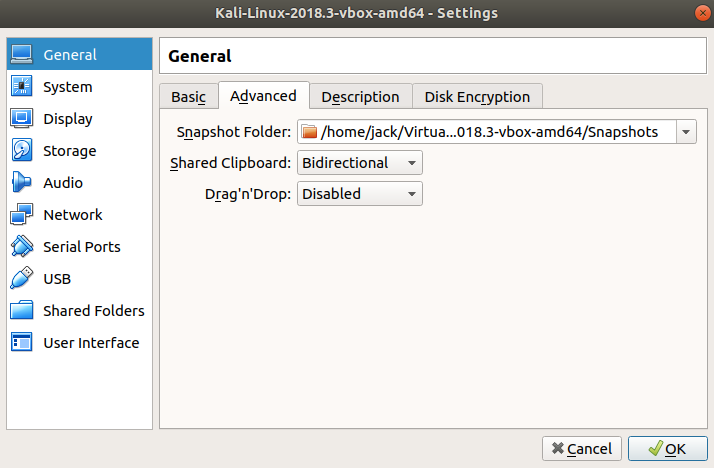
The next menu is "System", under "Motherboard", using the slider I will typically give a kali VM access to 2/3 of my RAM.
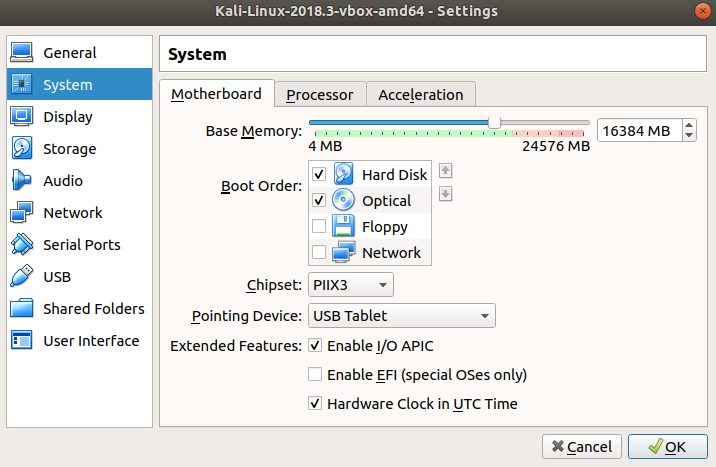
From here, I click the sub-menu for "Processor". Which, again using the slider, I give access to 1/2 my cores
Finally click "OK" to save these settings
Setting up networking
Now we need an internal network to connect our kali machine to any virtual machines we want to attack, without exposing them to the internet!
To do this click "File" from the top menu, then "Host network manager"
You should be presented with a pop up which lists internal networks. It is most likely empty at the moment
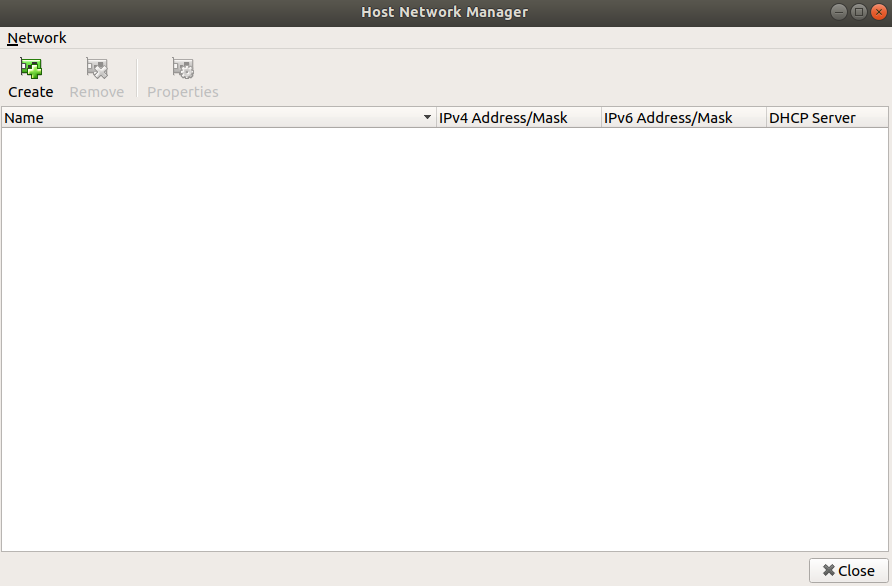
Here click the create button, a new item will be added to the list. You then want to tick the DHCP Server tickbox
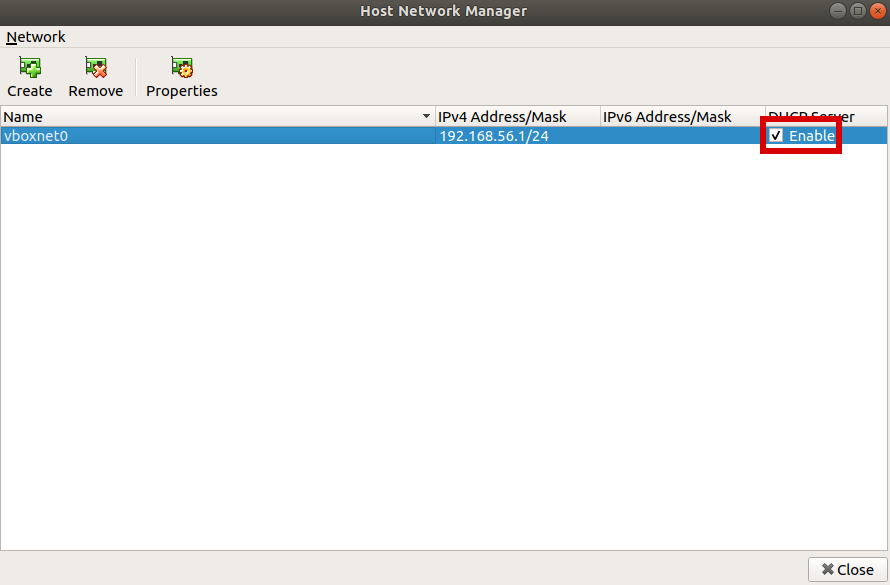
With the network setup, click "Close", then back on the main menu, right click on the kali VM and click "settings" again. From there click the "Network" tab
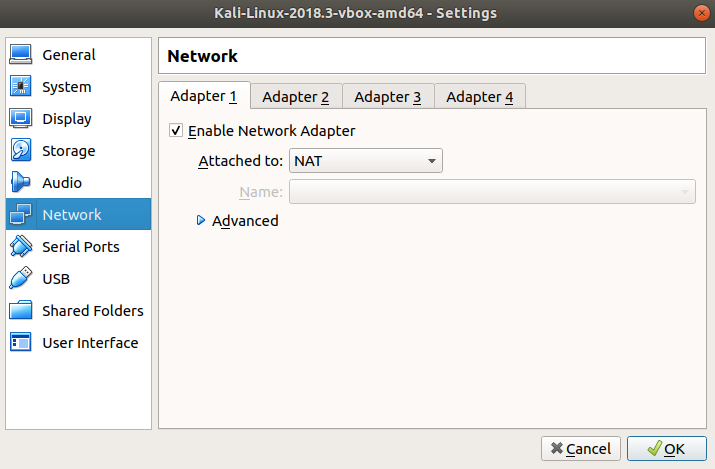
I normally change Adapter 1 to "Host-only Adapter" and make sure it selects the network we just created.
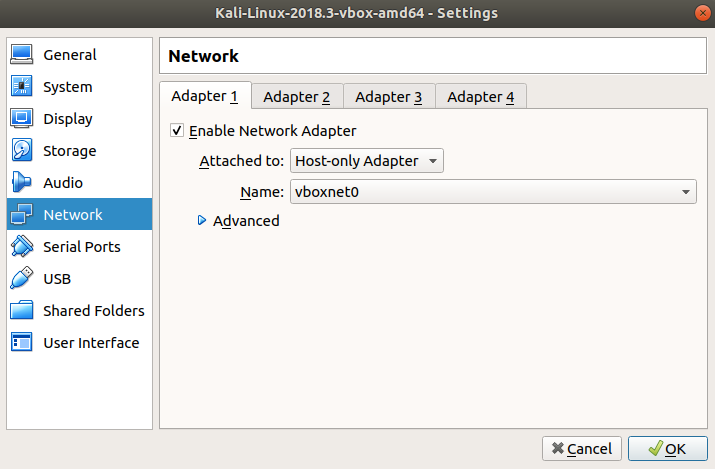
Then click on the "Adapter 2" sub-menu, this adapter will be used so the kali VM can toggle between being on the isolated internal network and connecting to the internet
On the "Adapter 2" menu, tick "Enable Network Adapter", then from the "Attached to:" drop down, select "NAT"
Note: Never give NAT access to a vulnerable virtual machine, make sure you always isolate them into the host only adapter
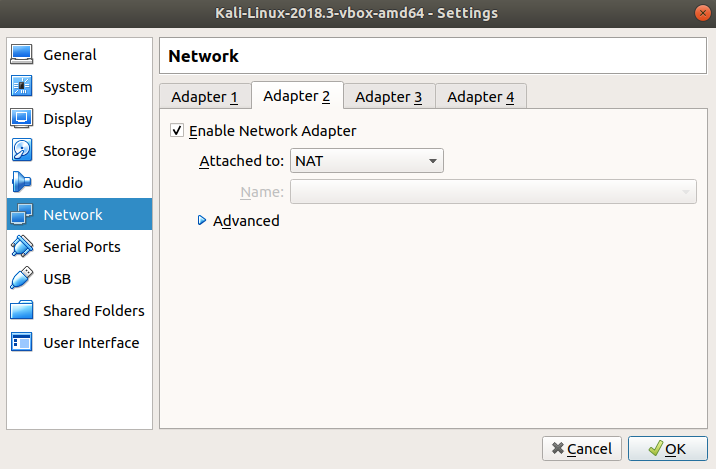
Once you've done this, click "OK".
The machine is now ready to be booted and configured.
Configuring Kali
To boot the machine, double click on it, a new window containing the VM should pop up. Wait until it displays something like this
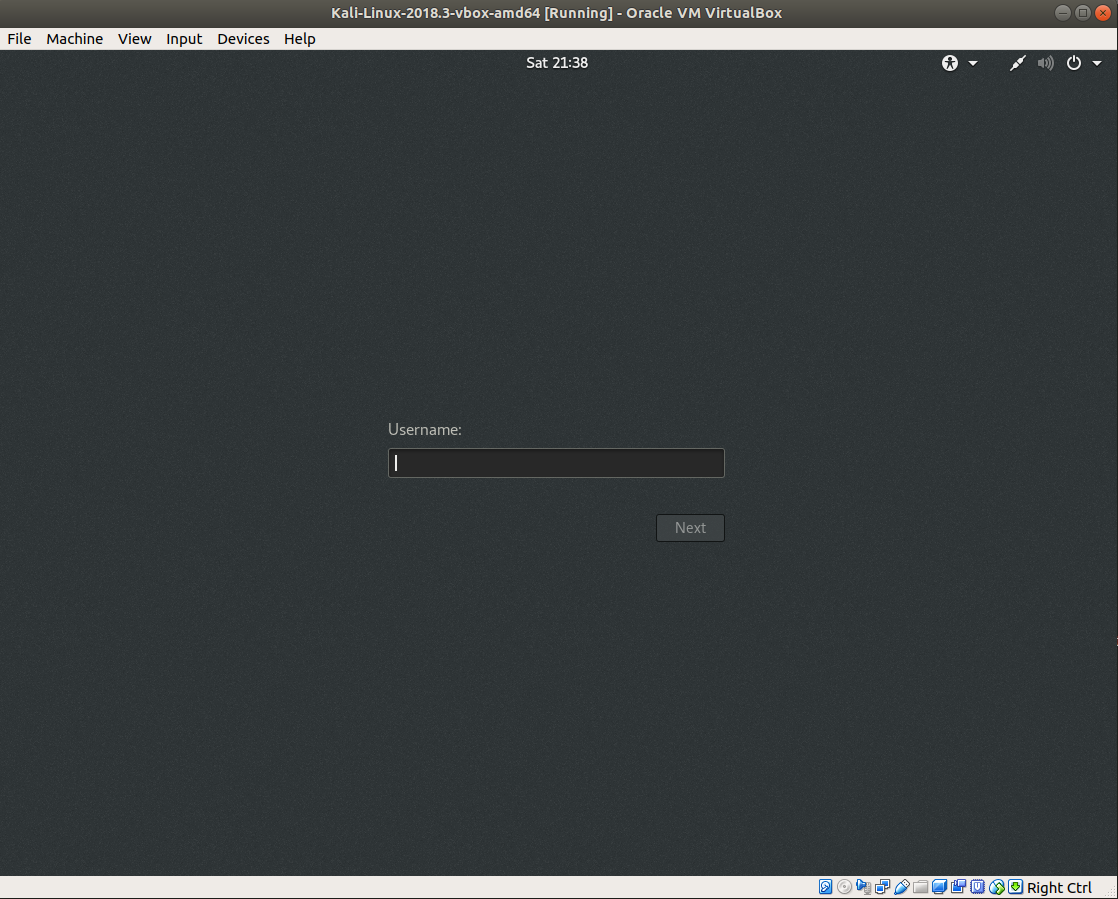
Now, the default login on these images is
Username: root
Password: toor
Login using these!
My first step is to change some default settings, click on the arrow in the top right, then on the settings button
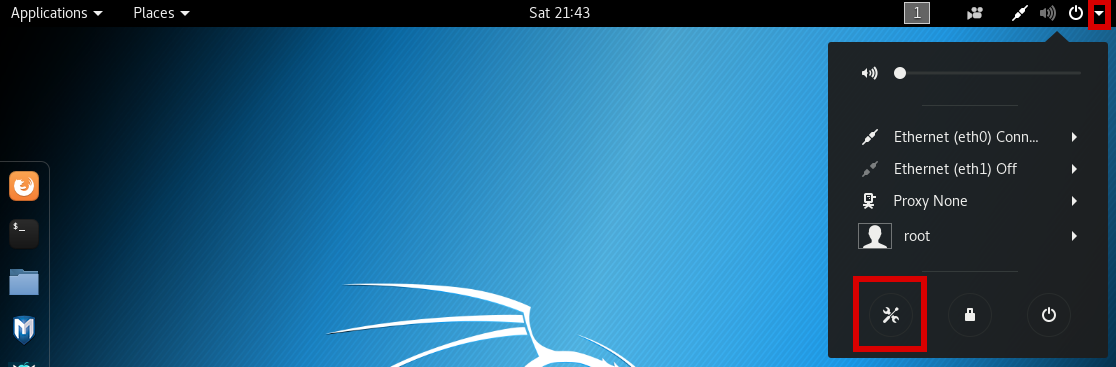
It should default to the "Power" menu, if not select it on the left. I then ensure "Blank Screen" is set to "Never" and "Automatic Suspend" is off
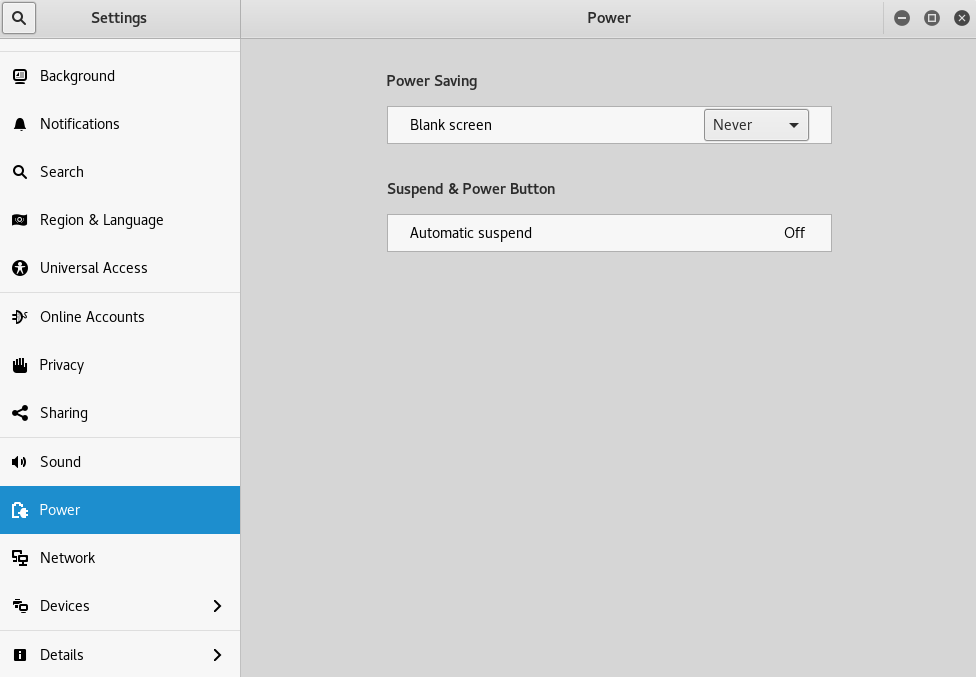
Personally, I then change the keyboard layout from US, to UK. But if you prefer the US layout you can skip this step. But to do it, you select "Region & Language" from the left menu
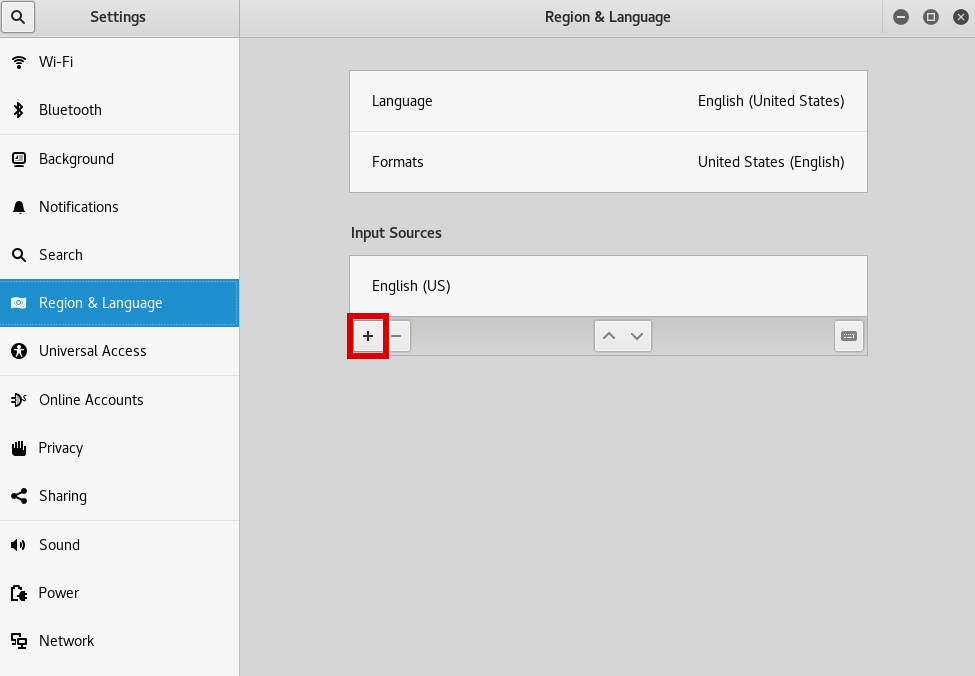
Then click the cross and add your preferred layout. At this stage you will have US and your preferred one enabled. To make your preferred one the only one, select "English (US)" then the minus symbol
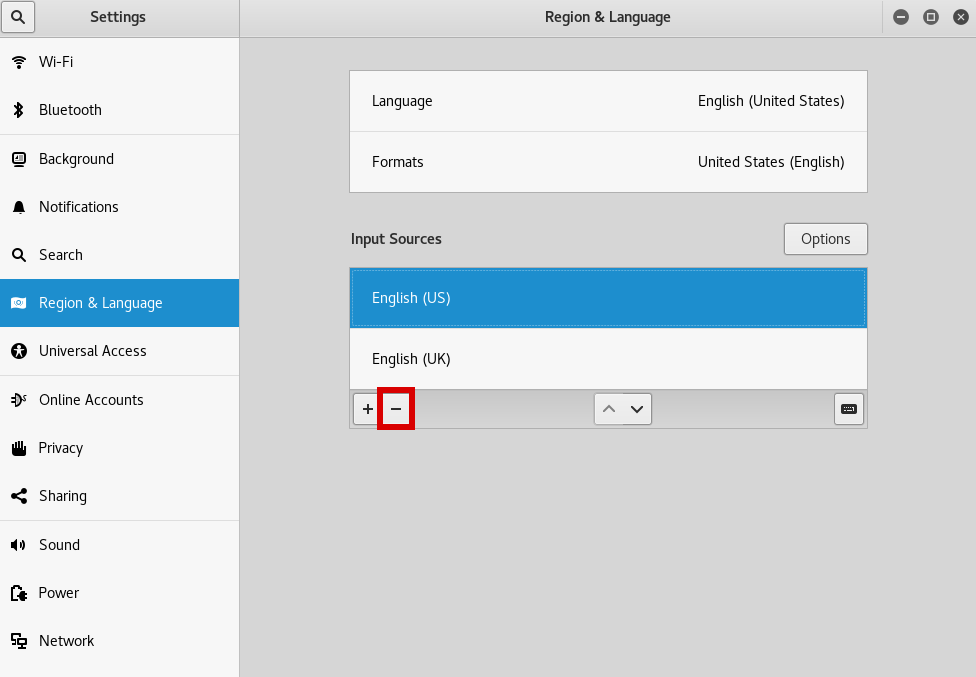
This will leave you with just your preferred keyboard layout.
That's the end of what we needed from the settings menu, so close that, and open a terminal by clicking on the icon from the quick access bar
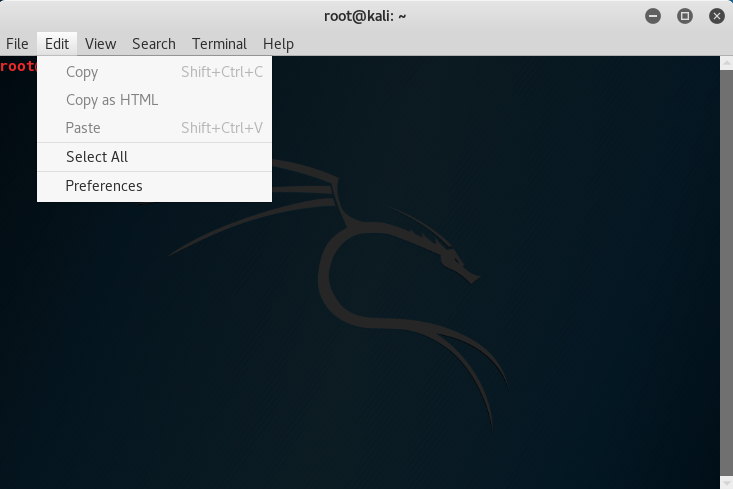
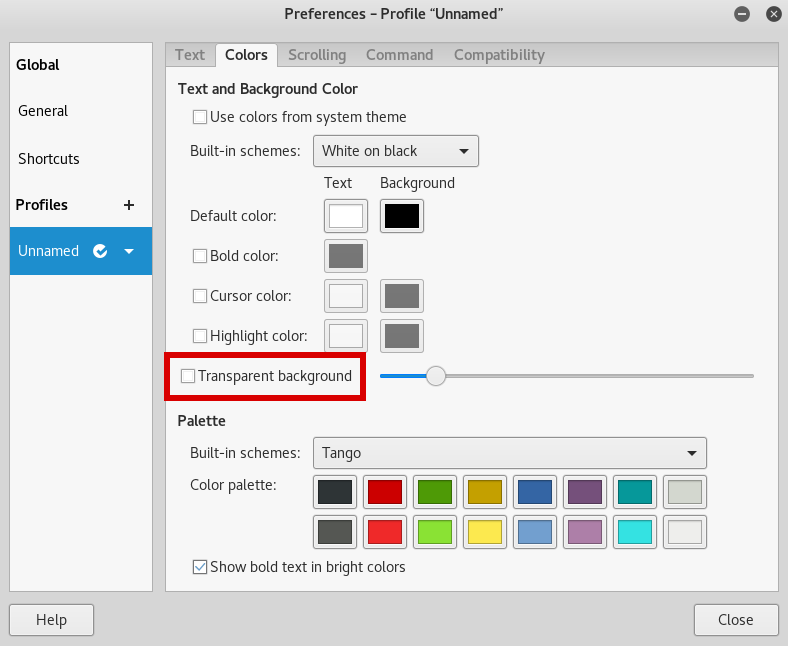
Here I prefer to turn off transparency on the terminal, first click "Edit" at the top of the terminal, and then "Preferences"
From here, click "Colors" and then untick "Transparent background", then click "Close"
Next I test to see which adapter the boot default is, I do this by attempting to ping (these are terminal commands that you should enter into the terminal opened earlier)
root@kali:~# ping 8.8.8.8
If you see
connect: Network is unreachable
Then it defaulted to the internal network, whereas if you see something like
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=63 time=24.7 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=63 time=24.6 ms
[SNIP]
--- 8.8.8.8 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 2421ms
rtt min/avg/max/mdev = 24.665/24.703/24.742/0.161 ms
It defaulted to the NAT adapter. For the next section you want to be on the NAT adapter, if you aren't you can change to it by clicking on the same dropdown which you opened the settings menu from, and then clicking on the other adapters name, then "Connect"
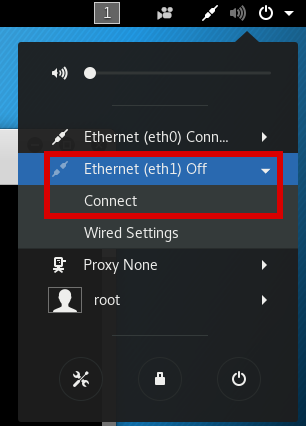
Use the ping command again to check you are now connected to the internet.
Once you're online, first we want to update the machine (each of these commands can take a while)
root@kali:~# apt-get dist-upgrade -y
Note: During the execution of this command you may be asked some options, it is generally safe to just accept the defaults, also if you get asked to read patch notes, you can press "q" to close them
Note 2: If you are asked to select grub partitions, if you are unsure what to do then tick every partition
Then
root@kali:~# apt-get update -y
And finally
root@kali:~# apt-get upgrade -y
A quick tip is to unzip the rockyou.txt wordlist which can be done using the following command
root@kali:~# gunzip /usr/share/wordlists/rockyou.txt.gz
And also to update wpscans database
root@kali:~# wpscan --update
With that the machine is configured and in general ready to go. You can, of course further customise. I personally install a set of tools, both public and my own developed ones. I also download my dot-files (e.g .bashrc, .gdbinit) which contain my settings and preferences to a lot of tools.
You may also wish to setup metasploits database, although I do not as I avoid using metasploit while I am still learning and practicing!